Network connection authentication method and device, electronic equipment and storage medium
A network connection and authentication method technology, applied in the fields of devices, network connection authentication methods, electronic equipment and storage media, can solve the problem of increased intranet data security, inability to determine users, increased labor costs, and limitations of intranet data security, etc. To solve the problem of enterprise network security management, reduce the use of people, and improve the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
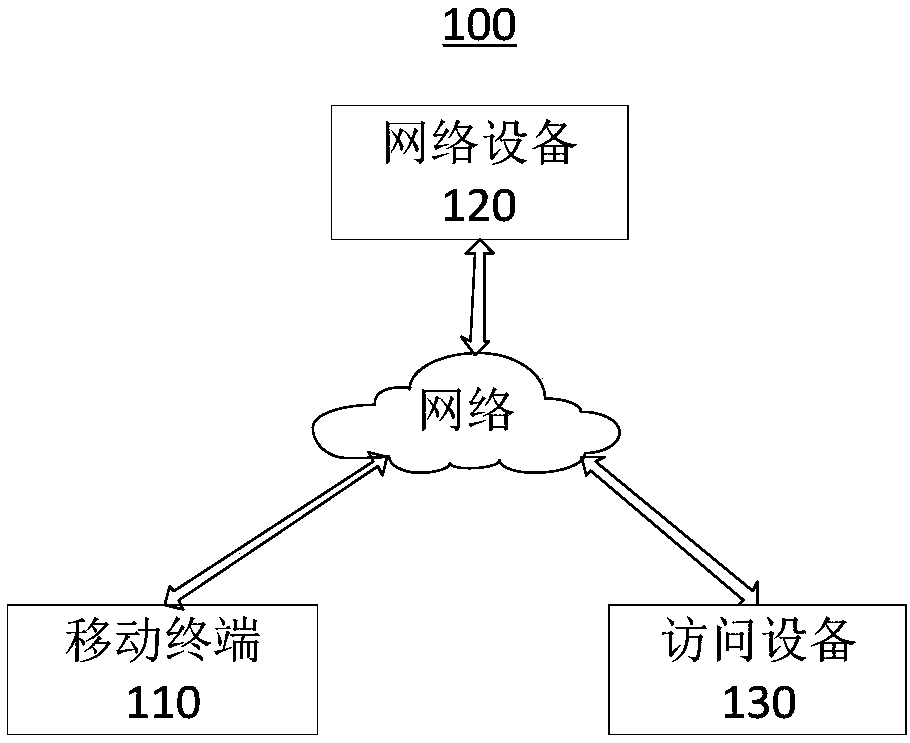
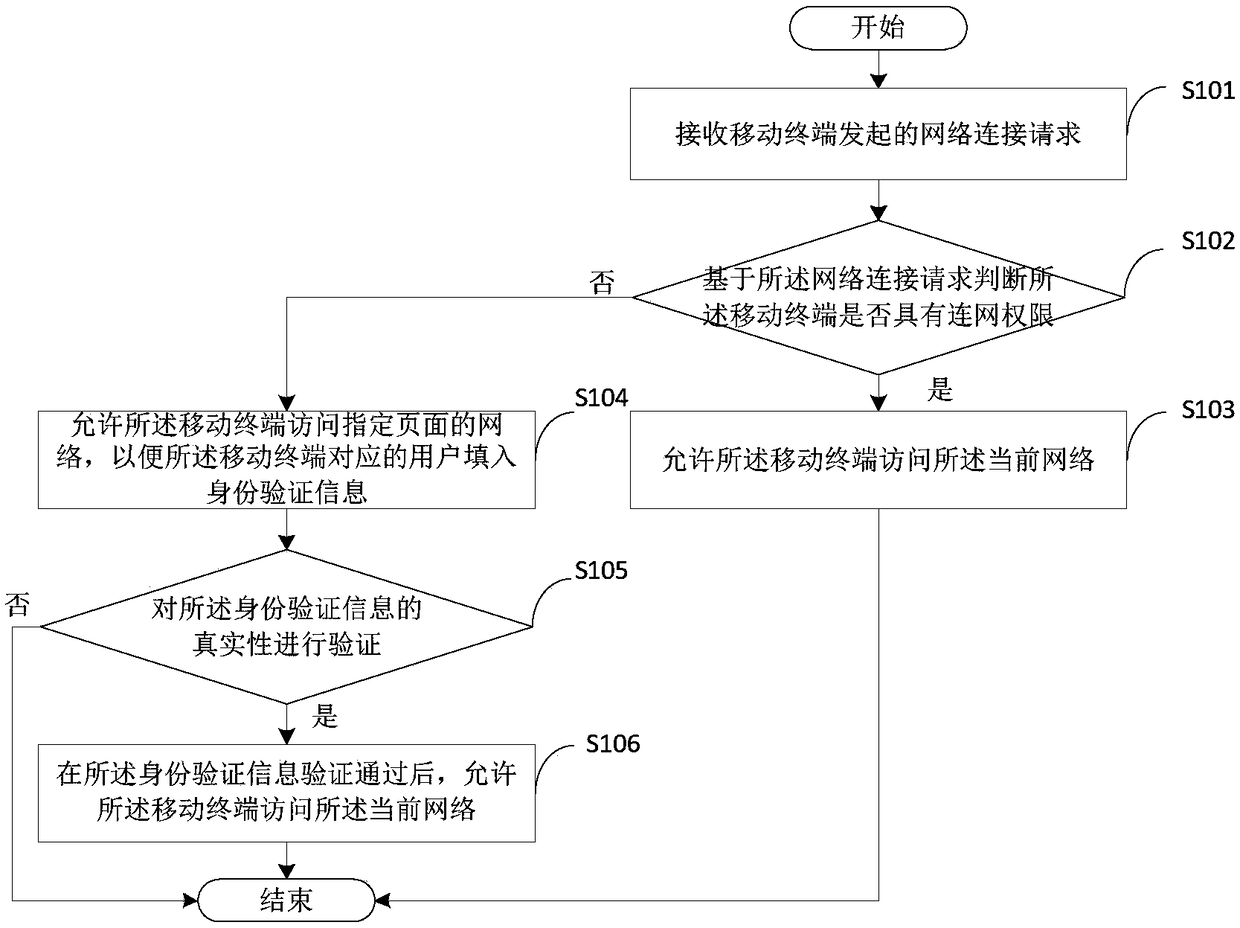
[0031] see image 3 , is a network connection authentication method applied to the above-mentioned network device 120 provided by the embodiment of the present invention, which will be combined below image 3 Describe the steps involved.
[0032]Step S101: Receive a network connection request initiated by a mobile terminal.
[0033] When the mobile terminal turns on the WiFi broadcast and enters the network coverage of the enterprise intranet, the network device can receive the WiFi broadcast information of the mobile terminal, that is, receive the network connection request initiated by the mobile terminal.
[0034] Step S102: Based on the network connection request, it is judged whether the mobile terminal has the right to connect to the network.
[0035] The network device will record and analyze the WiFi broadcast information (network connection request), and judge whether the mobile terminal has the network connection permission based on the network connection request, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com