A fine-grained access control method based on cp-abe
A CP-ABE, access control technology, applied in the field of data access control in the cloud environment, can solve the problems of difficult update of access control policies, difficulty of attribute revocation, consumption of large computing and communication resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
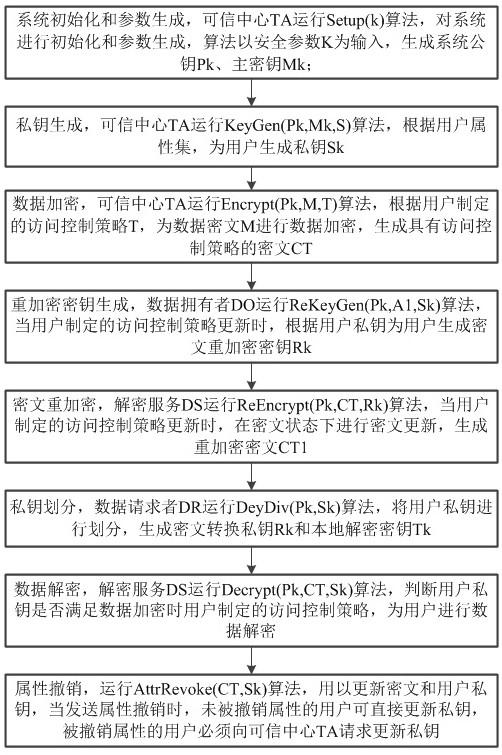
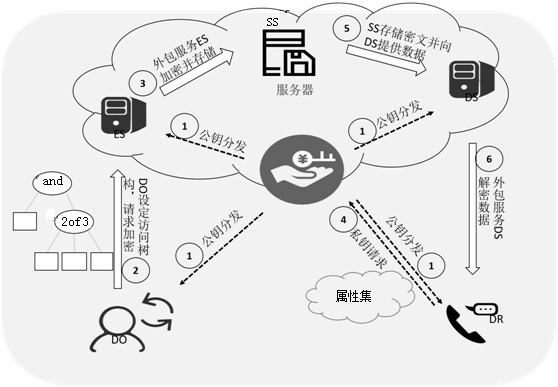
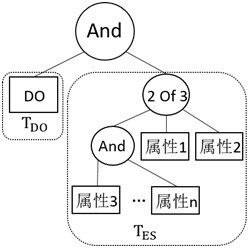
[0107] Such as Figures 1 to 3As shown, a fine-grained access control method based on CP-ABE includes the following steps:
[0108] Step 1: System initialization and parameter generation
[0109] It is mainly to configure the operating environment of the system and generate the key parameters required during the operation of the system, combined with Figure 4 The flow chart of parameter generation, the trusted center TA starts the system, sets and runs the Setup(k) algorithm, and selects the cyclic group where the cyclic group The order of is a prime number P, and the generators are g 1 , g 2 , set the bilinear map e: select The hash function; and the algorithm randomly selects two security parameters α, β∈Z p , output the public key and master key of the system;
[0110] Master key MK=(β,g 1 α ), reserved for TA;
[0111] public key distributed to system participants.
[0112] Step 2: Private key generation
[0113] TA runs the KeyGen (Pk, Mk, A) algorithm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com