Access control method and system and electronic equipment
A technology for access control and electronic equipment, applied in the field of communication, can solve the problems of limited LPA function and high difficulty in implementation, and achieve the effect of safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
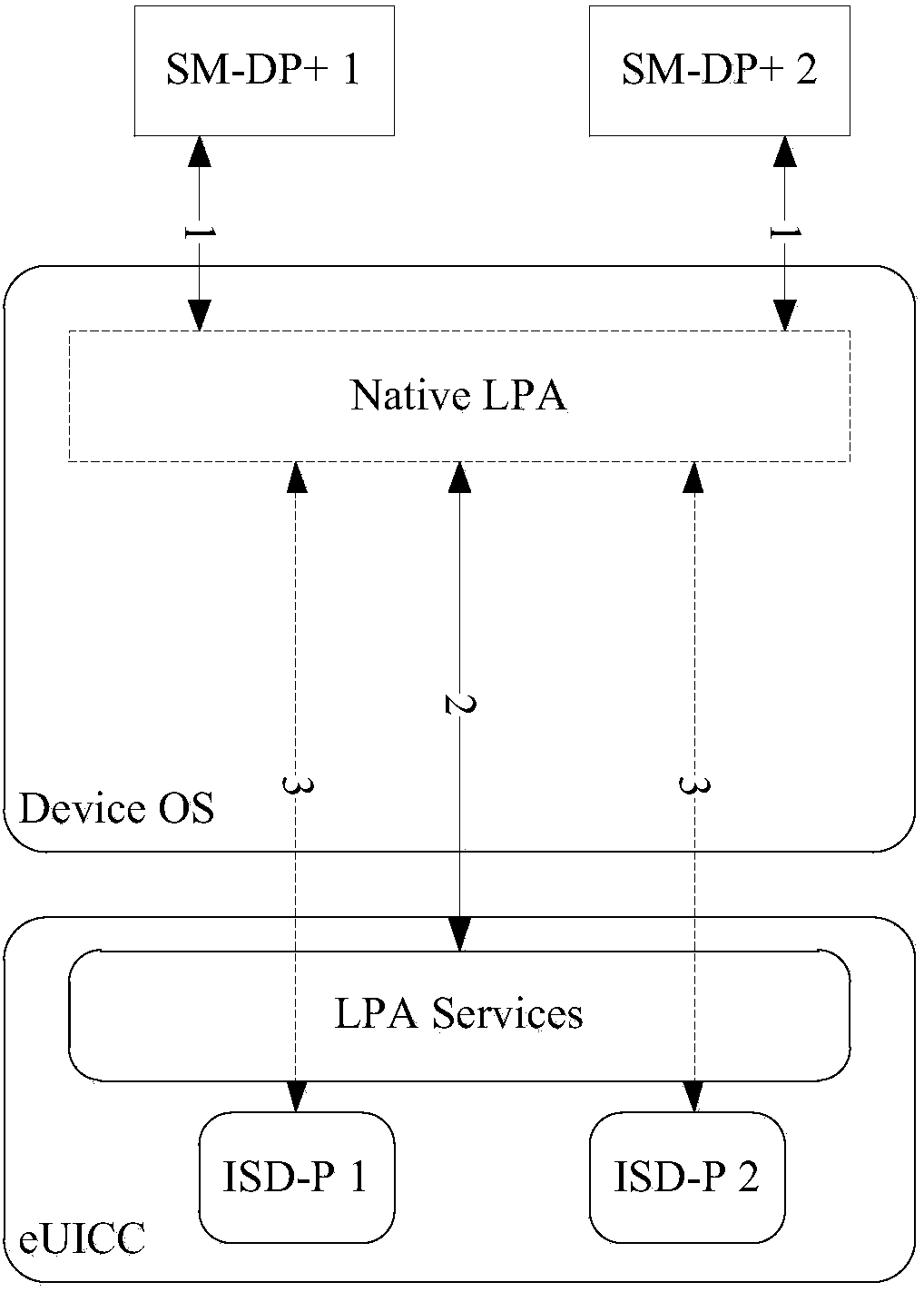
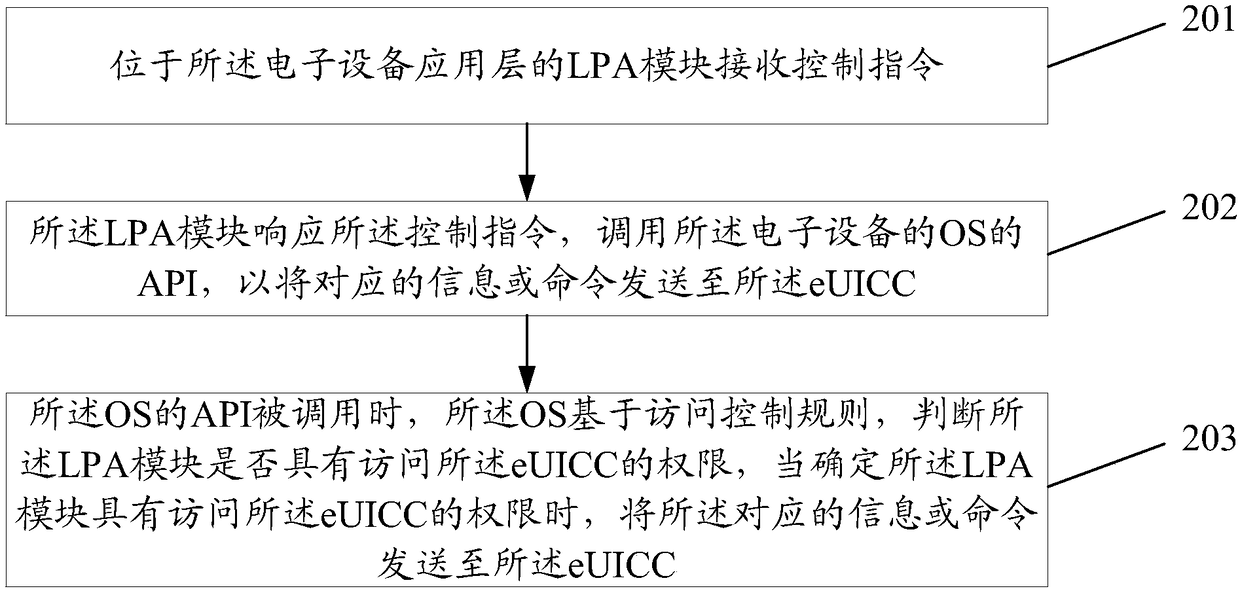
[0070] The access control method of the embodiment of the present invention is applied to electronic equipment, which may be: wearable equipment, mobile phone, Tablet, etc.; figure 2 As shown, the method includes the following steps:
[0071] Step 201: The LPA module located at the application layer of the electronic device receives the control instruction;
[0072] Here, the control instruction is used to instruct the eUICC to perform a control operation.
