CA authentication method and device based on block chain and electronic device
A CA certification, blockchain technology, applied in the field of information security, can solve user information security threats, electronic information storage and management security issues, digital certificate information security risks, etc., to reduce security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
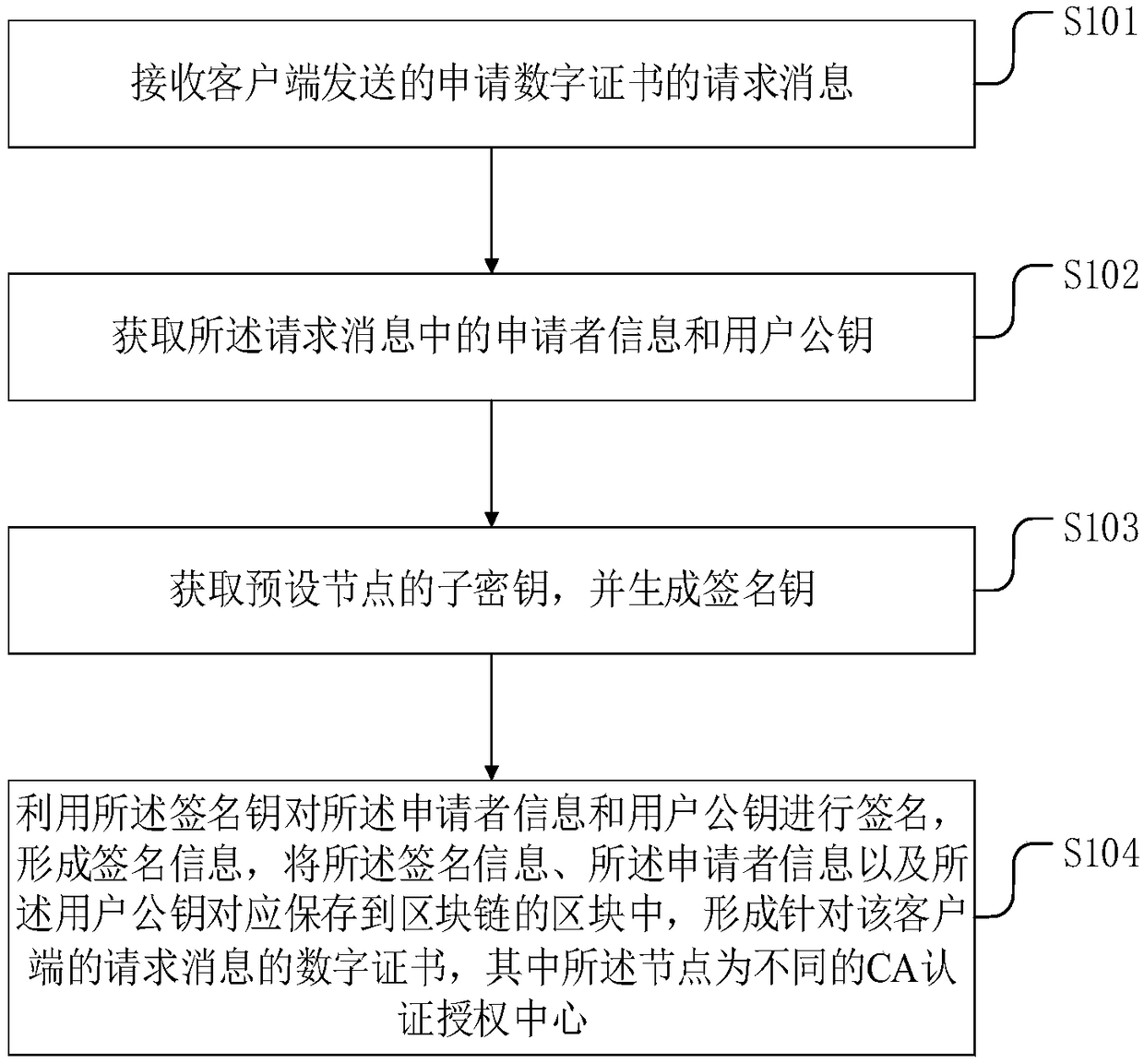
[0056] A blockchain-based CA authentication method provided in Embodiment 1 of this application, such as figure 1 shown, including:
[0057] S101: Receive a request message for applying for a digital certificate sent by a client.
[0058] Here, request messages for applying for different types of digital certificates sent by the client may be received. Based on the application angle classification of digital certificates, the types of digital certificates can be classified into server certificates, email certificates and personal certificates.
[0059] S102: Obtain the applicant information and user public key in the request message.
