Data desensitization method, device, apparatus and medium for unstructured data access
A technology for unstructured data and data desensitization, applied in the field of data desensitization and data sharing, can solve the problems such as the inability to provide unstructured data desensitization methods and the leakage of unstructured data sensitive information, so as to prevent leakage and improve The effect of the degree of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
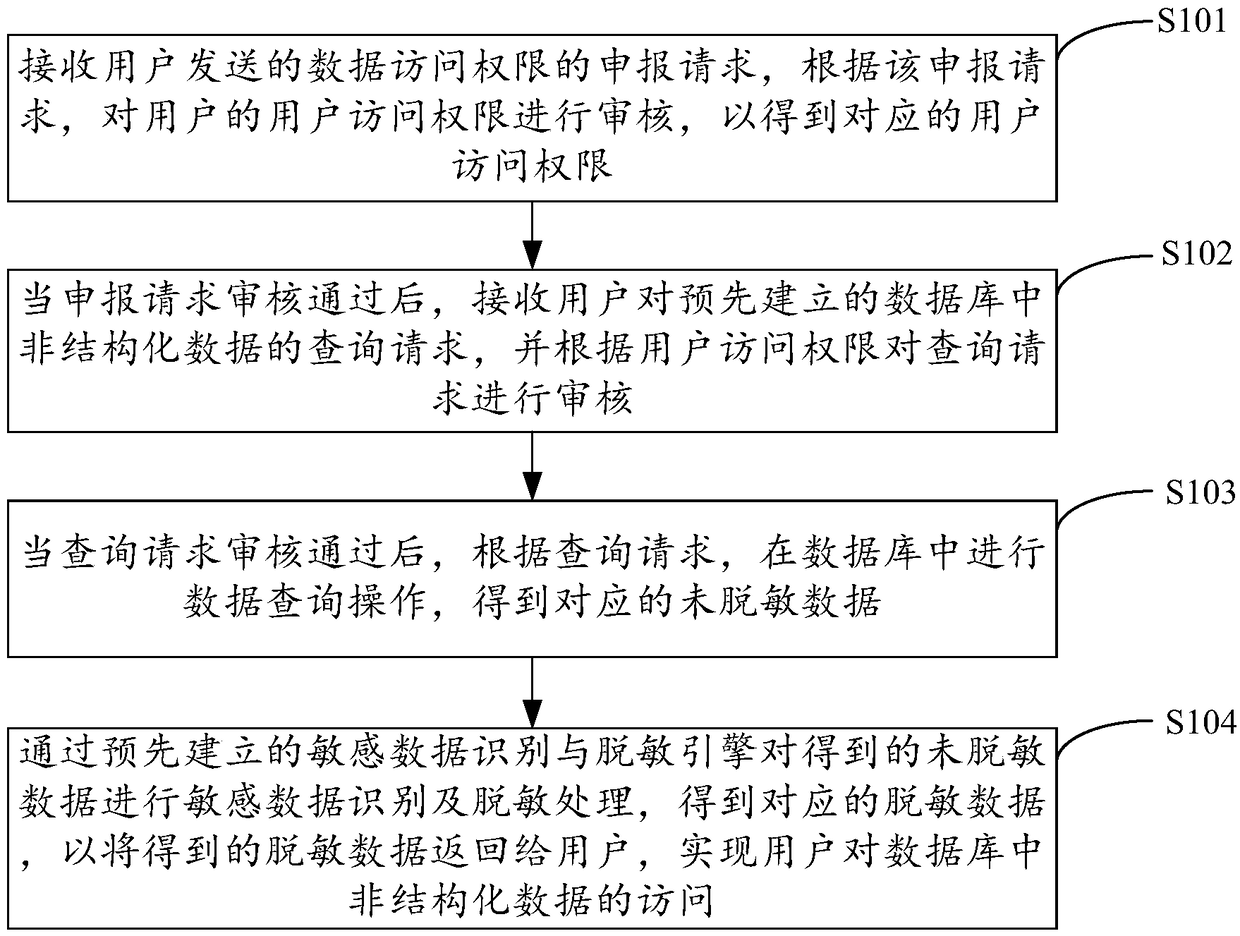
[0030] figure 1 It shows the implementation process of the data desensitization method for unstructured data access provided by Embodiment 1 of the present invention. For the convenience of description, only the parts related to the embodiment of the present invention are shown, and the details are as follows:
[0031] In step S101, a request for declaration of data access rights sent by a user is received, and according to the declaration request, the user access rights of the user are reviewed to obtain corresponding user access rights.
