Telecommunication fraud Trojan horse program intercepting method and device, terminal and storage medium
A Trojan horse program and program technology, applied in the field of network security, can solve the problems that the telecommunications fraud Trojan horse program cannot be identified and intercepted in time, and the success rate of telecommunications fraud Trojan horse interception is low, so as to avoid the low interception rate and improve detection and interception rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the purpose, technical solution and advantages of the present application clearer, the implementation manners of the present application will be further described in detail below in conjunction with the accompanying drawings.
[0034] For ease of understanding, the terms involved in the embodiments of the present application are explained below.
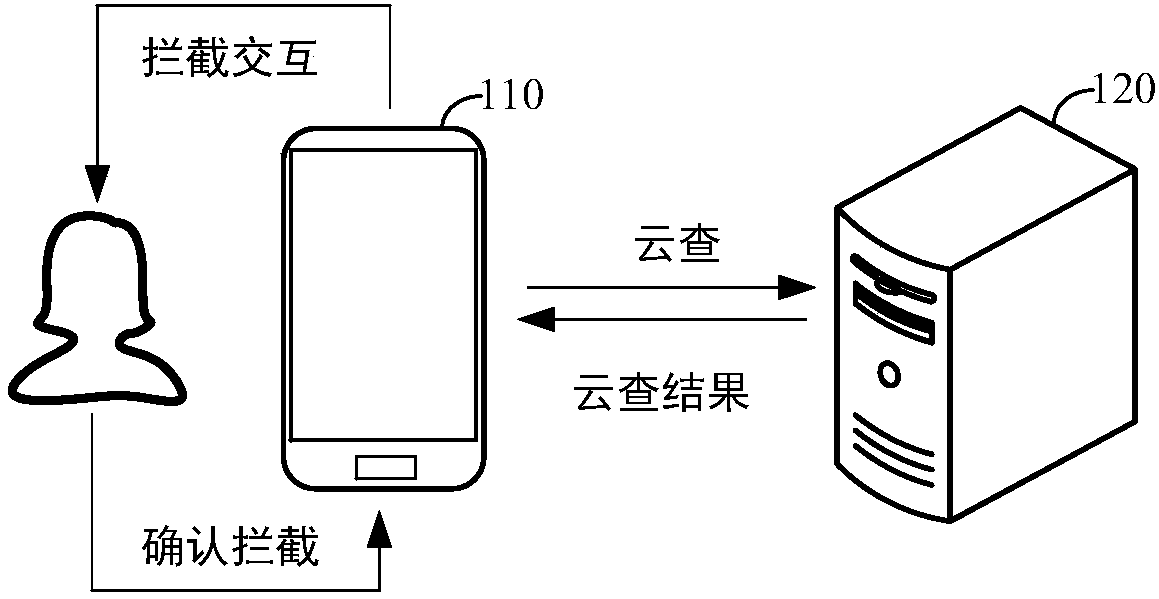
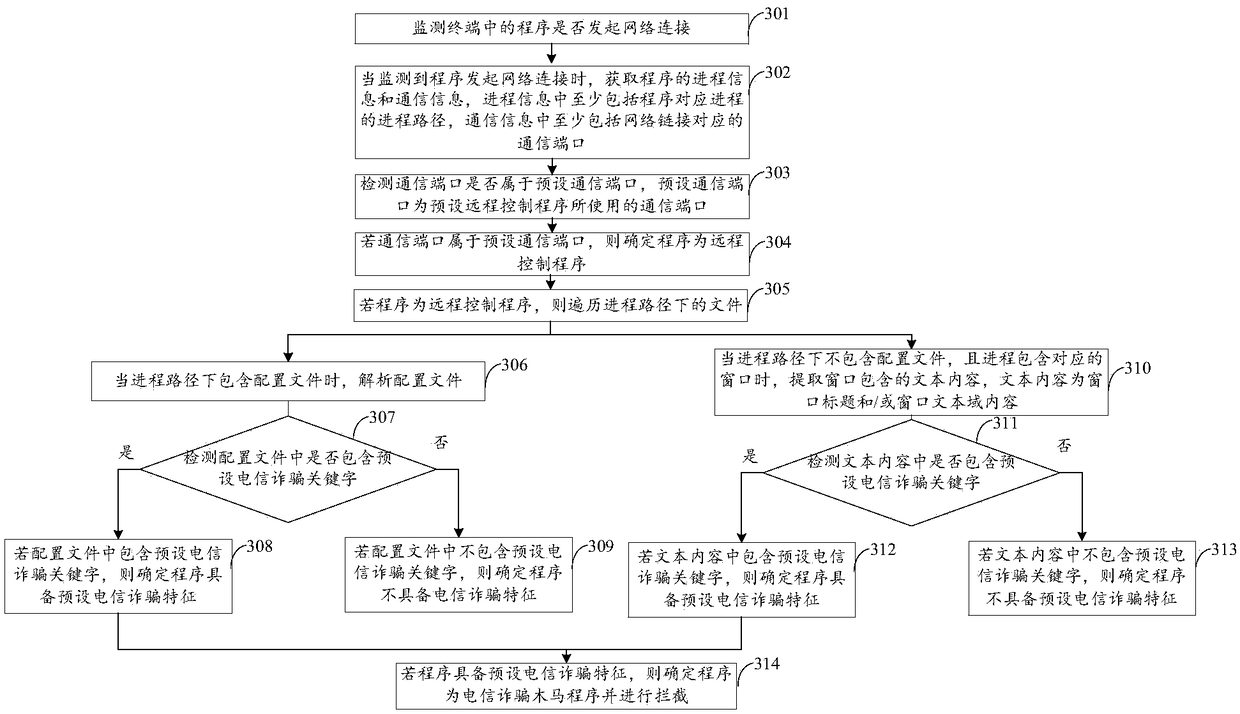
[0035] Remote control: refers to the behavior of using a terminal (such as a personal computer) to control another or multiple terminals to perform operations through the network. Usually, remote control is implemented between terminals through an installed remote control program, and common remote control programs include Teamviewer, LookMyPC, RemoteView, and the like.
[0036] Message Digest Algorithm 5 (MD5): A hash function used in the field of computer security to convert data (or files) into fixed-length strings. Even if very little data in the original data is changed, the MD5 value of the original dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com