Patents
Literature
55results about How to "Troubleshoot technical issues with poor security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information processing method and electronic equipment
ActiveCN104216520AImprove securityTroubleshoot technical issues with poor securityInput/output for user-computer interactionGraph readingInformation processingSimulation
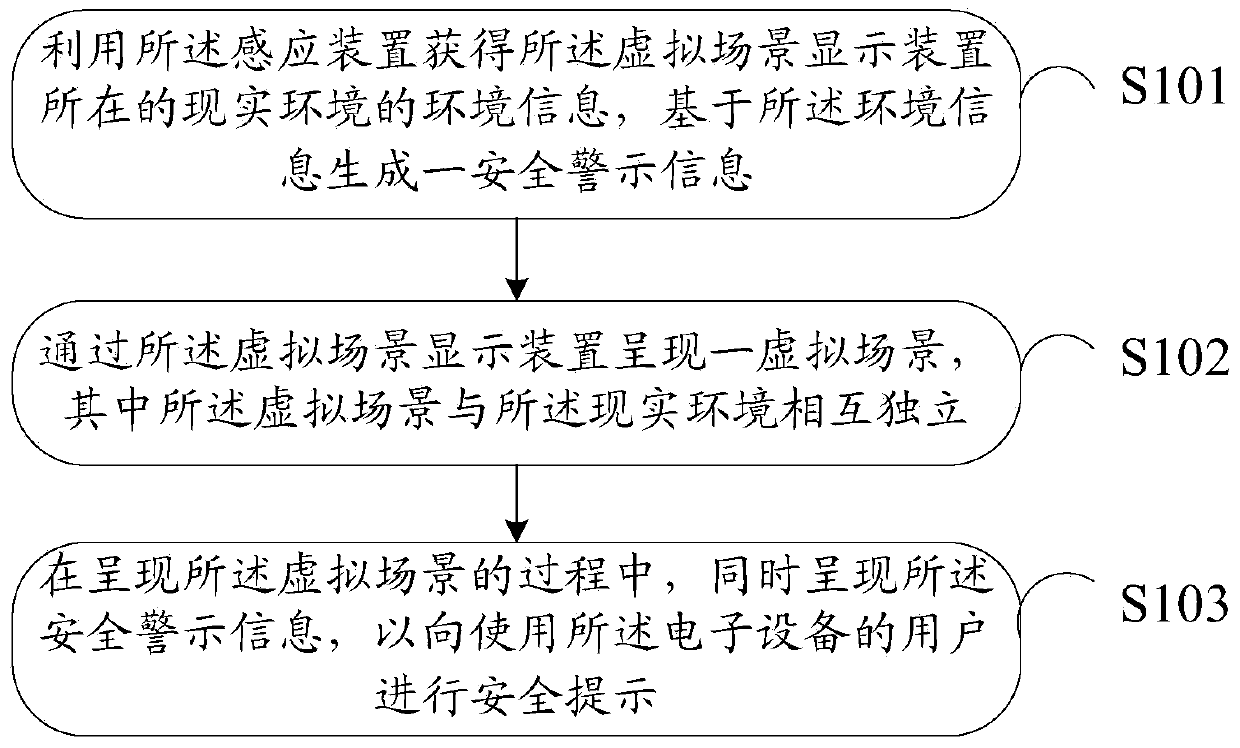
The invention discloses an information processing method and electronic equipment. The method is applied to the electronic equipment. The electronic equipment comprises a virtual scene display device and an induction device. The method comprises the following steps: acquiring environmental information of a real environment where the virtual scene display device is located by using the induction device and generating safety warning information based on the environmental information; presenting a virtual scene through the virtual scene display device, wherein the virtual scene is independent of the real environment; meanwhile presenting the safety warning information in the process of presenting the virtual scene so as to give safety tips for users of the electronic equipment. Through the technical scheme, the technical problem of poor safety existing during use of the virtual scene display device in the prior art is solved, and the safety for use of the virtual scene display device is improved.
Owner:LENOVO (BEIJING) LTD
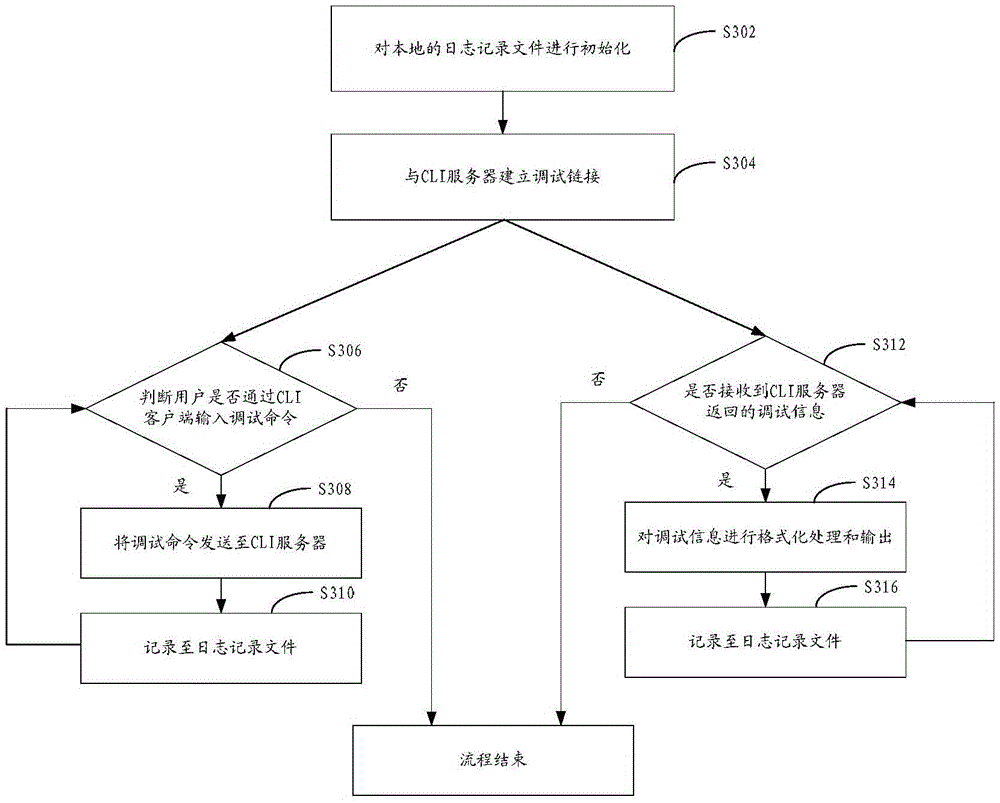
Debugging method and system of equipment
ActiveCN106708489AImprove securityTroubleshoot technical issues with poor securityTransmissionExecution for user interfacesCommand-line interfaceComputer hardware
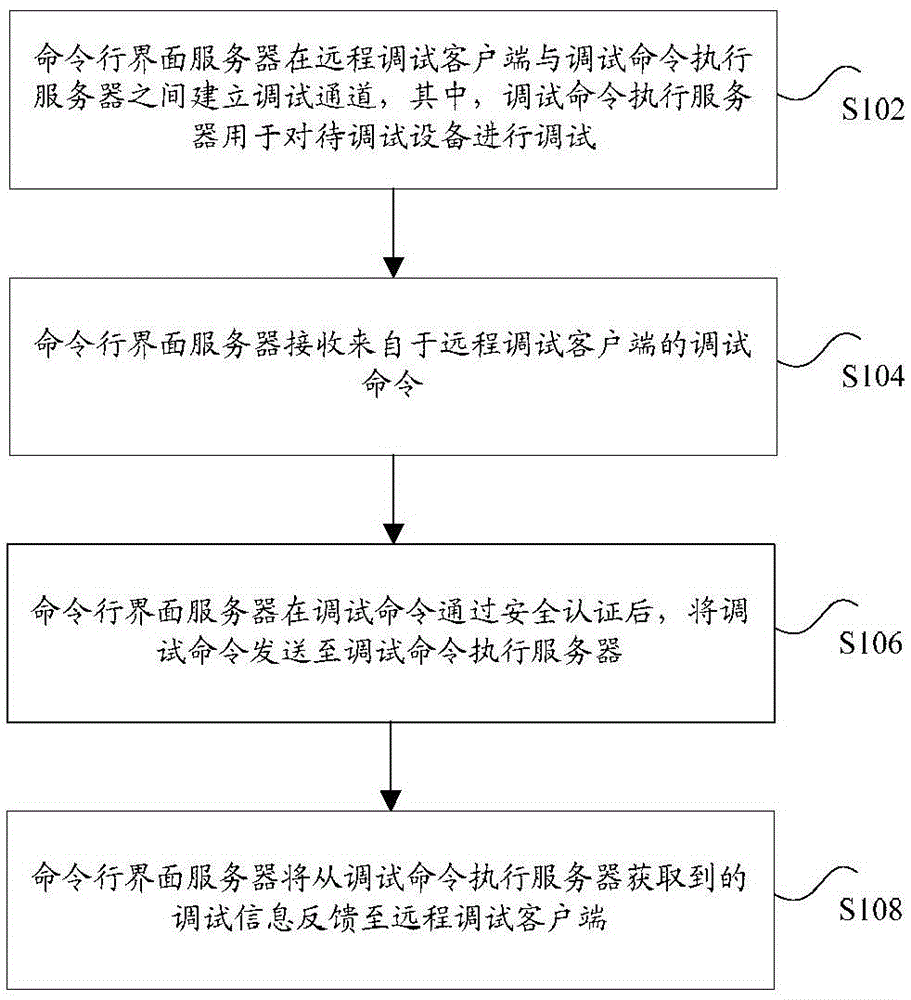
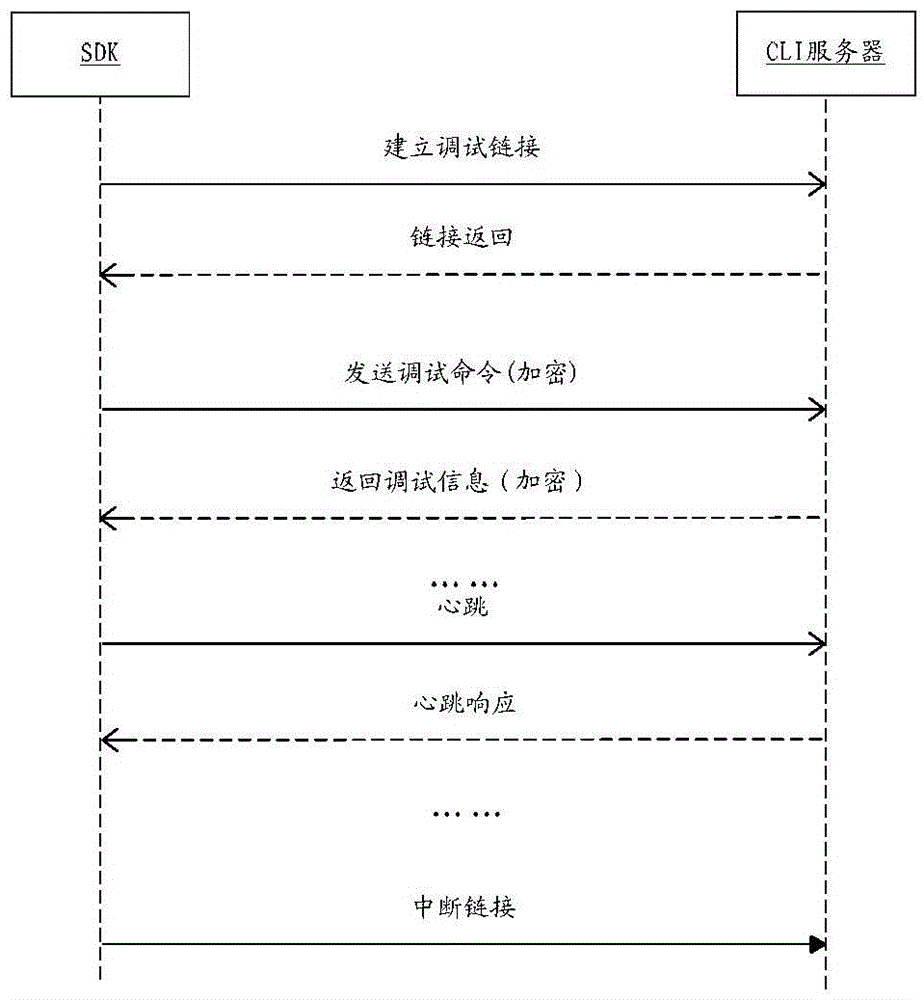
The invention discloses a debugging method and system of equipment. The method comprises the steps that a command line interface server establishes a debugging passage between a remote debugging client-side and a debugging command execution server, wherein the debugging command execution server is used for debugging the equipment to be debugged; the command line interface server receives a debugging command which comes from the remote debugging client-side; after the debugging command passes security certificate, the command line interface server sends the debugging command to the debugging command execution server; the command line interface server feeds back debugging information obtained from the debugging command execution server to the remote debugging client-side. According to the debugging method and the system of equipment, the technical problem that an equipment debugging pattern adopted in related technology is poor in network security is solved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Pipe clamping device and assembly machine
ActiveCN102672644ATroubleshoot technical issues with poor securityWork holdersMetal working apparatusSolenoid valveEngineering
The invention discloses a pipe clamping device and an assembly machine, relating to the technical field of automobile spare part assembly and solving the technical problems such as poor safety in prior arts. The pipe clamping device comprises a first clamping head, a second clamping head, a connection member, a spring, a clamping drive mechanism and a clamping degree detection element, wherein two opposite ends of the first clamping head are in movable connection with the connection member and the second clamping head respectively, the clamping drive mechanism includes a cylinder, a forward solenoid valve, and a backward solenoid valve, the cylinder includes a cylinder rod, a forward air pipe joint and a backward air pipe joint, and the clamping degree detection element is arranged on the wall of the cylinder and outputs a clamping signal when the spacing between the first and the second clamping head is smaller than a predetermined safety distance. The assembly machine includes the inventive pipe clamping device. According to the invention, safety and working efficiency of the assembly machine are improved.
Owner:HEBEI CHINAUST AUTOMOTIVE PLASTICS CORP LTD
Data transmission method and data transmission device
ActiveCN105553951ATroubleshoot technical issues with poor securityIncrease the difficulty of crackingMultiple keys/algorithms usagePublic key for secure communicationComputer terminalData transmission
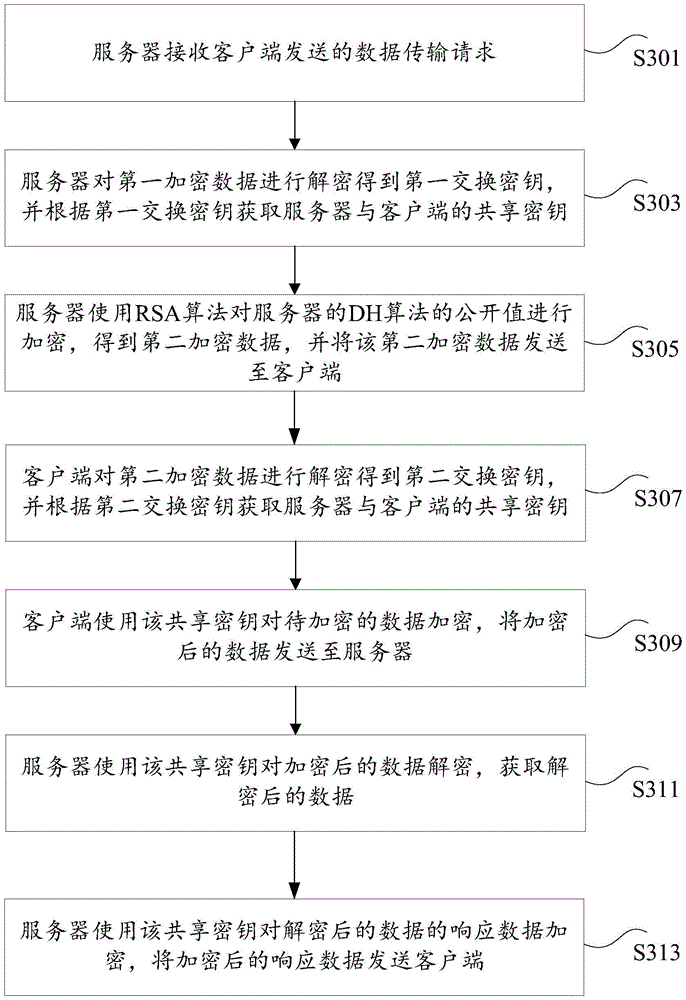
The invention discloses a data transmission method and a data transmission device. The method comprises the following steps: a first terminal acquires a data transmission request sent by a second terminal, wherein the data transmission request at least carries first encrypted data obtained by using a private key of the second terminal to encrypt a first exchange key of the second terminal; the first terminal uses a public key of the second terminal to decrypt the first encrypted data to get the first exchange key, and acquires a shared key of the first terminal and the second terminal according to the first exchange key; and the first terminal uses the shared key to encrypt to-be-transmitted data to get encrypted transmitted data, and sends the encrypted transmitted data to the second terminal. The technical problem that the existing encryption algorithm is of poor security in data transmission is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Network security assessment method and system
InactiveCN109245944ATroubleshoot technical issues with poor securityData switching networksAssessment methodsVulnerability factor
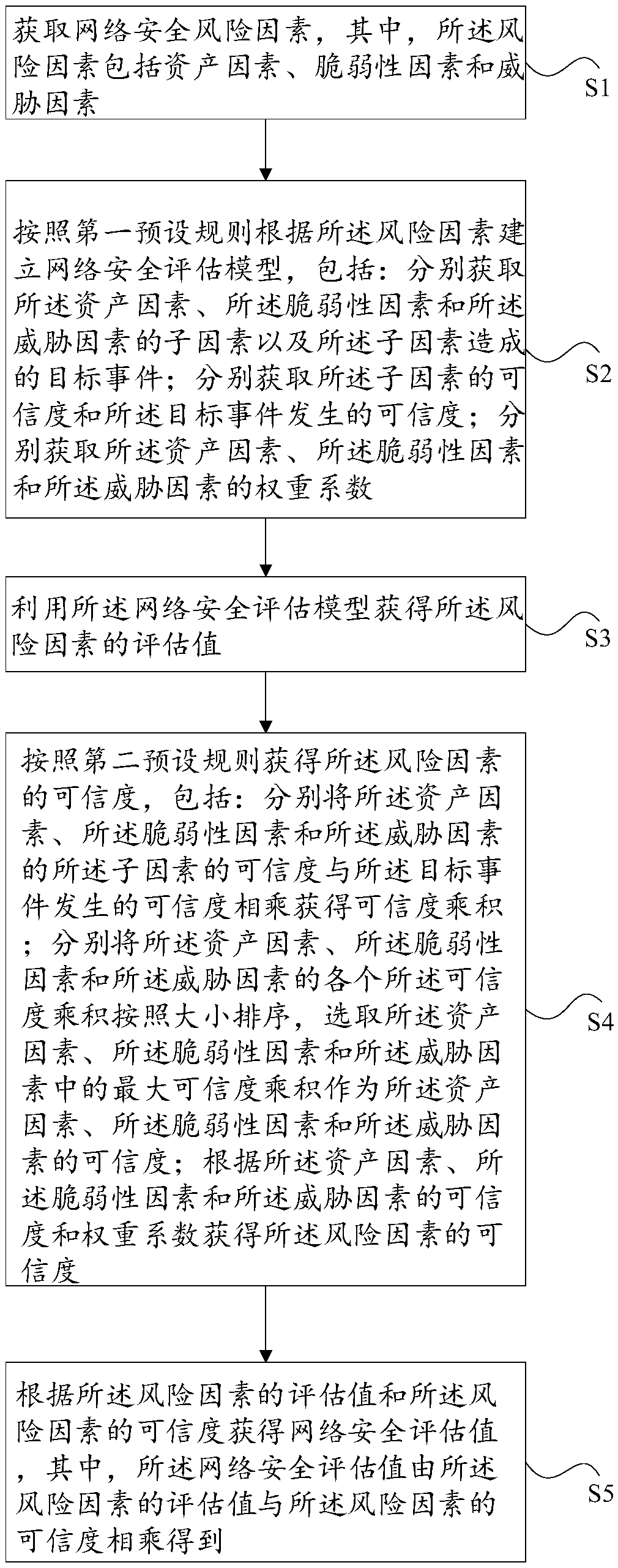
The present invention discloses a network security assessment method. The method includes the steps: obtaining network security risk factors, wherein the risk factors include an asset factor, a vulnerability factor, and a threat factor; establishing a network security assessment model according to the risk factors via a first preset rule; utilizing the network security assessment model to obtain evaluation values of the risk factors; obtaining credibility degrees of the risk factors according to a second preset rule; obtaining a network security evaluation value according to the evaluation values of the risk factors and the credibility degrees of the risk factors, wherein the network security assessment values are obtained by multiplying the evaluation values of the risk factors by the reliability degrees of the risk factors. The invention also provides a network security assessment system implementing the above method. The method and system solve the technical problem that the security defense technology in the related art has poor network security because the action is taken after an event and a possible network attack event cannot be predicted.
