Configuration item type constraint inference method based on name semantics
A technology of configuration items and types, applied in software maintenance/management, reverse engineering, etc., to achieve the effect of reducing the difficulty of extraction, good application scenarios, and avoiding complex program analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
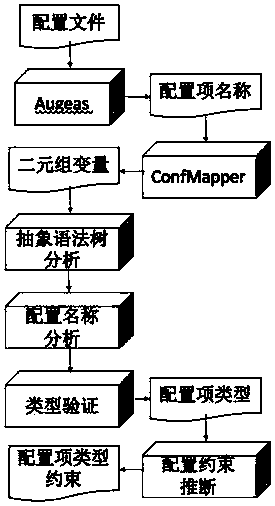
[0049] The key to the embodiment of the present invention is how to use the semantics of the configuration name to infer the configuration type, and how to define the configuration constraints through the configuration type. The following describes typical implementation methods for these two aspects.
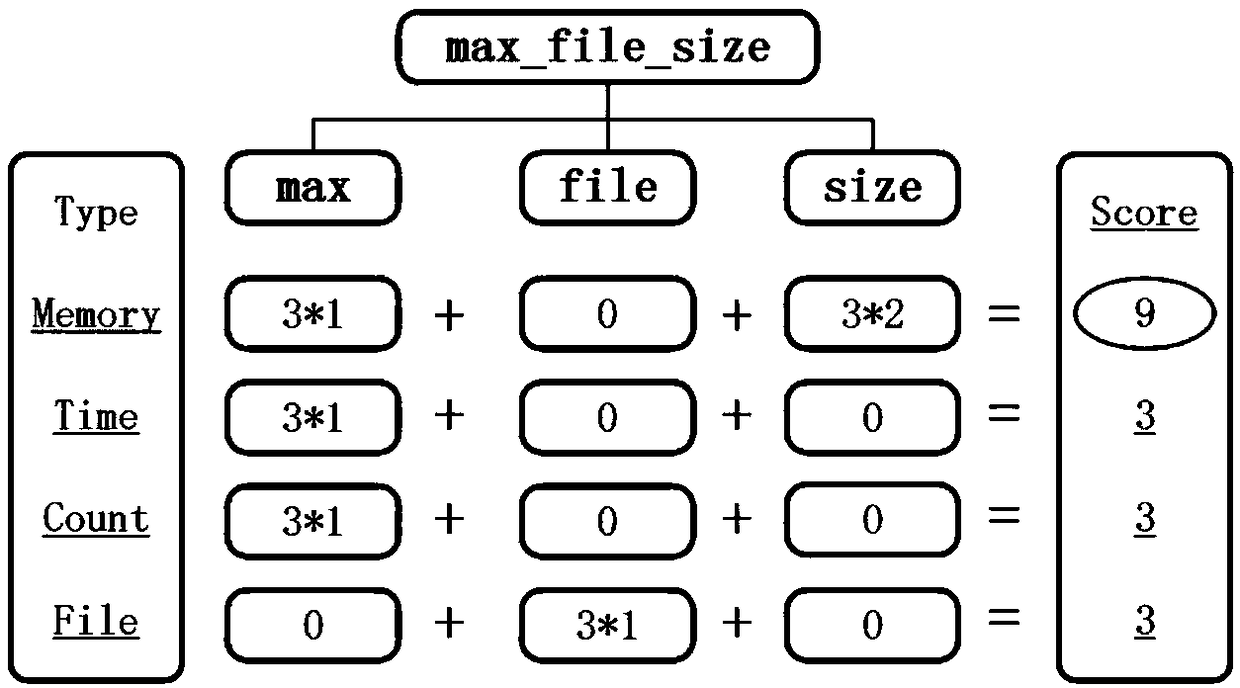
[0050] The first step is configuration type inference based on name semantics. The types corresponding to the configuration items are inferred mainly through name semantic analysis (take the configuration item "max_file_size" as an example).
[0051] (1.1) Firstly, the configuration item type is inferred through the name semantic information. Specific process such as figure 1 Shown:
[0052] (1.1.1) First, word segmentation is performed on the name of the configuration item "max_file_size". Mainly use the camel case naming method often use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com