[0032] The embodiments of the present invention are applicable to data sharing and interaction platforms, systems or devices, such as personal computers, servers, and the like. The user declares the data access authority to the preset third-party application authority declaration module, and the third-party application authority declaration module checks whether the user has the data query authority and the user's data access scope accordin...
Embodiment 2
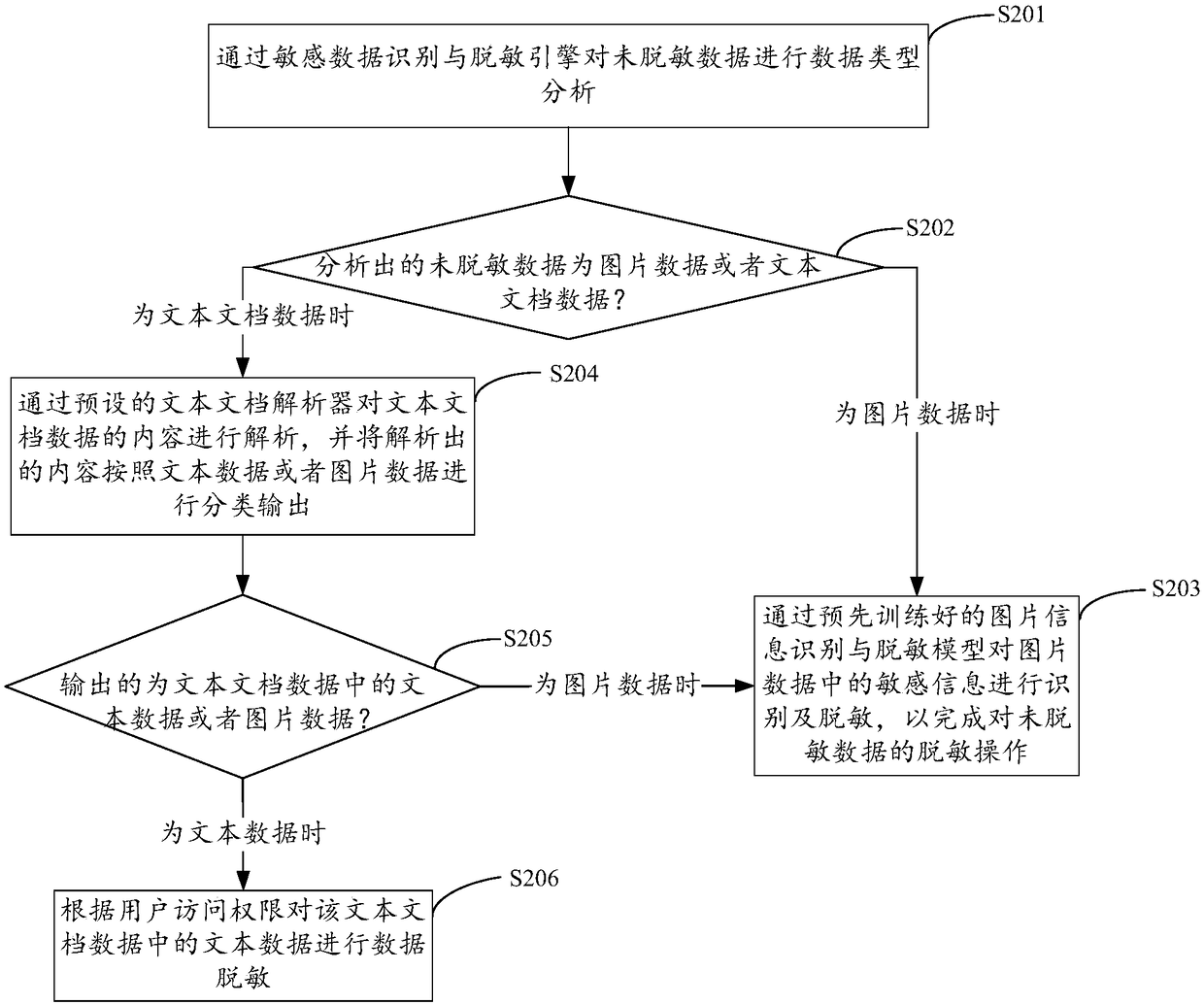
[0041] figure 2 It shows the implementation process of step S104 in the first embodiment provided by the second embodiment of the present invention to carry out sensitive data identification and desensitization processing on the non-desensitized data through the sensitive data identification and desensitization engine. The relevant parts of the embodiments of the present invention are described in detail as follows:
[0042] In step S201, the sensitive data identification and desensitization engine performs data type analysis on the non-desensitized data to determine that the non-desensitized data is image data or text document data.