Owner:SOUTHWEST PETROLEUM UNIV
Communication method in high-speed railway operation
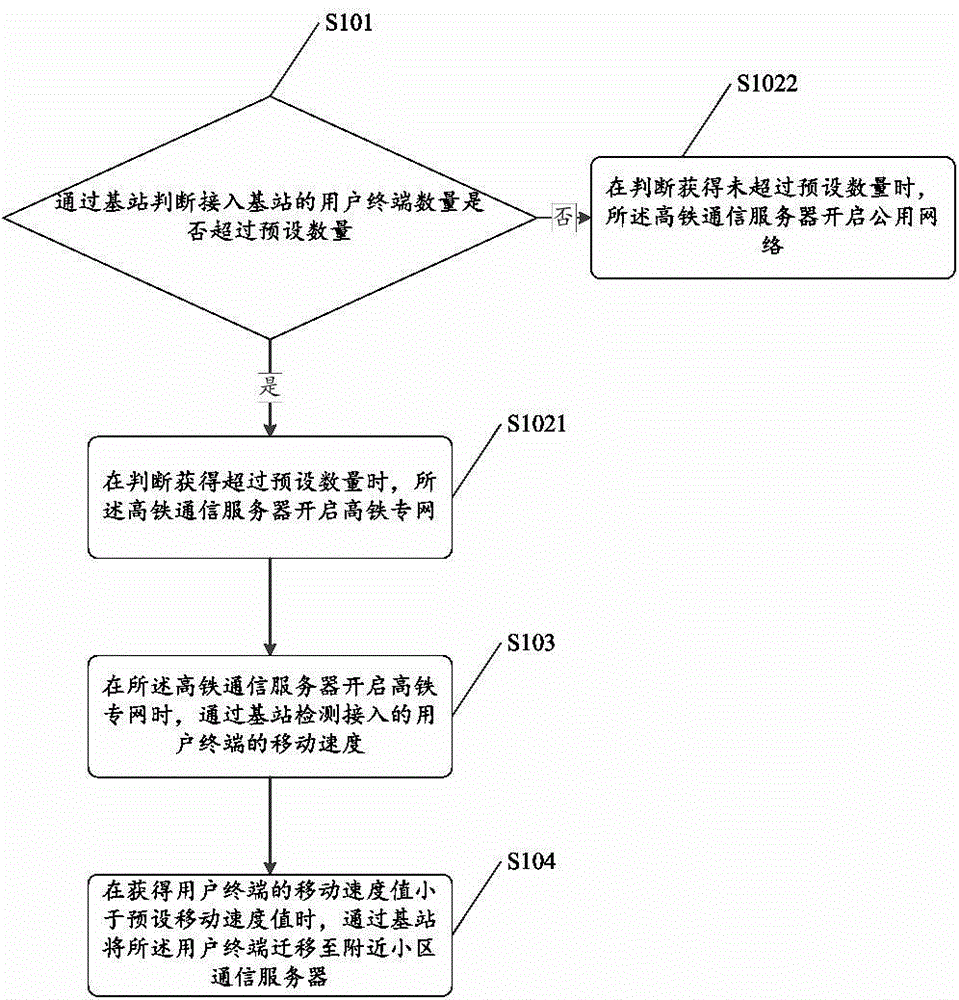
InactiveCN104918258ARelieve stressAddress poor securityNetwork planningCommunications serverMoving speed
The invention discloses a communication method in high-speed railway operation, relates to the technical field of communication, and solves the technical problem that the safety of high-speed railway communication network is relatively low in the prior art. The communication method is applied to the high-speed railway communication network which includes a high-speed railway communication server and a base station, and the high-speed railway communication server is connected with the base station via microwaves. The communication method comprises that the base station determines whether the amount of user terminals connected to the base station exceeds a preset amount; when the amount of the user terminals connected to the base station exceeds the preset amount, the high-speed railway communication server starts a high-speed railway private network; when the amount of the user terminals connected to the base station does not exceed the preset amount, the high-speed railway communication server starts a public network; when the private network is started, the moving speed of the user terminals is detected by the base station; and when the moving speed of the user terminal is lower than a preset moving speed, the base station transfers the user terminals to a communication server of a nearby cell. Thus, the safety of the high-speed railway communication network is improved.
Owner:成都亿邻通科技有限公司
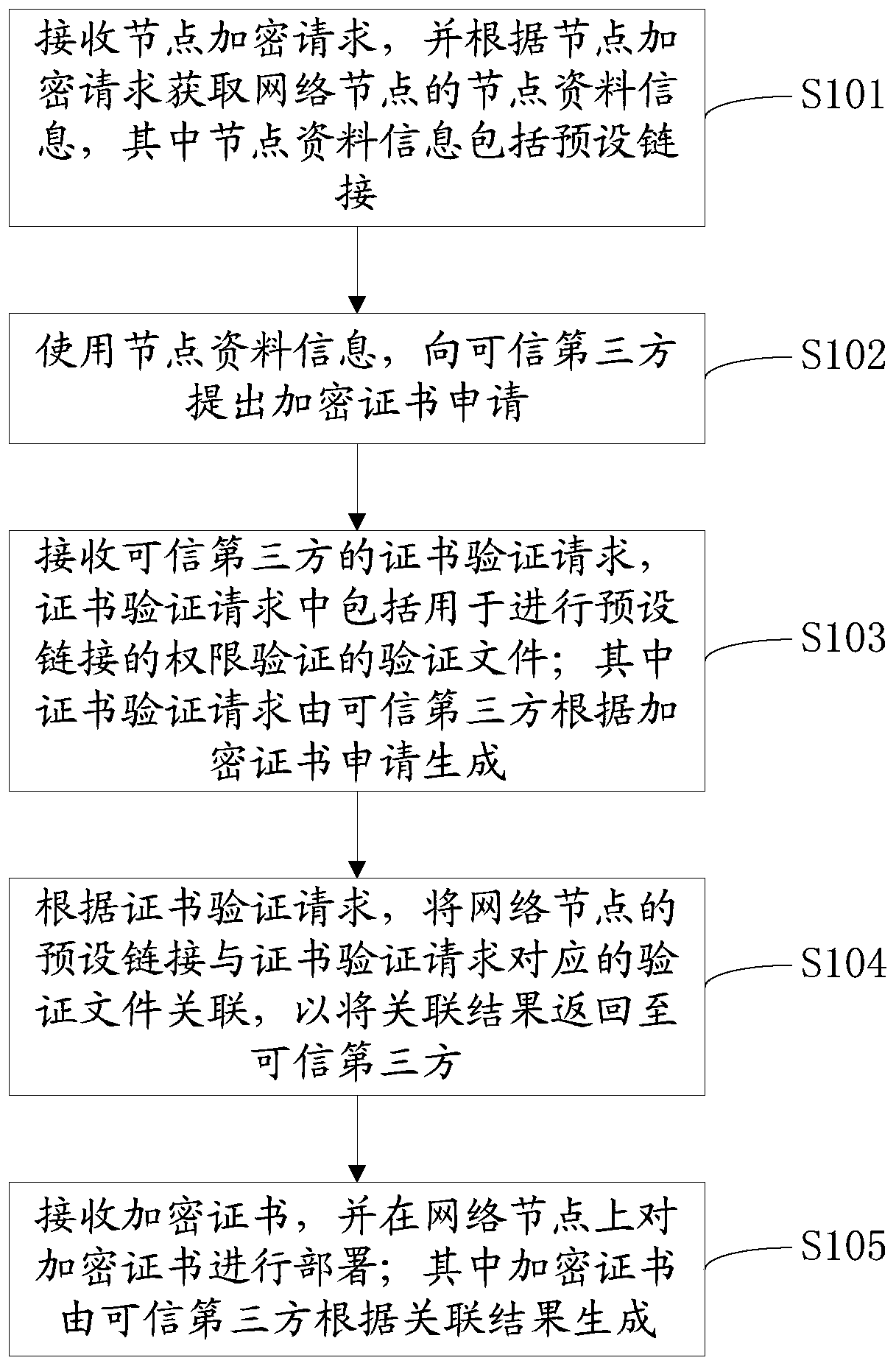
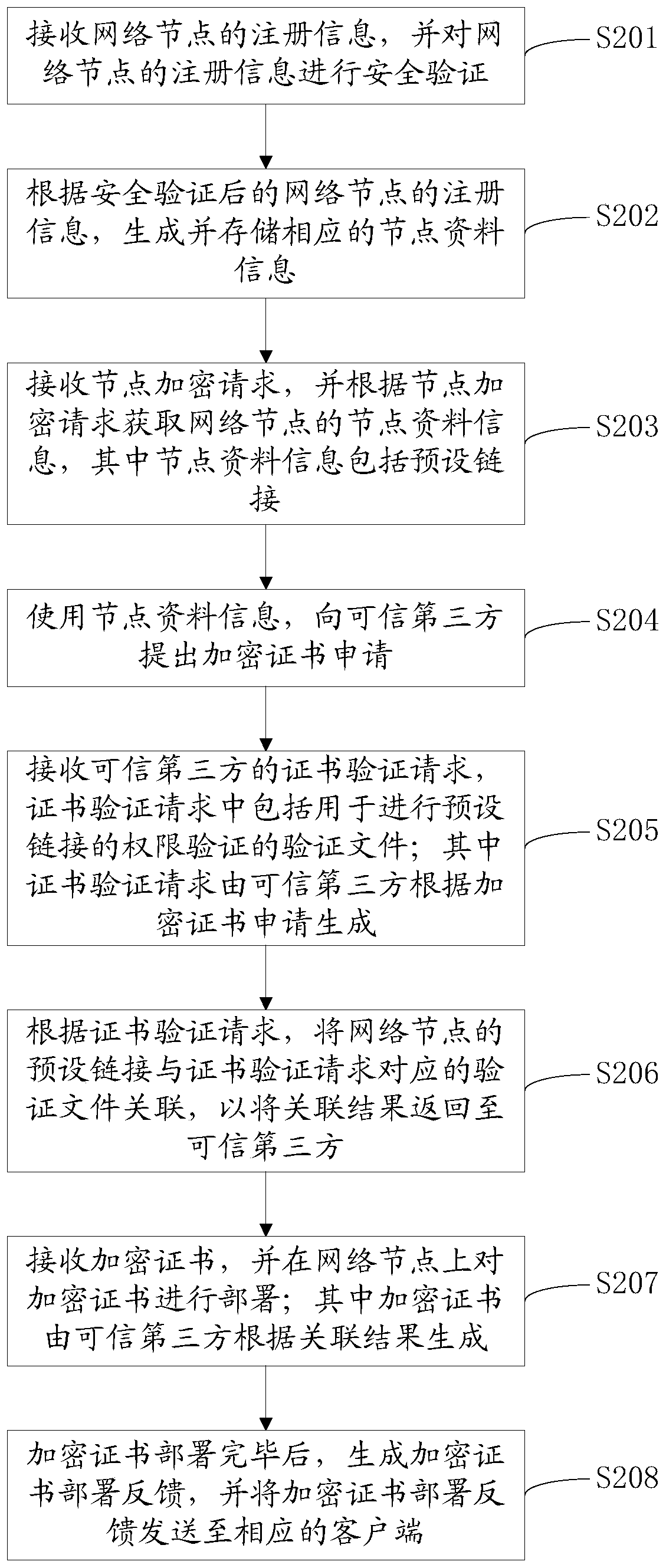
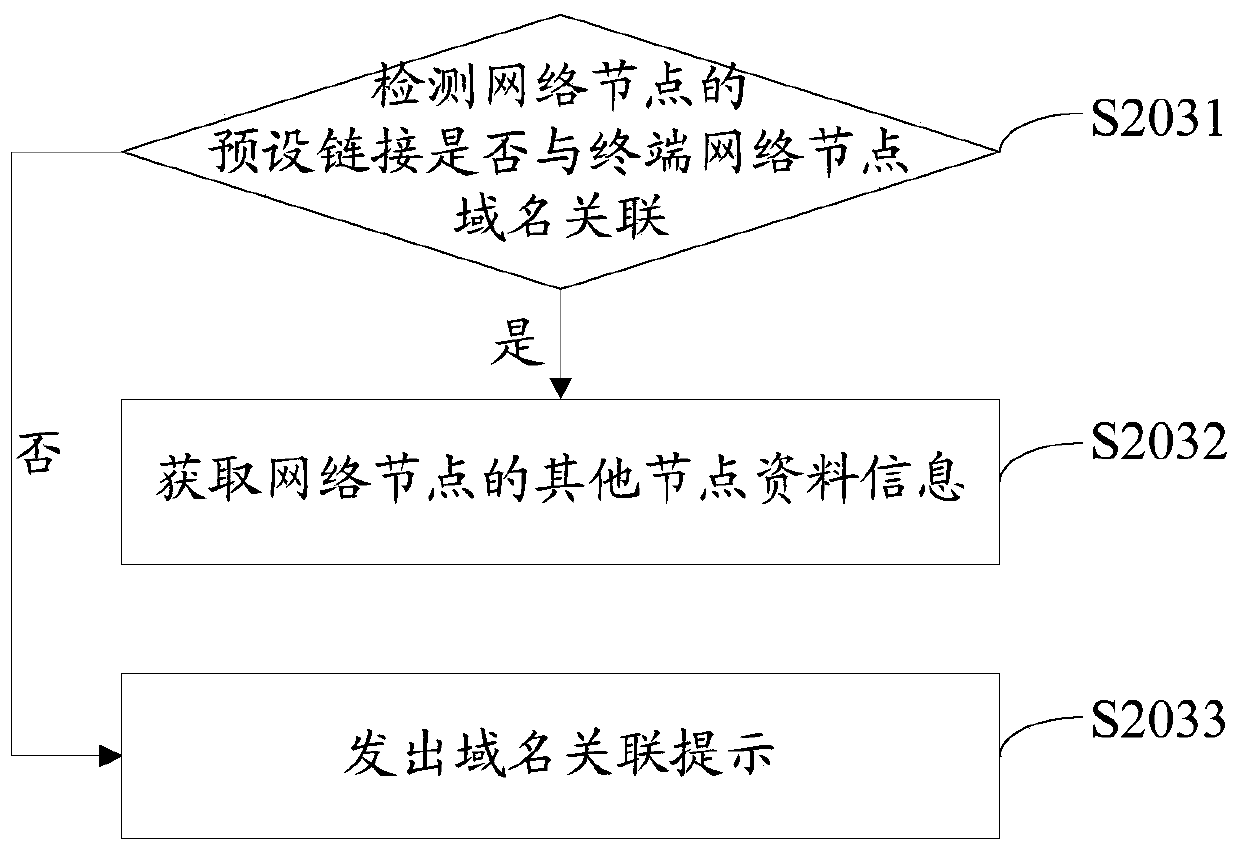
Network node encryption method and network node encryption device
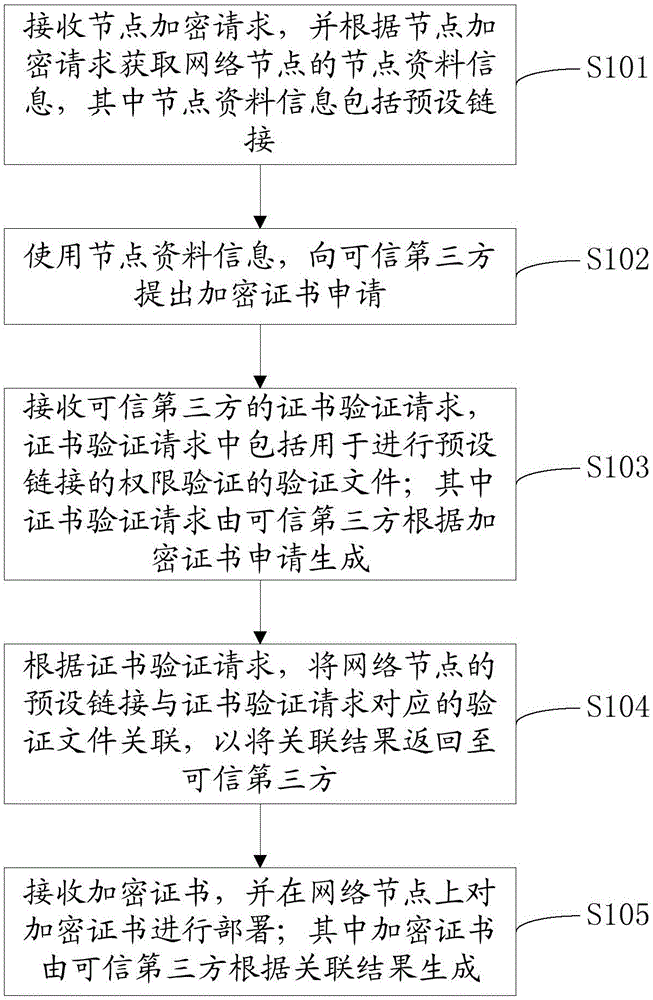
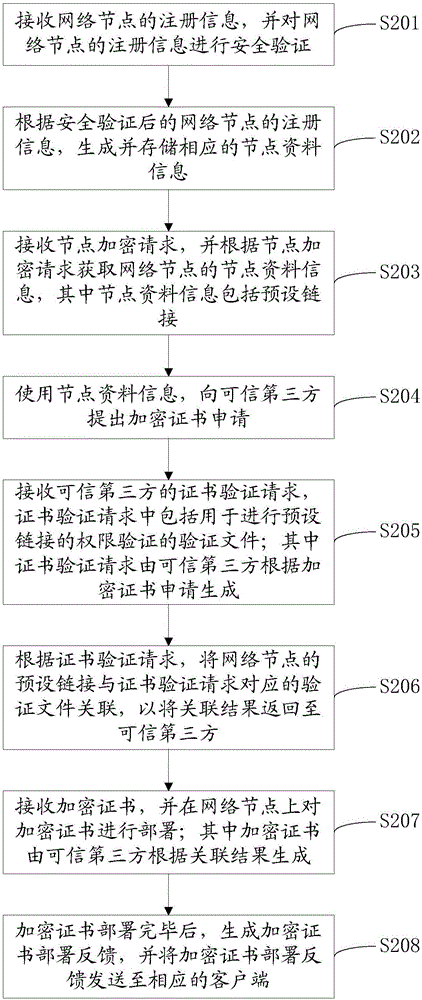
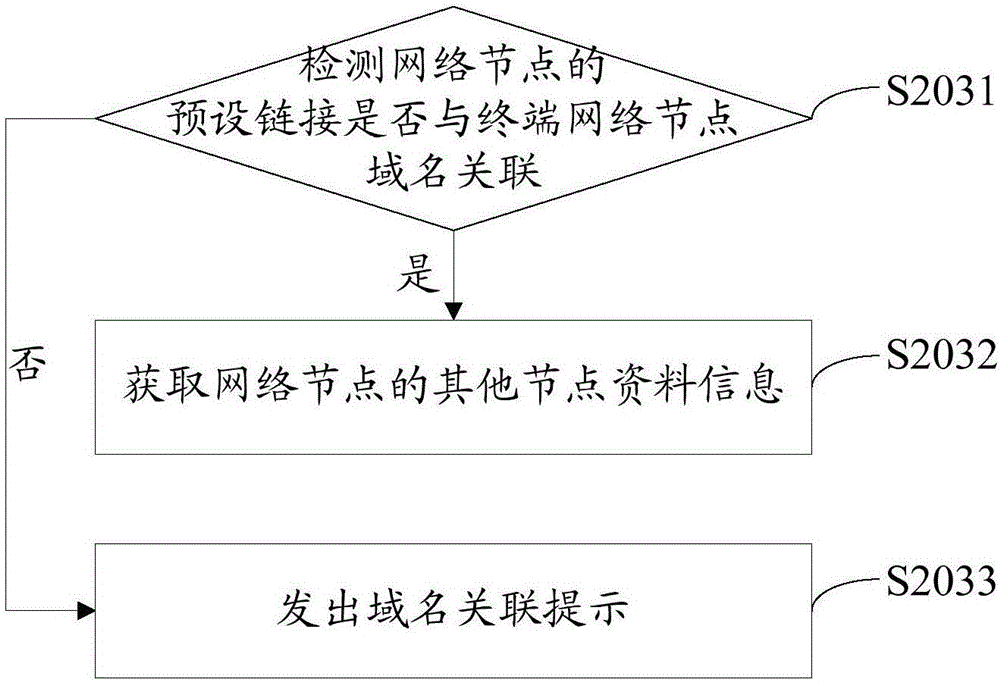
ActiveCN106302476AImprove securityTroubleshoot technical issues with poor securitySecuring communicationData informationTrusted third party
The invention provides a network node encryption method. The network node encryption method comprises the following steps: receiving a node encryption request, and obtaining node data information of a network node according to the node encryption request; using the node data information to propose an encryption certificate request for a trusted third party; receiving a certificate verification request, associating a preset link of the network node with a verification file corresponding to the certificate verification request according to the certificate verification request so as to return an association result to the trusted third party; and receiving an encryption certificate, and deploying the encryption certificate on the network node. The invention further provides a network node encryption device. By adopting the network node encryption method and the network node encryption device provided by the invention, the encryption certificate can be automatically applied for the trusted third party by using the node data information of the network node, and the network node is encrypted by using the encryption certificate, thereby avoiding the leakage of the encryption certificate and improving the security of the network node.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Electric car and control system for high voltage power supply of electric car
ActiveCN105437982ATroubleshoot technical issues with poor securityImprove securityElectric devicesVehicular energy storagePower controllerHigh voltage igbt
The invention discloses an electric car and a control system for a high voltage power supply of the electric car. The system comprises the high voltage power supply, multiple monitors, multiple position sensors and a power supply controller; the high voltage power supply is used for supplying power to multiple high voltage parts; each monitor is connected with the corresponding high voltage part and used for monitoring the connecting state of the high voltage part and a high voltage power line; each position sensor and a protective cover of the corresponding high voltage part are correspondingly arranged, and each position sensor is used for detecting the opening-closing state of the protective cover of the corresponding high voltage part; the power supply controller is used for starting the power supply function of the high voltage power supply when all the high voltage parts are connected with the high voltage power line and the protective covers of all the high voltage parts are closed. According to the electric car and the control system for the high voltage power supply of the electric car, the technical problem that in a related technique, the electric car safety is poor due to a high voltage system fault is solved.