[0060] If the digital certificate applied by the client is a server certificate, the applicant information may include a website domain name; if the digital certificate applied by the client is an email certificate, the applicant information may include an email address; if the The digital certificate applied by the client is a personal certi...
Embodiment 2
[0078] The process of validating digital certificates in a blockchain-based CA authentication method provided by the present application will be described below through Embodiment 2.
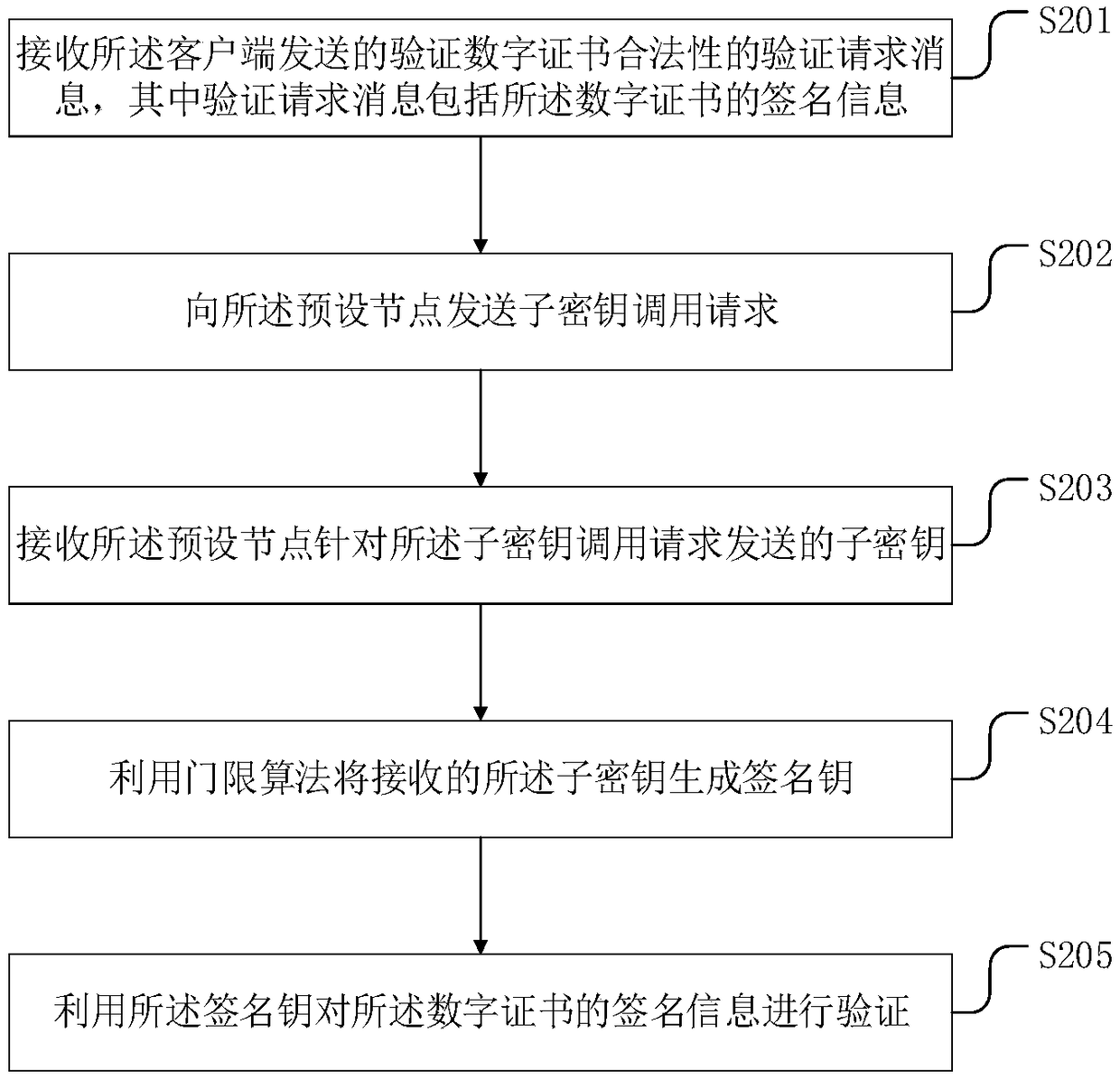
[0079] A blockchain-based CA authentication method provided in Embodiment 2 of the present application, such as figure 2 shown, including:
[0080] S201: Receive a verification request message sent by the client to verify the legality of the digital certificate, where the verification request message includes signature information of the digital certificate.
[0081] In specific implementation, verifying the legitimacy of the digital certificate means verifying the legitimacy of the signature information of the digital certificate, where it is necessary to verify the signature information of the digital certificate using the signature key used when forming the signature information of the digital certificate .
