Multi-step attack scene mining method based on neural network and Bayesian network attack graph
A Bayesian network and attack scenario technology, which is applied in the field of multi-step attack scenario mining, can solve the problems of high computational overhead, high false alarm rate, and high complexity of data mining algorithms, and achieve the effect of improving mining efficiency and eliminating false alarms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the method of the present invention will be further described in detail below in conjunction with specific implementation methods and accompanying drawings.
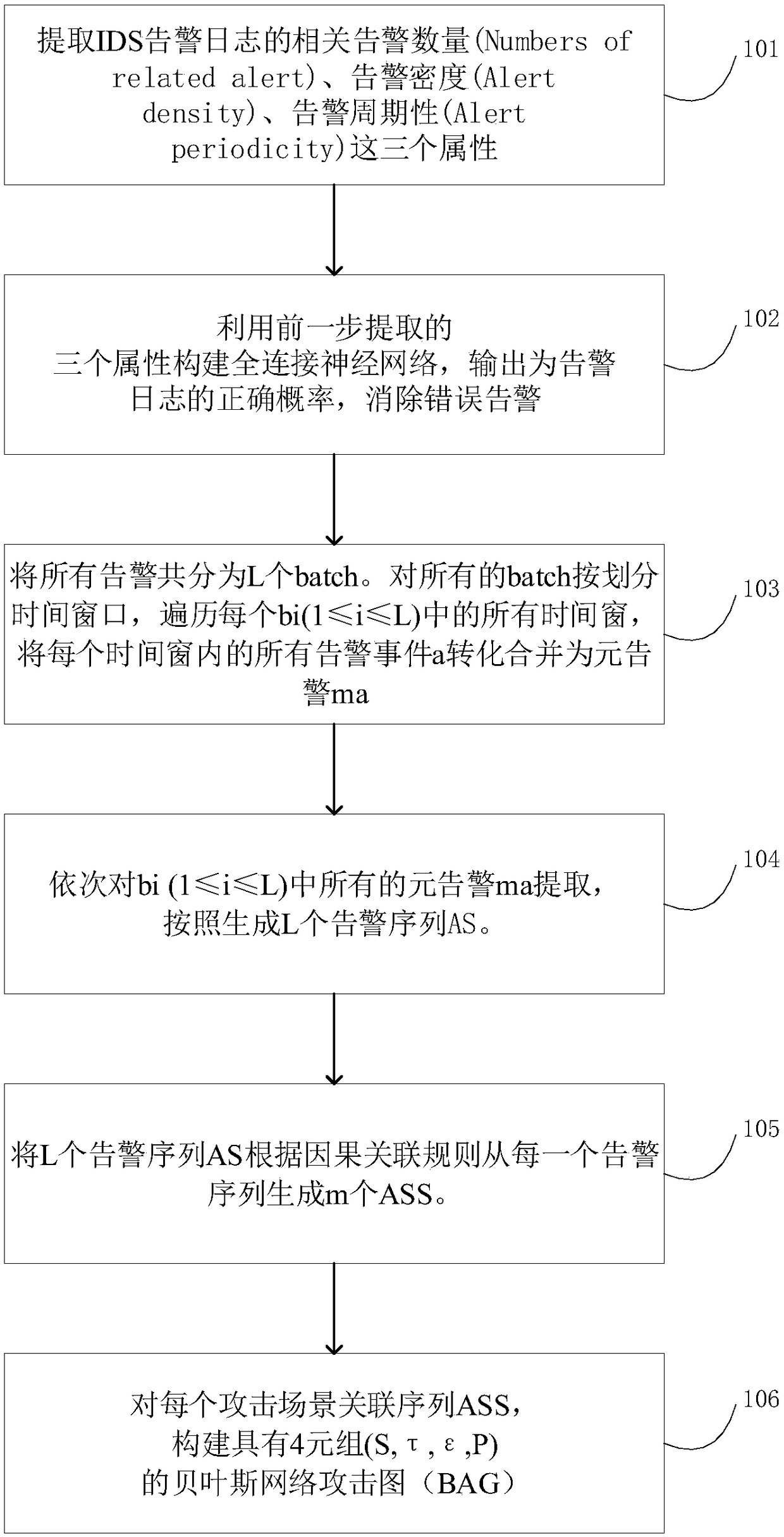
[0036] Such as figure 1 As shown, the offline mode of the multi-step attack scene mining method based on neural network and Bayesian network attack graph of the present invention, the method comprises the following steps:
[0037] Step 101 , extracting three attributes of the IDS alarm log, namely, Numbers of related alerts, Alert density, and Alert periodicity.
[0038] Step 102, using the three attributes extracted in the previous step to construct a fully connected neural network, and output the correct probability of the alarm log to eliminate false alarms.
[0039] Step 103, divide all alarms into L batches. Divide time windows for all batches, traverse all time windows in each bi (1≤i≤L), convert and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com