Patents
Literature
175 results about "Virtual finite-state machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
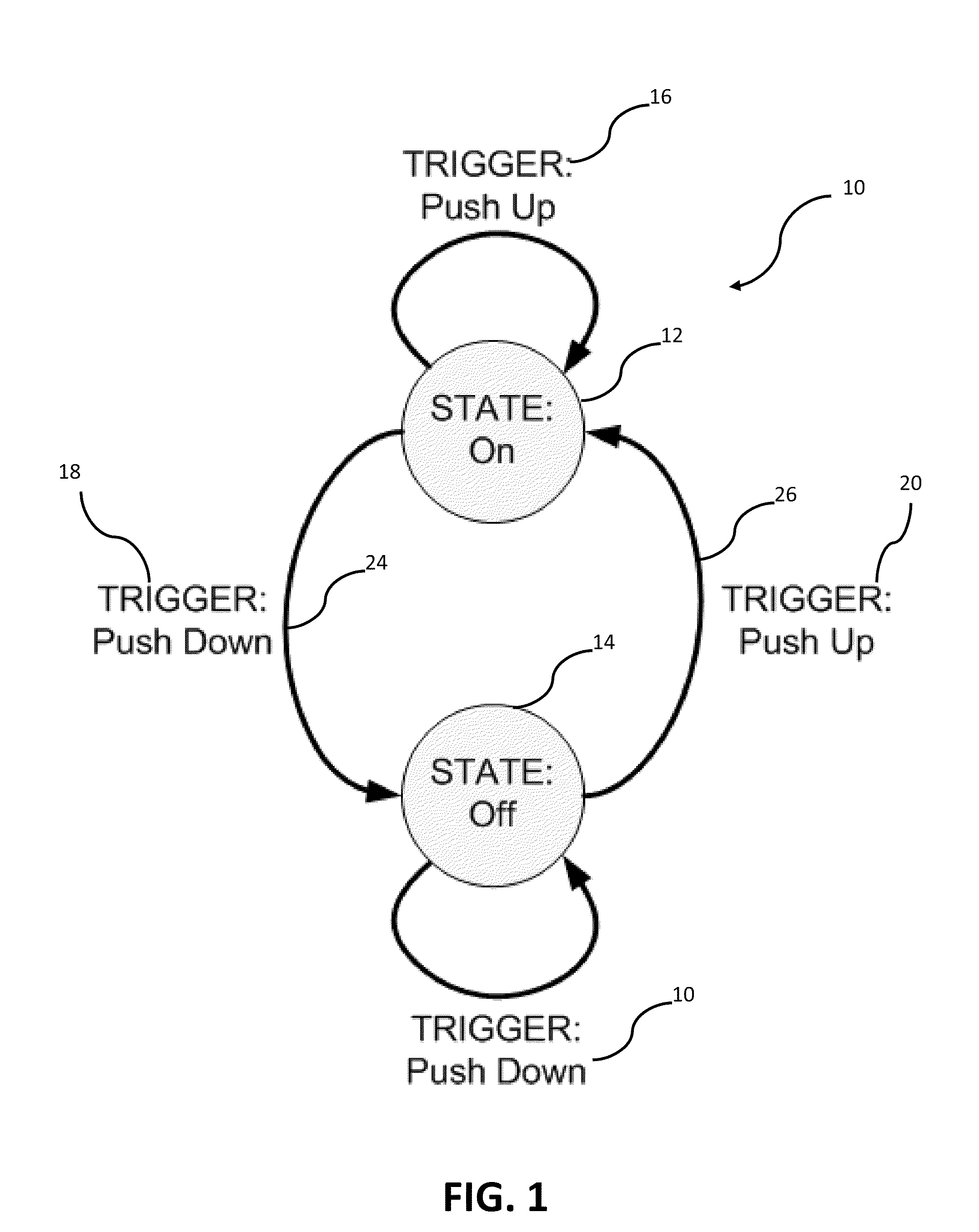
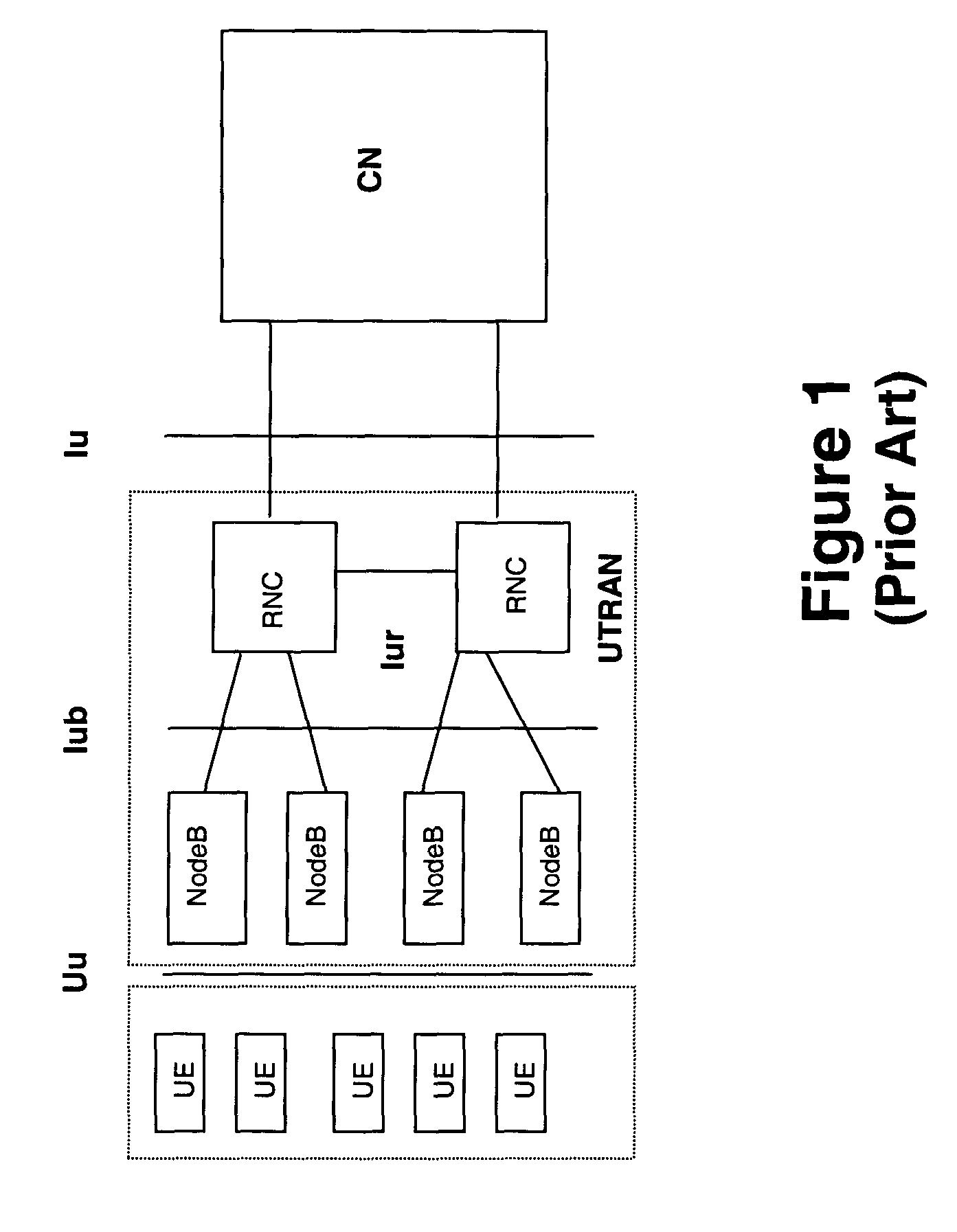
A virtual finite state machine (VFSM) is a finite state machine (FSM) defined in a Virtual Environment. The VFSM concept provides a software specification method to describe the behaviour of a control system using assigned names of input control properties and of output actions.