[0043] In the embodiment of the present invention, the non-desensitized data is analyzed by the pre-established sensitive data identification and desensitization engine, and the non-desensitized data is determined to be image data or text document data according to the analysis result.
[0044] In step S202, analyze the data type of the undese...
Embodiment 3
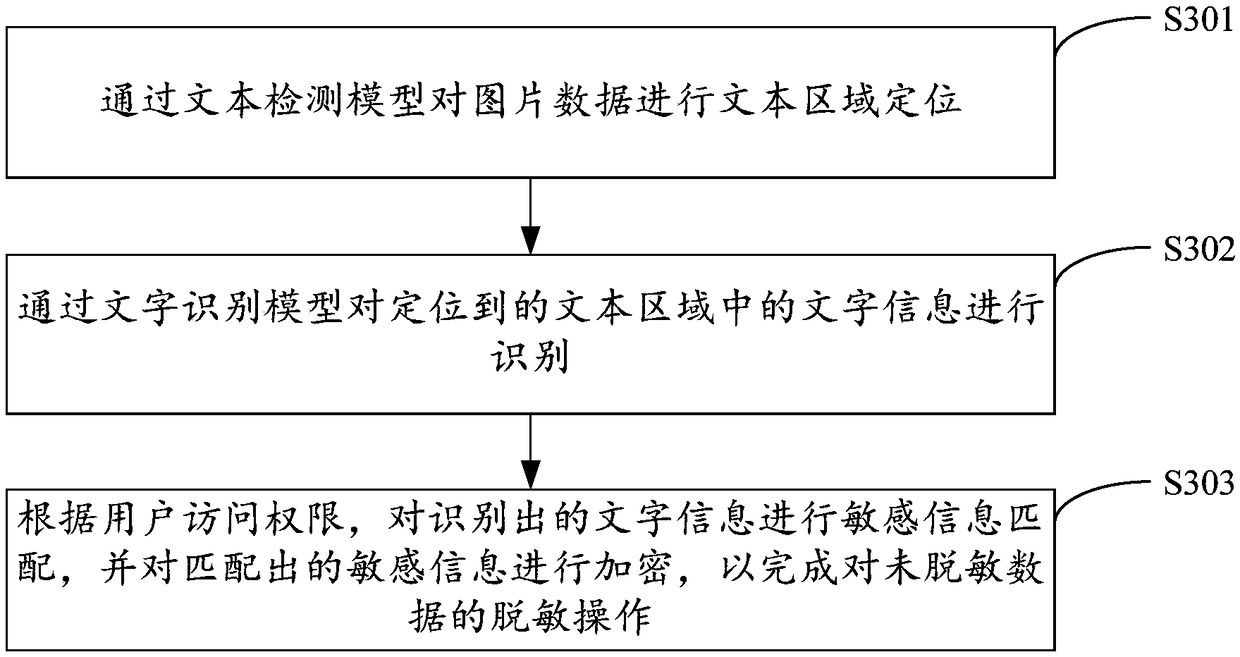
[0073] image 3 It shows the implementation process of step S203 in the second embodiment provided by the third embodiment of the present invention to identify and desensitize the sensitive information in the picture data through the pre-trained picture information identification and desensitization model. Out of the part related to the embodiment of the present invention, detailed description is as follows:
[0074] In step S301, text region positioning is performed on image data through a text detection model.
[0075] In the embodiment of the present invention, when using the text detection model to locate the text region of the picture data, preferably, the following steps are used to realize the location of the text region:
[0076] (1) Utilize the convolution part of the VGG-16 convolutional neural network that has trained parameters in the text detection model to extract the picture features in the picture data, and obtain the corresponding feature map;
[0077] (2) G...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com