Opportunity network routing method based on social utility degree mechanism
A utility and social technology, applied in the field of opportunistic network routing based on social utility mechanism, can solve problems such as large transmission delay, and achieve the effect of reducing delivery delay, reducing control overhead, and good environmental adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
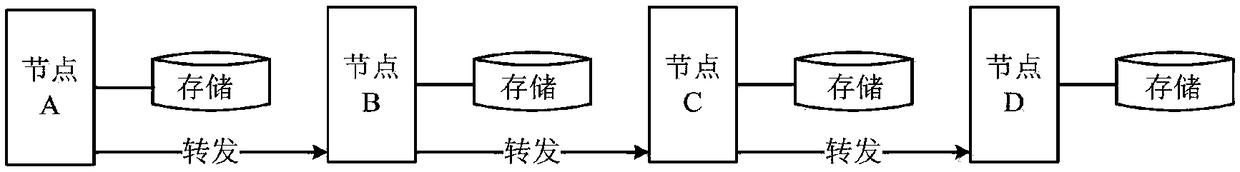
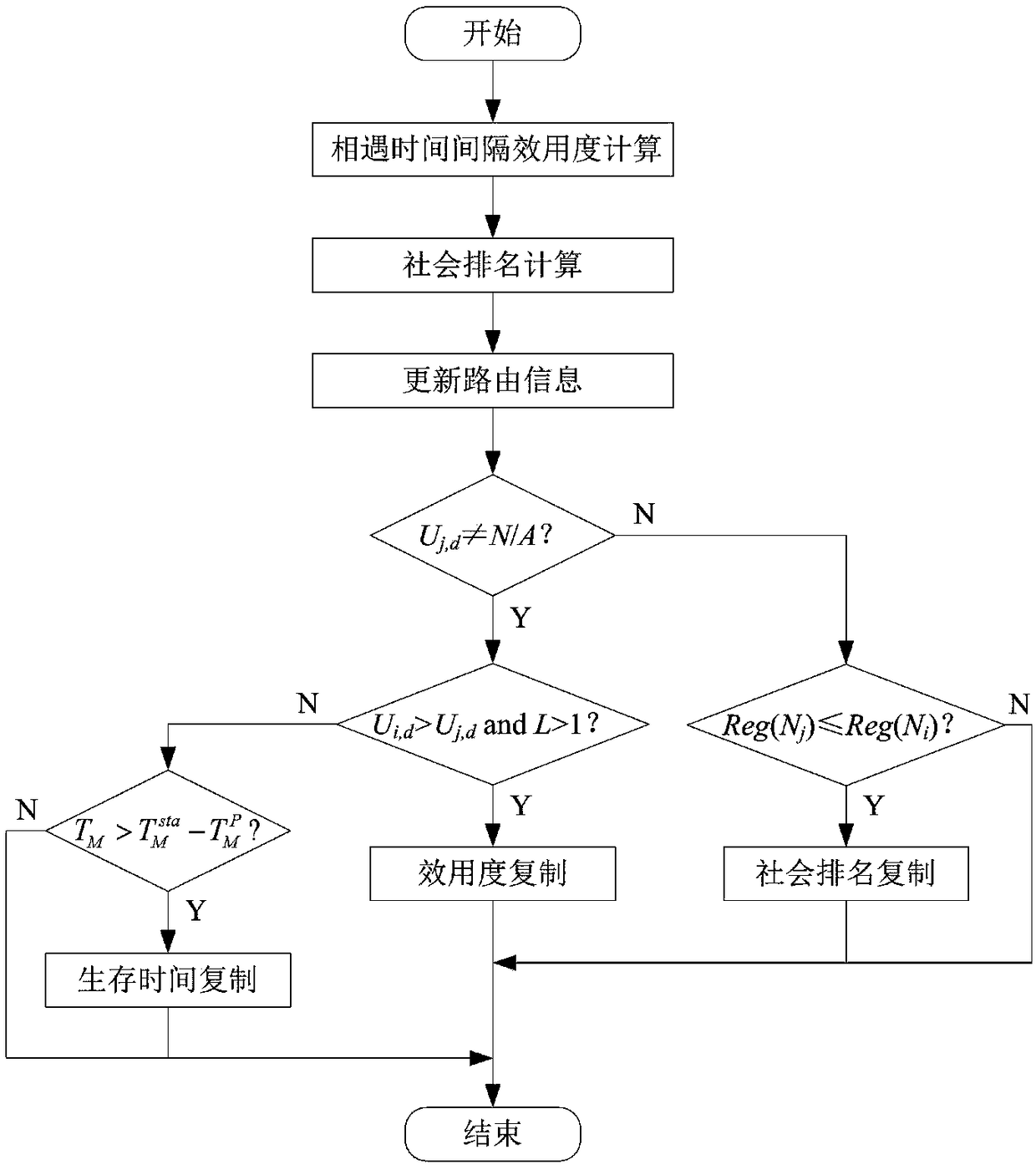
[0026] An opportunistic network routing method based on social utility mechanism. In the opportunistic network routing protocol based on social utility, two nodes predict the next hop of information transmission according to the utility of the time interval between encounters with the message destination node. As a decision basis, the relay node with a higher social ranking is selected as the next hop, and the number of message copies is dynamically allocated according to the social utility of the node, so as to optimize the routing and forwarding process. Specifically, the message delivery process of the routing algorithm based on social utility mainly includes the following implementation steps.
