Software detection method, device, equipment and medium
A detection method and software technology, applied in the computer field, can solve problems such as inability to effectively detect ransomware and difficulty in ensuring the security of computer systems, and achieve the effect of high reliability and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
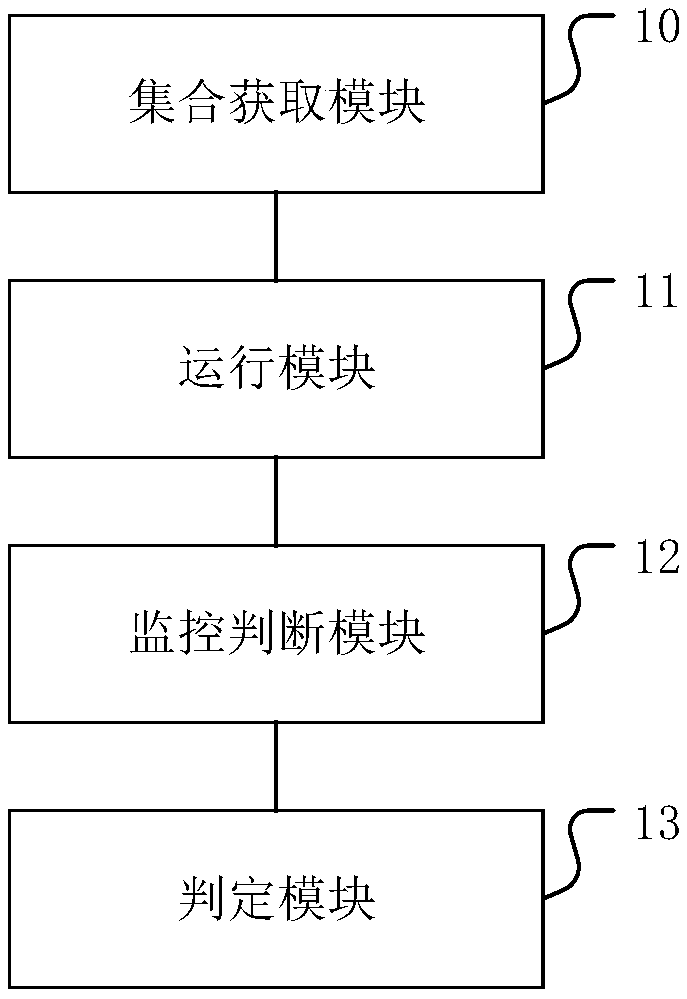
Image
Examples
Embodiment 1
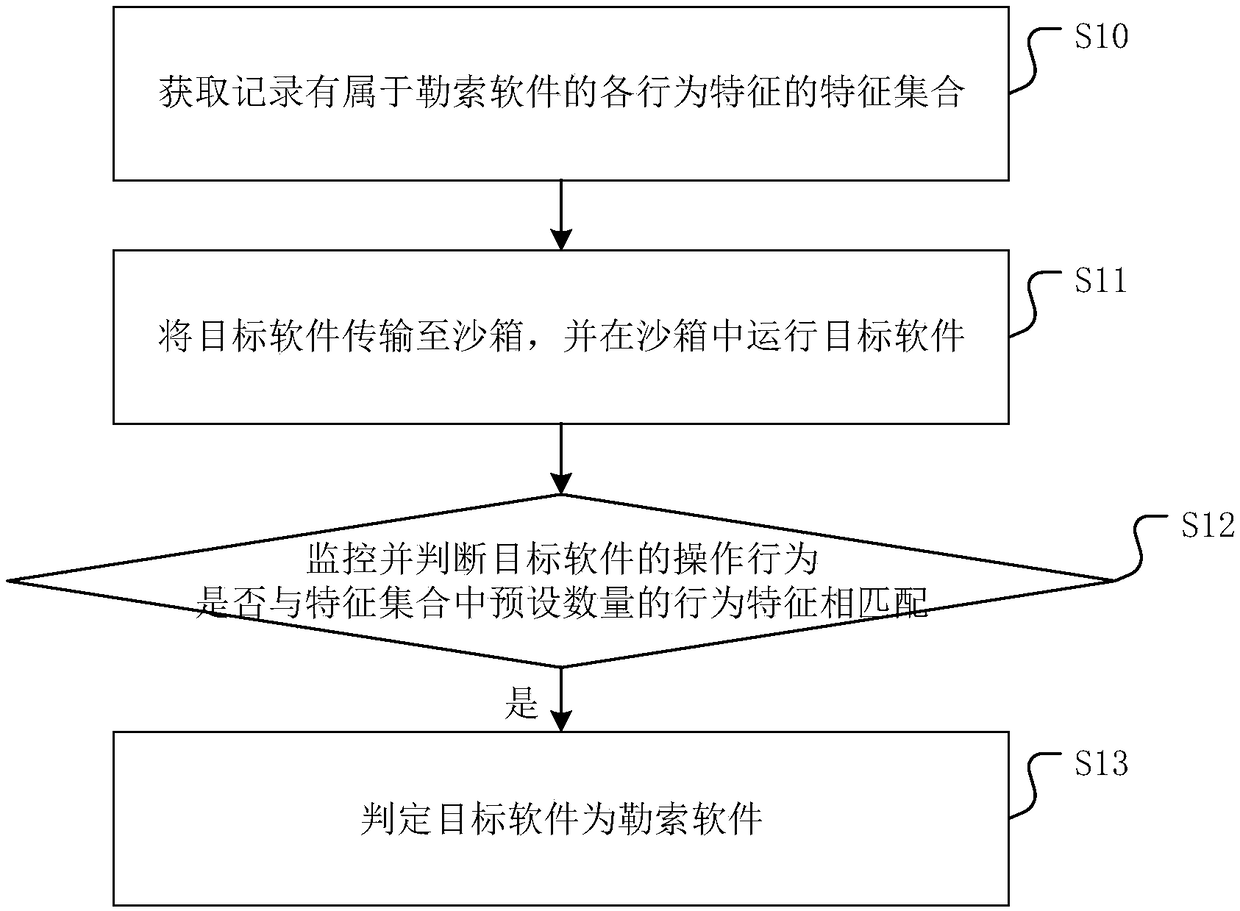
[0044] figure 1 It is a flowchart of a software detection method provided by an embodiment of the present invention. Please refer to figure 1 , the specific steps of the detection method of the software include:
[0045] Step S10: Obtain a feature set recording various behavioral features belonging to ransomware.
[0046] It should be noted that the feature set referred to in this step records various behavioral features that ransomware often executes, and it needs to be emphasized that the behavioral feature in the feature set in this step is not limited to one.
[0047] Step S11: transferring the target software to the sandbox, and running the target software in the sandbox.
[0048] It should be noted that the sandbox is a virtual system environment based on virtualization technology. The programs running in this environment are all independent. After the sandbox is closed, all operations performed in the sandbox will be restored, and will not affect The computer system...