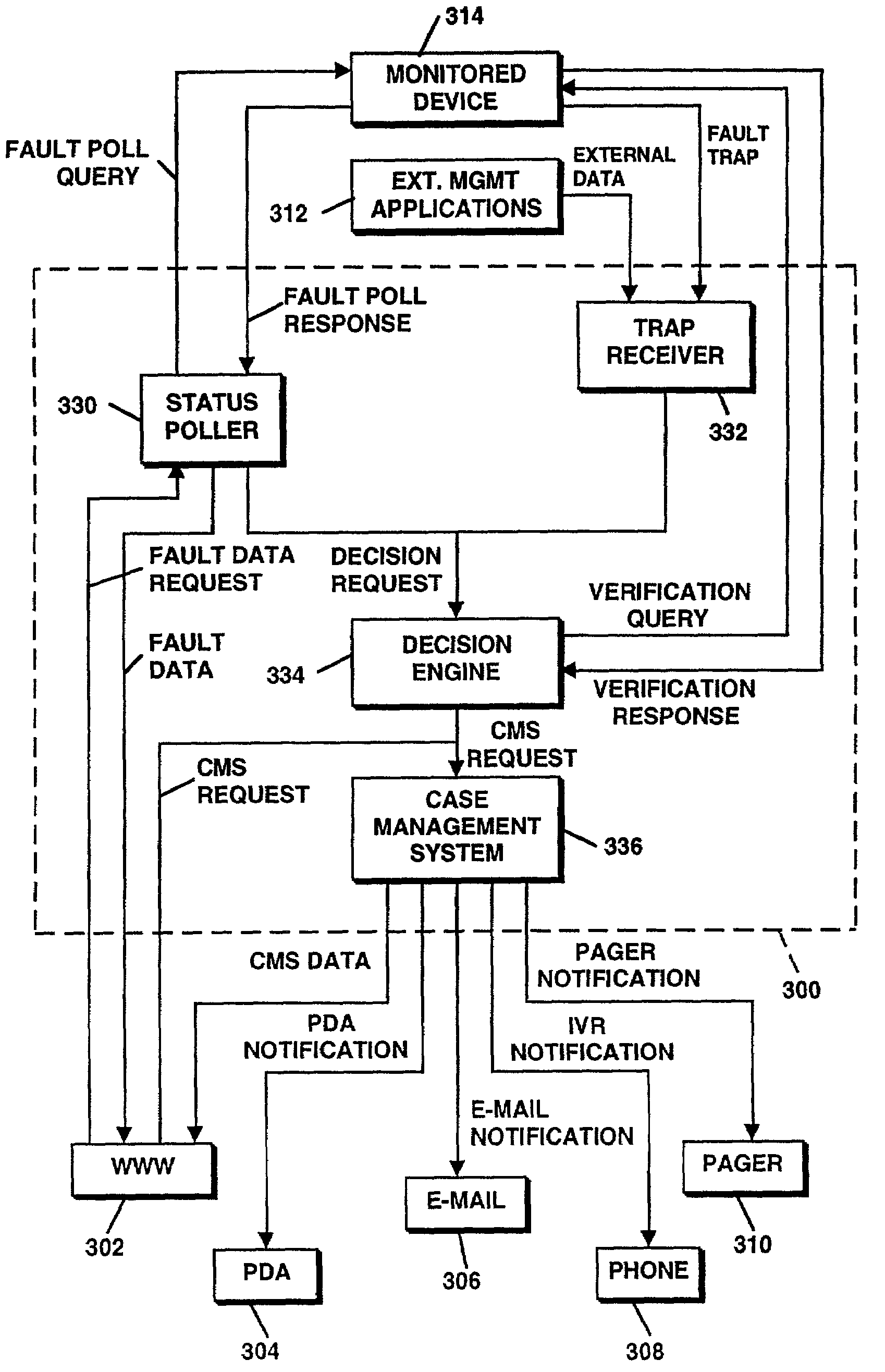
Method and apparatus for maintaining the status of objects in computer networks using virtual state machines
ActiveUS7197561B1Error detection/correctionMultiple digital computer combinationsVirtual finite-state machineFinite-state machine
A network appliance for monitoring, diagnosing and documenting problems among a plurality of devices and processes (objects) coupled to a computer network utilizes periodic polling and collection of object-generated trap data to monitor the status of objects on the computer network. The status of a multitude of objects is maintained in memory utilizing virtual state machines which contain a small amount of persistent data but which are modeled after one of a plurality of finite state machines. The memory further maintains dependency data related to each object which identifies parent / child relationships with other objects at the same or different layers of the OSI network protocol model. A decision engine verifies through on-demand polling that a device is down. A root cause analysis module utilizes status and dependency data to locate the highest object in the parent / child relationship tree that is affected to determine the root cause of a problem. Once a problem has been verified, a “case” is opened and notification alerts may be sent out to one or more devices. A user interface allows all objects within the network to be displayed with their respective status and their respective parent / child dependency objects in various formats.
Owner:OPTANIX INC
System of finite state machines
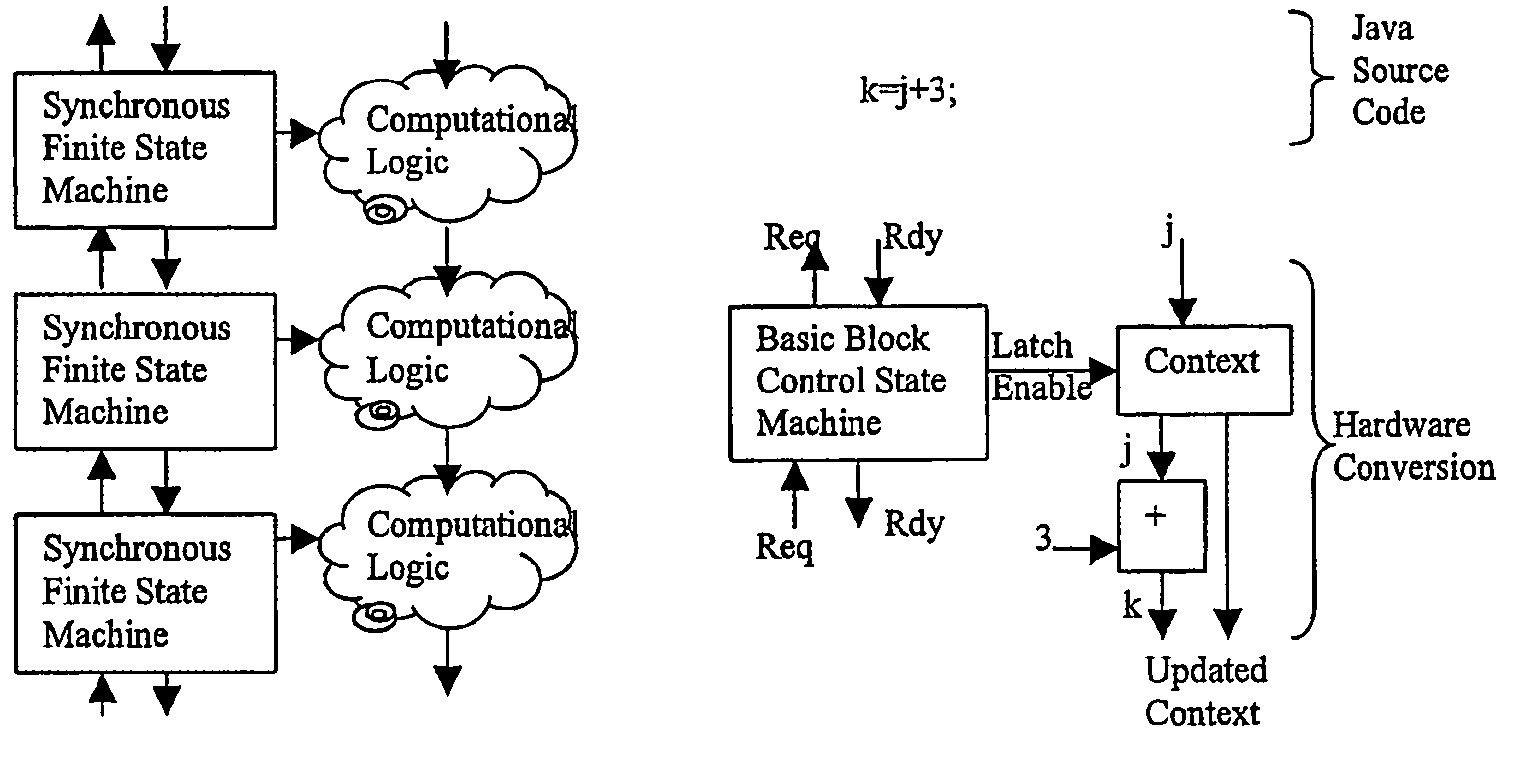
InactiveUS7224185B2Enough timeConcurrent instruction executionMultiple digital computer combinationsSufficient timeComputational logic
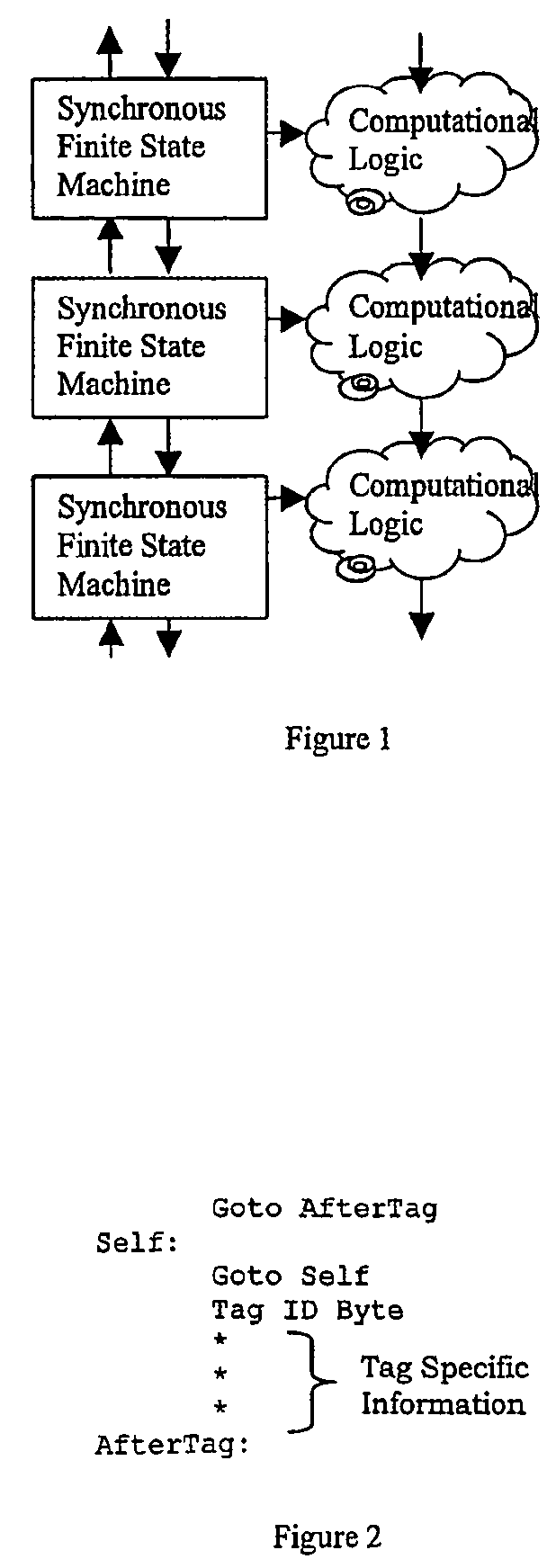
