Space-ground integrated network security state analysis method based on finite state machine
A finite state machine and network security technology, applied to electrical components, transmission systems, etc., can solve problems such as real-time analysis difficulties, and achieve the effect of reducing false positives and false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
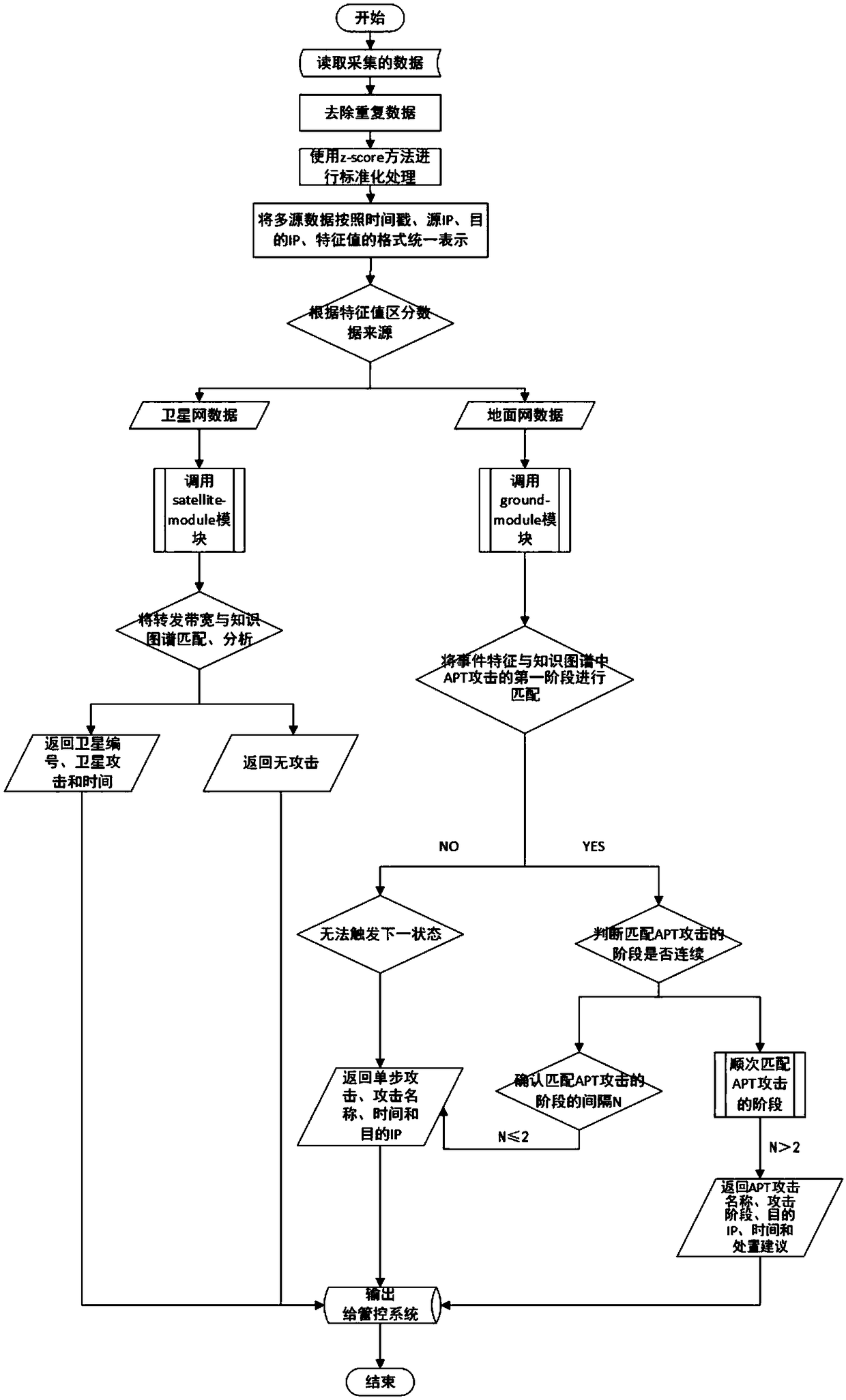
[0032] The method for analyzing the security state of the space-ground integration network based on the finite state machine of the present invention first constructs the knowledge map of the space-ground integration network before starting the analysis:
[0033] Step 1: Build an ontology in the field of network security,
[0034] Ontology models include: attack, event, gateway, satellite, vulnerability, operating system, application software, process, registry, and file. In the field of network security, ontology refers to the shared concept of network security situational element knowledge. These conceptual attributes and the relationship between concepts are then guided by the principle of ontology to construct a network security knowledge map;
[0035] Step 2: Construct the knowledge graph of the space-earth integration network. The model of the knowledge graph includes concepts, instances, attributes, relationships, and rules. Examples are specific examples of concepts, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com