Key negotiation method, apparatus, and system
A technology of key agreement and key, which is applied in the field of communication, can solve problems such as poor key security, and achieve the effect of reducing the possibility and solving the problem of poor key security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
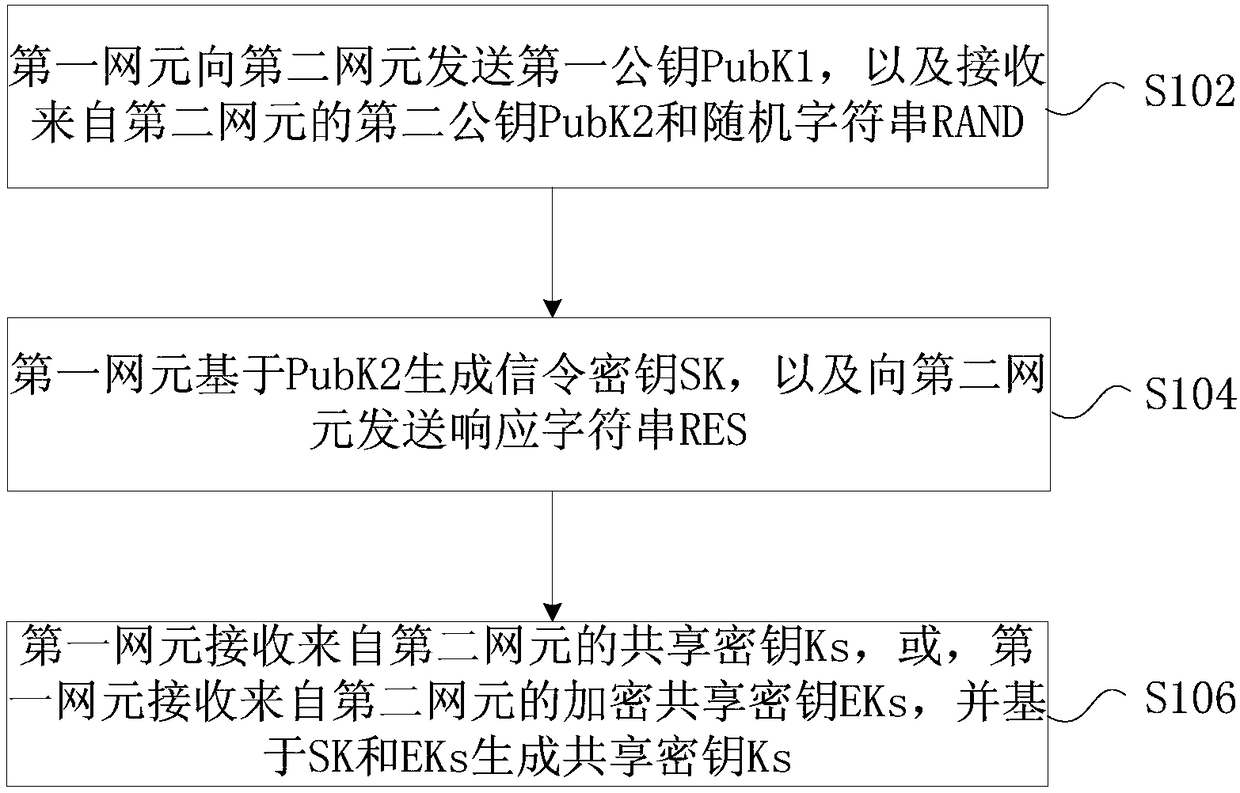
[0043] In this embodiment, a key agreement method is provided, figure 1 is a flowchart of a key agreement method according to an embodiment of the present invention, such as figure 1 As shown, the process includes the following steps:
[0044] Step S102, the first network element sends the first public key PubK1 to the second network element, and receives the second public key PubK2 and the random character string RAND from the second network element;
[0045] Step S104, the first network element generates a signaling key SK based on PubK2, and sends a response string RES to the second network element;
[0046] Step S106, the first network element receives the shared key Ks from the second network element, or, the first network element receives the encrypted shared key EKs from the second network element, and generates the shared key Ks based on SK and EKs.
[0047] Through the above steps, since the first network element and the second network element negotiate the transmis...