A system of finite state machines built with asynchronous or synchronous logic for controlling the flow of data through computational logic circuits programmed to accomplish a task specified by a user, having one finite state machine associated with each computational logic circuit, having each finite state machine accept data from either one or more predecessor finite state machines or from one or more sources outside the system and furnish data to one or more successor finite state machines or a recipient outside the system, excluding from consideration in determining a clock period for the system logic paths performing the task specified by the user, and providing a means for ensuring that each finite state machine allows sufficient time to elapse for the computational logic circuit associated with that finite state to perform its task.
Owner:CAMPBELL JOHN +1
Hardware accelerator personality compiler
InactiveUS20040172234A1Software engineeringSpecial data processing applicationsState switchingAutomaton
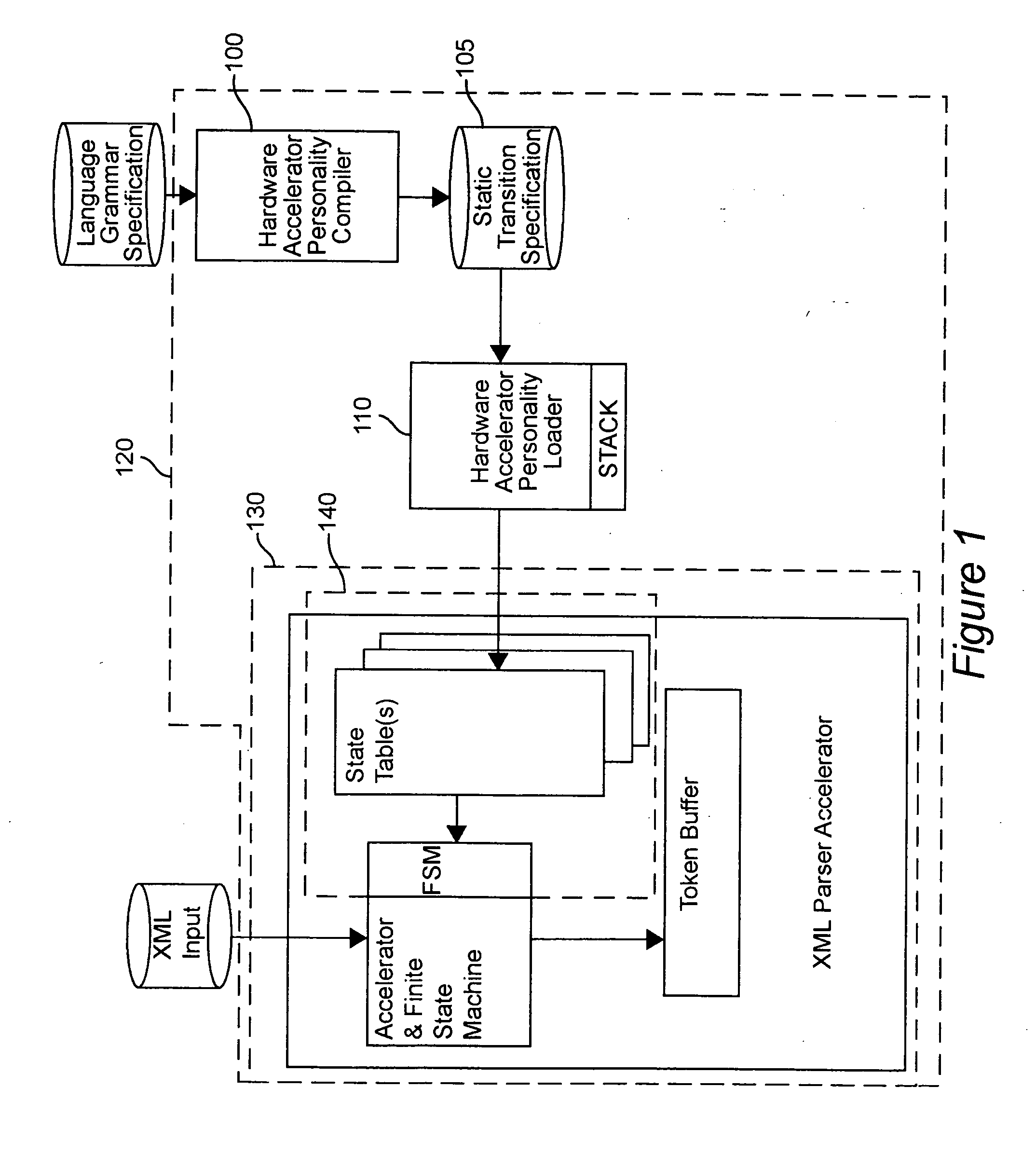
Error-free state tables are automatically generated from a specification of a group of desired performable functions, such as are provided in a programming language in a formal notation such as Backus-Naur form or a derivative thereof by discriminating tokens corresponding to respective performable functions, identifications, arguments, syntax, grammar rules, special symbols and the like. The tokens may be recursive (e.g. infinite), in which case they are transformed into a finite automata which may be deterministic or non-deterministic. Non-deterministic finite automata are transformed into deterministic finite automata and then into state transitions which are used to build a state table which can then be stored or, preferably, loaded into a finite state machine of a hardware parser accelerator to define its personality.
