Method for suppressing malicious NA messages in DAD process suitable for SEND protocol
A message and protocol technology, applied in the computer field, can solve problems such as malicious node theft, and achieve the effect of avoiding consumption and avoiding host CPU resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
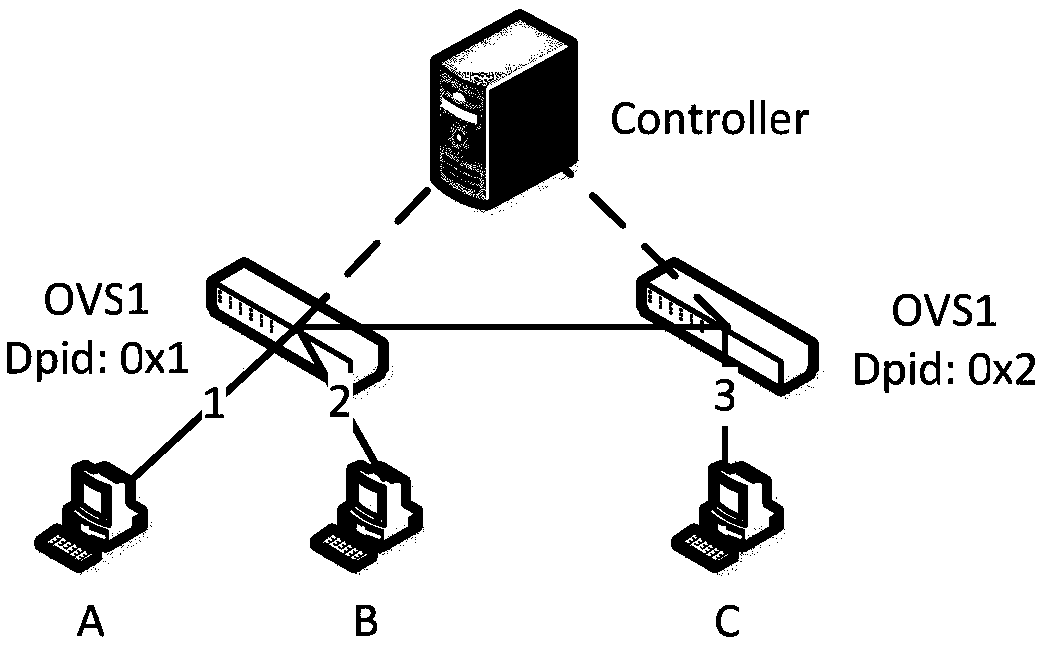
[0103] Assuming that the SDN network consists of 1 controller, 2 Openflow switches and 3 hosts, and has been running for a period of time (more than 3 minutes), its topology diagram refers to figure 2 , the configuration of each host is shown in Table 7.
[0104] Table 7
[0105]
[0106] First, the controller issues a flow table to monitor the DAD packets in the network. The flow table is shown in Table 8.
