Multi-ring protection configuration method and system of PTN ring network protection
A configuration method and technology of a configuration system, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as increasing the complexity of configuration planning in the early stage and problem location in the later stage, and affecting the large-scale deployment of ring networks, so as to achieve enhanced ease of use. operational effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
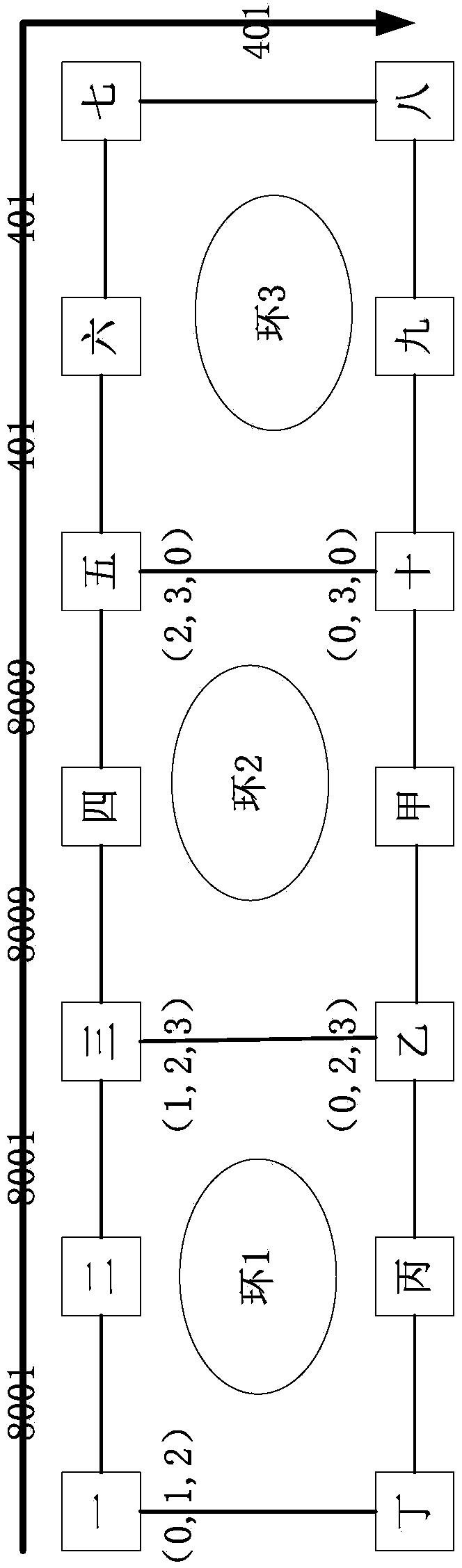
[0053] The LSP path may pass through multiple MPLS-TP shared rings. According to the characteristics of the service path, the LSP is bound to each ring network segment by segment, which can realize the segment-by-segment protection of the LSP path. In order to realize the multi-point fiber cut protection function to the greatest extent, the rings that physically intersect each other can be associated. The rings that may be associated with the same ring include its upstream ring and downstream ring. The embodiment of the present invention mentioned in the draft On the basis of double-ring protection, a multi-ring protection configuration method for PTN ring network protection is provided, including the following steps:
[0054] For each ring of the intersecting ring relationship, add the intersecting ring configuration with corresponding entries. This configuration is a sub-configuration of the overall configuration of the ring. Each configuration includes: intersecting ring KEY...