Owner:LOCKHEED MARTIN CORP
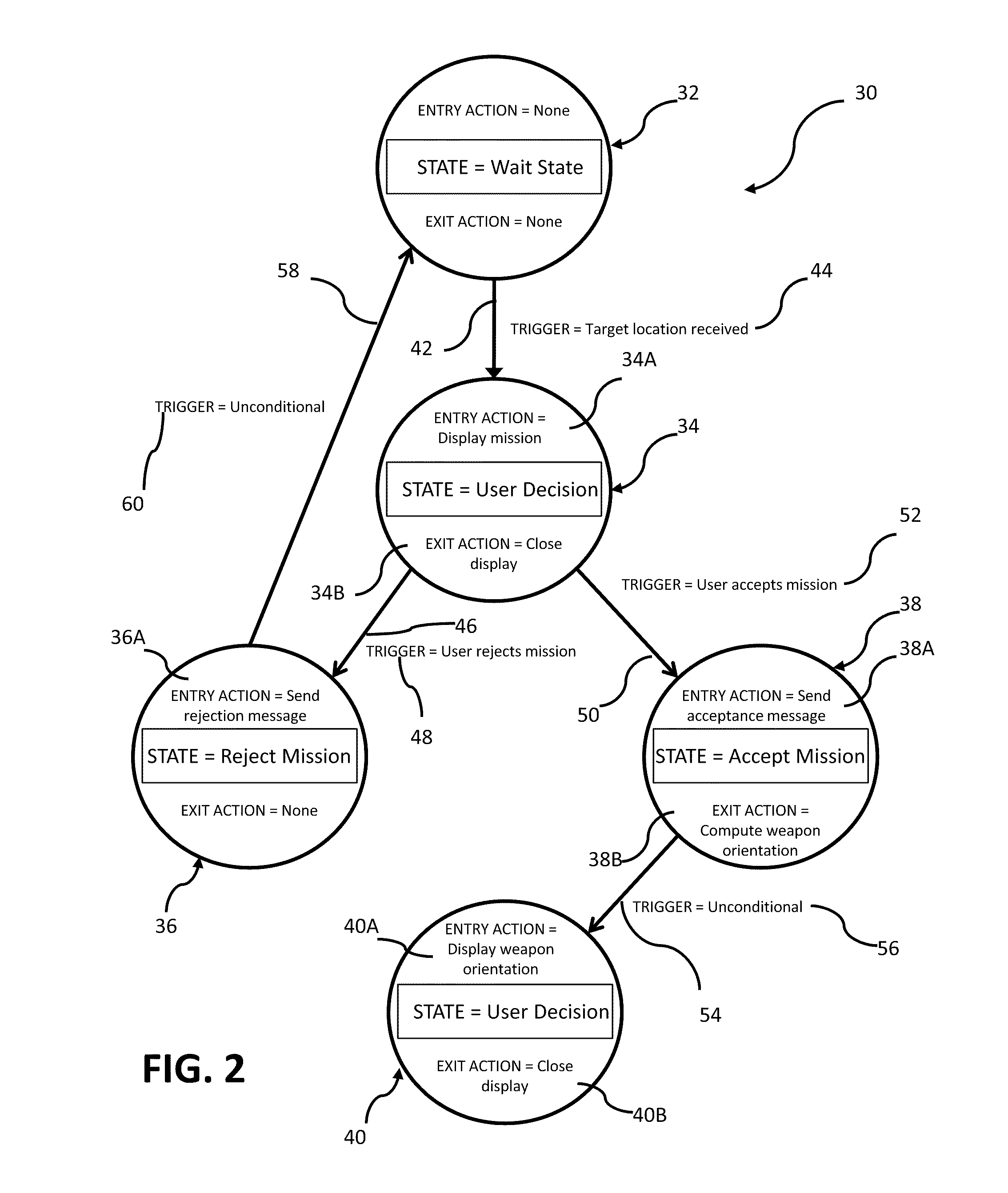
Technique using persistent foci for finite state machine based software test generation
InactiveUS6944848B2Reduce in quantitySoftware testing/debuggingSpecific program execution arrangementsTest suiteTheoretical computer science
A system for automatic generation of test programs employs test generation foci linked to a finite state machine behavioral model of a software application under test to produce abstract test suites that are executed by an execution engine. The foci include directive expressions that tag coverage variables of the behavioral model. The execution engine operates until the tagged coverage variables have assumed all their possible values. Both the behavioral models and the foci are archivable and can be retrieved and reused independently.
Owner:IBM CORP
Modeling of temporarily static objects in surveillance video data
ActiveUS20130051613A1Character and pattern recognitionVirtual finite-state machineFinite-state machine
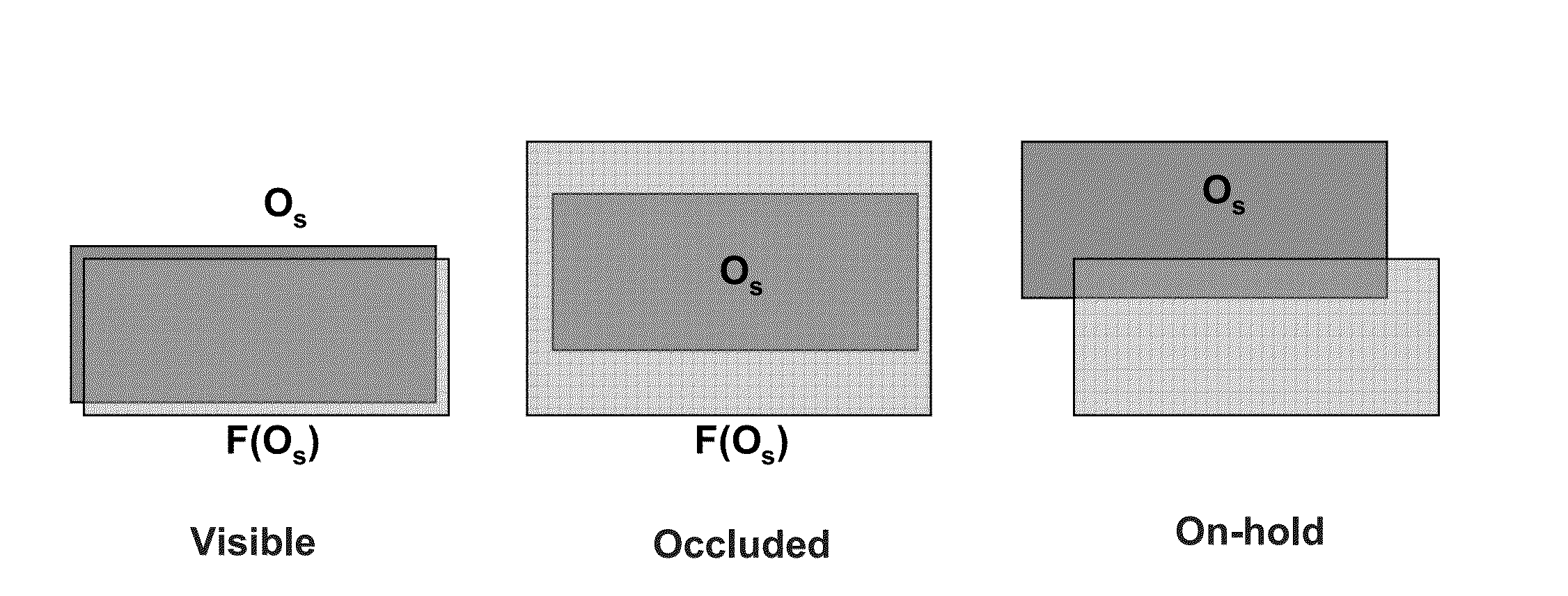
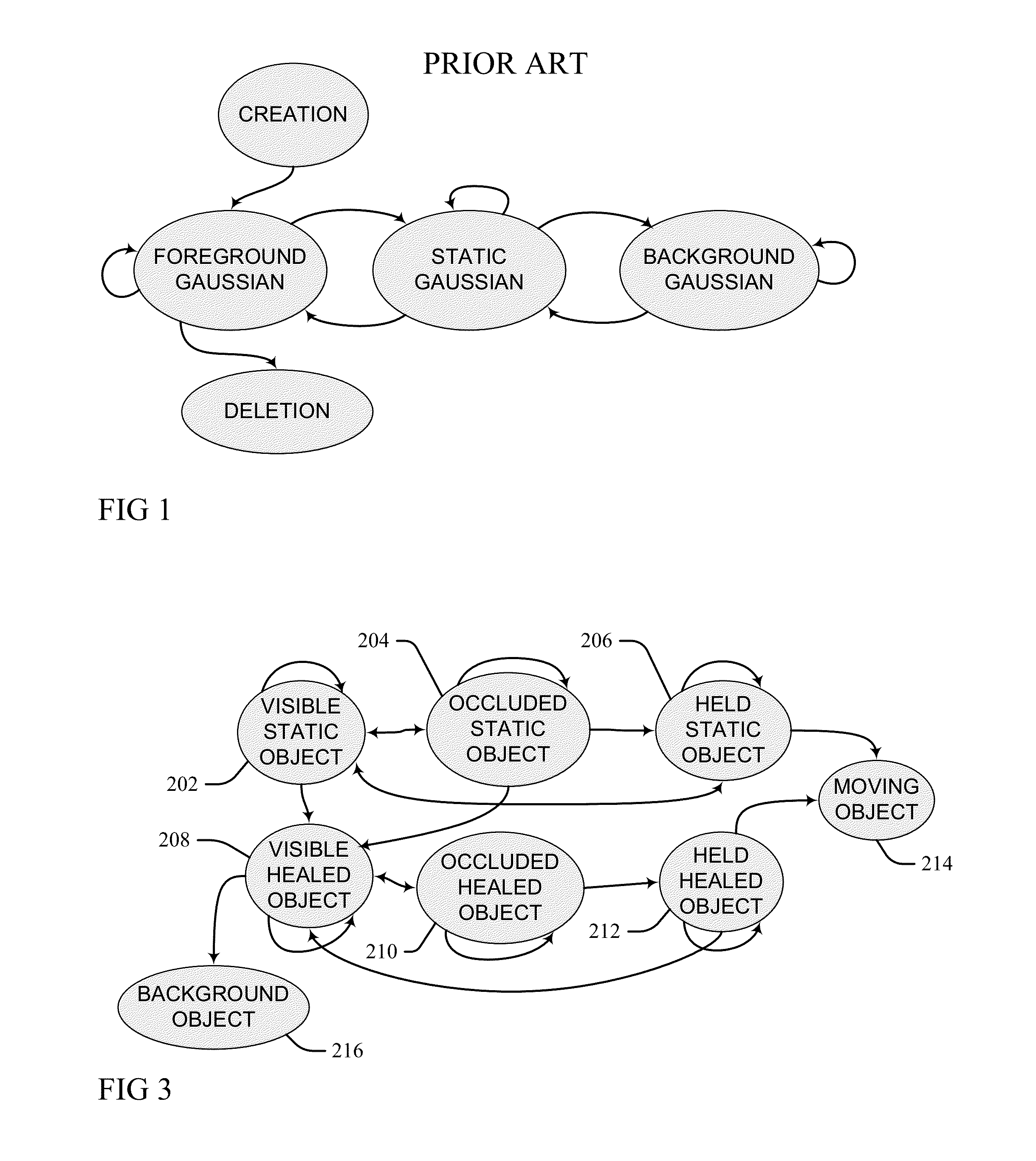
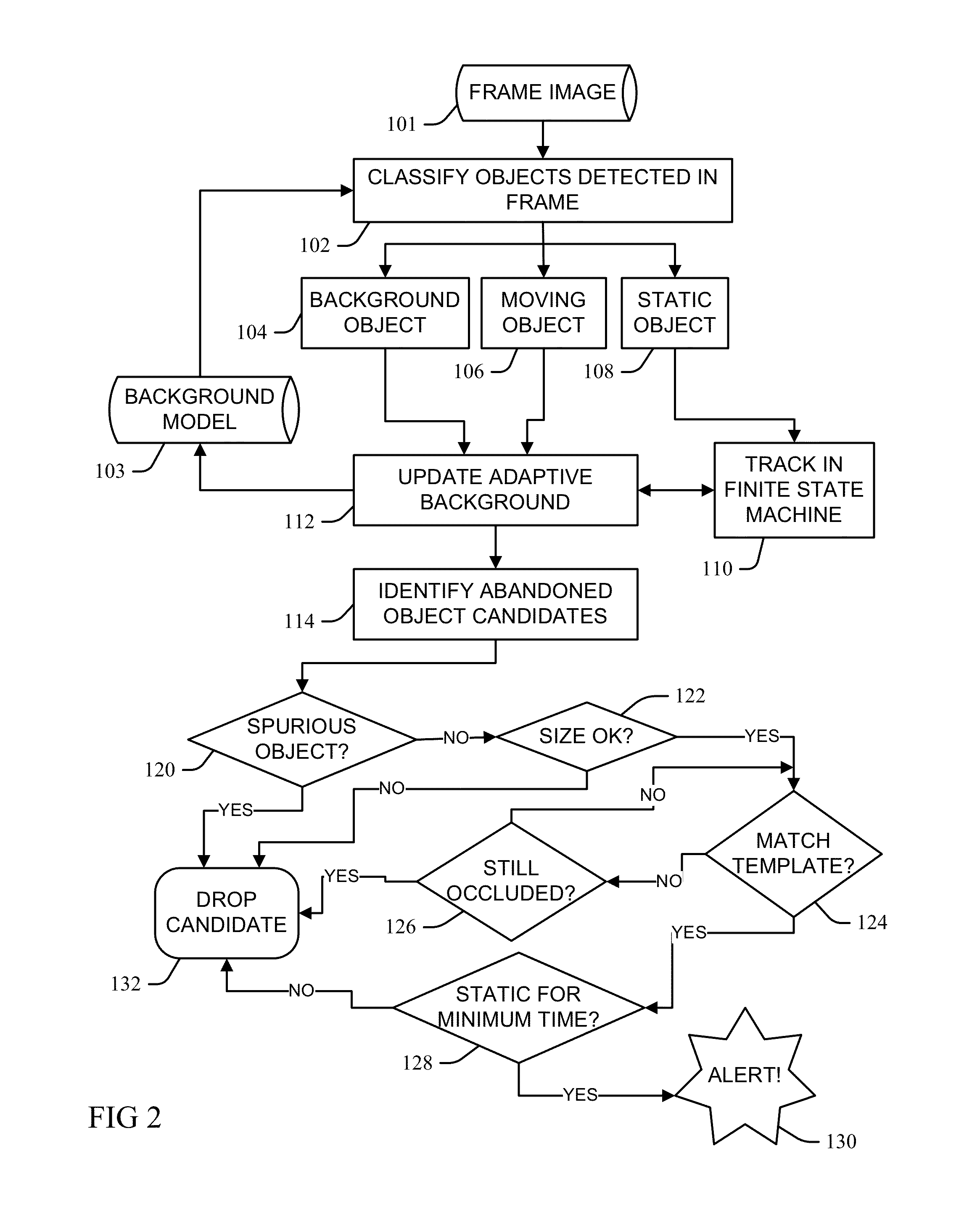
A foreground object blob having a bounding box detected in frame image data is classified by a finite state machine as a background, moving foreground, or temporally static object, namely as the temporally static object when the detected bounding box is distinguished from a background model of a scene image of the video data input and