Owner:BEIJING ELECTRIC VEHICLE
Composite bathtub
The technical proposal of the invention discloses a composite bathtub and a manufacture process thereof, and relates to the manufacture of the bathtub. The composite bathtub mainly comprises a flexible material shell, a shell, and a foamed polyurethane flexible material layer and a fiber bonding layer which are positioned between the flexible material shell and the shell as filling layers, wherein the flexible material shell is bonded to the foamed polyurethane flexible material layer and combined with the shell into a whole through the foamed polyurethane flexible material layer and the fiber bonding layer. The manufacture process for the bathtub is mainly characterized in that a mould for an inner shell of the bathtub is a mould for manufacturing the flexible material shell, and is an upper mould and a lower mould capable of absorbing the material of the flexible material shell; and in the flow of forming the bathtub, a polyurethane liquid is injected into an outer shell of the bathtub firstly, and then the upper mould absorbing flexible plates of the flexible material shell is placed into the outer shell of the bathtub, and the polyurethane liquid is foamed to become the foamed polyurethane flexible material layer. The product manufactured by the invention is flexible and full of elasticity, and improves the bathing comfort and using safety.
Owner:宣城市银河洁具有限责任公司
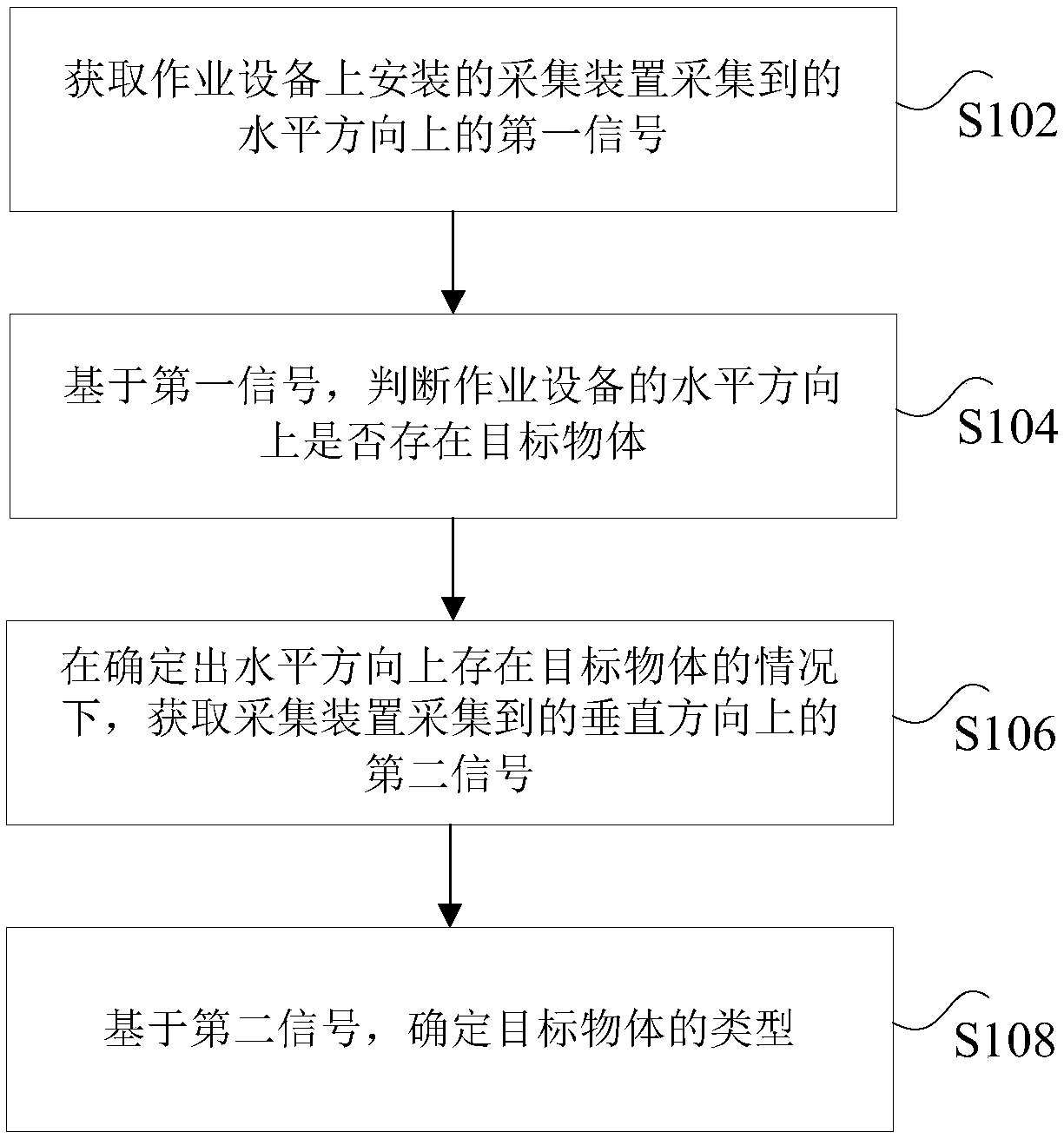
Target object recognition method and device and operation equipment
The invention discloses a target object recognition method and device and operation equipment. The method comprises the following steps of acquiring a first signal in a horizontal direction collectedby an acquisition device installed on the operation equipment; judging whether a target object exists in the horizontal direction of the operation equipment based on the first signal; when it is determined that the target object exists in the horizontal direction, acquiring a second signal in a vertical direction acquired by the acquisition device; and based on the second signal, determining the type of the target object. According to the target object recognition method and device and operation equipment, the technical problem that the target object in the advancing direction of the operatingequipment cannot be recognized in the related technology, so that the safety of the operating equipment is poor is solved.
Owner:GUANGZHOU XAIRCRAFT TECH CO LTD
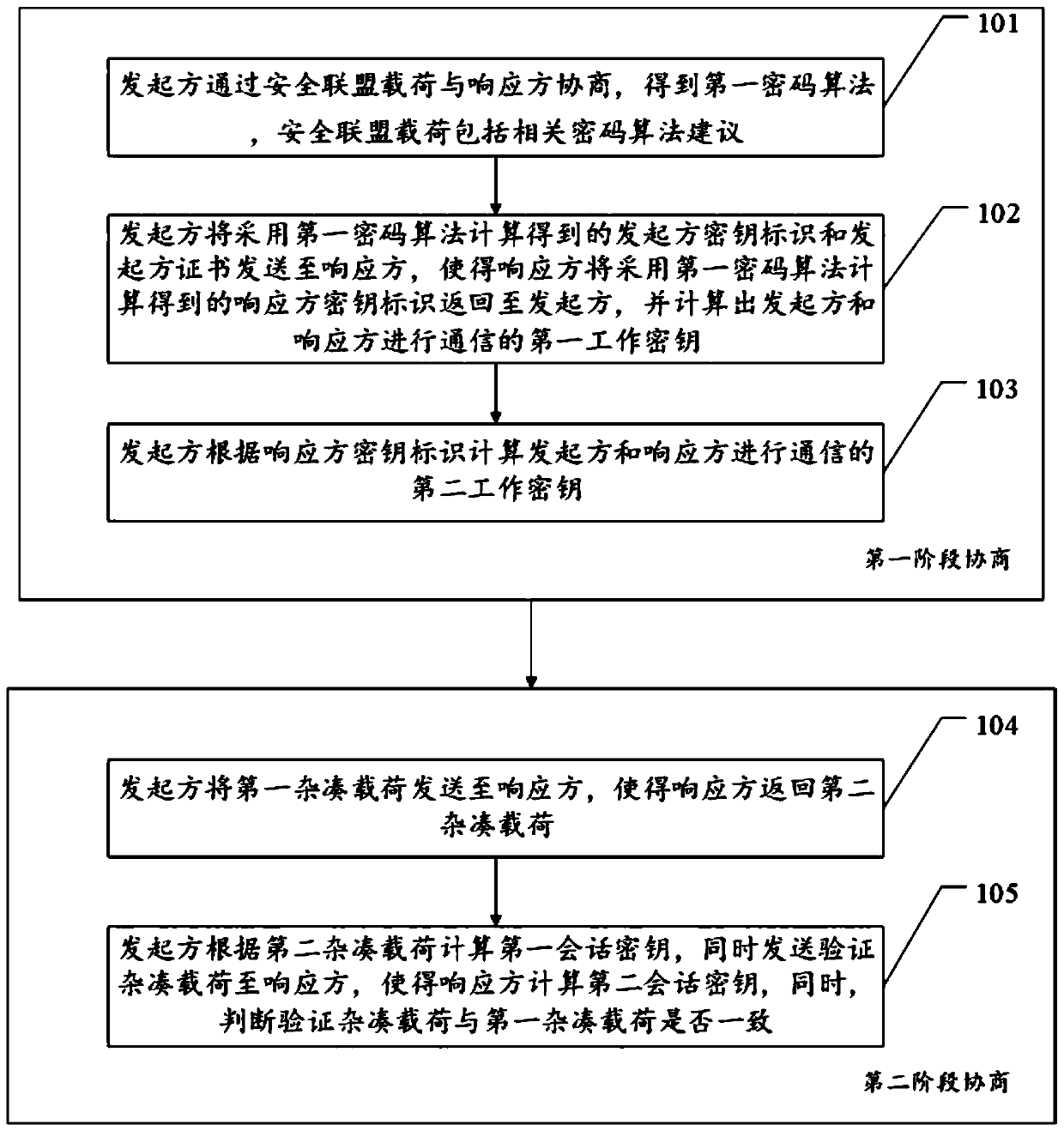
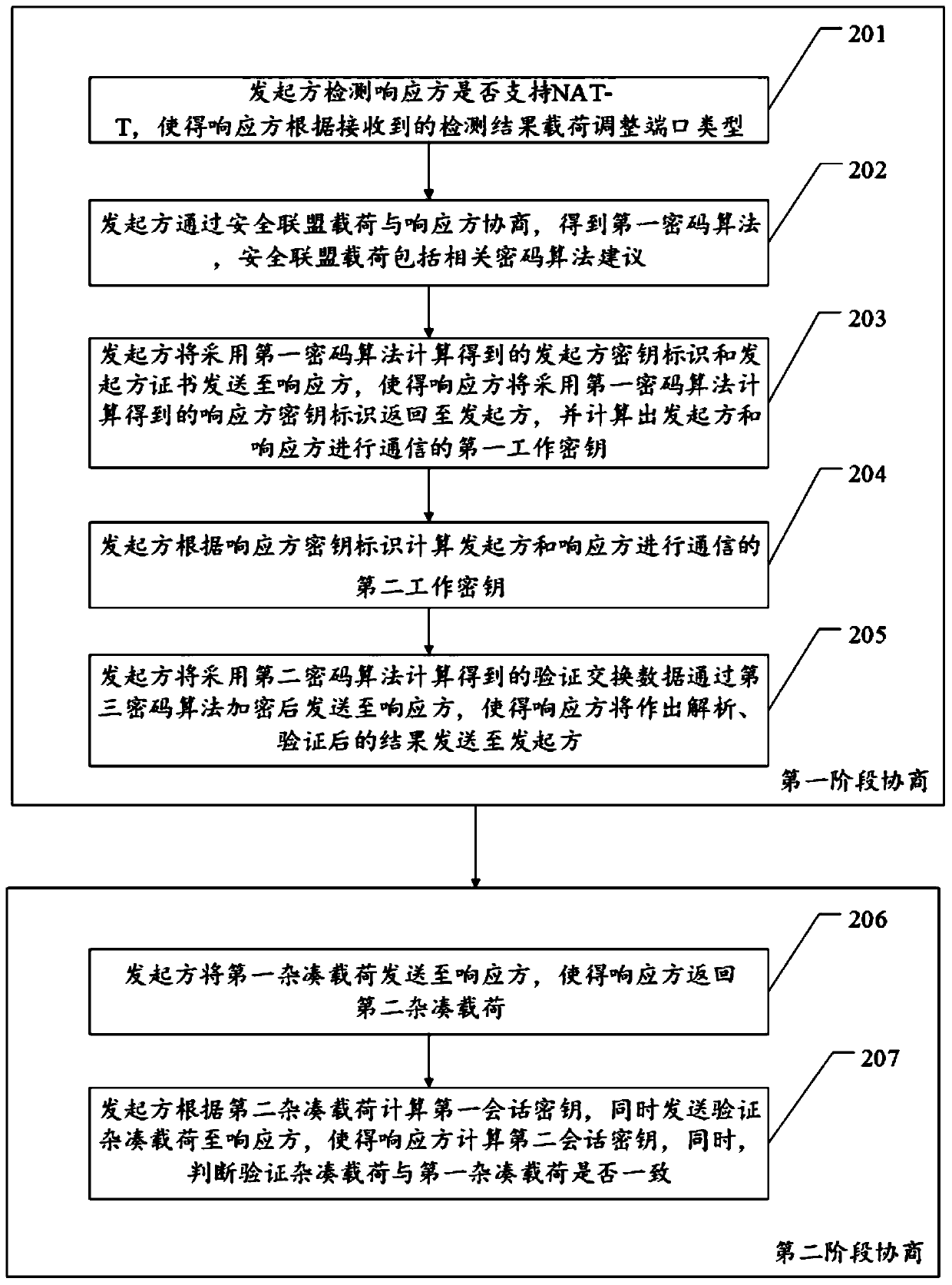
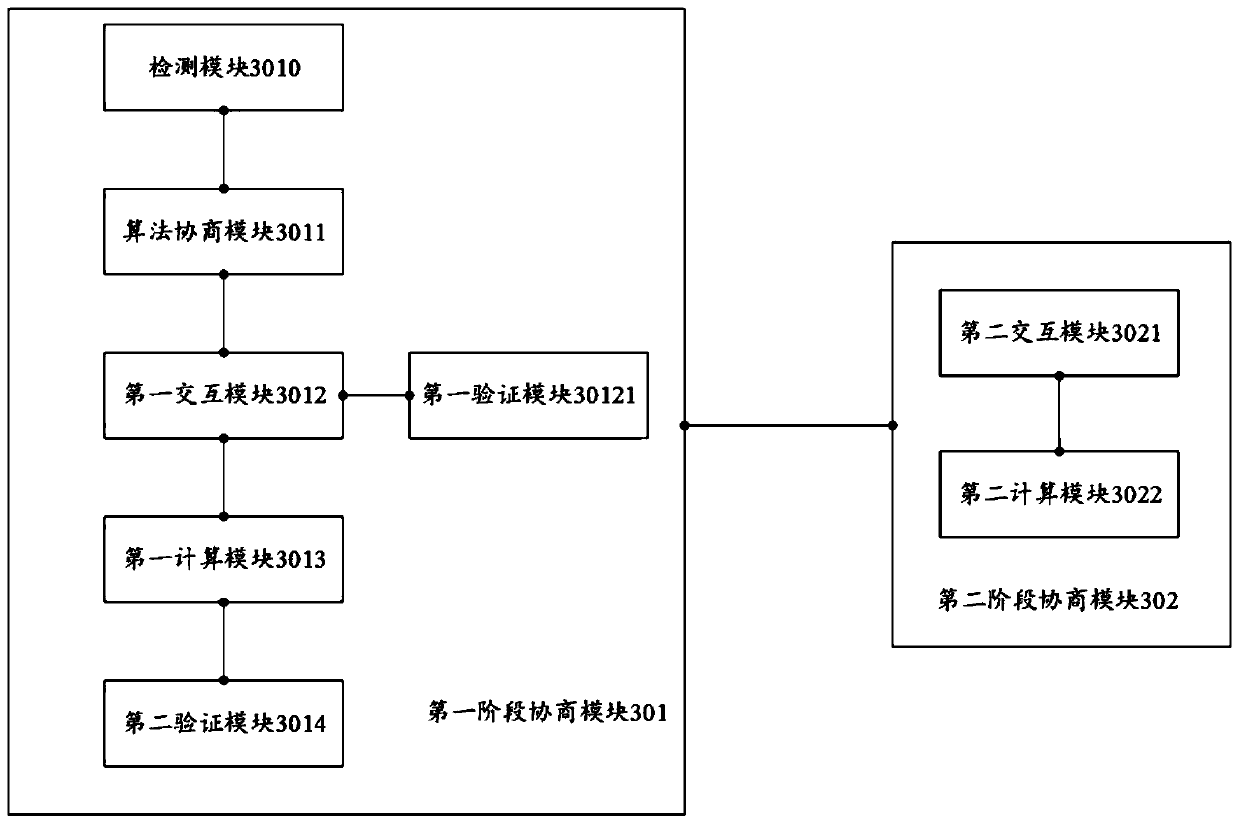
Key negotiation method, device and equipment
PendingCN111130775ASimplify the interaction processEnsure safetyKey distribution for secure communicationUser identity/authority verificationComputer networkEngineering
The invention discloses a key negotiation method, device and equipment. The method comprises first-stage negotiation and second-stage negotiation; in the first-stage negotiation, an initiator negotiates with a responder through a security alliance load to obtain a first cryptographic algorithm, and then, the initiator and the responder obtain a working key for communication between the initiator and the responder by adopting a first cryptographic algorithm and interaction between the initiator and the responder; in the second-stage negotiation, the initiator sends a first hash load to the responder, so that the responder returns a second hash load, and the initiator calculates the first session key according to the second hash load and sends a verification hash load to the responder, so that the responder calculates the second session key and judges whether the verification hash load is consistent with the first hash load or not. According to the method and the device, the technical problems of relatively long negotiation time and relatively poor security between two communication parties due to a complex key calculation process in the prior art are solved.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
Positive electrode material, positive electrode, preparation method of positive electrode, and lithium secondary battery
InactiveCN112331843AImprove ionic conductivityImprove the impact resistance of heavy objectsPositive electrodesSecondary cells servicing/maintenanceElectro conductivityALUMINUM PHOSPHATE
The invention belongs to the technical field of lithium secondary battery positive electrode materials, and particularly relates to a positive electrode material, a positive electrode, a preparation method of the positive electrode, and a lithium secondary battery. According to the positive electrode material disclosed by the invention, lithium titanium aluminum phosphate and / or doped lithium titanium aluminum phosphate are / is used as the additive, so that the weight impact resistance of the lithium secondary battery can be remarkably improved, the ionic conductivity of the positive electrodematerial can be improved, the impedance and the temperature rise are reduced, and the cycle life of the lithium secondary battery is further prolonged.