[0107] Table 8
[0108]
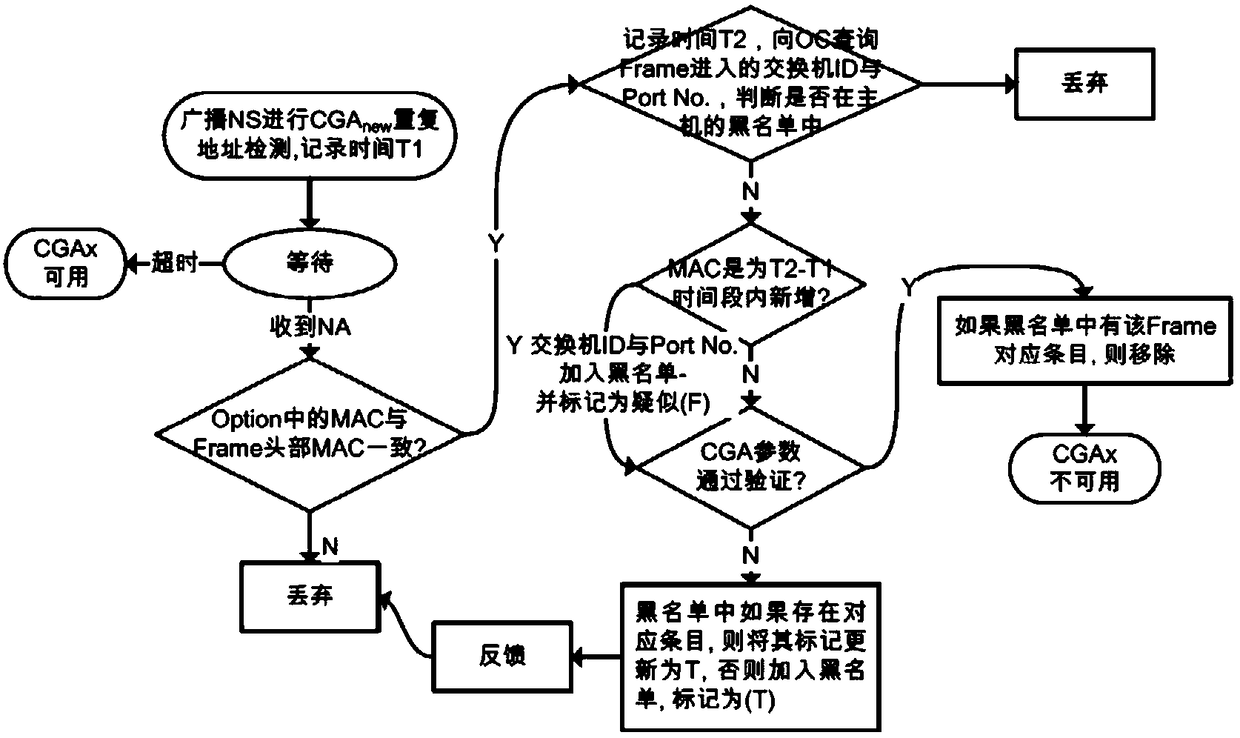
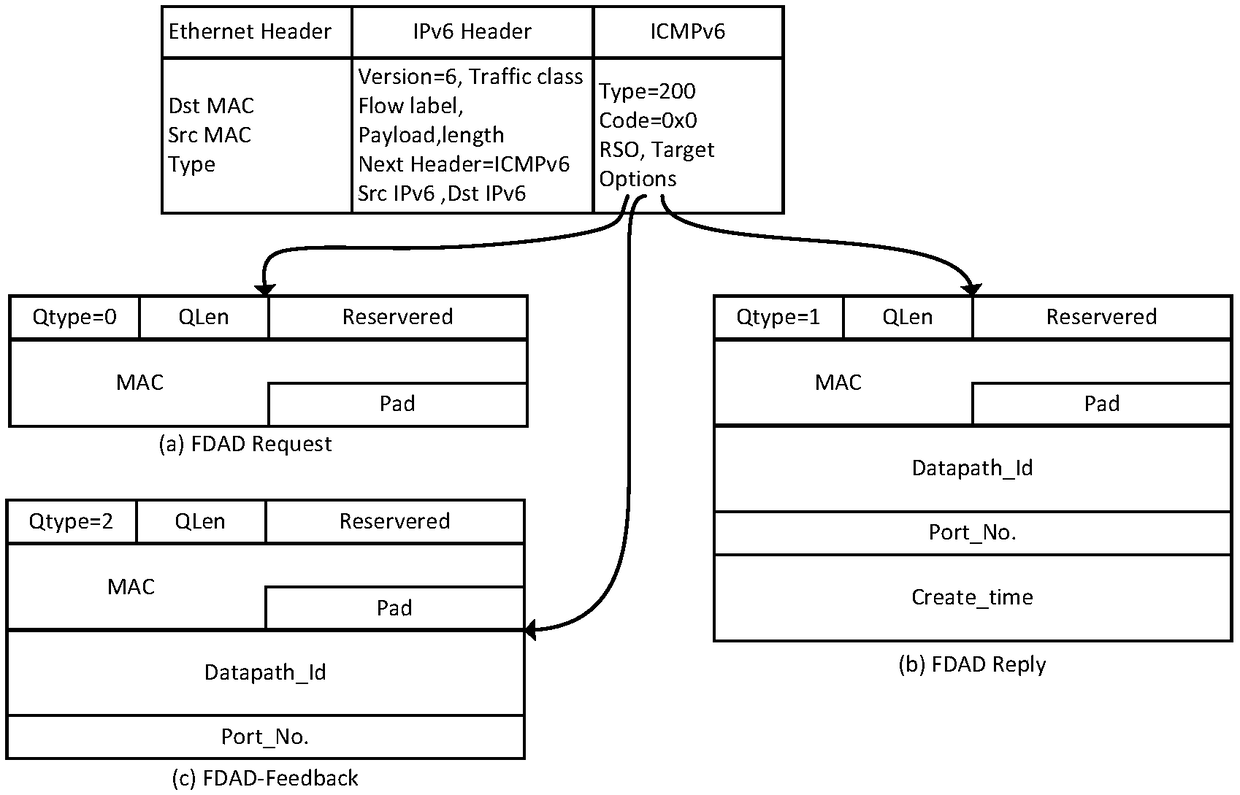
[0109] Assuming that host A generates a new link-local address CGAnew by using the CGA address configuration method (for the sake of demonstration, assume that the last 32 bits of CGANEW are cc00-aabb), then send NS to detect duplicate addresses. The format of NS is shown in Table 9 . After receiving the NS, OVS1 sends the Packet_In message to the controller according to the requirements of the flow table, and the controller generates a new entry in the monitoring table according to the Packet_In message and the NS message carried by th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com