A password evaluation test system and a password evaluation test method
A test system and test method technology, applied in transmission systems, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as hardware and software tool verification, algorithm strength and randomness not provided
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
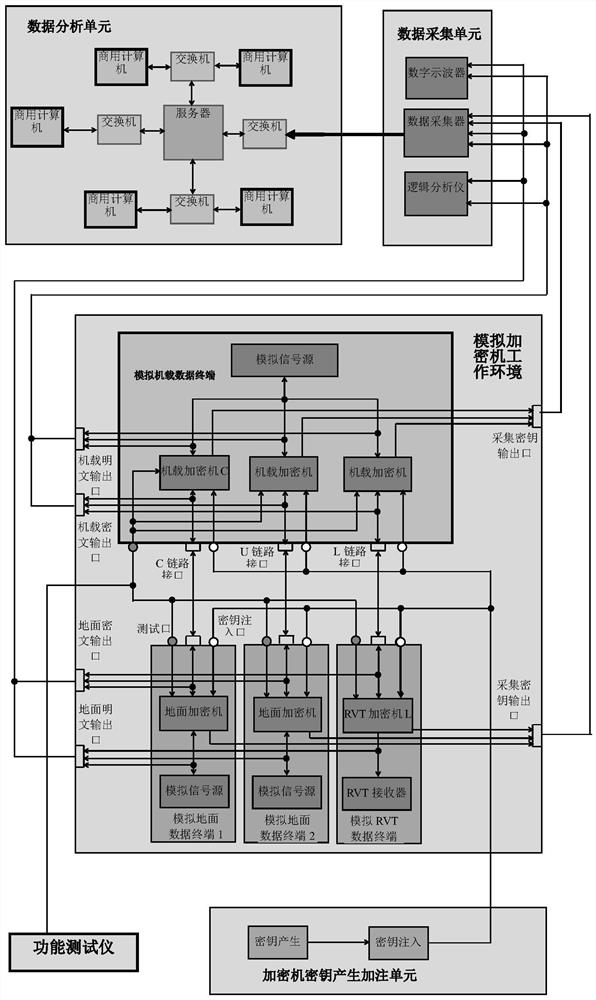
[0071] This embodiment applies the password evaluation system and method to the user's drone, see the attached figure 1 , the system block diagram of the password evaluation test system of the present embodiment, the hardware equipment includes:
[0072] (1) encryption machine, described encryption machine comprises airborne encryption machine, ground encryption machine and RVT encryption machine in use, and is connected with plaintext output port and ciphertext output port by respective link interface, is used for loading cryptographic algorithm , and conduct an encryption strength test and verification on the strength of the actual loaded password;
[0073] (2) An encryption set key generation filling unit, including a key generator and a key injector, the key generator is composed of a key data processing card and a management host, and is used to generate key data. The key injector is used to receive the key generated by the key generating device and inject it into the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com