Owner:DONGGUAN CHUANGMING BATTERY TECH
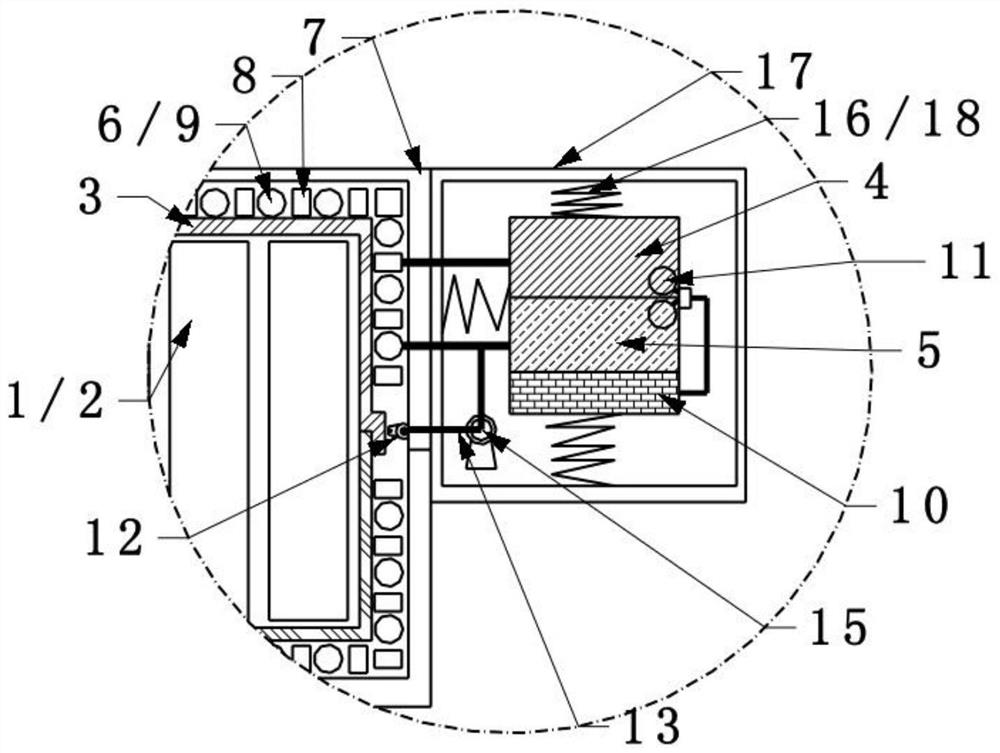
Explosion door
ActiveCN111877946ATroubleshoot technical issues with poor securityPromote escapeBuilding locksWar-like protectionGear driveGear wheel
The invention provides an explosion door in the technical field of explosion doors. The explosion door comprises a door frame, a door body is hinged to the door frame, a plurality of lock holes are formed in the door frame, a plurality of telescopic lock heads capable of being inserted into the lock holes are arranged on the door body, a transmission gear is mounted in the door body and is in transmission connection with the telescopic lock heads, and a first circular through hole and a second circular through hole are formed in the door body; a first internal thread is arranged on the first circular through hole, a first circular plate is connected into the first circular through hole, a first external thread matched with the first internal thread is arranged on the first circular plate,the center of the first circular plate is connected with one end of a fixing shaft, the other end of the fixing shaft is connected with a second circular plate, a bearing is installed on the fixing shaft, and a first gear sleeves the outer ring of the bearing; and the two sides of the first gear are each provided with a second gear, the first circular plate and the second circular plate are each provided with a rotatable driving rod, and the ends, stretching into the door body, of the driving rods are each connected with a third gear. By means of the explosion door, escape is facilitated, andsafety is high.
Owner:JIANGSU JIANWEI PROTECTION ENG TECH CO LTD
Data transmission method and device, storage medium and electronic device
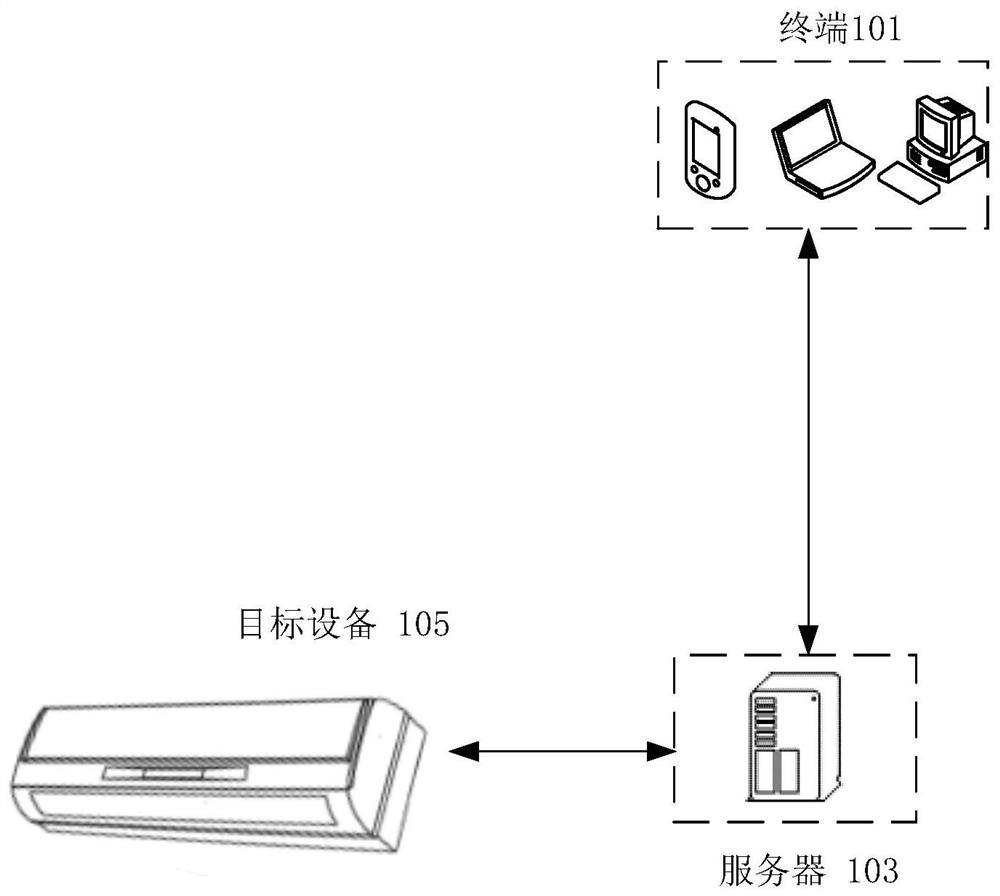
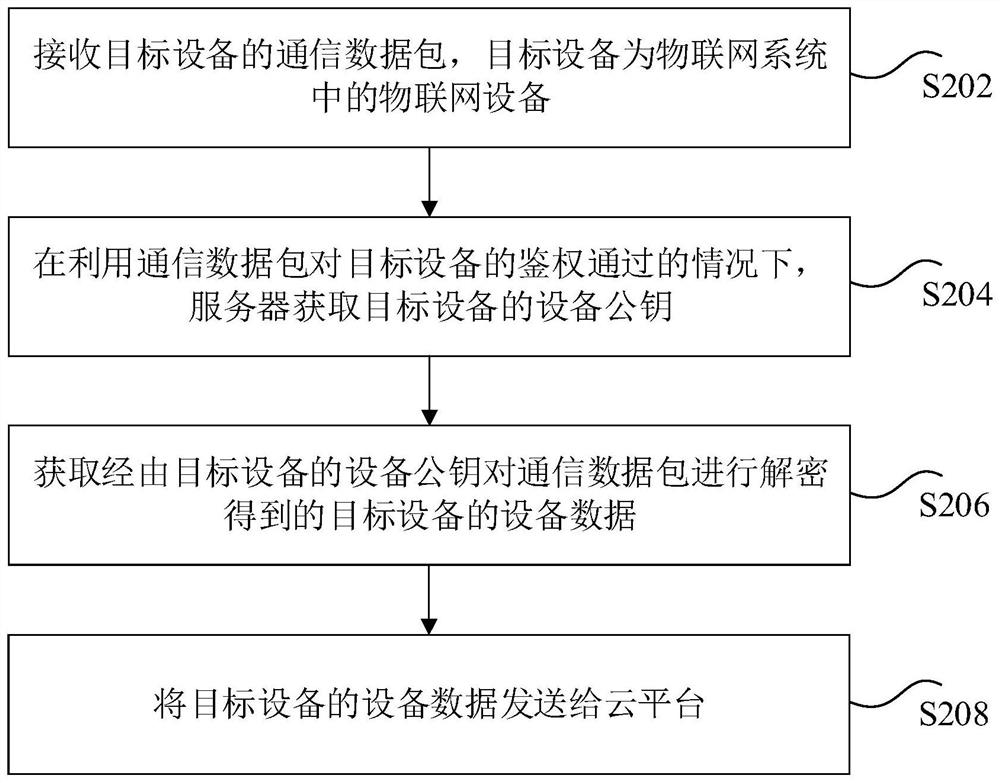
ActiveCN113114665ATroubleshoot technical issues with poor securityPrevent intrusionTransmissionInstrumentsData packThe Internet
The invention discloses a data transmission method and device, a storage medium and an electronic device. The method comprises: receiving a communication data packet of a target device, wherein the target device is an Internet of Things device in an Internet of Things system, the communication data packet is a data packet sent to a cloud platform in the Internet of Things system, and the cloud platform is used by a user terminal to call the Internet of Things device; acquiring a device public key of the target device under the condition that the authentication of the target device by using the communication data packet is passed; acquiring device data of the target device obtained by decrypting the communication data packet through the device public key of the target device; and sending the device data of the target device to the cloud platform. The technical problem that the security of the Internet of Things system in the related technology is poor is solved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD
Smart home protection system and protection method thereof
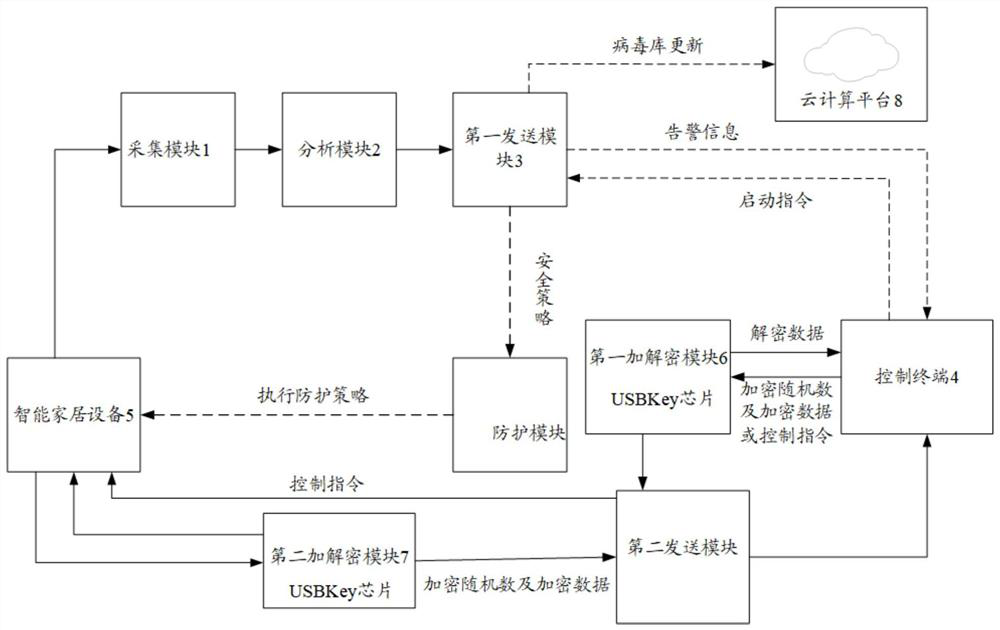
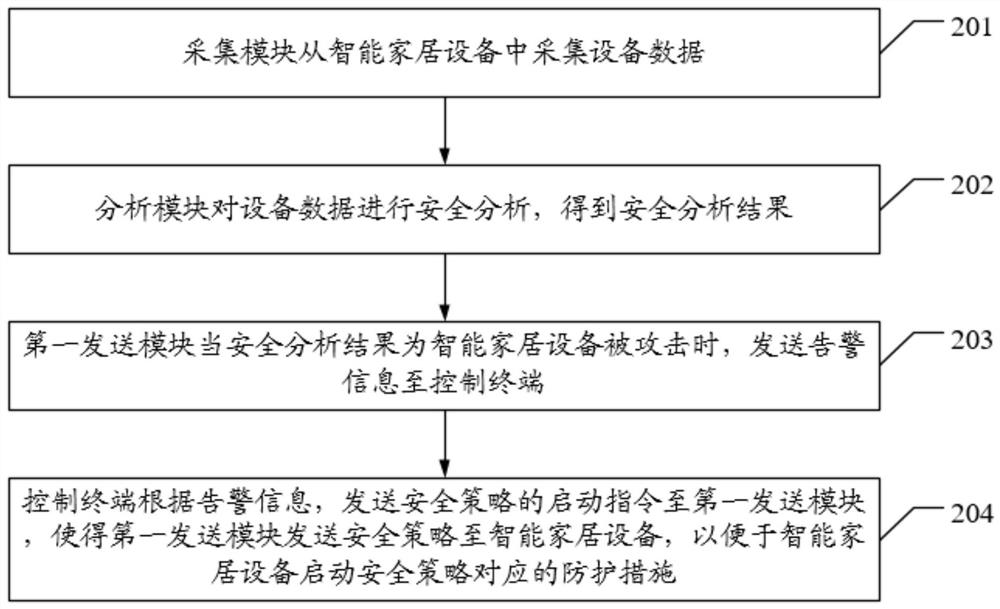
PendingCN112073422AAddress poor securityImprove the protective effectUser identity/authority verificationHome automation networksEmbedded systemAcquisition apparatus
The invention discloses a smart home protection system and a protection method thereof, and the protection system comprises an acquisition module, an analysis module, a first sending module, and a control terminal. The acquisition module is connected with smart home equipment and is used for acquiring equipment data from the smart home equipment; the analysis module is used for performing safety analysis on the equipment data to obtain a safety analysis result; the first sending module is used for sending alarm information to the control terminal when the safety analysis result shows that thesmart home equipment is attacked; and the control terminal is used for sending a starting instruction of the security policy to the first sending module according to the alarm information, so that thefirst sending module sends the security policy to the smart home device, the smart home device starts a protection measure corresponding to the security policy, and the technical problem of poor security of an existing smart home protection system is solved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
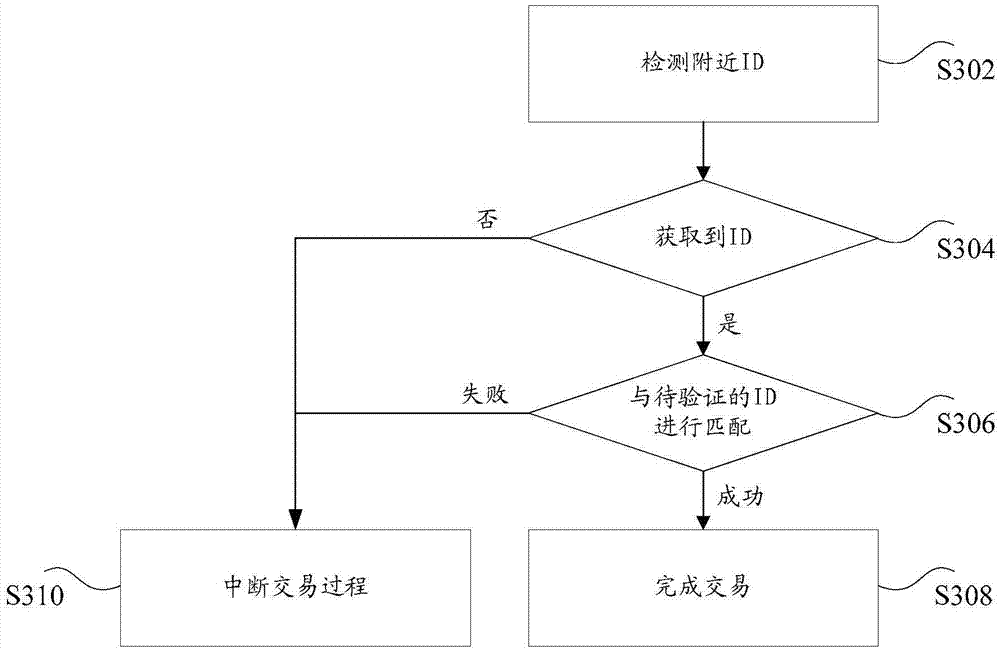
Safety processing method, device and system for virtual resources
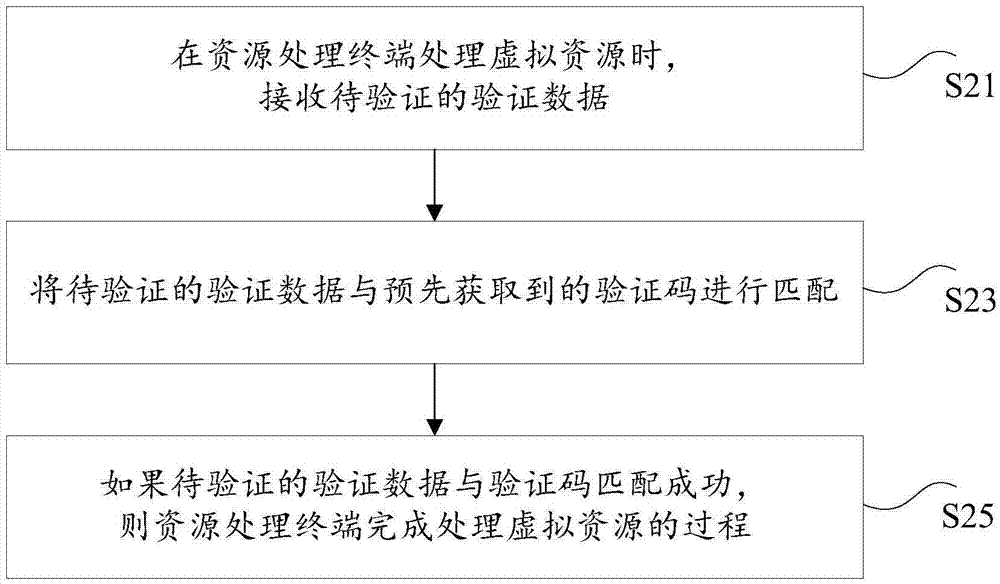
ActiveCN106921498AImprove securityWithout compromising convenienceUser identity/authority verificationComputer terminalSafe handling
The invention discloses a safety processing method, device and system for virtual resources. The method comprises the steps of: when processing the virtual resources at a resource processing terminal, receiving verification data to be verified; carrying out matching on the verification data to be verified and a verification code acquired in advance, wherein the resource processing terminal acquires the verification code from a verification code generation terminal communicated with the resource processing terminal; and if the verification data to be verified is successfully matched with the verification code, by the resource processing terminal, completing a process of processing the virtual resources. The safety processing method, device and system disclosed by the invention solve the technical problem of poor safety of the process of processing the virtual resources, which is caused by network vulnerability, hacker intrusion and the like in the processing process that the terminal processes the virtual resources in the prior art.