[0082] S202: Send a subkey invocation request to the preset node.
[0083] In a ...
Embodiment 3
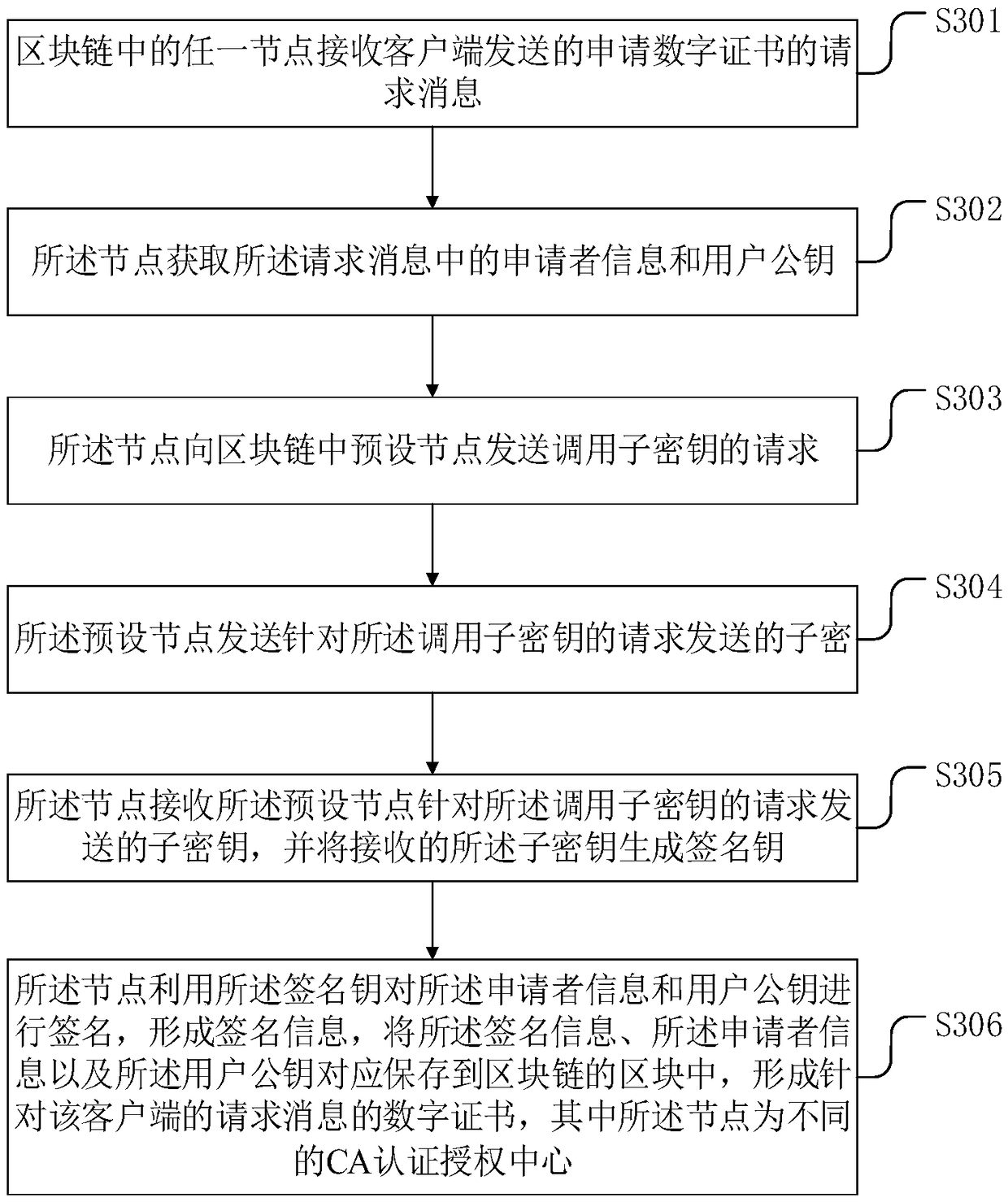
[0096] Another blockchain-based CA authentication method provided in Embodiment 3 of this application, such as image 3 shown, including:
[0097] S301: Any node in the blockchain receives a request message for applying for a digital certificate sent by the client.
[0098] Here, any node in the blockchain can receive request messages sent by clients to apply for different types of digital certificates. Based on the application angle classification of digital certificates, the types of digital certificates can be classified into server certificates, email certificates and personal certificates.
[0099] S302: The node obtains the applicant information and the user public key in the request message.
[0100]If the digital certificate applied by the client is a server certificate, the applicant information may include a website domain name; if the digital certificate applied by the client is an email certificate, the applicant information may include an email address; if the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com