Embodiment 2
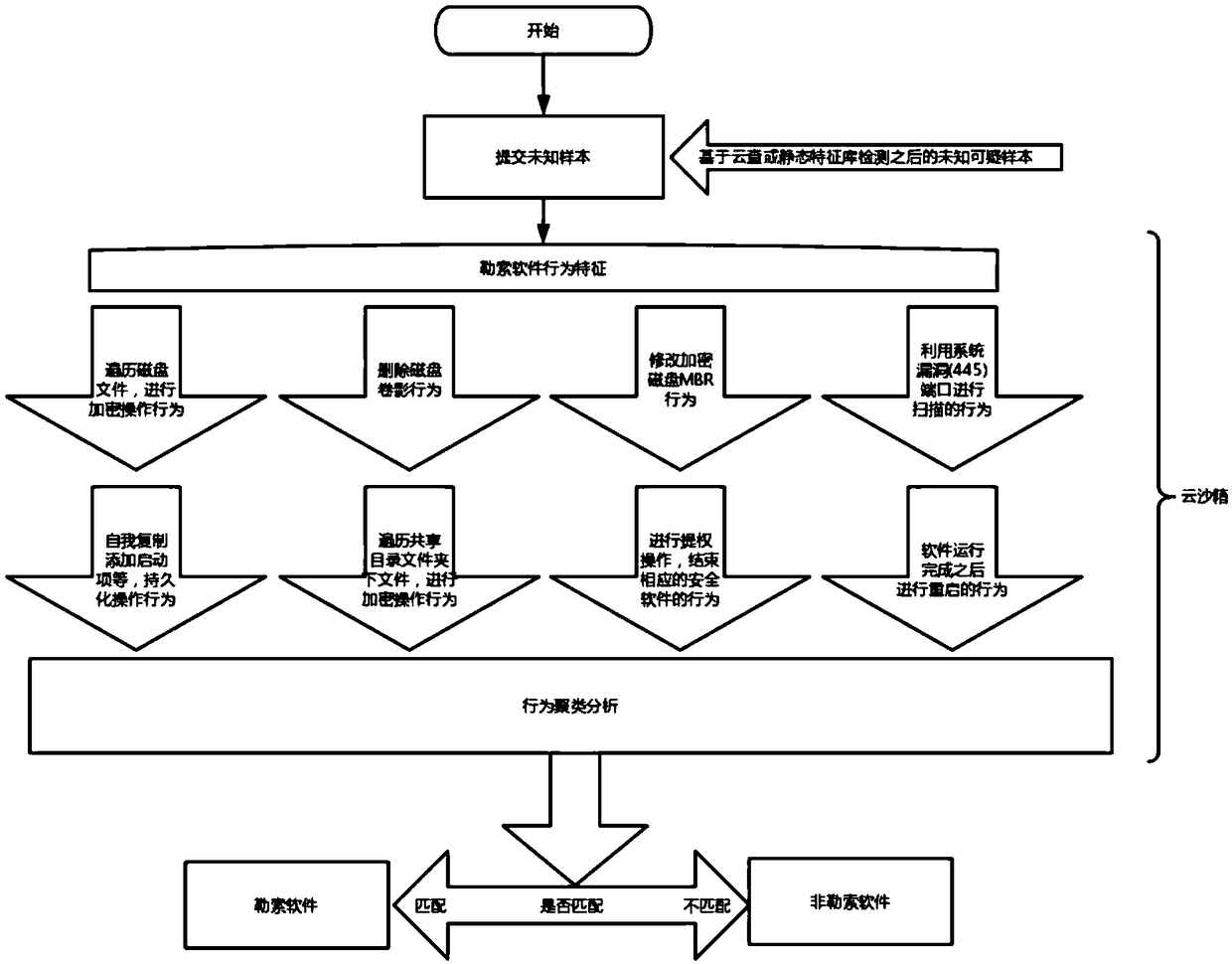
[0056] In order to facilitate the understanding of the first embodiment above, the following provides an embodiment of this solution in an actual scenario:
[0057] Users mark unknown and suspicious samples that cannot be obtained through cloud scanning or static scanning as target software. When running the target software on the user's host, the target software needs to be uploaded to the cloud sandbox to determine the behavior characteristics. The content of the judgment is to first obtain the feature set that records the behavioral features of the ransomware, monitor the working content of the target software, and then judge whether the operating behavior of the target software matches the preset number of behavioral features in the feature set. , it is determined that the target software is ransomware, and then the user is prompted and removed in time. If it is not ransomware, no processing is performed.
Embodiment 3
[0059] On the basis of the above embodiments, the present invention also provides the following series of preferred implementation manners.
[0060] As a preferred implementation, the specific operation content of the behavioral features in the feature set includes:
[0061] Obtain the disk directory through the GetDriveType system function, traverse the original files in the disk directory, and encrypt the original files.
[0062] It should be noted that the ransomware may search the files in a certain disk directory by traversing the disk directory, and find the original files that meet the conditions for modification and encryption. During specific execution, ransomware often traverses the disk directory through the GetDriveType system function, then traverses the original files in the corresponding disk directory through functions such as FindFirstFile and FindNextFile, and finally performs operations such as CreateFile and WriteFile to encrypt the corresponding original f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com