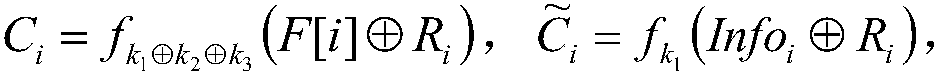An Efficient and Secure Outsourcing Big Data Audit Method in Cloud Environment
A cloud environment and big data technology, applied in the direction of digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of proving that information is not completely random, high computing overhead, insecurity, etc., to save storage overhead, low cost, etc. Communication cost, effect of low computational overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
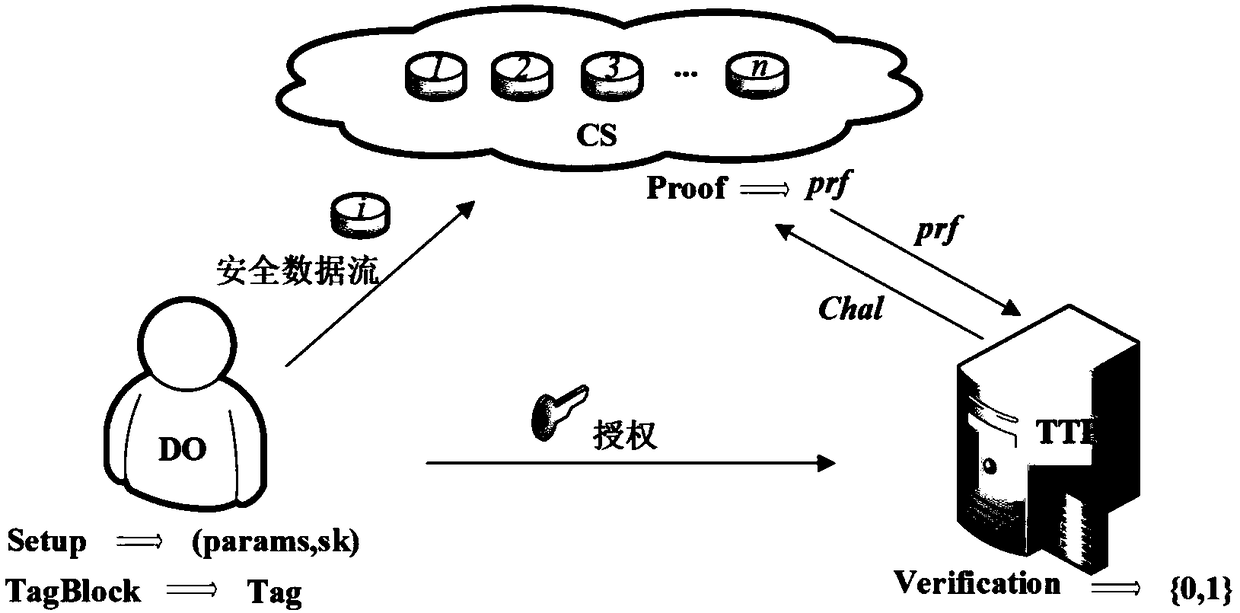
[0031] Formal definition of an outsourced big data audit solution:
[0032] An efficient and secure outsourced big data auditing solution in a cloud environment consists of the following five polynomial time algorithms:
[0033] (1) System establishment algorithm Setup(1 λ ): Input security parameter λ, output system public parameter params and private key sk;
[0034](2) Tag generation algorithm TagBlock(params, sk, F): input system public parameter params, private key sk and file F. Assuming that the file F is divided into n blocks, each file block is represented as F[i] (1≤i≤n), and the output file label T i ;
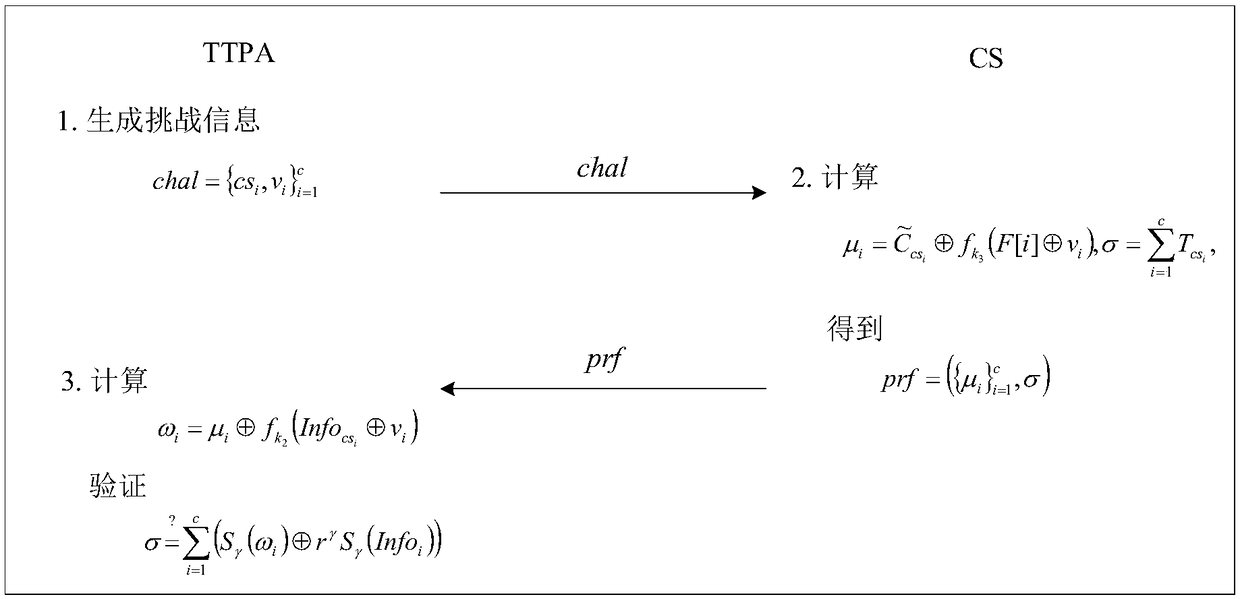
[0035] (3) Challenge algorithm Challenge: output challenge information chal;
[0036] (4) Proof algorithm Proof(params, F, T i ,chal): input system public parameters params, file F, file label T i and challenge information chal, output proof information prf;
[0037] (5) Verification algorithm Verification(params, sk, chal, prf): input system public parameter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com