Data hijacking judgment method and apparatus, and user terminal
A technology of user terminal and judgment device, applied in electrical components, transmission systems, etc., can solve problems such as affecting user experience, loss of service provider, and user's distrust of service provider.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
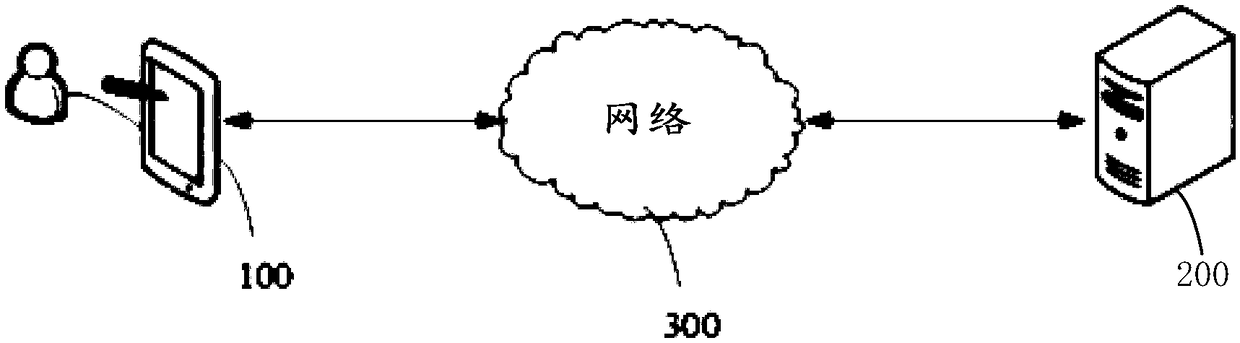
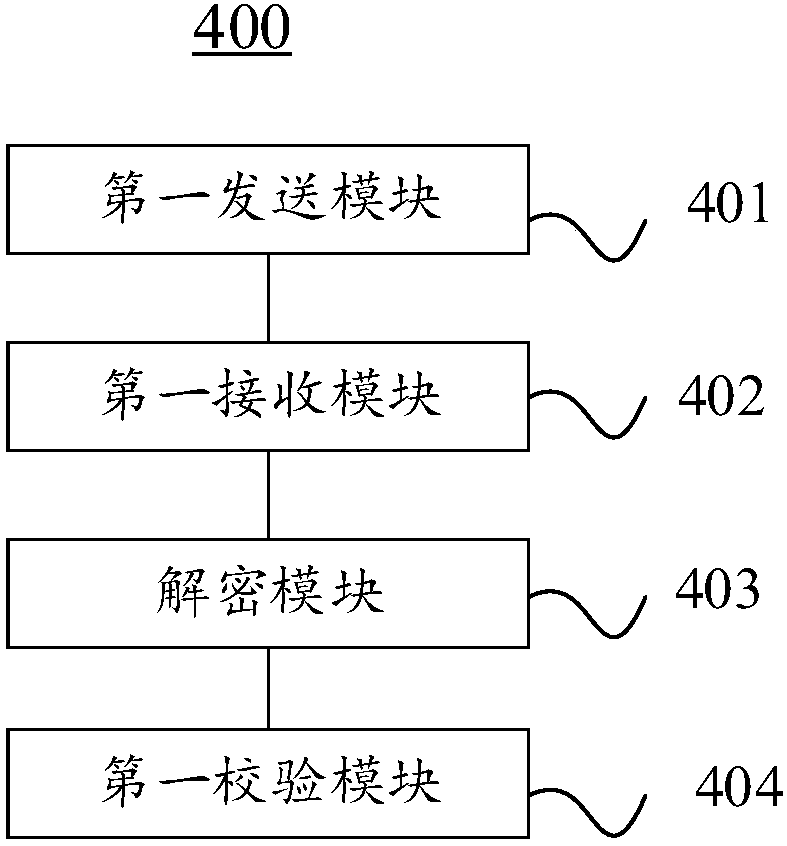
[0037] image 3 A schematic diagram of functional modules of a data hijacking judging apparatus 400 provided in the first embodiment of the present invention is shown. see image 3 , the apparatus 400 for judging data hijacking in this embodiment is applied to the user terminal 100 connected in communication with the server 200 . The data hijacking judging device 400 includes: a first sending module 401 , a first receiving module 402 , a decryption module 403 and a first checking module 404 .
[0038] The first sending module 401 is configured to initiate an http data request to the server 200 .
[0039] HTTP is a widely used network protocol on the Internet. It is a standard protocol for request and response between the user terminal 100 and the server 200 . The user terminal 100 initiates an http data request to the server 200 by using a browser (such as a UC browser), a web crawler, or other tools to obtain data resources (such as HTML files, images, and installer pack...
no. 2 example
[0052] Figure 5 A schematic diagram of functional modules of a data hijacking judging apparatus 500 provided by the second embodiment of the present invention is shown. see Figure 5 , the data hijacking judging apparatus 500 in this embodiment is applied to the server 200 connected to the user terminal 100 in communication. The data hijacking judging device 500 includes: a second receiving module 501 , a generating module 502 , an encryption module 503 and a second sending module 504 .
[0053] The second receiving module 501 is configured to receive an http data request initiated by the user terminal 100 . http is a standard protocol for request and response between the user terminal 100 and the server 200 . The user terminal 100 initiates an http data request to the server 200 by using a browser (such as a UC browser), a web crawler, or other tools, and is used to obtain data resources stored on the server 200 of the response (such as HTML files, images, and installer ...
no. 4 example
[0062] Figure 7 It is a flowchart of a data hijacking judging method provided by the fourth embodiment of the present invention. Please refer to Figure 7 , a method for judging data hijacking, applied to a communication-connected server 200 and a user terminal 100, said method comprising the following steps:
[0063] Step S101 , the user terminal 100 initiates an http data request to the server 200 .
[0064] In this embodiment of the present invention, step S101 may be performed by the first sending module 401 .
[0065] Step S102, the server 200 receives the http data request.
[0066] In this embodiment of the present invention, substep S102 may be performed by the second receiving module 501 .
[0067] Step S103, the server 200 generates http response data according to the http data request.
[0068] In the embodiment of the present invention, step S103 may be executed by the generation module 502 . Such as Figure 8 As shown, step S103 also includes the following...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com