Data encryption method, data query method, device, equipment and storage medium
A data encryption and encrypted index technology, applied in the field of data processing, can solve the problems of low data query efficiency and occupy too much system storage space, and achieve the effect of reducing complexity, improving security and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
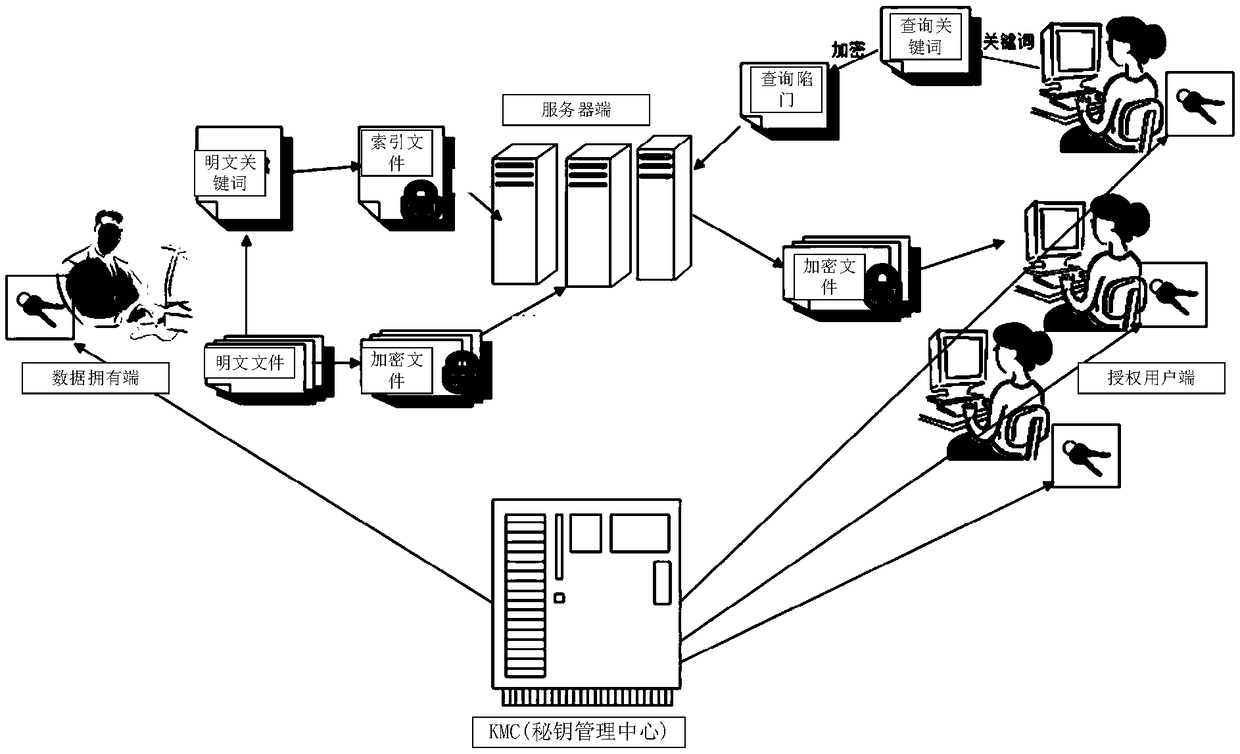
[0050] figure 2 A flow chart of the data encryption method in this embodiment is shown. The data encryption method is applied in various terminals to solve the problem of occupying too much system storage space during the data encryption process. like figure 2 As shown, the data encryption method includes the following steps performed by the data owner:
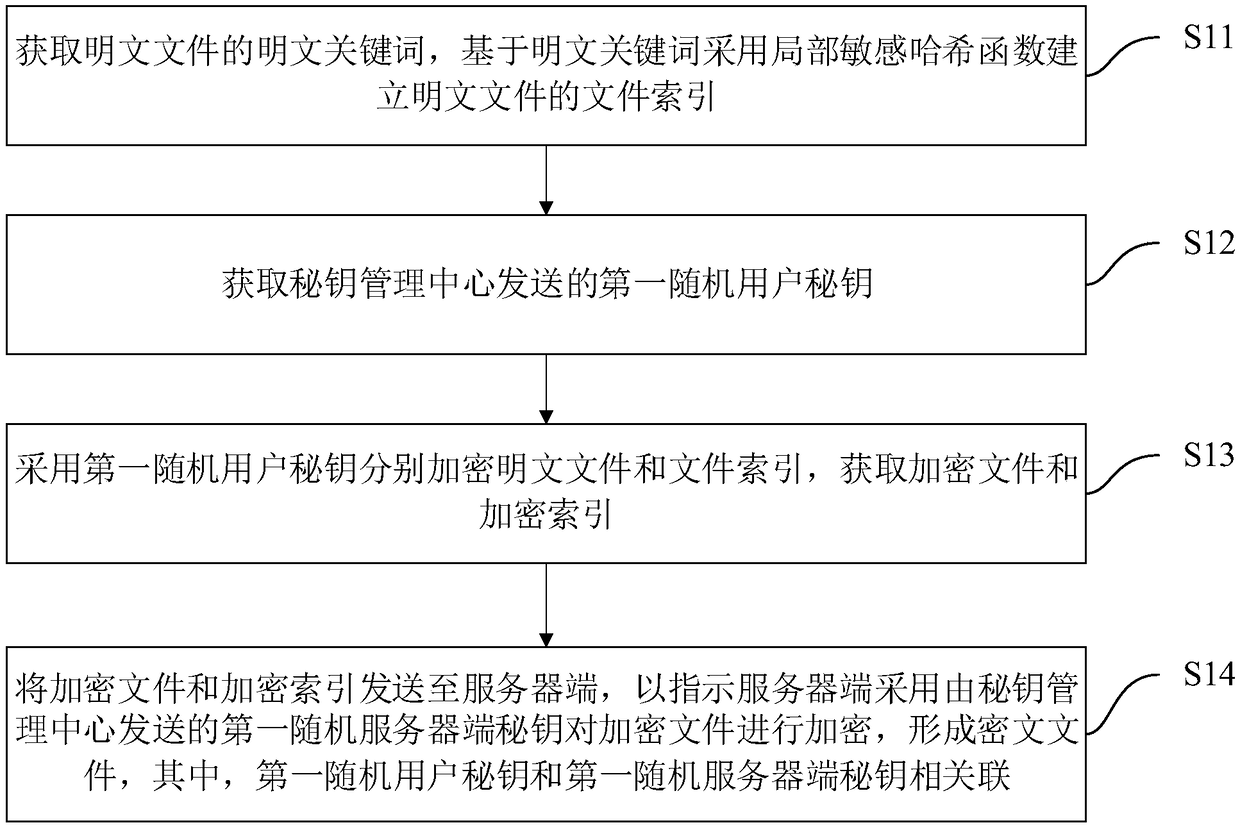
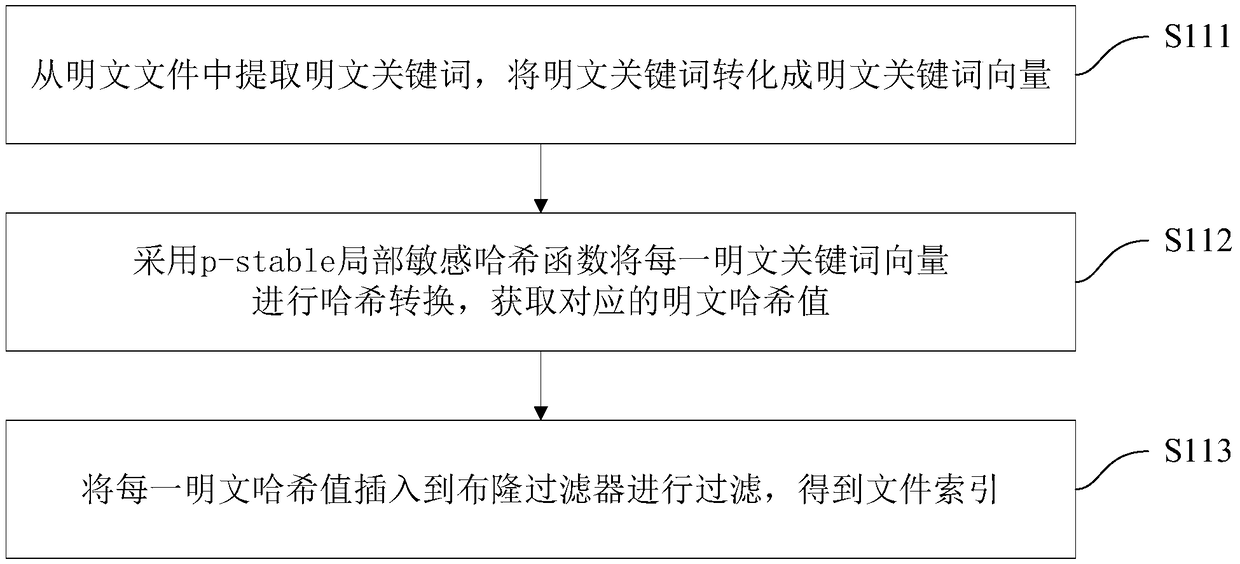
[0051] S11: Obtain the plaintext keywords of the plaintext files, and establish a file index of the plaintext files based on the plaintext keywords using a local sensitive hash function.
[0052] Wherein, the plaintext file refers to an unencrypted original file. Locality Sensitive Hashing (LSH, LocalitySensitive Hashing) function is a kind of Approximate Nearest Neighbor (ANN, Approximate Nearest Neighbor) search, which is used to measure text similarity. The locality-sensitive hash function can mine similar data from massive data, and it can be applied to text similarity detection, web search and other fields.
[005...
Embodiment 2