Owner:TENCENT TECH (SHENZHEN) CO LTD
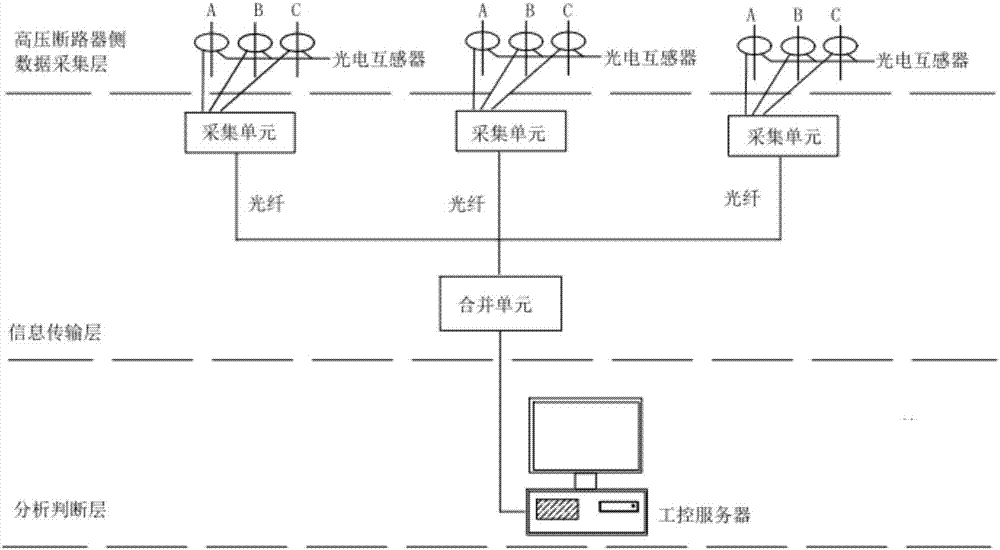
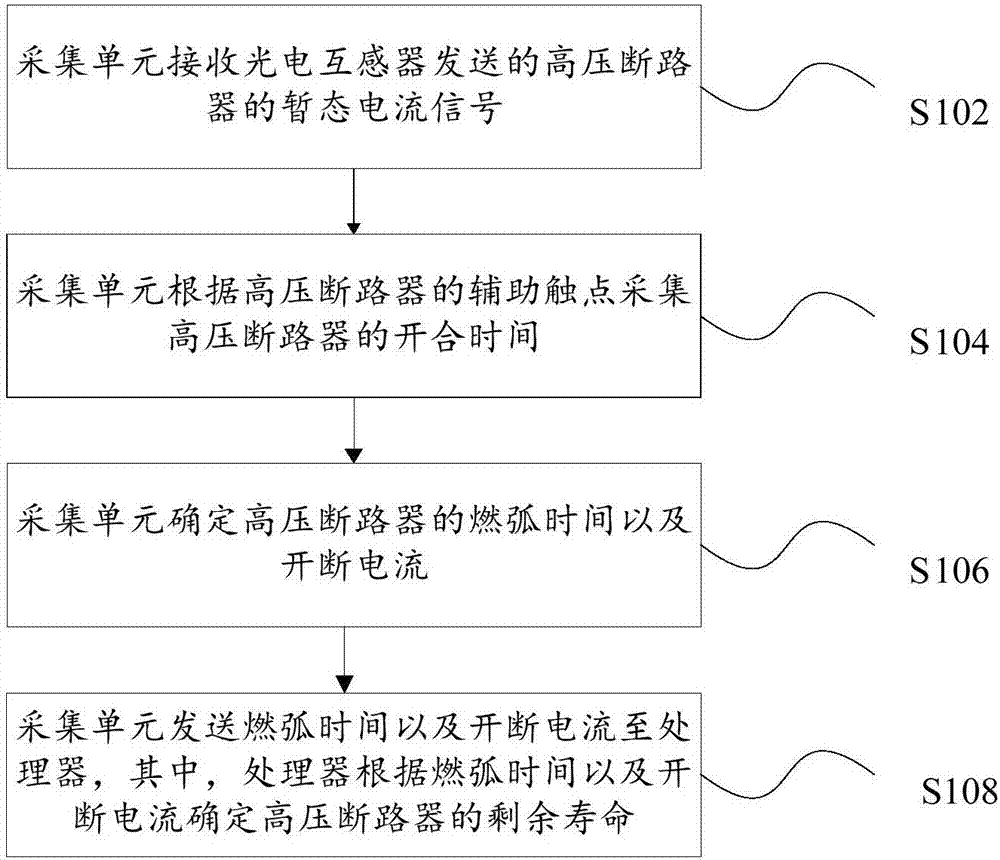
System, method and device for obtaining residual service life of high-voltage circuit breaker
InactiveCN106980085AImprove grid securityImprove securityCircuit interrupters testingInductorPower grid
The invention discloses a system, method and device for obtaining the residual service life of a high-voltage circuit breaker. The system comprises a photoelectric mutual inductor which is used for collecting a transient current signal passing through a high-voltage circuit breaker; a collection unit which is connected with the photoelectric mutual inductor and is used for obtaining the arcing time of the high-voltage circuit breaker and determining the switching-off current of the high-voltage circuit breaker according to the transient current signal; a processor which is connected with the collection unit, and is used for determining the residual service life of the high-voltage circuit breaker according to the switching-off current and the arcing time. The system solves a technical problem of poor safety of a power grid because the residual service life of the high-voltage circuit breaker cannot be obtained accurately.
Owner:ZHUHAI YINENG ELECTRONICS TECH
High-safety automobile built-in panoramic rearview system
InactiveCN112265502AImprove securityTroubleshoot technical issues with poor securityClosed circuit television systemsOptical viewingFenderComputer graphics (images)
The invention discloses a high-safety automobile built-in panoramic rearview system, and relates to the technical field of automobile accessories, the high-safety automobile built-in panoramic rearview system comprises a camera and a display screen, the camera is installed on an automobile and can collect images, the display screen can display the images, and the camera is electrically connected with the display screen through digital signals, the system further comprises a fender mirror outlet, a display screen mirror surface switching device, a display screen displacement positioning device,a display amplifying device, a display screen angle adjusting device, a magnifying lens angle adjusting device, an independent power supply and a control unit. By arranging the camera on the outer side of the vehicle body and arranging the three display screens in the vehicle, visualization of the blind area of the vehicle is achieved, the display screen mirror surface switching devices are arranged on the display screens, and the display areas of the display screens are converted into mirror surfaces through the display screen mirror surface switching devices when imaging of the display screens fails. Meanwhile, two of the display screens extend out of the automobile body through the display screen displacement positioning device, so that the display screens are used as rearview mirrors.
Owner:张启斌
Key negotiation method, apparatus, and system
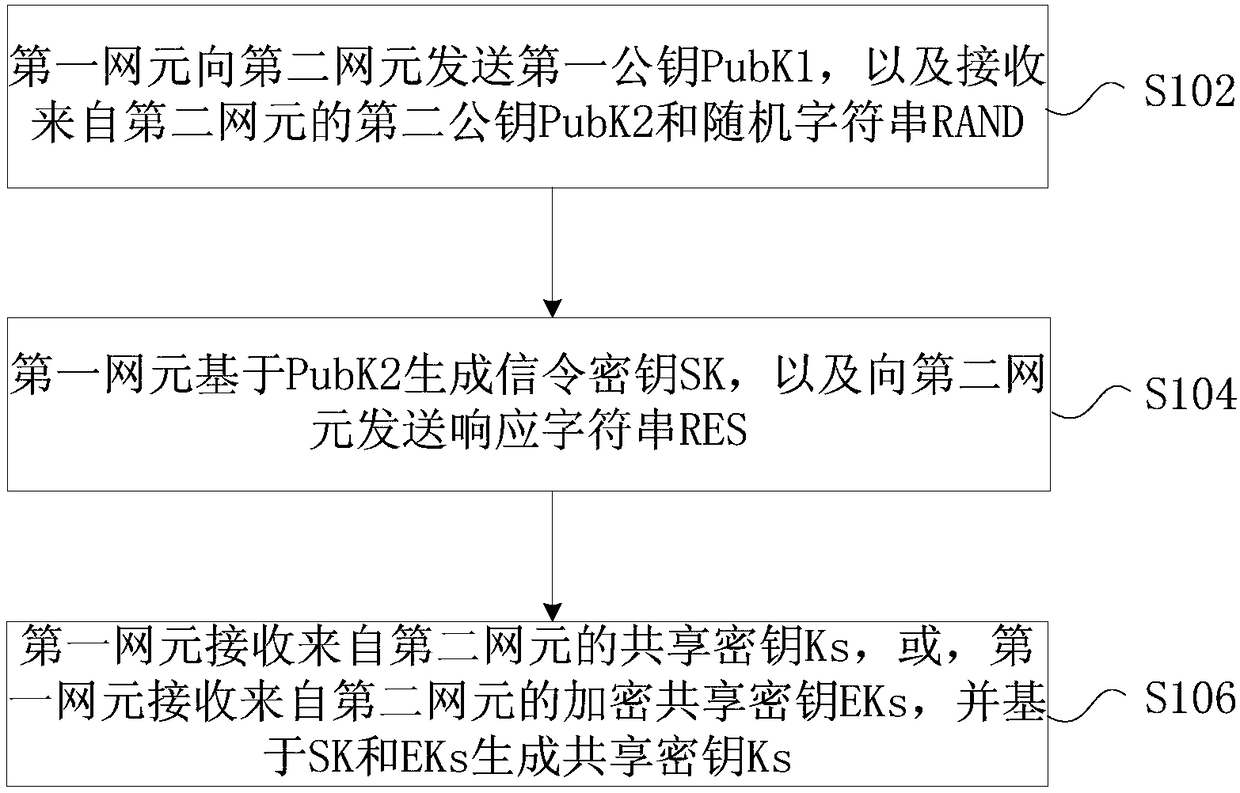
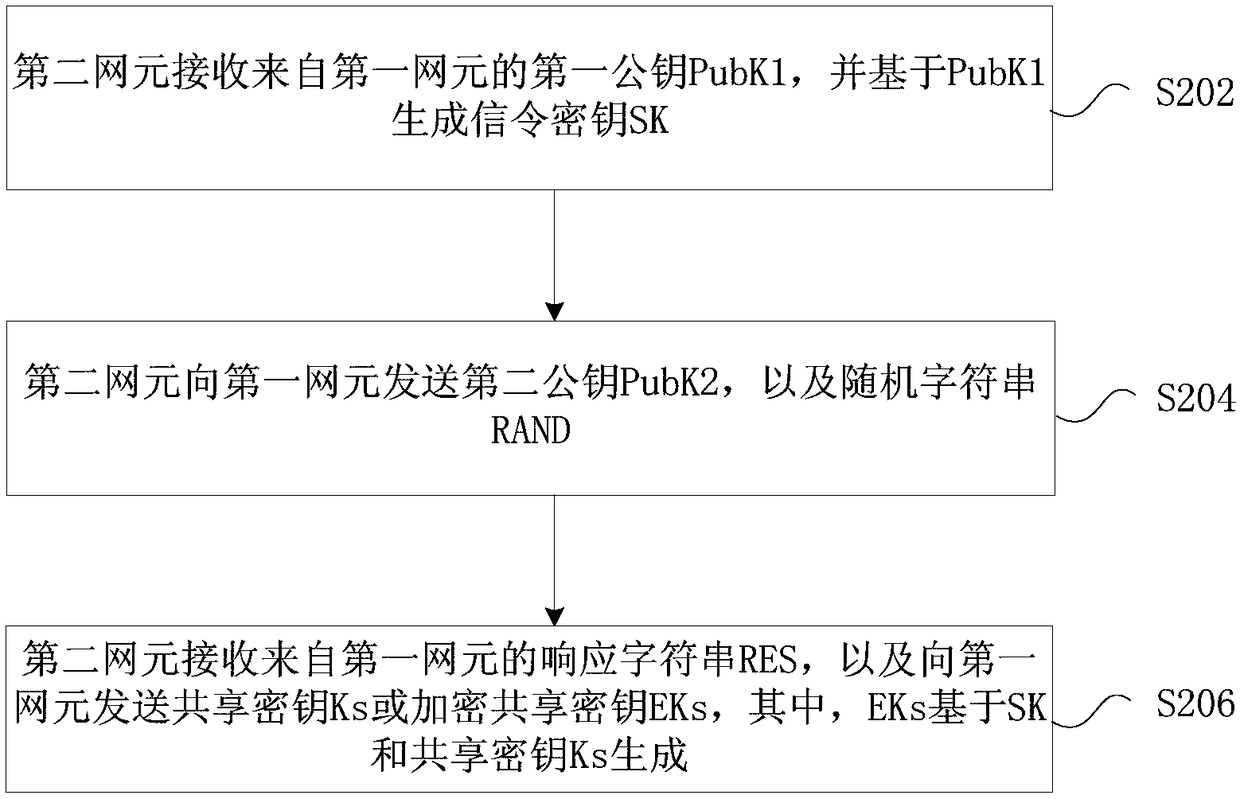
InactiveCN109391938ATroubleshoot technical issues with poor securityReduce the possibility of disclosureKey distribution for secure communicationSecurity arrangementPlaintextComputer security
The invention provides a key negotiation method, apparatus, and system. According to one embodiment, the method comprises the following steps that: a first network element sends a first public key PubK1 to a second network element and receives second public key PubK2 and a random character string RAND from a second network element; the first network element generates a signaling key SK based on the PubK2 and sends a response character string RES to the second network element; and the first network element receives a shared key Ks from the second network element or the first network element receives an encrypted shared key EKs from the second network element and generates a shared key Ks based on the SK and the EKs. Therefore, a technical problem that the key safety is poor because of key transmission based on a plaintext according to the related technique is solved.
