Container-based virtual desktop device isolation method and device
A technology of virtual desktops and containers, applied in the computer field, can solve problems such as large attack surface of container security vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The concept, specific structure and technical effects of the present application will be clearly and completely described below in conjunction with the embodiments and drawings, so as to fully understand the purpose, scheme and effect of the present application. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other. The same reference numbers are used throughout the drawings to indicate the same or similar parts.
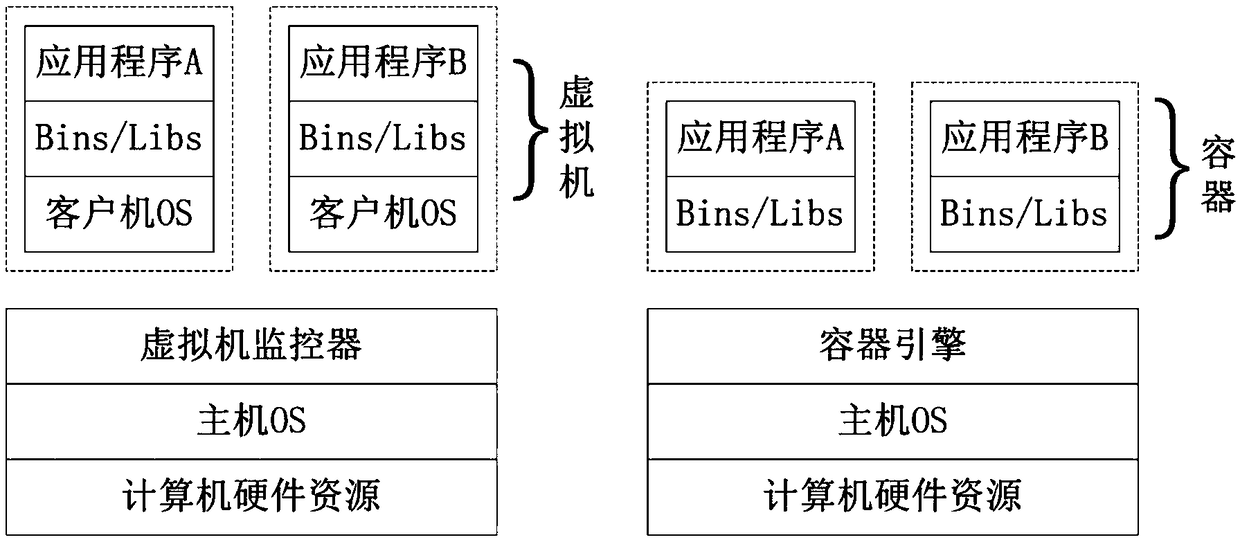
[0069] refer to figure 1 The schematic diagram of the existing virtual machine and container structure is shown. As two typical examples of virtualization technology, virtual machines and containers contain applications and the necessary components (such as system binaries and libraries) to run the applications, and are respectively passed through the virtual machine monitor running on the physical computer. (Hypervisor) and container engine (Docker...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com