An Information Hiding Method Based on Encryption and Natural Language Generation
A technology of natural language and information hiding, which is applied in the field of cryptography and information hiding, can solve the problems that encrypted text does not conform to natural language grammar and has no semantics, and achieve the effect of ensuring safe sharing, improving similarity, and improving embedding rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
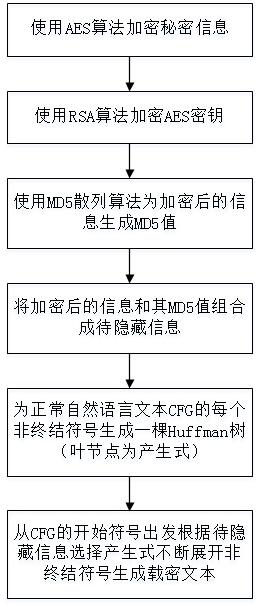
[0037] Embodiment 1 of the present invention introduces the specific process of using several cryptographic techniques to encrypt secret information and adding verification information, and finally obtain the information to be hidden in binary form. Specific steps include:
[0038] S1: Encode the secret information S into a binary stream S' according to a specific encoding method; for example, S in English text form can be encoded into binary form through ASCII encoding method, and S in Chinese text form can be encoded into binary form through Chinese character encoding method etc;
[0039] S2: Select an AES initial key K with a length of 128 bits, and then use the AES key expansion algorithm to expand K to generate the expanded key K' used for encryption; use the expanded key K' to process the binary stream S in step S1 'Carry out multiple rounds of AES encryption to obtain the encrypted binary stream E(S');
[0040] S3: Use the RSA key generation algorithm to generate a pa...
Embodiment 2
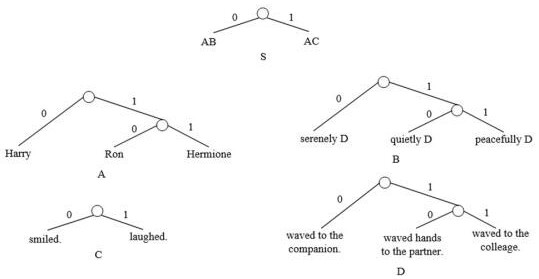
[0045] Embodiment 2 of the present invention introduces the specific process of generating encrypted text according to a piece of binary secret information and context-free grammar (CFG) of normal text. Assuming that the binary secret information to be hidden is 0101101, the CFG of a normal text is as follows figure 2 , where the number in parentheses after each production is the probability of the production appearing in normal text. Specific steps include:
[0046] S1: According to the probability of each production of each non-terminal symbol of CFG, use the Huffman compression coding algorithm to generate a Huffman binary tree for each non-terminal symbol of CFG, and each production of each non-terminal symbol is this non-terminal A leaf node of the Huffman tree of terminal symbols; if all the left branch paths of this binary tree are marked with 0, and all the right branch paths of this binary tree are marked with 1, then each production corresponds to a binary code, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com