Embodiment 2
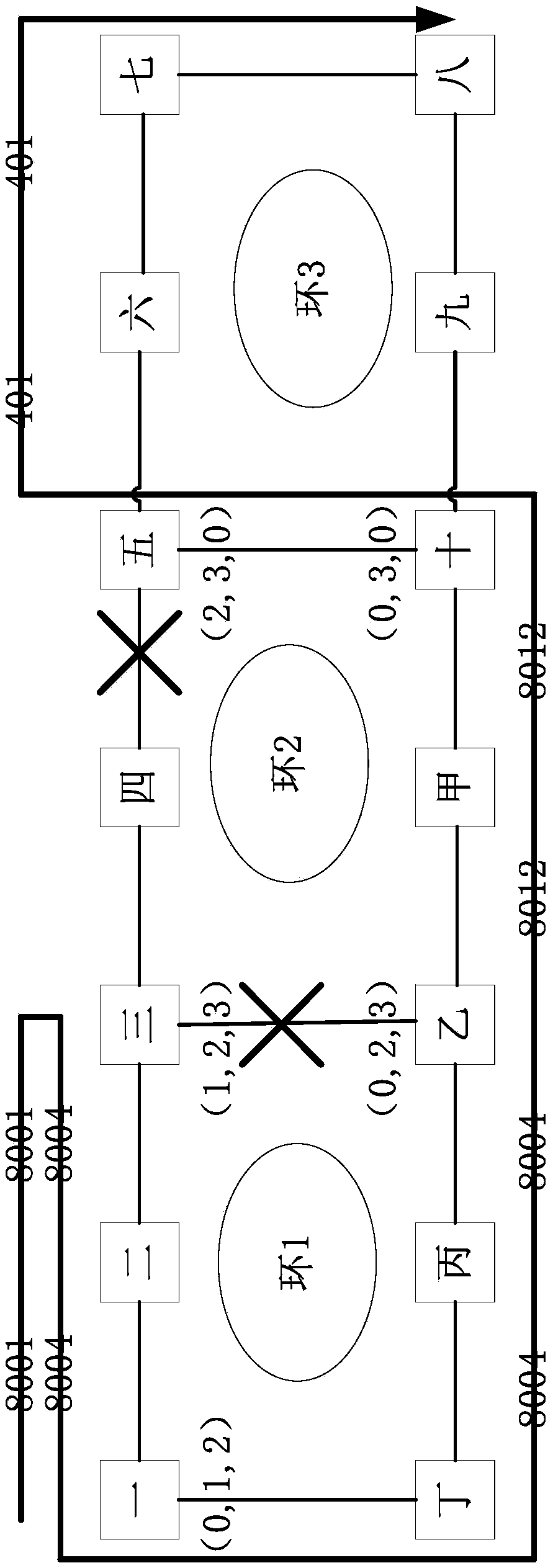
[0057] On the basis of Embodiment 1, after the LSP binds more than three rings, the following steps are also included:
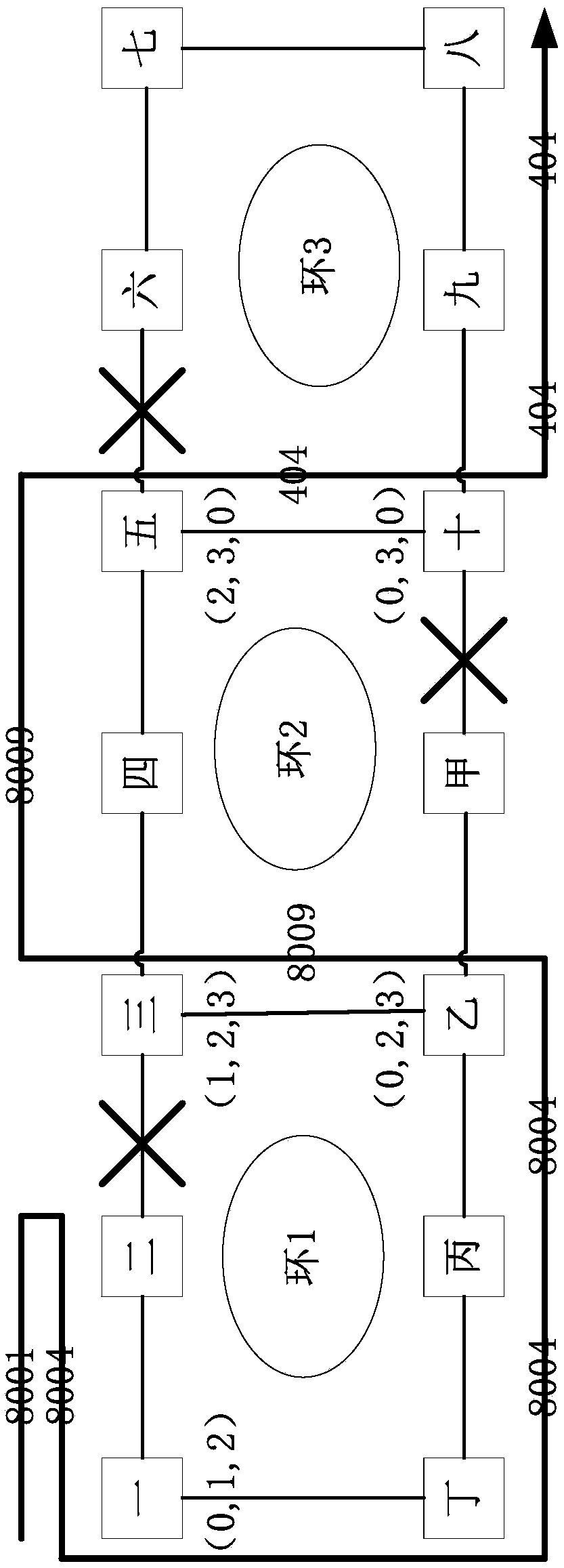
[0058] Perform protection switching on the nodes in the ring. The specific process is as follows:
[0059] At the uplink node of the uplink ring, the LSP enters the uplink at this node, and labels the intersecting ring label corresponding to the "uplink" with the current ring. The switching object is the intersecting ring label group. The switching principle is the single Ring switching principle;
[0060] At the uplink node of the local ring, the LSP pops up the intersecting ring label corresponding to the uplink ring and the local ring at the local node, and after the LSP label exchange, puts the intersecting ring label corresponding to the local ring and the downlink ring; the switching principle is single-ring switching Combination with intersecting ring switching;
[0061] The uplink ring and another intersecting node of the local ring, which is symme...
Embodiment 3
[0066] On the basis of embodiment 2, among the three bound ring KEY values, the local ring KEY value of the LSP with the bound ring relationship is not 0, and the KEY value of the uplink ring and the KEY value of the downlink ring are zero or non-zero according to the actual situation .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com