A database encryption method based on an AES algorithm
An encryption method and database technology, applied in the field of database encryption based on the AES algorithm, can solve the problems of easy-to-crack information, low security, leakage, etc., and achieve the effect of high difficulty in cracking and strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described below in conjunction with the accompanying drawings.
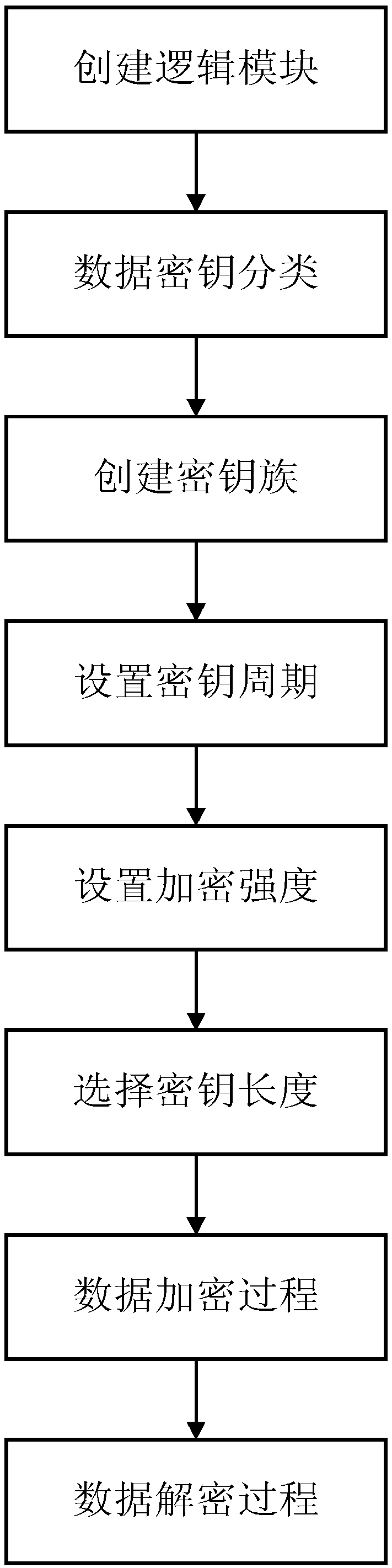
[0044] refer to Figure 1 ~ Figure 4 , a kind of database encryption method based on AES, comprises the following steps:
[0045] 1) Create a logical module and divide the encryption system into five logical modules, namely: key storage module, key engine module, key information module, key management module and data storage module;
[0046] 2) Data key classification, create a master key and a work key in the key management module, the master key is responsible for encrypting the work key, and the work key is responsible for encrypting the database table or data item;
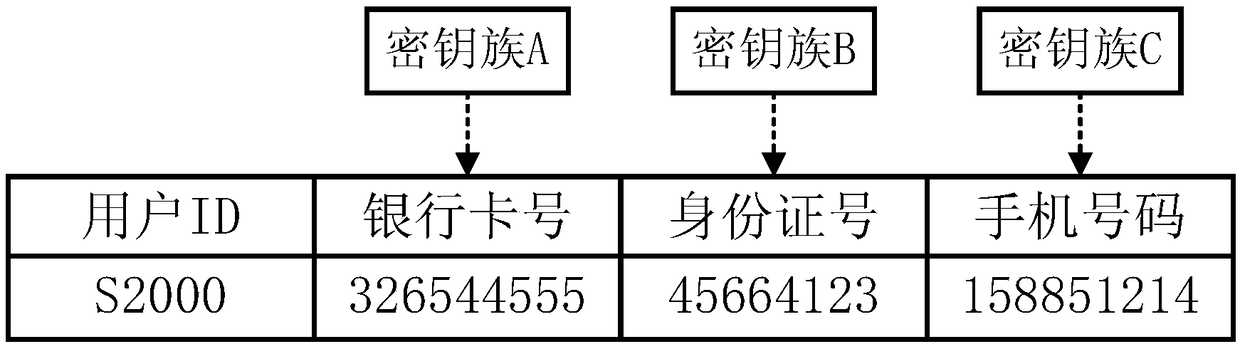
[0047] 3) Create a key family, group data according to attributes or functions, create corresponding key families according to the number of groups, and assign targeted encryption objects to each key in the key family, such as figure 2 shown;
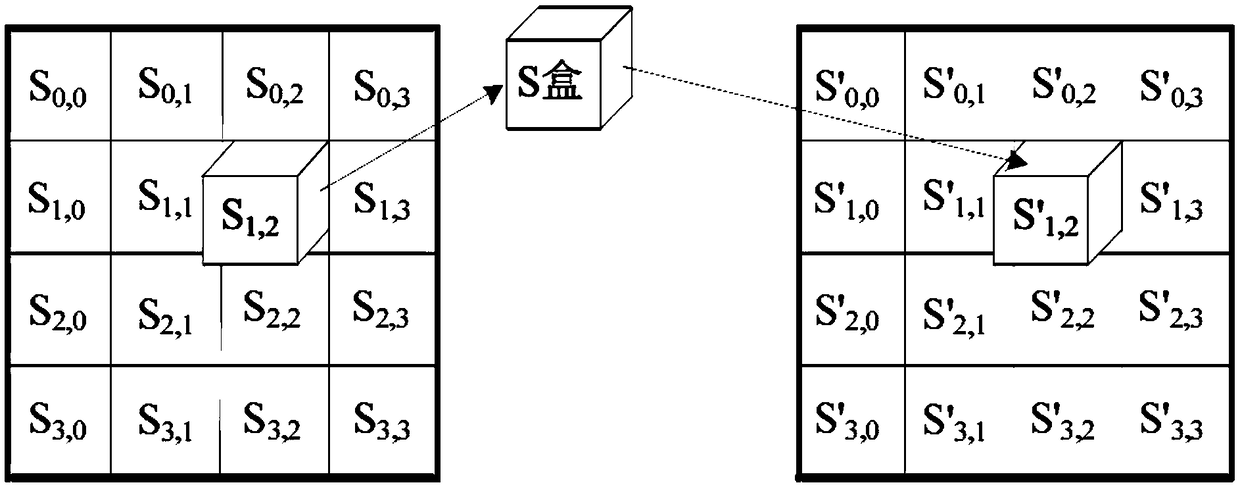
[0048] 4) Set the key cycle. When creating the key, se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com