remains static in the scene image for a threshold period. The bounding box is tracked through matching masks in subsequent frame data of the video data input, and the object sub-classified within a visible sub-state, an occluded sub-state, or another sub-state that is not visible and not occluded as a function of a static value ratio. The ratio is a number of pixels determined to be static by tracking in a foreground region of the background model corresponding to the tracked object bounding box over a total number of pixels of the foreground region.
Owner:KYNDRYL INC
Method for synthesizing linear finite state machines
InactiveUS7260591B2Random number generatorsDigital function generatorsCellular automationVirtual finite-state machine
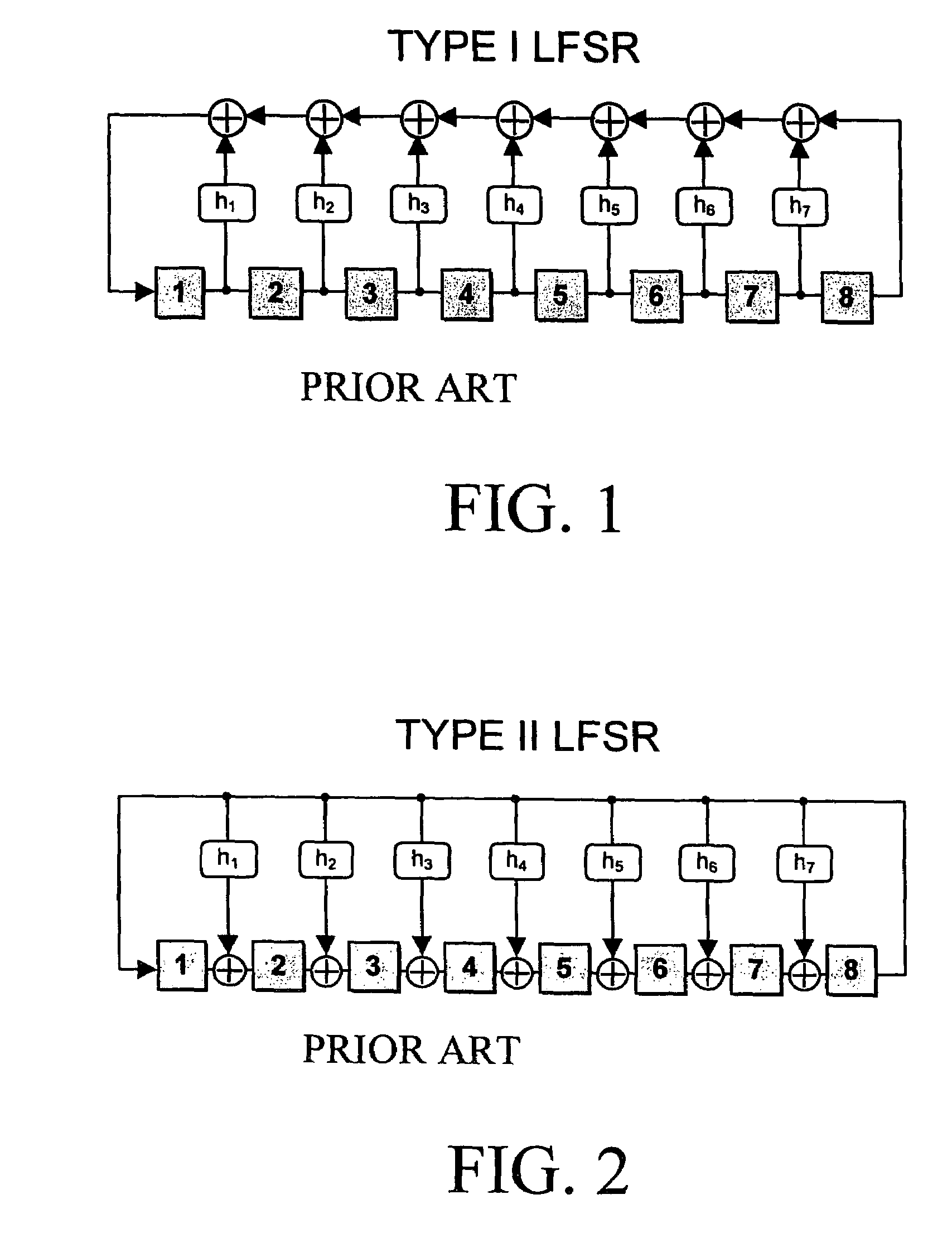
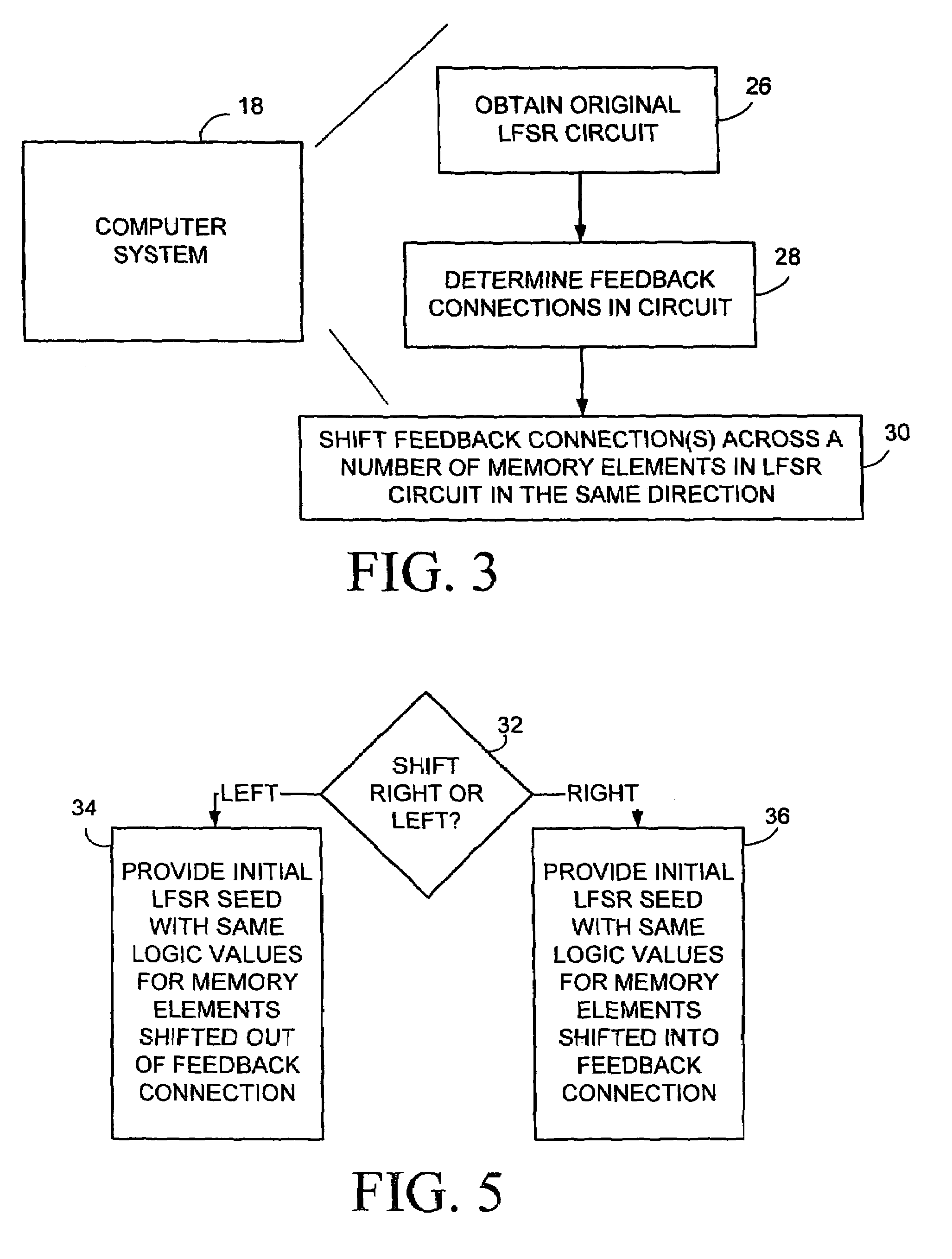
Method and apparatus for synthesizing high-performance linear finite state machines (LFSMs) such as linear feedback shift registers (LFSRs) or cellular automata (CA). Given a characteristic polynomial for the circuit, the method obtains an original LFSM circuit such as a type I or type II LFSR. Feedback connections within the original circuit are then determined. Subsequently, a number of transformations that shift the feedback connections can be applied in such a way that properties of the original circuit are preserved in a modified LFSM circuit. In particular, if the original circuit is represented by a primitive characteristic polynomial, the