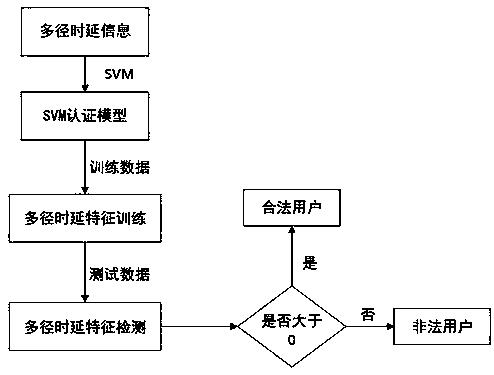
Wireless communication physical layer authentication method
A technology of wireless communication and authentication method, applied in the field of wireless transmission, can solve the problems of large influence of transmission signal, complicated calculation, and insufficient use of wireless channel characteristics, etc., to achieve the effect of improving authentication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Objects, advantages and features of the present invention will be illustrated and explained by the following non-limiting description of preferred embodiments. These embodiments are only typical examples of applying the technical solutions of the present invention, and all technical solutions formed by adopting equivalent replacements or equivalent transformations fall within the protection scope of the present invention.
[0027] When doing the performance simulation of the identity authentication mechanism, the authentication performance that the mechanism proposed in the present invention can achieve under different SNRs is mainly considered. The accuracy of identity authentication is mainly represented by error rate, which cannot be proved in theory, but can only be statistically estimated through a large number of identity authentication test data. Taking an OFDM (Orthogonal Frequency Division Multiplexing) system with single transmission and single reception as an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com