Strong identity authentication system and strong identity authentication method based on PAM architecture
A technology of identity authentication and authentication module, which is applied in the field of linux identity authentication and information transmission security, can solve problems such as easy guessing and low security, and achieve the effects of reducing development workload, high security, and preventing user information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
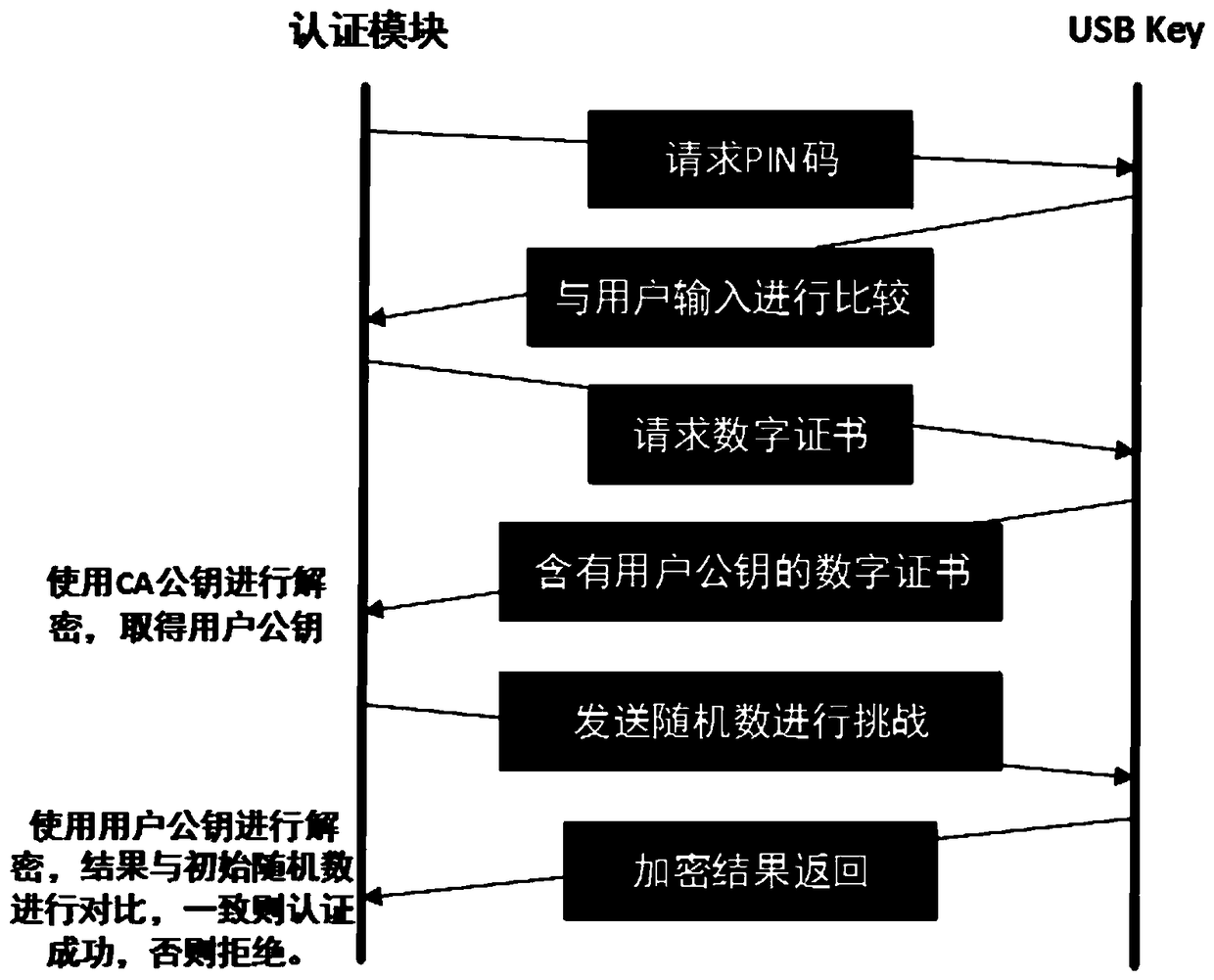
[0024] Embodiment 1: The strong identity authentication method based on the PAM framework uses the Linux-PAM framework, the USBKey authentication method based on digital certificates, and the remote login uses the SSH (Secure Shell) security protocol. In order to enable the system to use USB Key for identity authentication, it is necessary to write a PAM authentication module to complete identity authentication based on USB Key.