method preserves the maximum-length property of the original circuit in the modified circuit and enables the modified circuit to produce the same m-sequence as the original circuit. Through the various transformations, a modified LFSM circuit can be created that provides higher performance through shorter feedback connection lines, fewer levels of logic, and lower internal fan-out.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Data structure and system for IP address lookup and IP address lookup system
ActiveUS20040267732A1Digital data processing detailsData switching networksSearch data structureThree stage
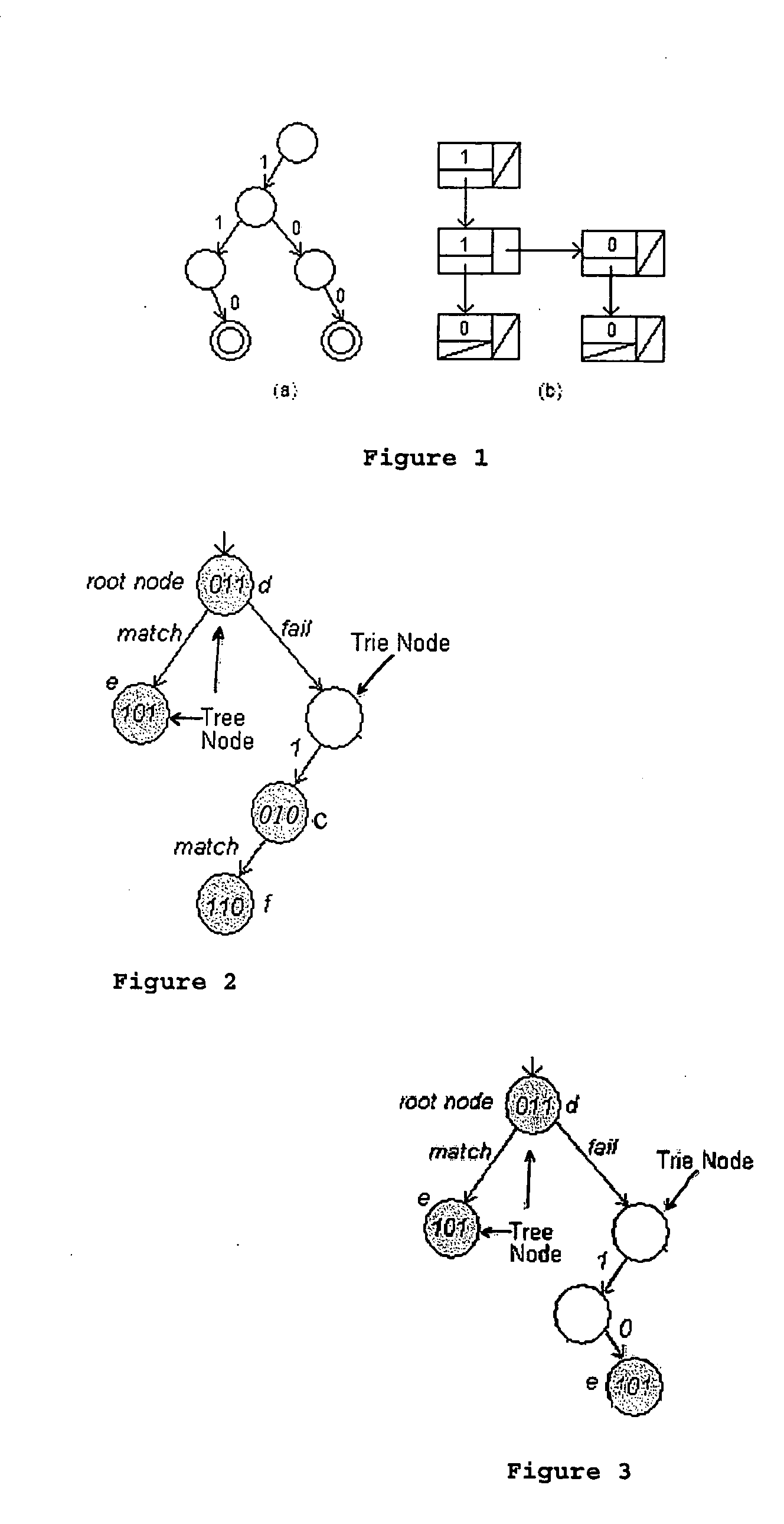
A tree data structure for storing strings of searchable data divided into substrings has at least one first type node that has a substring associated with it and at least one second type node that does not having a substring associated with it. A second type node is directly linked to a first type node by a fail transition. A first type node is directly linked to a second type node by a match transition. An IP address lookup system has memory for storing a tree data structure and a controller for storing and loading an incoming IP address. The system has a finite state machine having three stages including a first stage for loading the IP address and performing a length calculation, a second stage for searching the data structure to find a match, and a third stage for determine the next-hop address index.
