A collaborative signature method and system for communication parties based on sm2 algorithm
A technology for communication parties and both parties, applied in the fields of information security and cryptography applications, can solve the problems of low latency, large amount of communication data, and complex computing process, and achieve low latency, small amount of communication data, and low complexity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
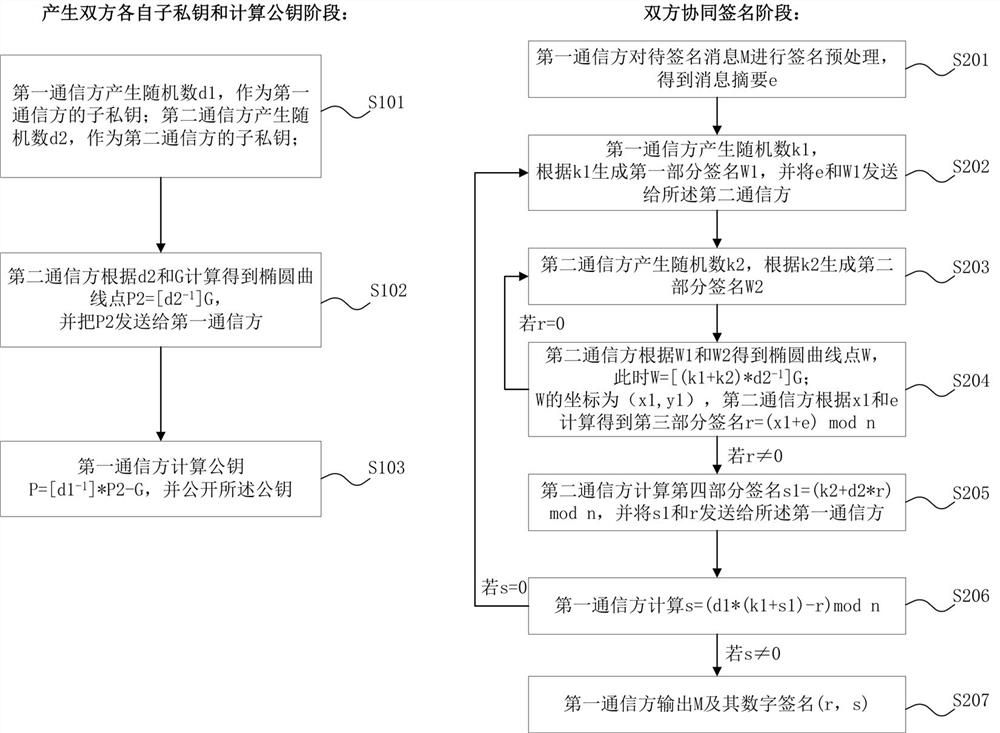
[0058] Such as figure 1 As shown, a cooperative signature method of both communication parties based on the SM2 algorithm, the method involves the first communication party and the second communication party, and the first communication party and the second communication party share the SM2 algorithm elliptic curve E and E The base point G whose upper order is n; the method comprises the following steps:
[0059] 1. The stage of generating the respective sub-private keys of both parties and calculating the public key
[0060] S101. The first communication party generates a random number d1∈[1,n-1] as the sub-private key of the first communication party; the second communication party generates a random number d2∈[1,n-1] ], as the sub-private key of the second communicating party;
[0061] S102. The second communication party calculates and obtains the elliptic curve point P2=[d2 according to d2 and G -1 ]G, and send P2 to the first communication party, where d2 -1 Represen...
Embodiment 2
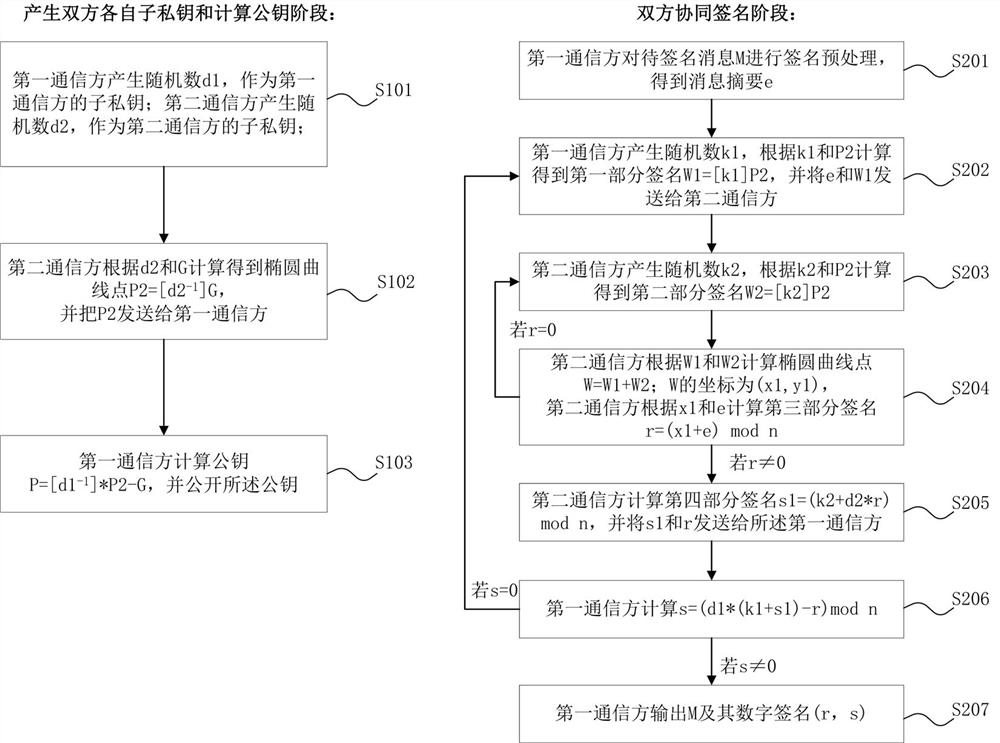
[0085] Based on the same inventive concept as the above-mentioned method, as figure 2As shown, this embodiment is a preferred specific implementation of the collaborative signature method, and the difference from Embodiment 1 is that steps S202, S203, and S204 are respectively:
[0086] S202. The first communication party generates a random number k1∈[1,n-1], calculates the first part signature W1=[k1]P2 according to k1 and P2, and signs the message digest e and the first part W1 is sent to the second communication party;
[0087] S203. The second communication party generates a random number k2∈[1,n-1], and calculates the second part signature W2=[k2]P2 according to k2 and P2;
[0088] S204. The second communication party calculates the elliptic curve point W=W1+W2 according to the first partial signature W1 and the second partial signature W2, and the coordinates of W are (x1, y1); then according to x1 and the The message digest e is calculated to obtain the third part of...
Embodiment 3
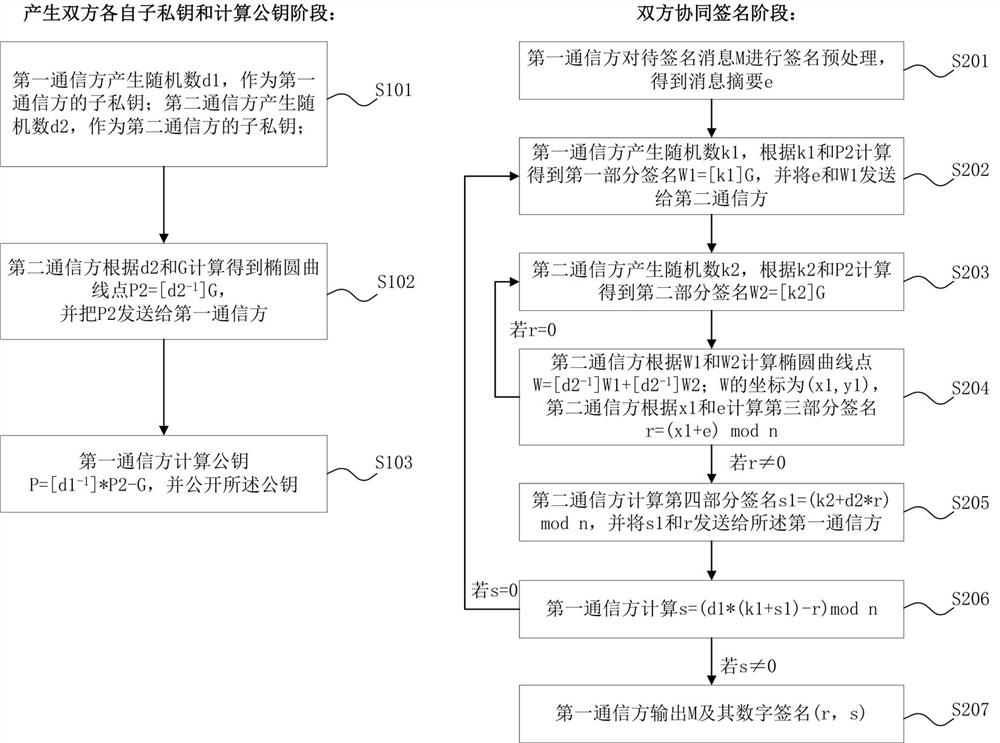
[0099] Based on the same inventive concept as the above-mentioned method, as image 3 As shown, this embodiment is another preferred specific implementation of the cooperative signature method, and the difference from Embodiment 1 is that steps S202, S203, and S204 are respectively:
[0100] S202. The first communication party generates a random number k1∈[1,n-1], calculates the first partial signature W1=[k1]G according to k1 and G, and sends e and W1 to the second communication party ;
[0101] S203. The second communication party generates a random number k2∈[1,n-1], and calculates the second part signature W2=[k2]G according to k2 and G;
[0102] S204. The second communication party calculates the elliptic curve point W=[d2 according to the first partial signature W1 and the second partial signature W2 -1 ]W1+[d2 -1 ] W2, the coordinates of W are (x1, y1); then calculate the third part of the signature r=(x1+e)mod n according to x1 and e, if r=0, return to S203.
[010...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com