Network port security-based micro-isolation system
A technology for isolating systems and network ports, applied in the field of micro-isolation systems, it can solve the problems of inconsistent hardware firewall functions, difficult upgrades, and increased procurement and maintenance costs, so as to solve the security management of east-west traffic and avoid the spread of attack risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0040] Example: The specific micro-isolation implementation process is as follows:
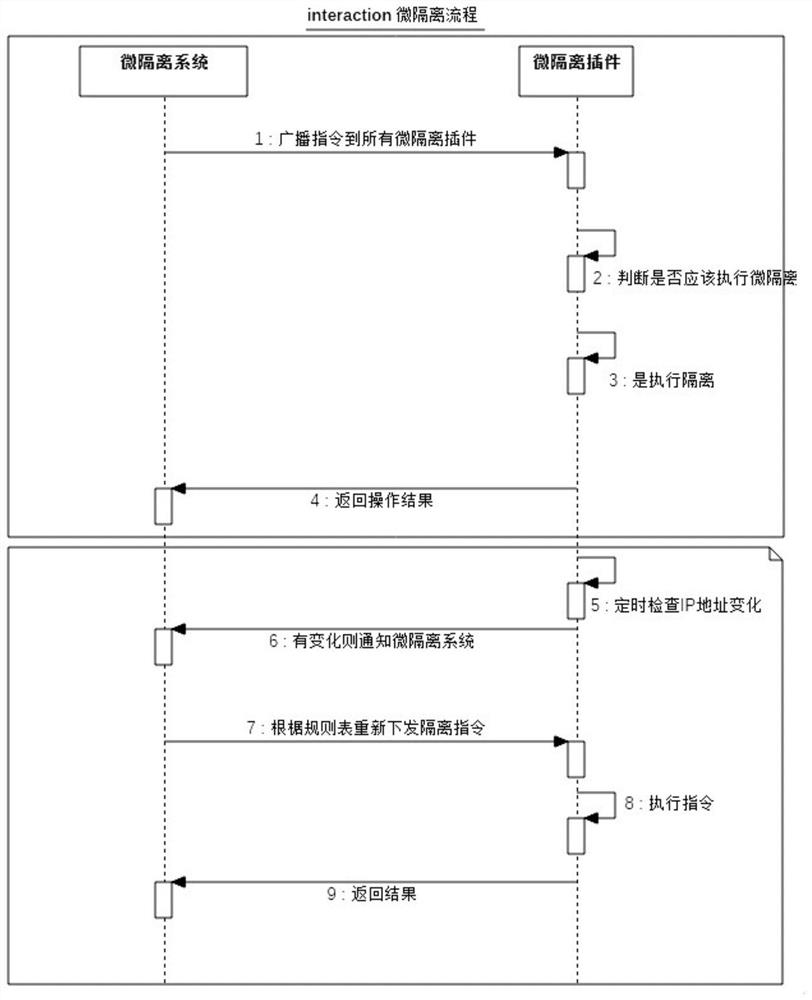
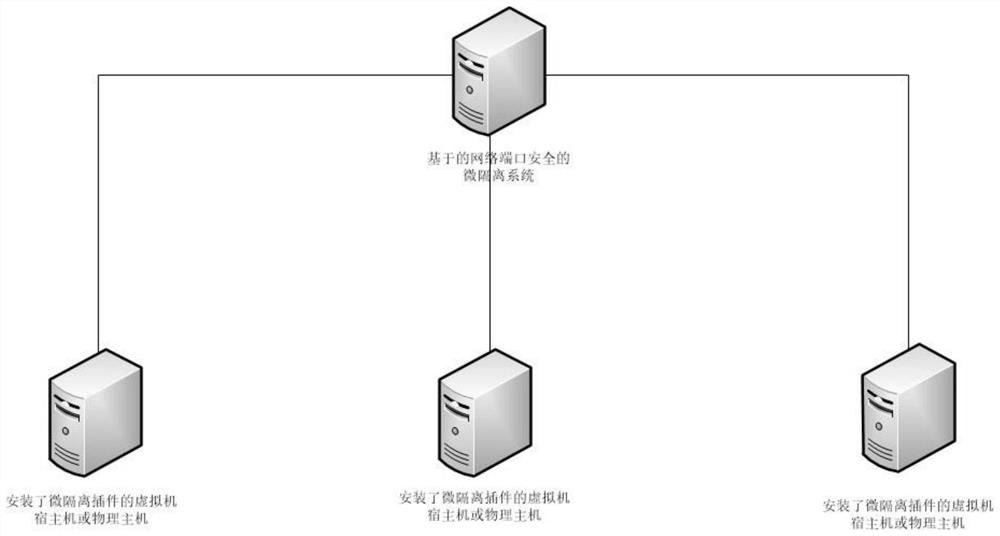
[0041] S1. Through the micro-isolation system, issue isolation instructions to the micro-isolation plug-in of the host (such as image 3 shown);
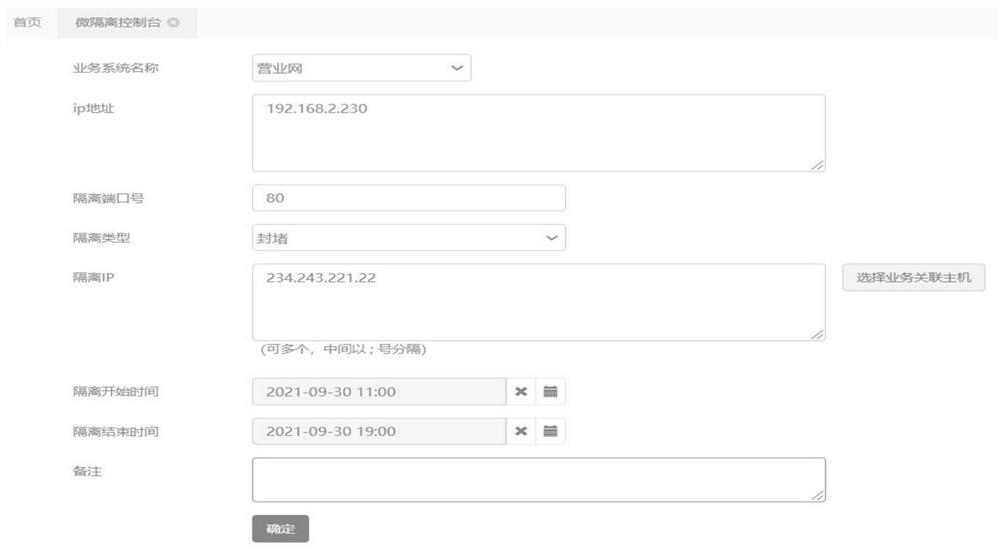
[0042] S2. The micro-isolation plug-in receives the instruction, executes the isolation, and returns the result (such as Figure 4 shown); specifically, through the following steps:
[0043] S21. Install the micro-isolation plug-in on each host computer, and broadcast instructions from the micro-isolation system to all micro-isolation plug-ins;
[0044] S22, the micro-isolation plug-in, compares whether the server IP address in the instruction is consistent with the external IP address of the server local machine and the internal virtual machine, thereby judging whether the isolation instruction should be executed at the local firewall;
[0045] S23. After it is determined that it needs to be executed, execute the isolation instruction;
[0046]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com