Owner:ZTE CORP
Authentication server, card authentication system, password-free authentication method and password-free authentication system
PendingCN113347179ATroubleshoot technical issues with poor securityTransmissionInternet privacyPassword
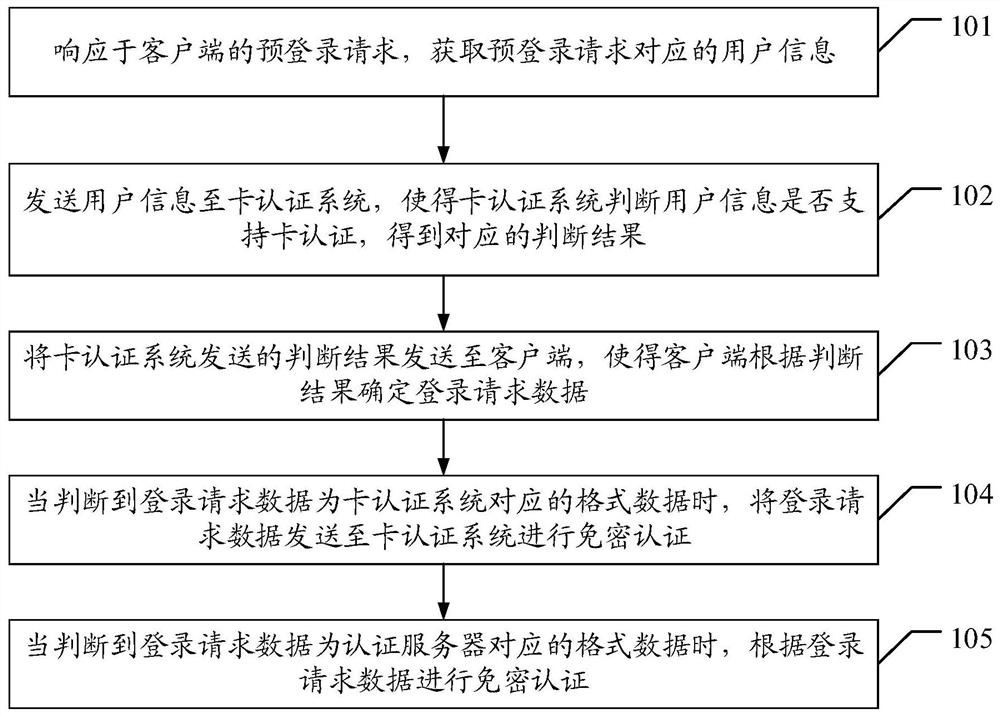
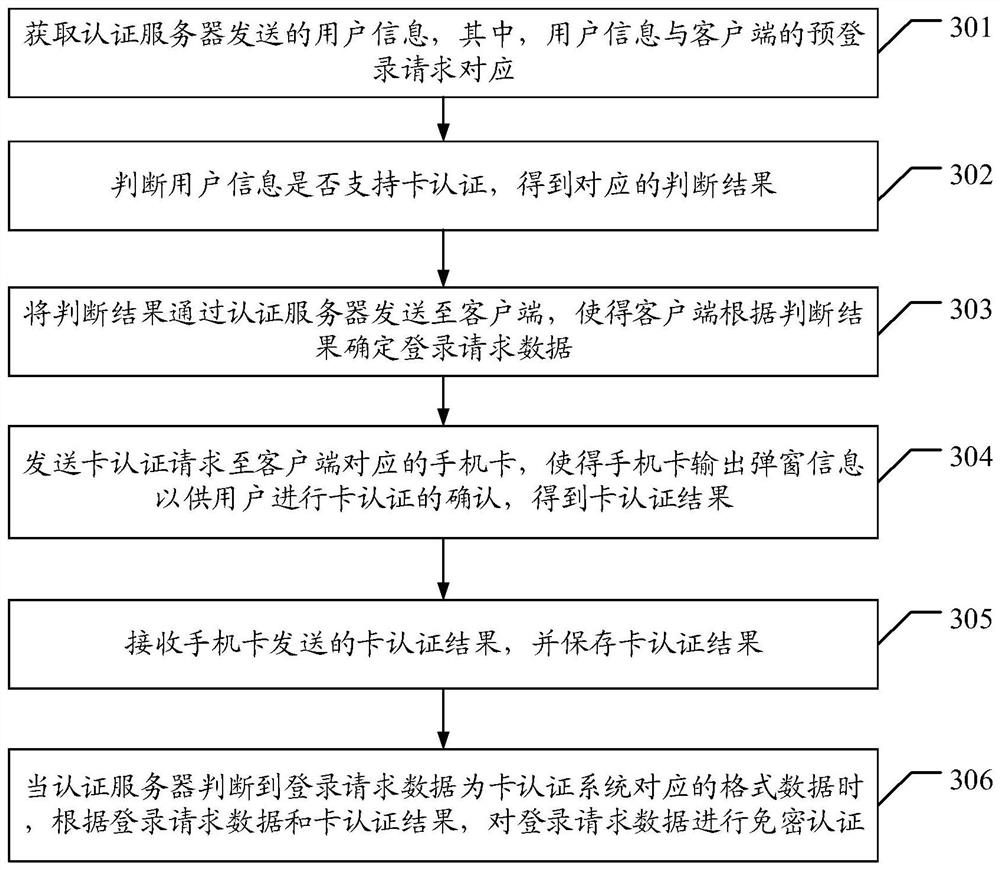
The invention discloses an authentication server, a card authentication system and a password-free authentication method and system. The password-free authentication method applied to the authentication server comprises the steps: in response to a pre-login request of a client, acquiring the user information corresponding to the pre-login request; sending the user information to a card authentication system, so the card authentication system judges whether the user information supports card authentication or not, and a corresponding judgment result is obtained; sending a judgment result sent by the card authentication system to the client, so the client determines login request data according to the judgment result; and when it is judged that the login request data is format data corresponding to the card authentication system, sending the login request data to the card authentication system for password-free authentication. The technical problem that in the prior art, a password-free authentication method is poor in safety is partially solved.
Owner:E-SURFING DIGITAL LIFE TECH CO LTD
High-safety electric vehicle
PendingCN112519582AReduce fire riskAddress poor securityElectric devicesCell component detailsAutomotive engineeringElectrical battery
The invention discloses a high-safety electric vehicle which comprises a vehicle body and a battery pack. The battery pack comprises a battery unit and a battery pack shell; the high-safety electric vehicle further comprises a polyurethane bin, a carbon dioxide bin, a brittle pipe and a shell. The polyurethane bin is filled with flame-retardant polyurethane; the carbon dioxide bin is filled with liquid carbon dioxide; the shell is sleeved on the battery pack shell; the brittle pipes are made of hard plastic, are densely distributed between the battery pack shell and the shell and are fixedly connected to the battery pack shell and the shell; the brittle pipes comprise a first brittle pipe and a second brittle pipe; one end of the first brittle pipe is closed, and the other end communicateswith the polyurethane bin; one end of the second brittle pipe is closed, and the other end is communicated with the carbon dioxide bin; when the battery pack shell is damaged and cracks occur in thebattery pack shell during collision of the electric vehicle, the brittle pipes at the cracks are broken at the same time, the flame-retardant polyurethane and the carbon dioxide are sprayed out from the broken positions of the brittle pipes to seal the cracks, and oxygen is prevented from entering to reduce the spontaneous combustion risk of batteries.
Owner:JIANGSU JINPENG VEHICLE CO LTD
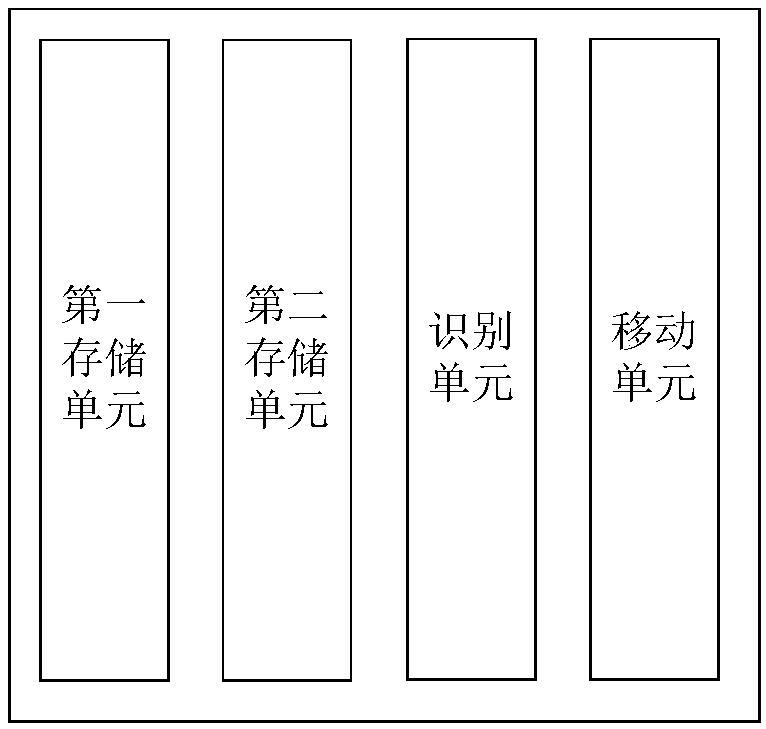
Distribution box intelligent management system
InactiveCN110503280AReasonable system designSecurityResourcesInformation technology support systemFingerprintEngineering
The invention discloses a power distribution box intelligent management system, comprising a first storage unit which is used for the protection storage of a power distribution box, and the power distribution box is stored in the first storage unit when the power distribution box is not operated, a second storage unit which is used for carrying out operation processing on the distribution box, a recognition unit which is used for carrying out face or fingerprint recognition on an operator of the distribution box, and a moving unit for moving the distribution box from the first storage unit tothe second storage unit, wherein when recognition fails, the distribution box is stored in the first recognition unit, and when recognition succeeds, the distribution box is moved to the second storage unit. The power distribution box intelligent management system solves the technical problem that an existing distribution box is poor in safety, achieves the technical effects that the system designis reasonable, and guarantees the safety of the distribution box.
Owner:黄琳
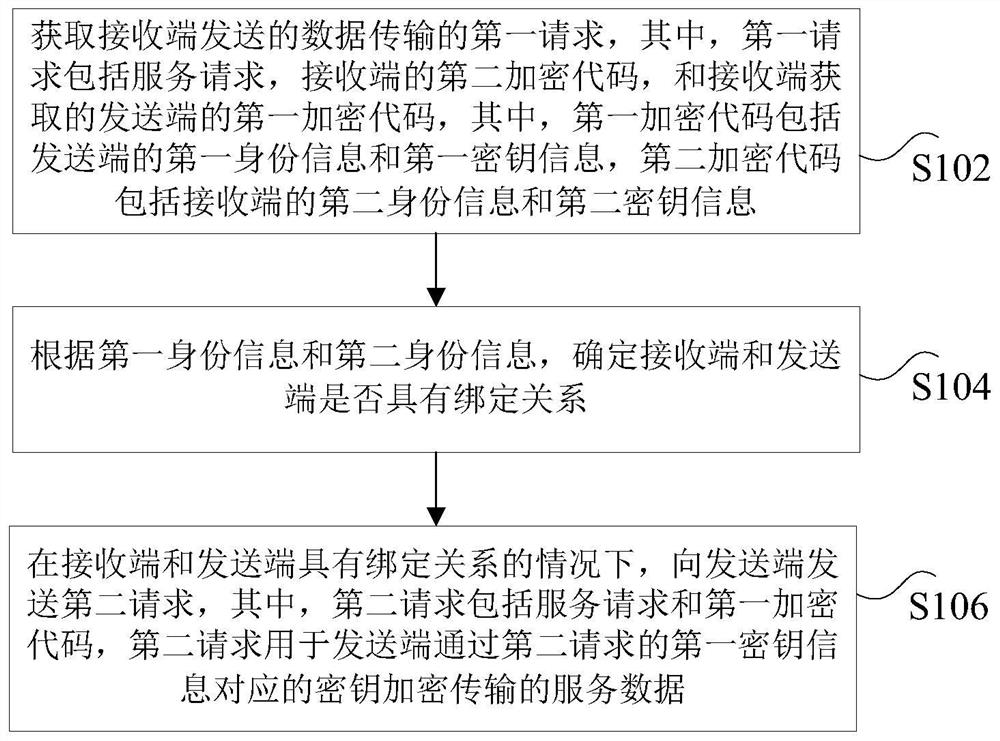
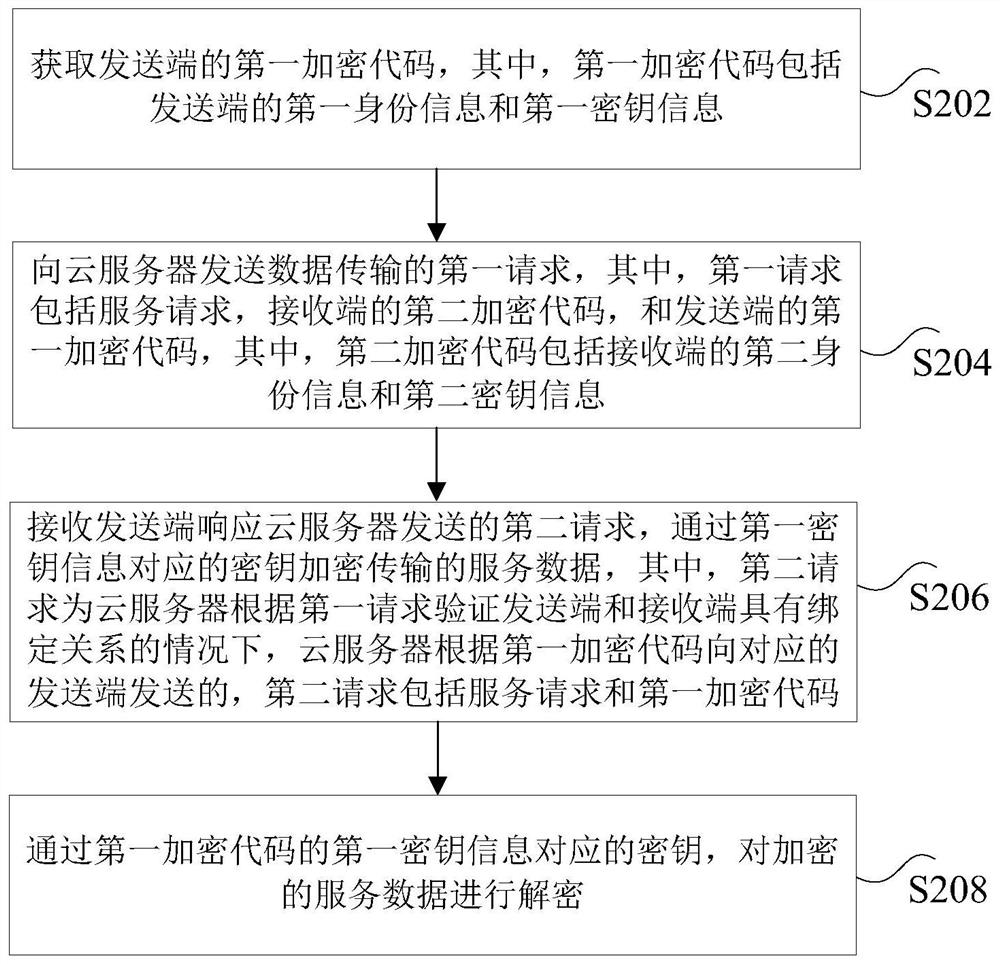
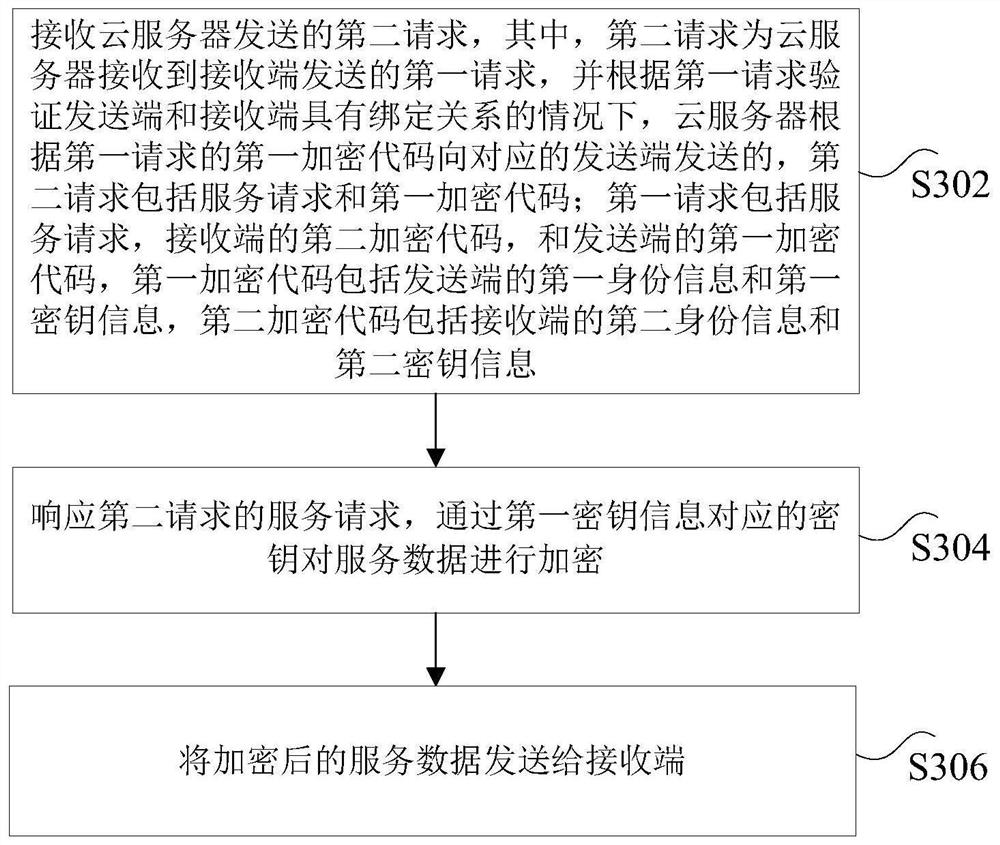
Data transmission method, cloud server, receiving end and sending end
ActiveCN112769783AImprove securityTroubleshoot technical issues with poor securityTransmissionData transmissionEncryption
The invention discloses a data transmission method, a cloud server, a receiving end and a sending end. The method comprises the steps: acquiring a first request, sent by a receiving end, of data transmission, wherein the first request comprises a service request, a second encryption code of the receiving end and a first encryption code of a sending end, the first encryption code comprises first identity information and first secret key information, and the second encryption code comprises second identity information and second secret key information; according to the first identity information and the second identity information, determining whether the receiving end and the sending end have a binding relationship; under the condition that the receiving end and the sending end have the binding relationship, sending a second request to the sending end, wherein the second request comprises the service request and the first encryption code, and the second request is used for the sending end to encrypt the transmitted service data through a key corresponding to the first key information of the second request. According to the invention, the technical problem of poor data transmission security caused by easy interception of a data transmission method in the prior art is solved.