Embodiment 2
[0091] In this embodiment, a key agreement device and system are also provided, which are used to implement the above embodiments and preferred implementation modes, and those that have already been described will not be repeated. As used below, the term "module" may be a combination of software and / or hardware that realizes a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
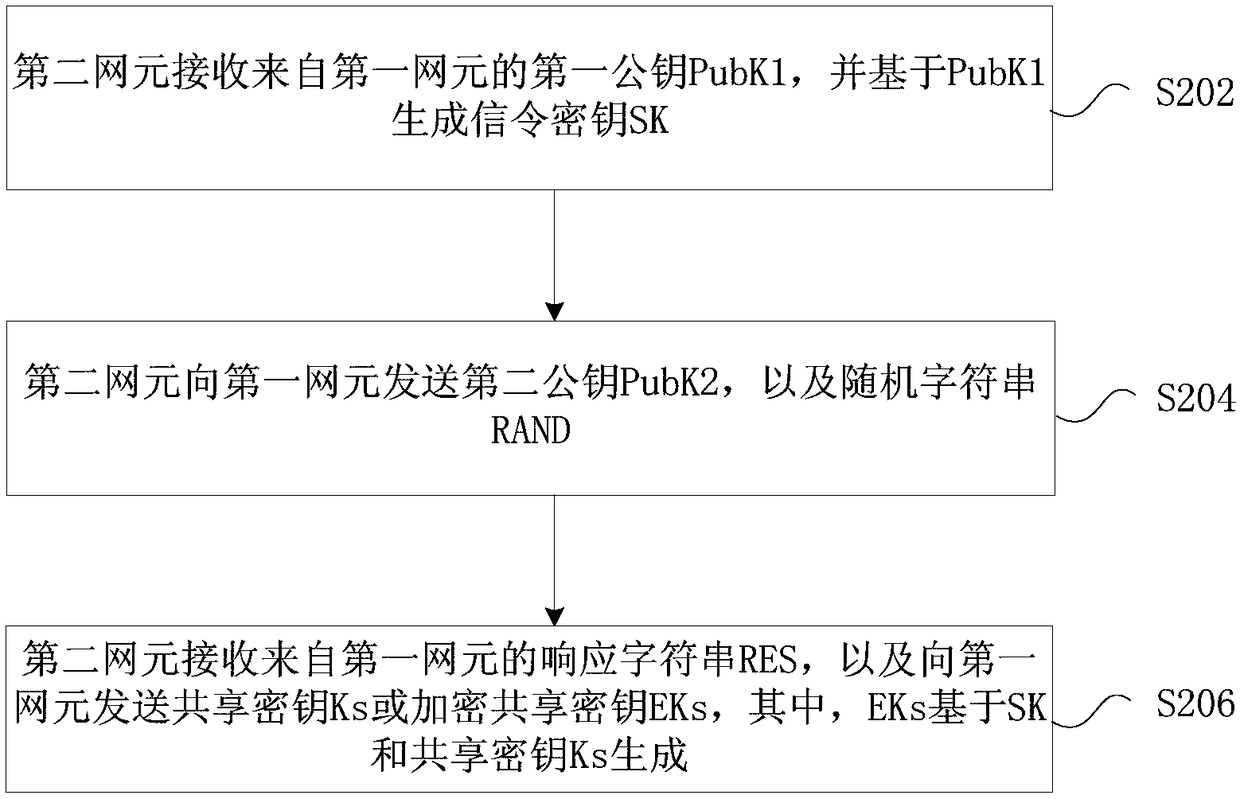
[0092] image 3 is a structural block diagram of a key agreement device according to an embodiment of the present invention, such as image 3 As shown, applied in the first network element, the device includes:
[0093] The transmission module 30 is configured to send the first public key PubK1 to the second network element, and receive the second public key PubK2 and the random character string RAND from the second network...
Embodiment 3
[0110] This embodiment is an optional embodiment according to the present invention, and is used to fully explain and illustrate this application by gathering specific scenarios:
[0111] Figure 6 It is a schematic flow chart of the core network-based key transfer method according to the embodiment of the present invention figure 1 ,Such as Figure 6 As shown, the long-term key LTK or shared key Ks already exists between the second network element and the third network element, and the process includes:
[0112] Step 601: the first network element, the visited network (such as the mobility management function MMF, or the security anchor function SEAF, or the access management entity AMF, etc.) sends the second network element, the home network (such as the authentication service function AUSF, or the authentication authorization Accounting AAA, or authentication vector storage function ARPF, or HSS, etc.) sends a shared key establishment request, such as sending an Authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com