[0025] There is a certain safe data storage space in the USB Key, which is used to store secret data such as digital certificates and user secret keys. The read and write operations of this storage space must be realized through specific programs, and users cannot directly read them. The built-in CPU of the USB Key can realize various algorithm operations of data summary, data encryption and decryption and signature used in the PKI system, and the encryption and decryption operations are carried out in the USB Key.
[0026] The PAM authentication mod...
Embodiment 2
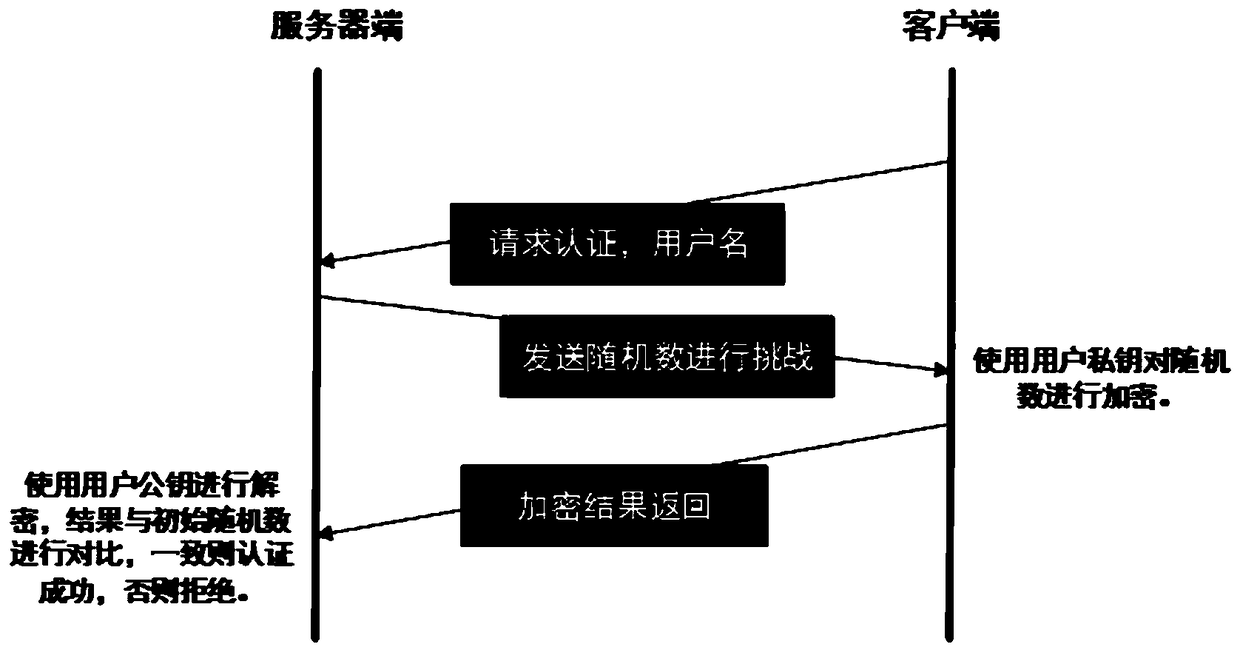
[0040] Embodiment 2: A strong identity authentication system based on the PAM architecture, including a PAM authentication module and a USB Key authentication method. The USB Key authentication is to store the required digital certificate for login and its corresponding private key in the USB Key. You must have a USB Key and PIN code to log in. At the same time, the digital certificate and private key in the USB Key are issued by the CA Certificate Authority (Certificate Authority), which achieves the purpose of unified management. Specifically, it includes an authentication module, an account management module, a session management module, and a password management module. The authentication module is used to authenticate users or set / destroy credentials. The account management module will perform operations related to access, account and credential expiration, password restrictions / rules, etc. The session management module is used to initialize and terminate sessions. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com