Owner:XIAN WANXIANG ELECTRONICS TECH CO LTD
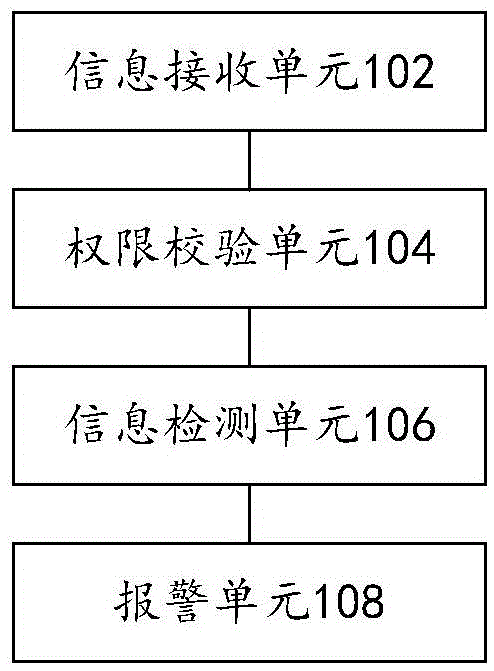
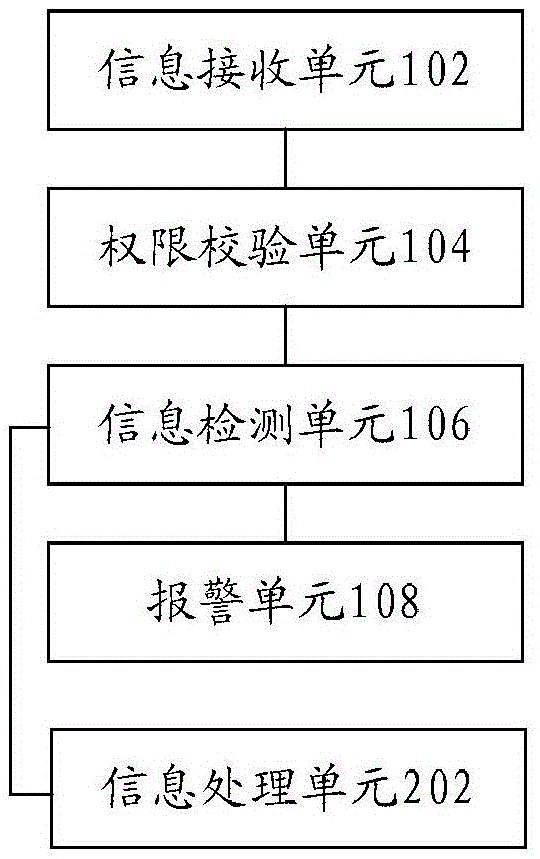
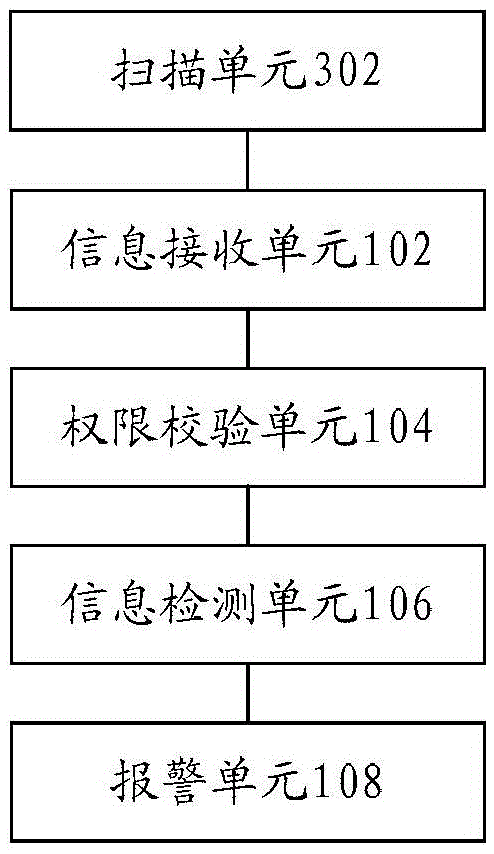
Information security detection method and system
InactiveCN105488430ATo achieve the purpose of security protectionImprove securityDigital data protectionDigital data authenticationSystem safetyManagement system
The invention discloses an information security detection method and system. The system comprises an information receiving unit, a permission checkout unit, an information detection unit and an alarming unit, wherein the information receiving unit is used for receiving information to be detected, wherein the information to be detected comprises identity information and operation information; the permission checkout unit is used for detecting whether the identity information has a permission corresponding to the operation information, transmitting the information to be detected to the information detection unit under a situation that the identity information has the permission, and sending a first alarming instruction which contains the identity information to the alarming unit under the situation that the identity information does not have the permission; the information detection unit is used for detecting whether the occurrence frequency of the operation information exceeds a preset threshold value or not, and sending a second alarming instruction which contains the operation information to the alarming unit under the condition that the occurrence frequency exceeds the preset threshold value; and the alarming unit is used for giving an alarm on the basis of the first alarming instruction or the second alarming instruction. The technical problem of poor system security since no security protection technologies which aim at a management system are in the presence in the prior art is solved.
Owner:STATE GRID BEIJING ELECTRIC POWER +1
Network node encryption method and network node encryption device
ActiveCN106302476BImprove securityTroubleshoot technical issues with poor securitySecuring communicationData informationTrust third party
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
High-stability explosion-proof carbon-based capacitor module
ActiveCN113593914AImprove securityTroubleshoot technical issues with poor securityLiquid electrolytic capacitorsCapacitor terminalsElectric capacityControl theory
The invention is a divisional application of an invention patent with the application number of ''202010987882.0'', belongs to the field of battery modules, and discloses a high-stability explosion-proof carbon-based capacitor module. The invention provides the high-stability explosion-proof carbon-based capacitor module. The high-stability explosion-proof carbon-based capacitor module comprises a module shell, multiple groups of module battery cells, module poles, an exhaust safety valve and a gas recovery box. The multiple groups of module battery cells are arranged in the module shell; the module poles are arranged on the module shell, are connected with the module battery cells and are used for providing electric energy; the exhaust safety valve is arranged on the module shell and used for exhausting a gas in the module shell when the pressure intensity in the module shell is larger than a set value; and the gas recovery box is connected with the exhaust safety valve through a condensation pipe so as to recycle the gas exhausted by the exhaust safety valve. According to the high-stability explosion-proof carbon-based capacitor module provided by the invention, the leakage of the electrolyte is avoided through the arrangement of the exhaust safety valve and the gas recovery box, and the use safety of the carbon-based capacitor module is improved.
Owner:SHANXI TUMEN NEW ENERGY CO LTD
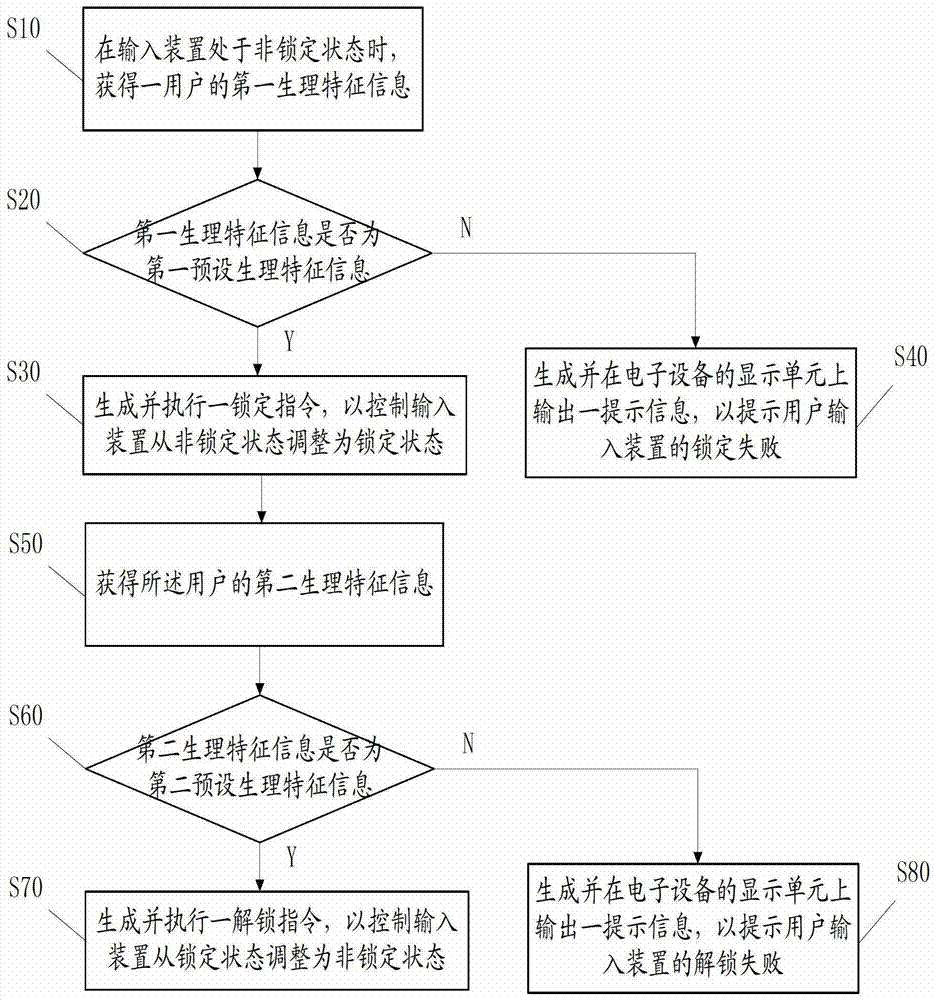
A method and electronic device for locking an input device
ActiveCN104346551BSimplify technical effectsPrevent leakageInternal/peripheral component protectionDigital data authenticationInput deviceElectronic equipment
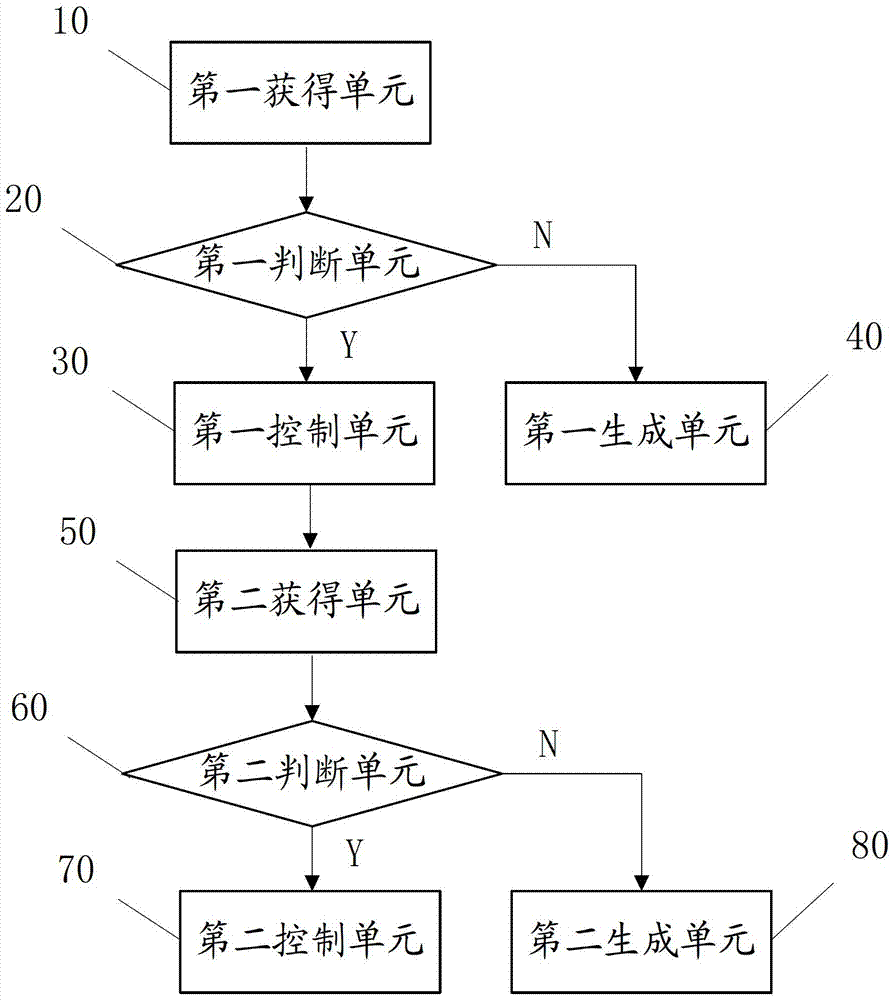
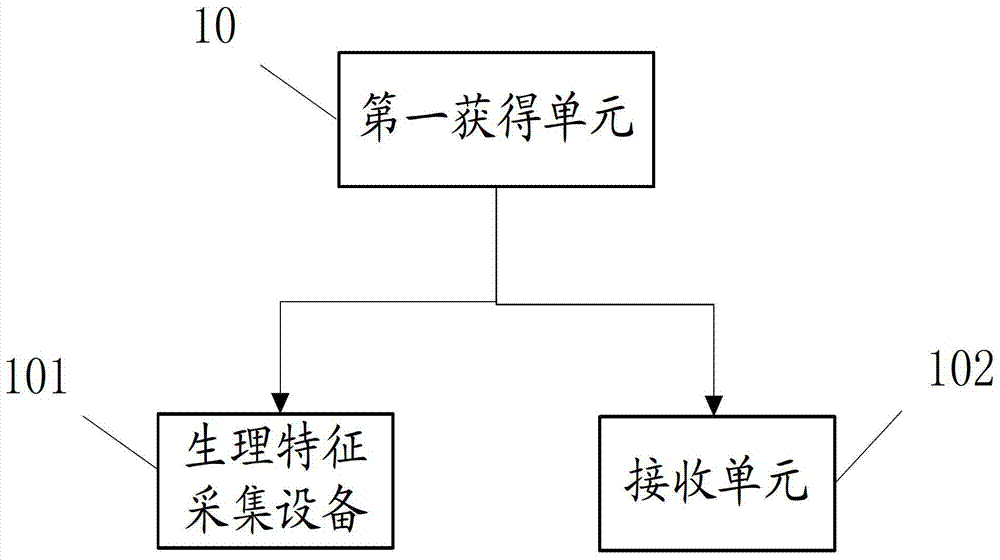
The invention discloses an input device locking method and electronic equipment. The method comprises the following steps: when an input device is in a non-locking state, acquiring first physiological feature information of a user; judging whether the first physiological feature information is the first preset physiological feature information or not, obtaining a first judgment result; when the first judgment result indicates that the first physiological feature information is the first preset physiological feature information, generating and executing a locking command to control the input device to be adjusted to the locking state from the non-locking state.