[0027] Step 1: The source node in the network generates an initial copy of the message, and first determines whether the node encountered by the source node is its destination node. If yes, send the message directly to the destination node, and then delete other copies of the messa...
Embodiment approach 2
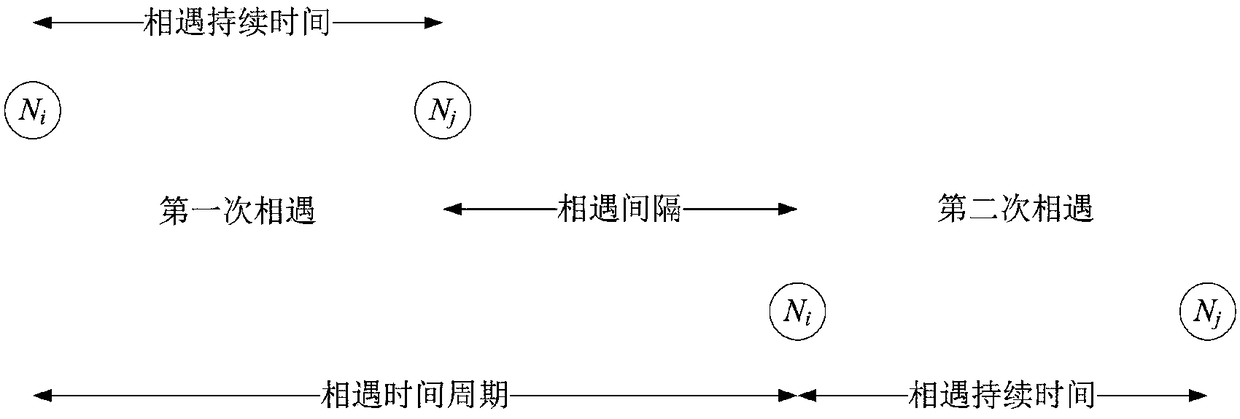
[0047] The difference between the second specific implementation method and the first specific implementation method lies in the calculation of social utility in step 2. Nodes move in the network, and the encounter frequency between nodes obeys a power law distribution. That is, the more social nodes encounter the more nodes and the more frequently they meet, it can be considered that the number of node encounters obeys the Poisson process. We calculate the probability of encounters between nodes according to a Poisson process.
[0048] Poisson process probability that nodes i and j meet
[0049] Assuming that the node carrying the message is i, the destination node is d, and the meeting node is j, then the utility degree between node i and node d is defined as:
[0050]
[0051] The difference between this embodiment and the first embodiment lies in the message management method in step 13 and step 14. The form of a message in the network mainly has three states: gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com