Multi-dimensional and multi-granularity network space security measurement method
A network space and security measurement technology, applied to electrical components, transmission systems, etc., can solve the problems of not specifying the starting point and the end point of the attack, many attack paths, and a large amount of calculation, so as to achieve the real and objective measurement of the vulnerability dimension. The effect of improving accuracy and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in detail below with reference to the accompanying drawings and examples.
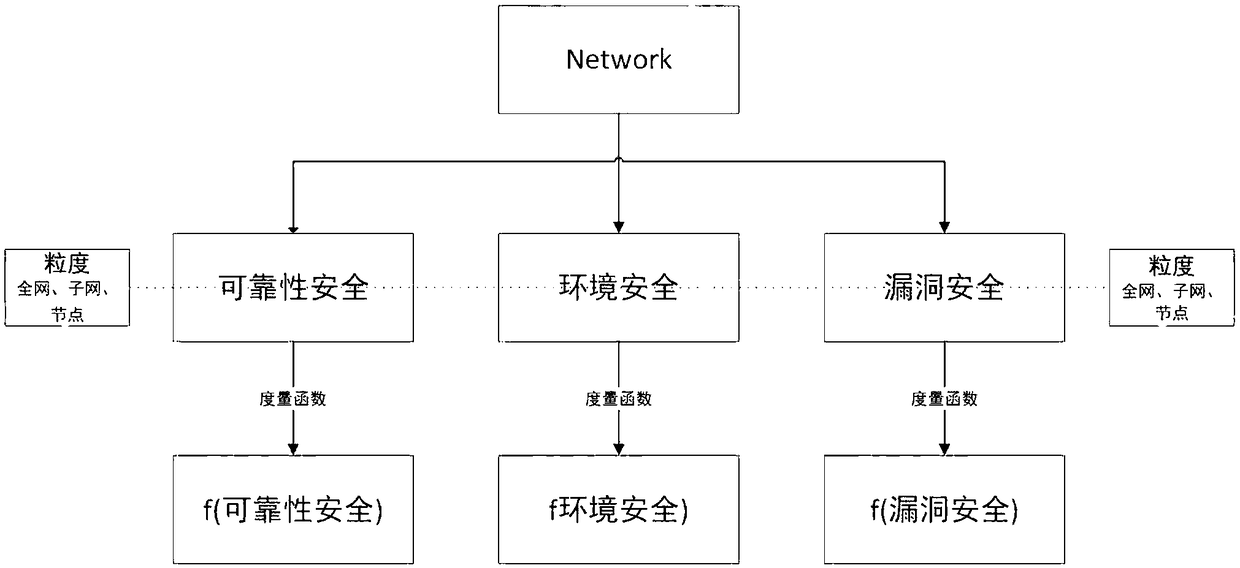
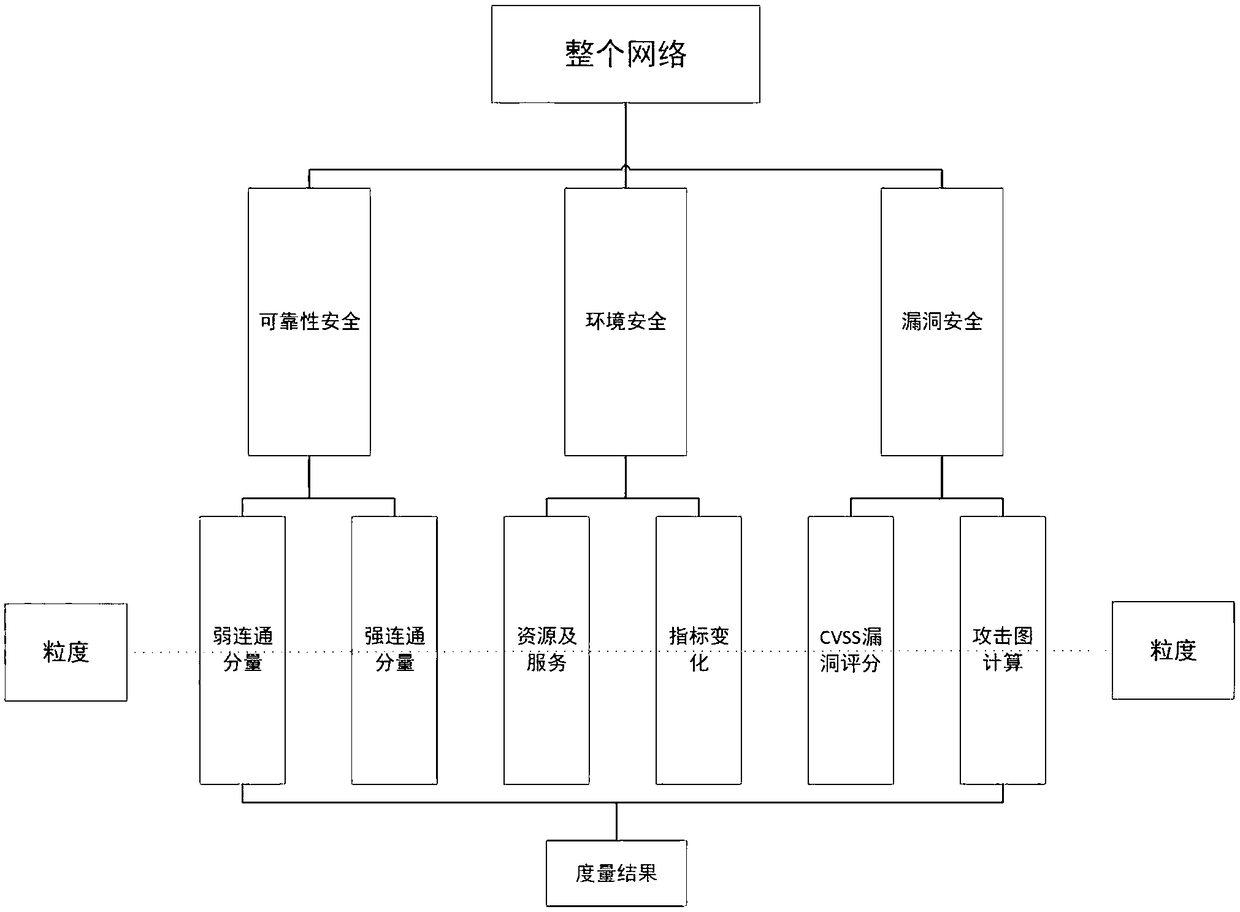
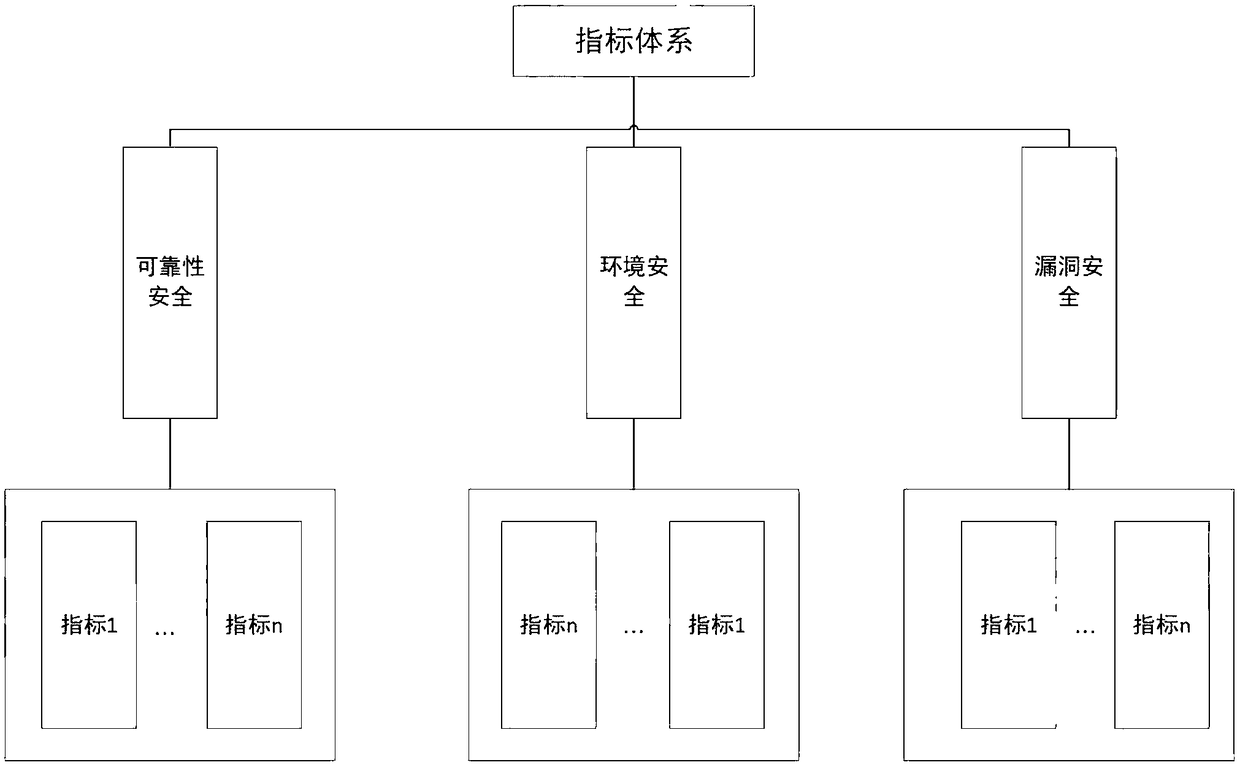
[0035] In order to obtain more accurate and comprehensive measurement and evaluation of network space security, the present invention firstly divides the network system into three levels according to the logical layering, which are respectively reliability security, environmental security, and loophole security, that is, Network={(reliability security , environment security, vulnerability security)|granularity}( figure 1 ).
[0036] These three levels are considered from the hardware environment, software resources and loopholes on which the network depends. Reliability and security start from the network connection relationship, only considering the network topology, regardless of the services and assets owned by each node. Therefore, this layer considers the connectivity and connectivity efficiency of all nodes, that is, measures the weakly connected a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com