A method and system for product experience authentication based on member authentication
An identity verification method and ID card technology, applied in the product experience identity verification method and system field based on membership authentication, to achieve the effects of easy operation, protection of physical and mental health, and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
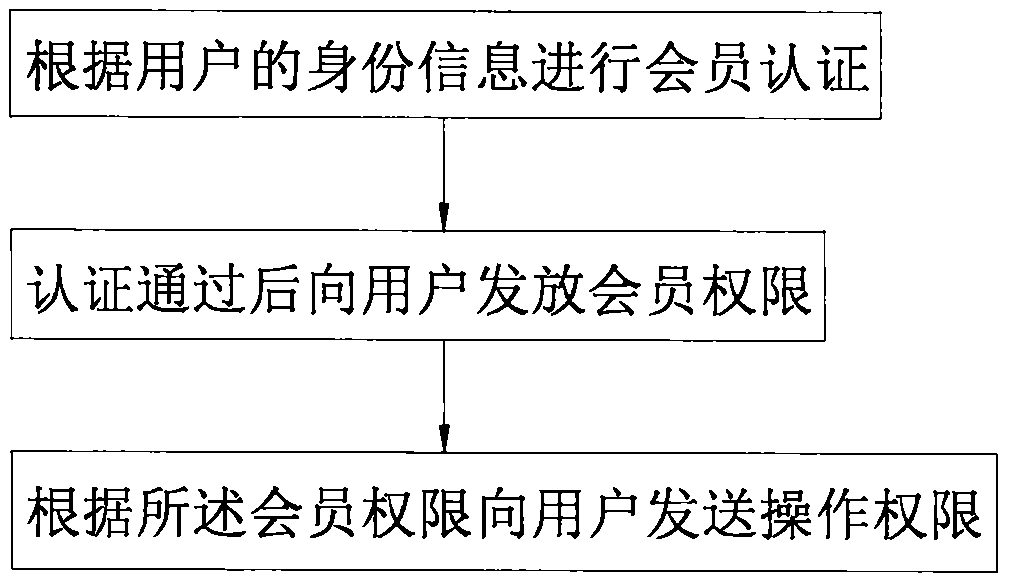
[0039] On the one hand, this embodiment discloses a product experience authentication method based on membership authentication, see figure 1 , which includes:
[0040] Membership authentication based on the user's identity information;
[0041] After the authentication is passed, the membership authority is issued to the user;
[0042] Send operation permissions to users according to membership permissions.
[0043] Membership authentication is performed before granting operation authority to the user. The membership authentication process is the process of verifying and entering the user's identity information for the first time. When logging in again, the member's identity information used when logging in will be combined with the stored user's identity. The information is compared one by one, and the login is completed after the comparison is successful. This identity verification method is easy to operate, and can record the user's operation preferences. After the user ...
Embodiment 2
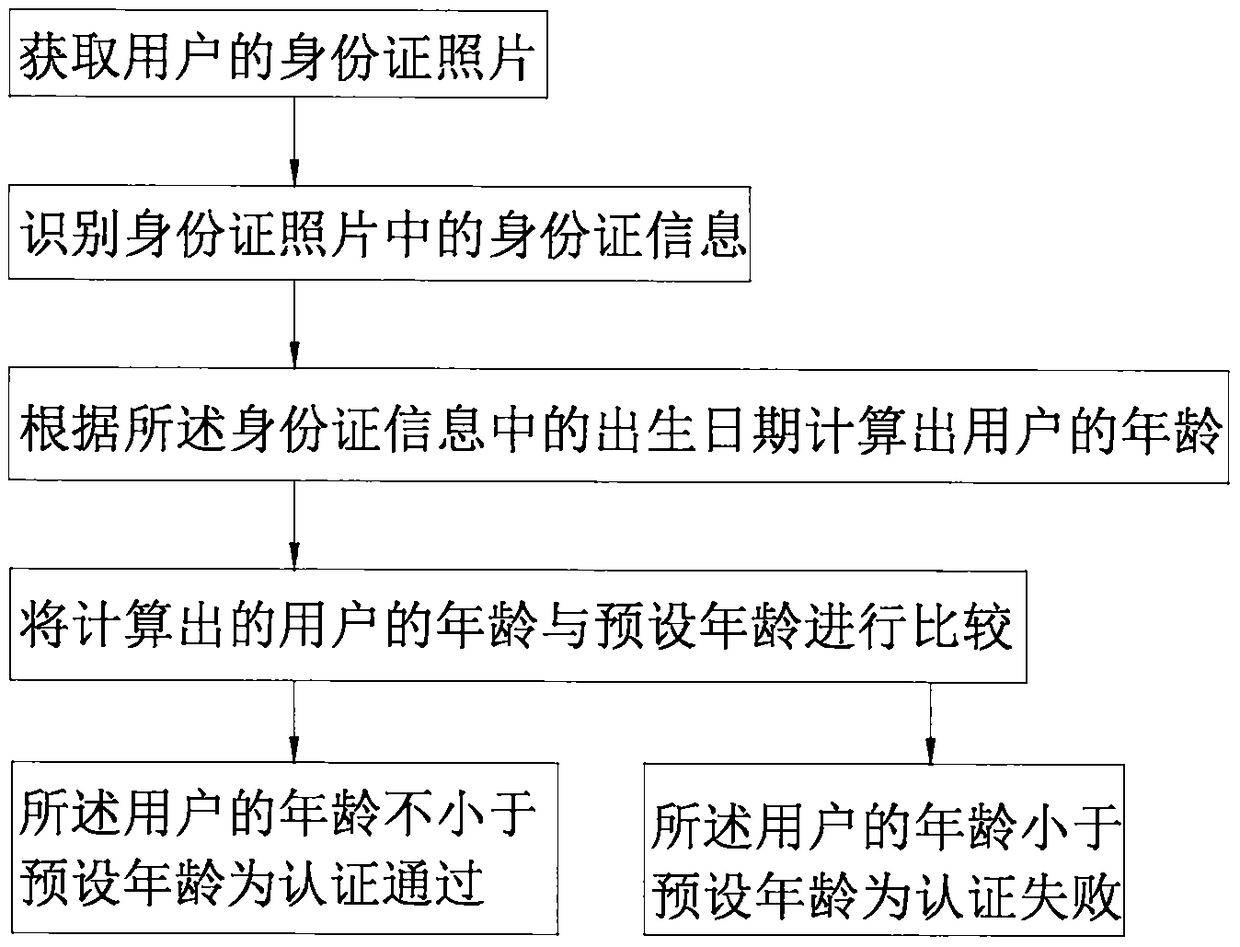
[0050] On the basis of Embodiment 1, the user's identity information includes ID card information, that is, membership verification is performed through the ID card, see figure 2 , the process of membership authentication includes:
[0051] Obtain the user's ID card photo, specifically, take a photo of the user's ID card photo through the camera;
[0052] Identify the ID card information in the ID card photo. The identification process can be realized through the current general OCR (optical character recognition) and other text recognition modules. The ID card information includes the date of birth;
[0053] Calculate the user's age according to the date of birth in the identified ID card information, specifically this calculation is realized by a calculation module, and the specific calculation process is the user's age=the current date-the date of birth in the ID card information;
[0054] Comparing the calculated age of the user with the preset age, the authentication is...
Embodiment 3
[0057] On the basis of Embodiment 1, the user's identity information includes two-dimensional code information, and member authentication includes:
[0058] Acquiring and identifying the two-dimensional code information;
[0059] Call the date of birth in the QR code information and calculate the user's age based on the date of birth, and compare the user's age with the preset age. If the user's age is not less than the preset age, the authentication is passed. Let age be authentication failure.
[0060] The difference between this embodiment and embodiment 2 is that the data sources that need to be entered during membership authentication are different. Embodiment 2 uses ID card information as the data source, and this embodiment uses two-dimensional codes as the data source. Other authentication processes are the same. About The same part is no longer described repeatedly, and the following is only described as follows with respect to the different parts of Embodiment 2:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com