Owner:LENOVO (BEIJING) LTD
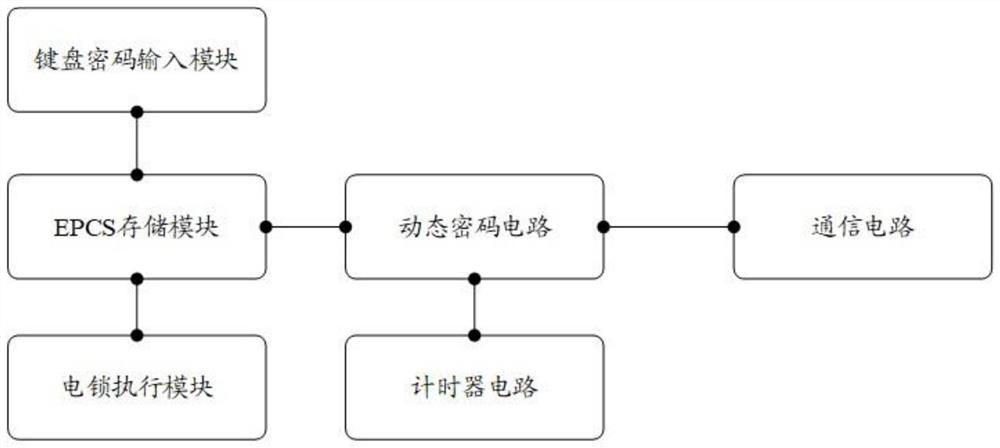
A dynamic password circuit, access control system and access control method
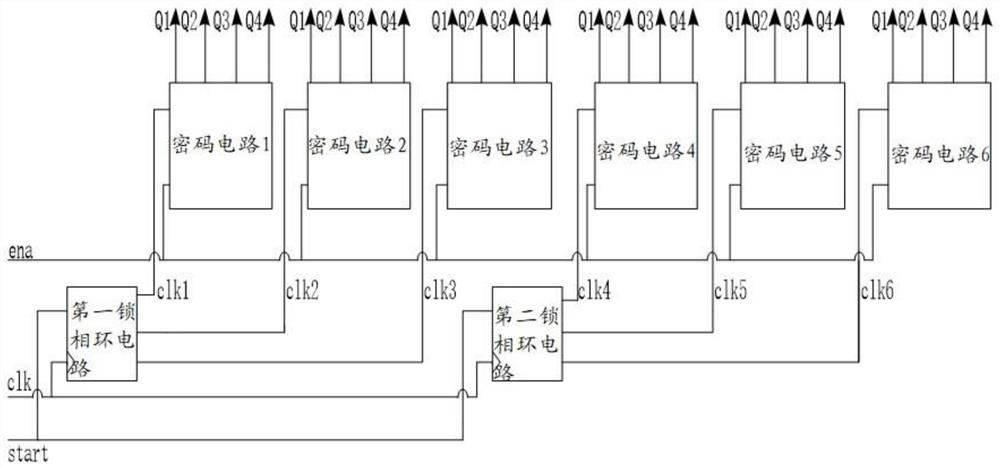
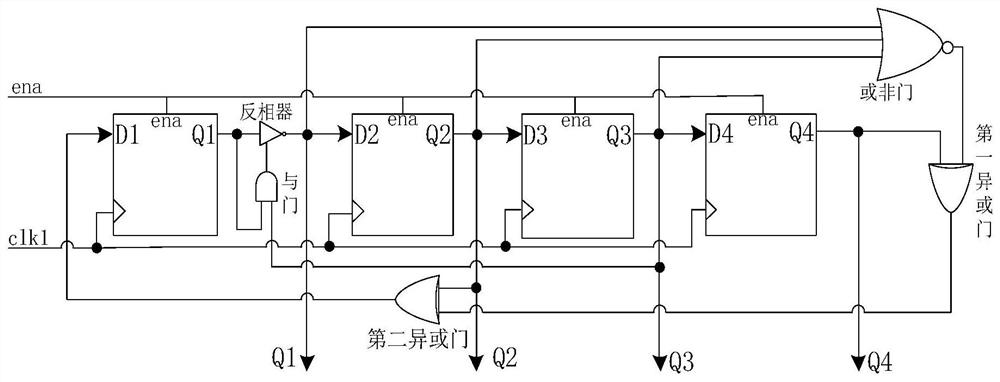
InactiveCN111540102BAvoid password disclosure flawsTroubleshoot technical issues with poor securityIndividual entry/exit registersPhase locked loop circuitPassword
Owner:SOUTH CHINA NORMAL UNIVERSITY
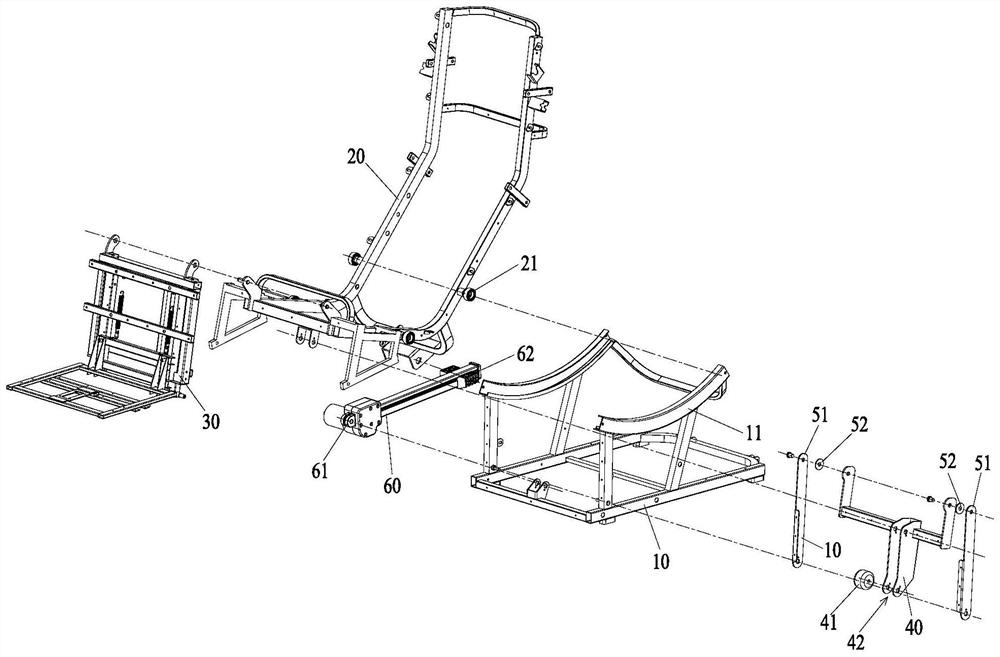
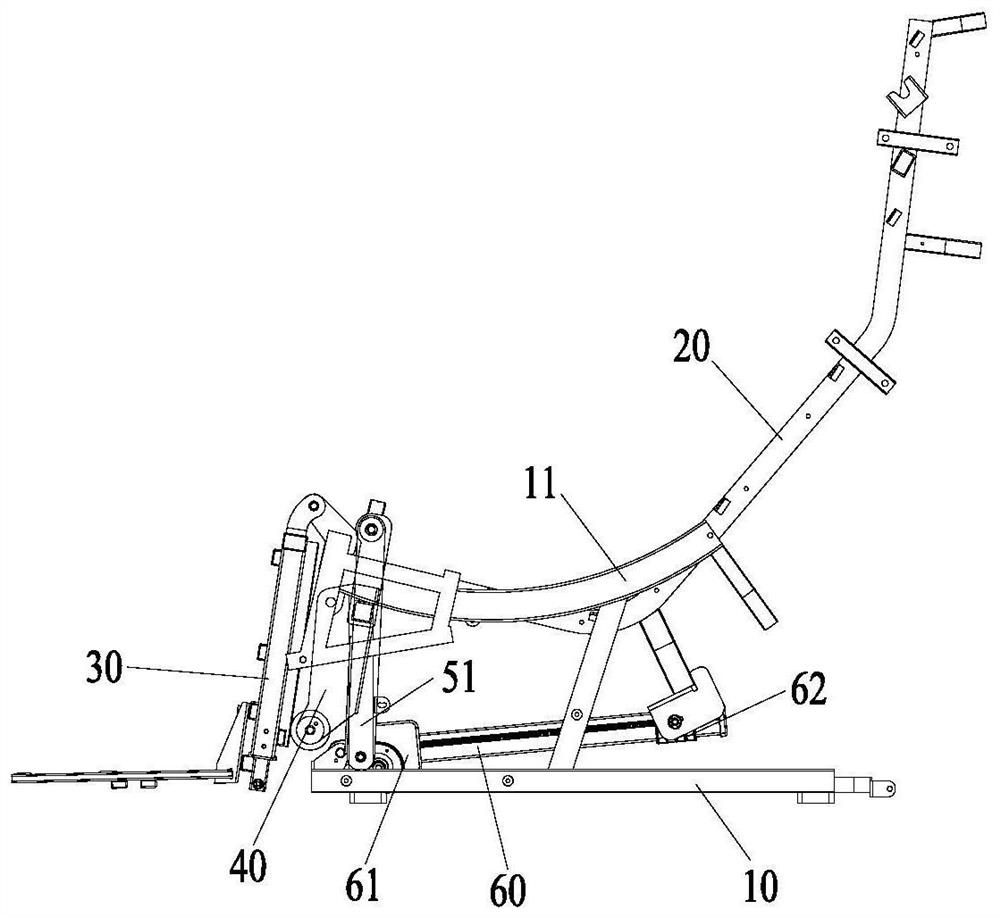
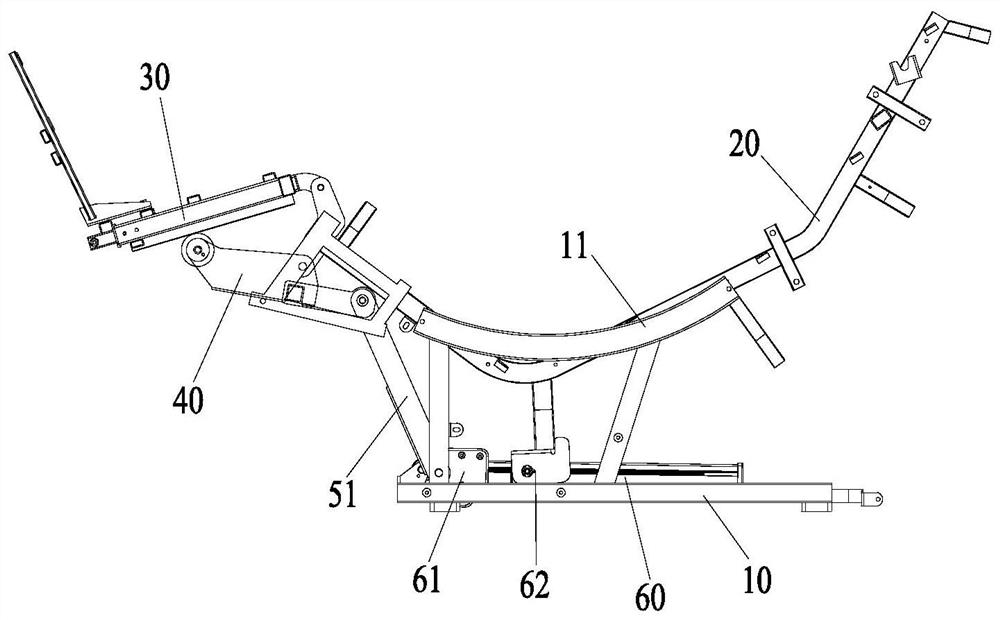
Chair frame and massage chair
PendingCN113143729ATroubleshoot technical issues with poor securityVibration massageSuction-kneading massagePhysical medicine and rehabilitationMassage
The invention provides a chair frame and a massage chair. The chair frame comprises a base, a seat support, a shank support, a supporting arm and a driving device; the seat support is arranged on the upper portion of the base; the shank support is hinged to the seat support; furthermore, the front side of the shank support is used for supporting the legs of a user; the supporting arm is hinged to the seat support; one end of the supporting arm is a supporting end; the supporting end abuts against the portion, deviating from the hinge point, of the rear side of the shank support; the driving device is connected between the supporting arm and the seat support; and the driving device is configured to be capable of driving the supporting end to ascend or descend so as to drive the shank support to rotate relative to the seat support. On the basis that the functionality of the chair frame is guaranteed, when the shank support executes the leg retracting action, the shank support does not bear the pulling acting force of the supporting arm but moves through the gravity action borne by the shank support; the anti-pinch effect is good; and the safety is high.
Owner:XIAMEN OGAWA INTELLIGENT HEALTH EQUIP CO LTD
Method, device, storage medium and processor for assigning control rights
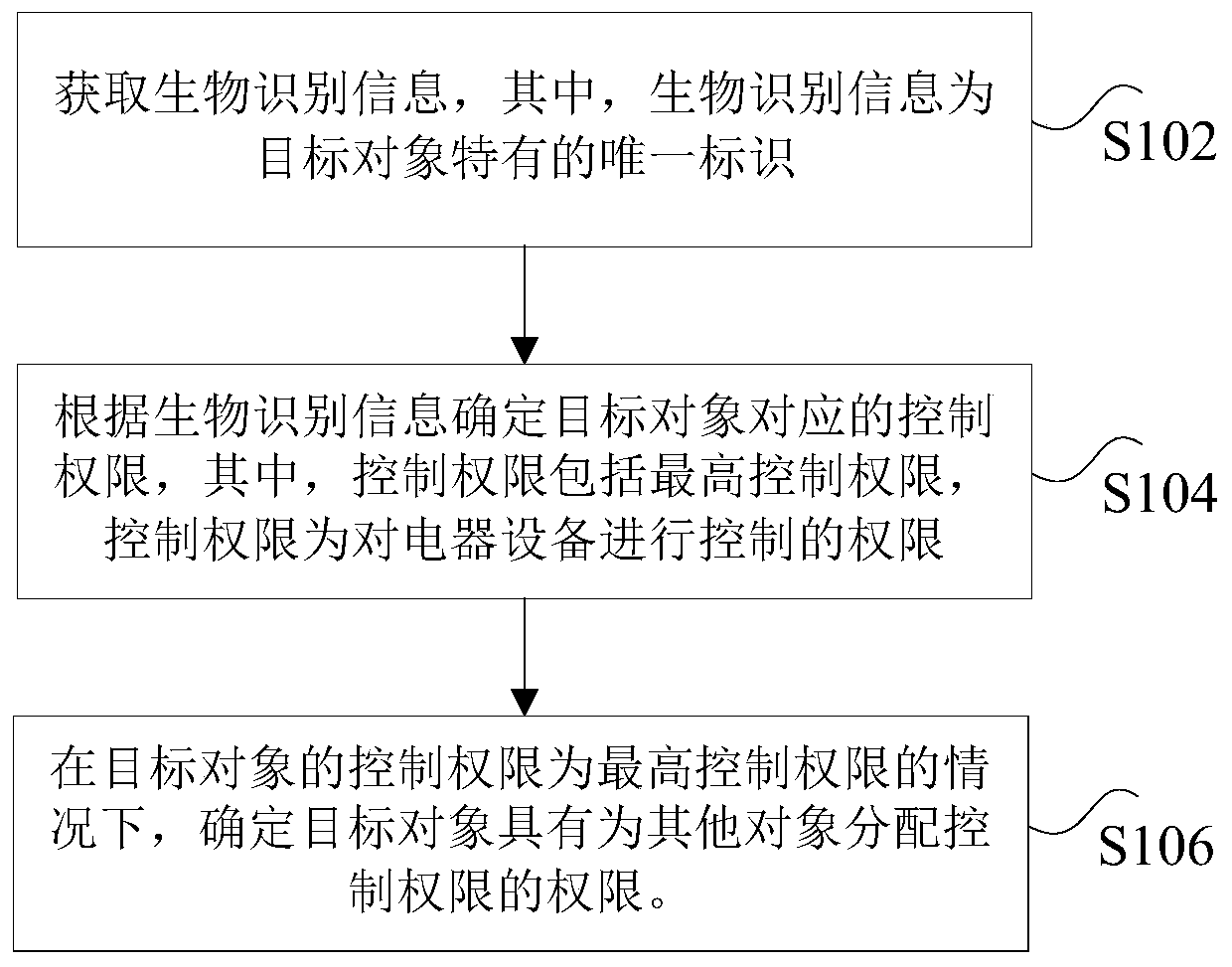
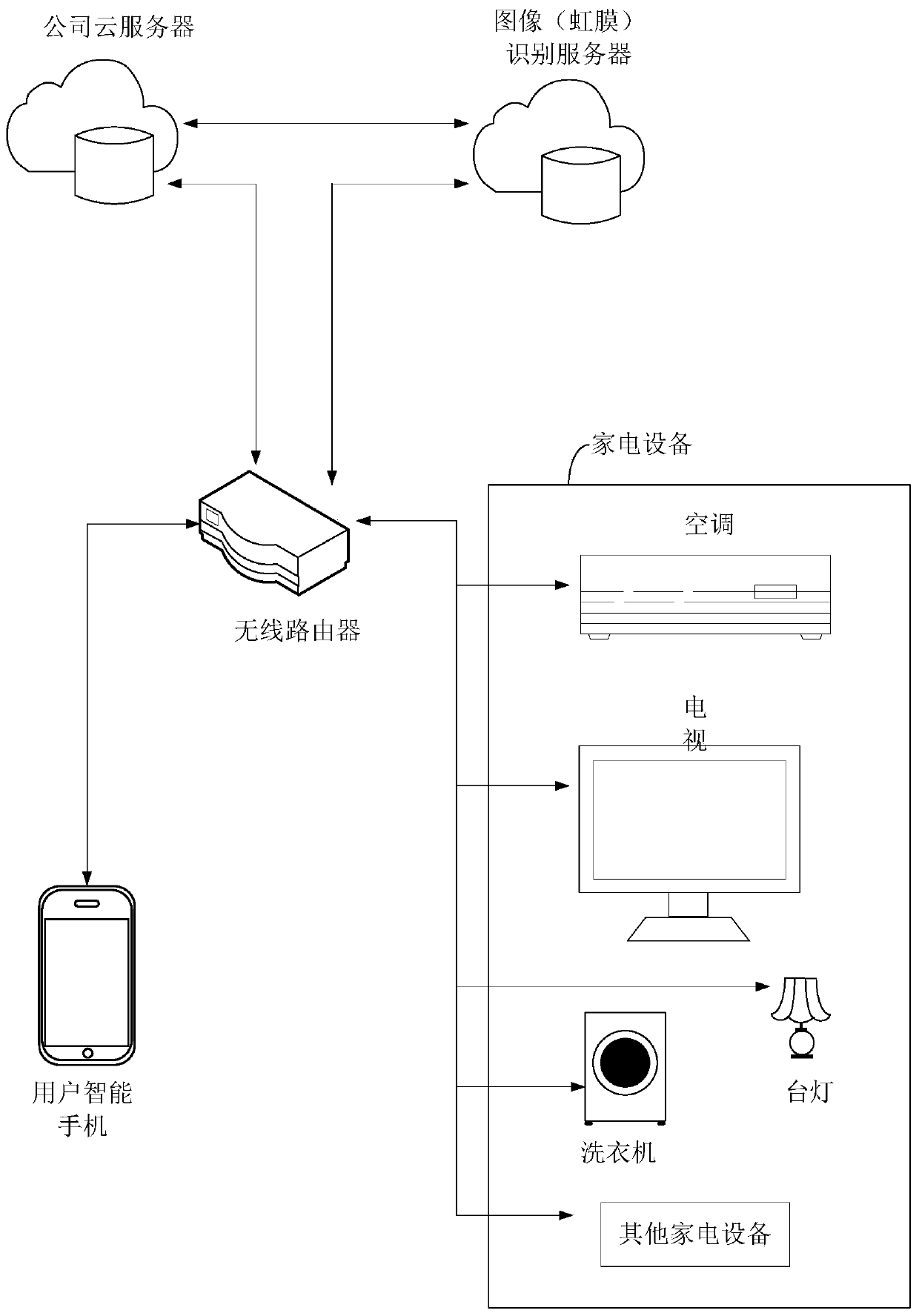
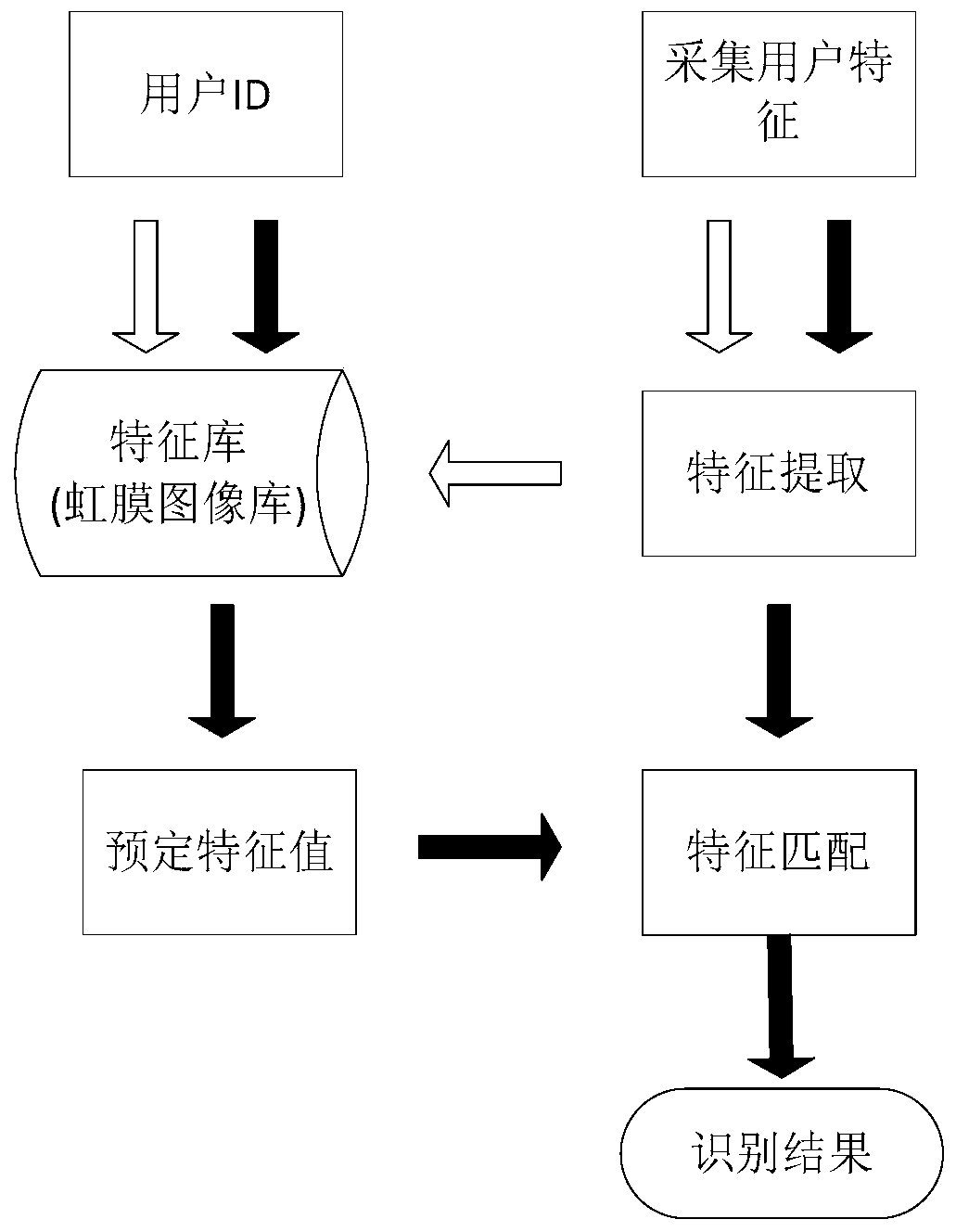
ActiveCN108107743BTroubleshoot technical issues with poor securityEasy to manageComputer controlTotal factory controlComputer networkDistribution control
Owner:GREE ELECTRIC APPLIANCES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com