[0073] Wherein, in actual application, the control instruction may be a control instruction issued by the user when performing related operations on the ISD-P in the eUICC, for example, when performing operations such as activation / deactivation and deletion; the control instruction may also be When the user implements SM-DP+ or the service platform interacts with the eUICC through the electronic device (the LPA module). During the interaction, another example is: the control command sent by the user when the user implem...
Embodiment 2
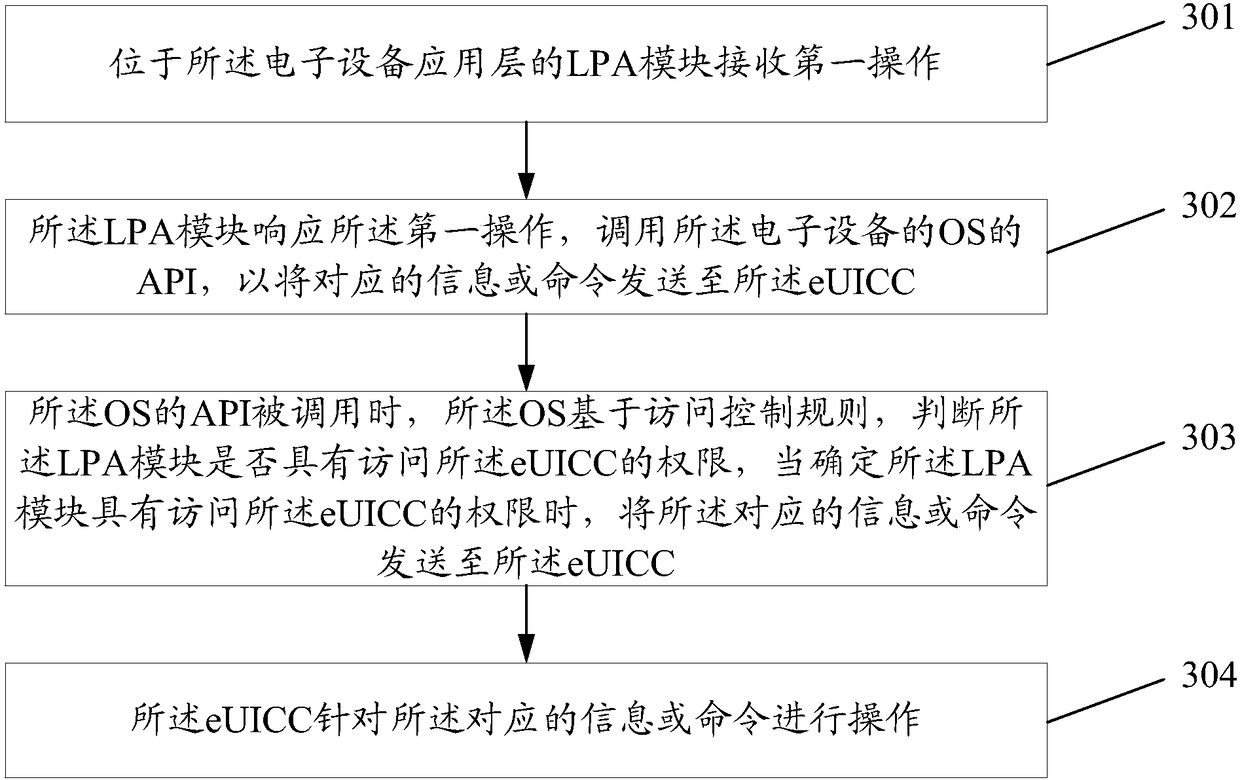
[0099] In order to implement the method of the embodiment of the present invention, this embodiment provides an electronic device, which may be: a wearable device, a mobile phone, a Tablet, etc.; such as Figure 4 As shown, the electronic equipment includes:
[0100] The LPA module 41 located at the application layer of the electronic device is used to receive a control instruction; the control instruction is used to instruct the eUICC to perform a control operation; and in response to the control instruction, call the API of the OS module 42 to transfer the corresponding information or command sent to said eUICC;
[0101] The OS module 42 is configured to determine whether the LPA module has access to the eUICC based on access control rules when its own API is called, and when it is determined that the LPA module 41 has access to the eUICC, set The corresponding information or command is sent to the eUICC, so that the eUICC operates on the corresponding information or comman...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com