[0098] Figure 5 A functional block diagram of a data encryption device corresponding to the data encryption method in Embodiment 1 is shown. like figure 2 As shown, the data encryption device includes a file index establishment module 11 , a first random user key acquisition module 12 , an encrypted file and encrypted index acquisition module 13 and an encrypted file and encrypted index sending module 14 . Among them, the implementation functions of the file index establishment module 11, the first random user secret key acquisition module 12, the encrypted file and encrypted index acquisition module 13, and the encrypted file and encrypted index sending module 14 are the same as step 1 of the data encryption method in embodiment 1. One-to-one correspondence, to avoid redundant description, this embodiment does not describe in detail one by one.
[0099] The file index building module 11 is configured to acquire plaintext keywords of plaintext files, and establish fi...
Embodiment 3
[0113] Image 6 A flow chart of the data query method in this embodiment is shown. The data query method is applied to various terminals to solve the problem of low data query efficiency. like Image 6 As shown, the data query method includes the following steps executed by the server:
[0114] S21: Obtain query keywords, and process the query keywords by using a local sensitive hash function to form a query trapdoor.
[0115] Wherein, the query keyword refers to a keyword used to query the plaintext file. The query keywords are sent from the authorized client to the server. The server side obtains the query key words from the authorized user side, and processes the query key words with a local sensitive hash function to form a query trapdoor. Among them, a trapdoor is an "organ" set in a certain system or a certain file, so that when specific input data is provided, the security policy is allowed to be violated. For example, a login processing subsystem allows p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com