Owner:HONG KONG POLYECNNIC UNIV
Methods and systems for accessing data from a DVD using a sync detector including a 26 state finite state machine
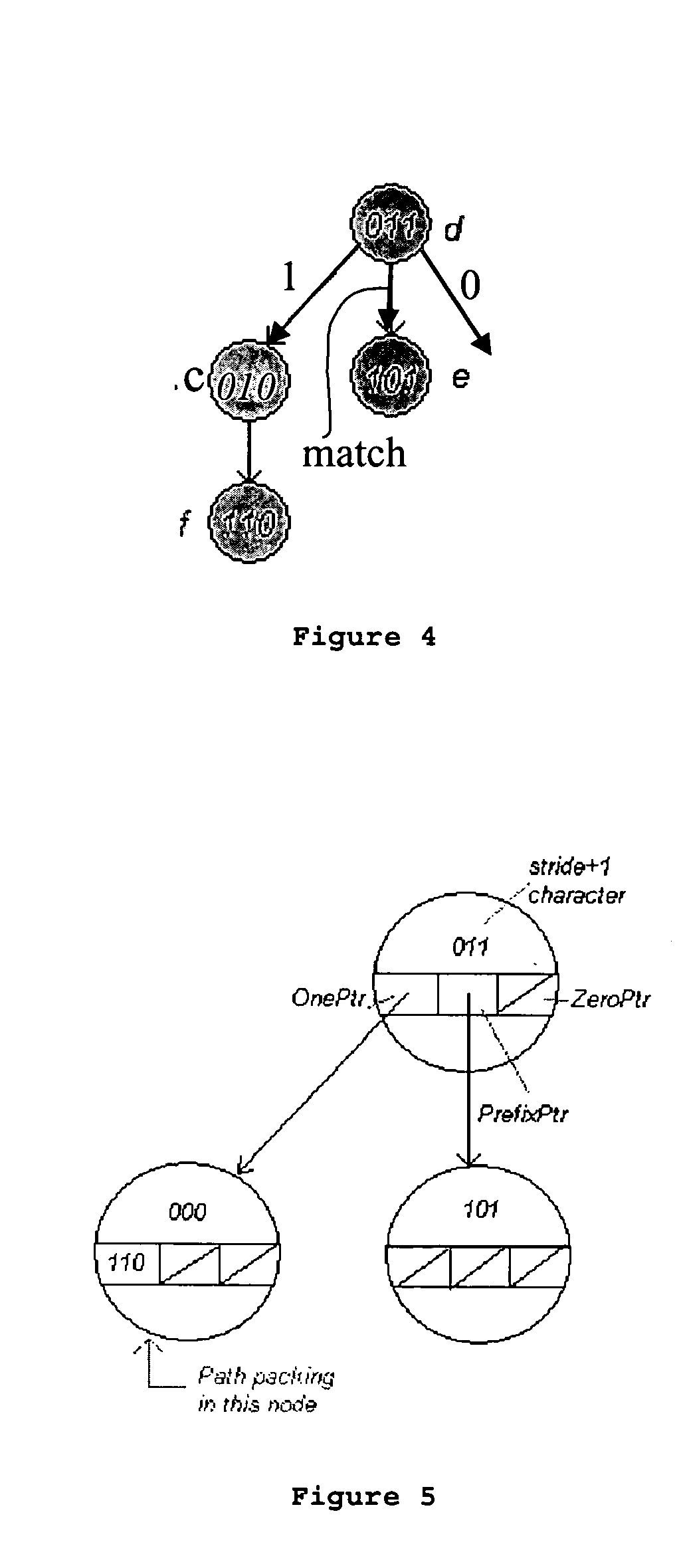
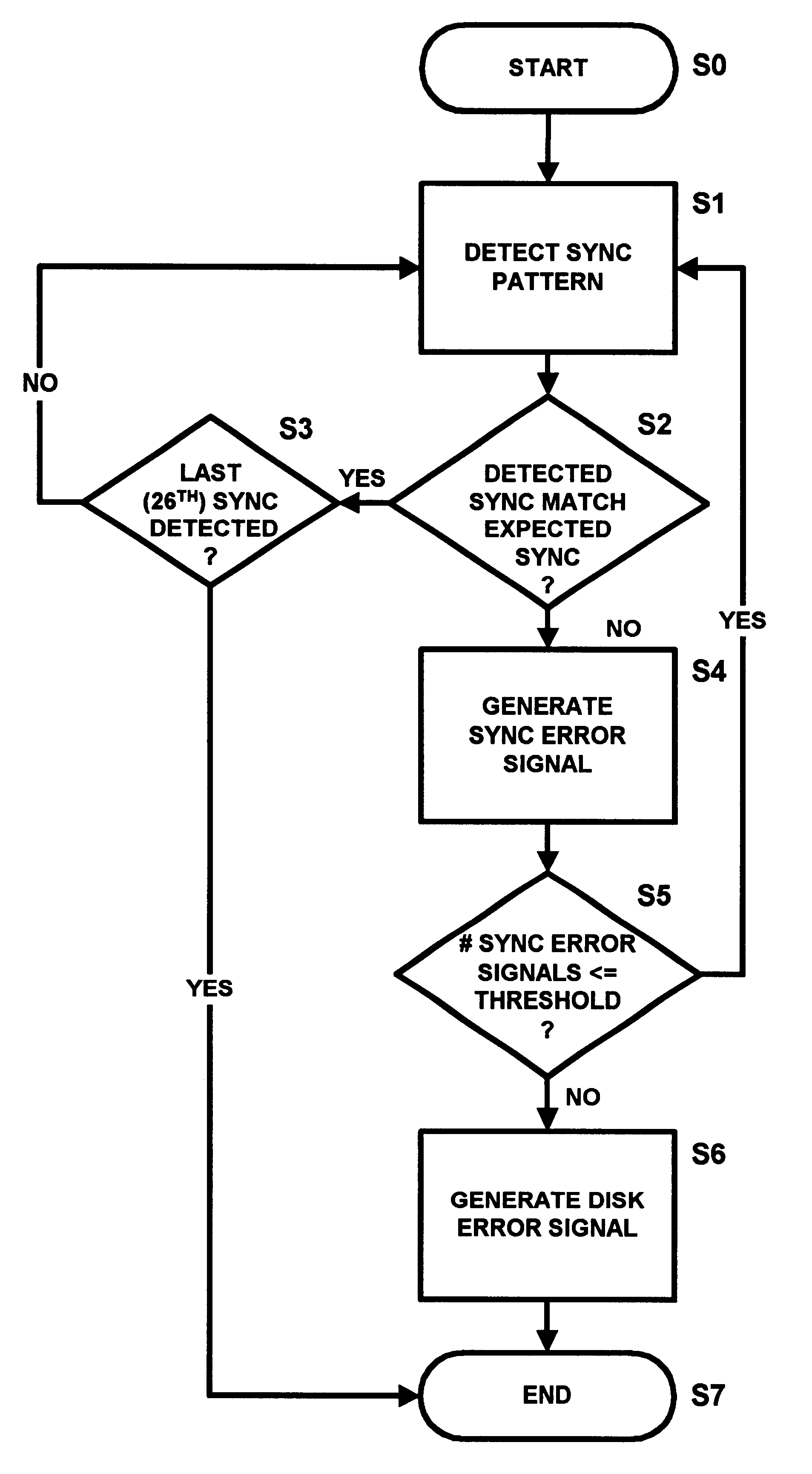
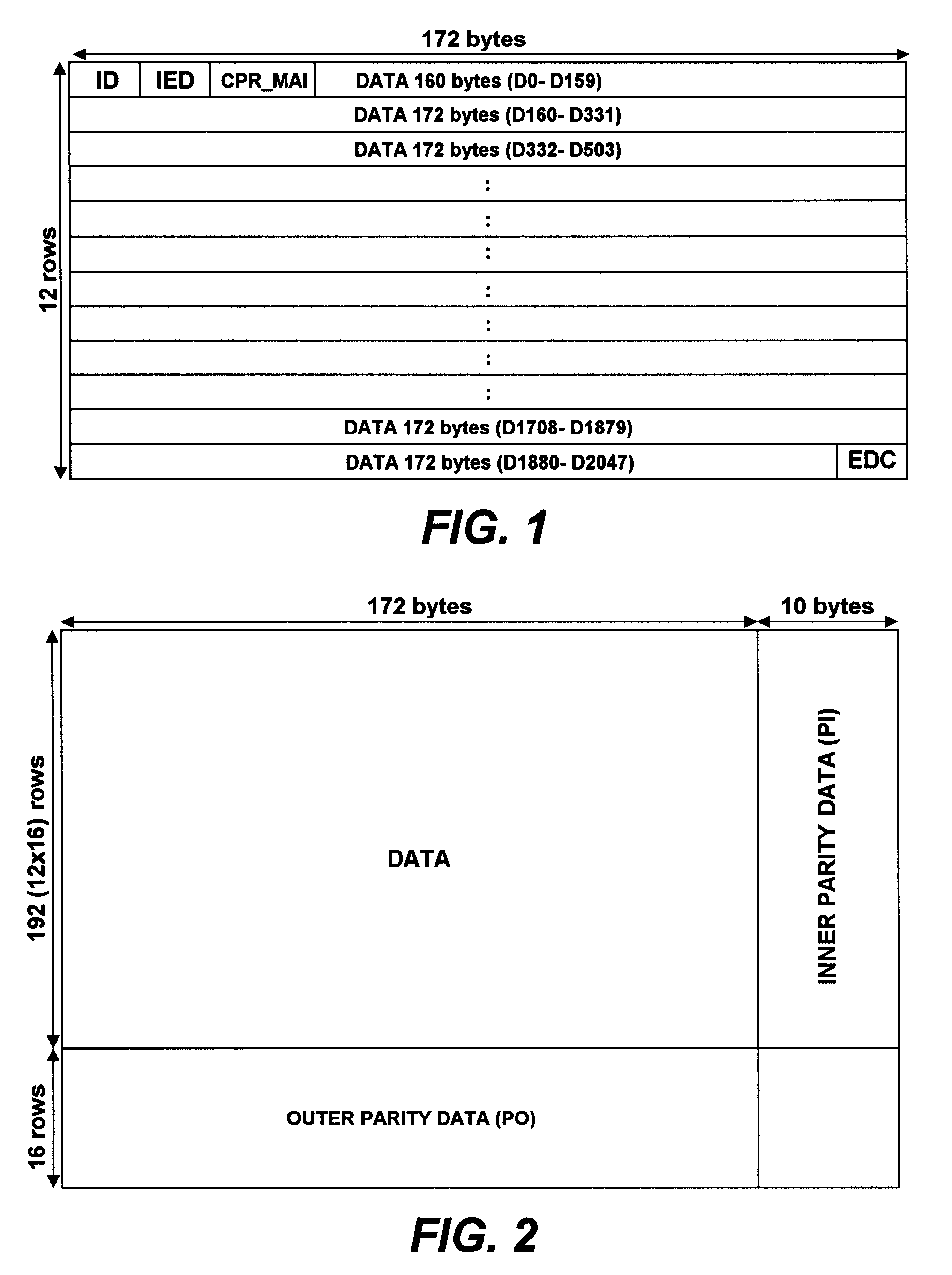
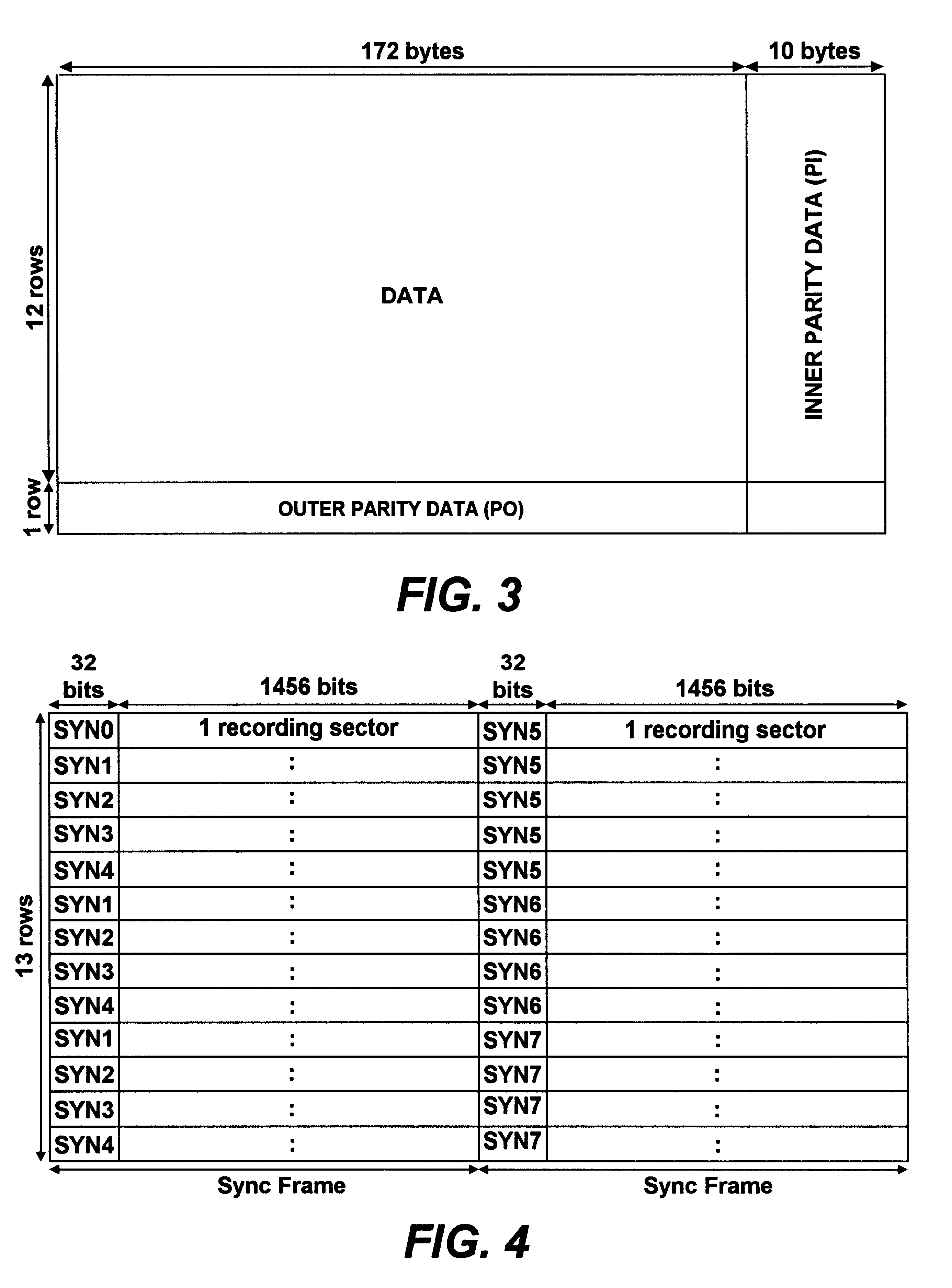
An apparatus and a method to access data from a digital recording medium configured to store data in sectors delimited by a predetermined sequence of sync patterns. The apparatus includes a sync pattern detector and a sync sequence detector to detect whether a sequence of sync patterns detected by the sync pattern detector matches the predetermined sync pattern sequence. The sync sequence detector generates a sync error signal whenever a detected sync pattern fails to match an expected sync pattern taken from the predetermined sync pattern sequence. A sync error signal counter counts the number of sync error signals generated by the sync sequence detector and a comparator compares the number of sync error signals counted by the sync error signal counter with a sync error threshold, the comparator generating a disk error signal when the threshold is exceeded. As the method and the implementing device need not rely upon the successful detection of any one sync pattern in the sector including the first sync pattern of the sector, data accesses may be carried out even though the first or a predetermined number of subsequent sync patterns in the sector may be unreadable or corrupted.
Owner:CSR TECH INC
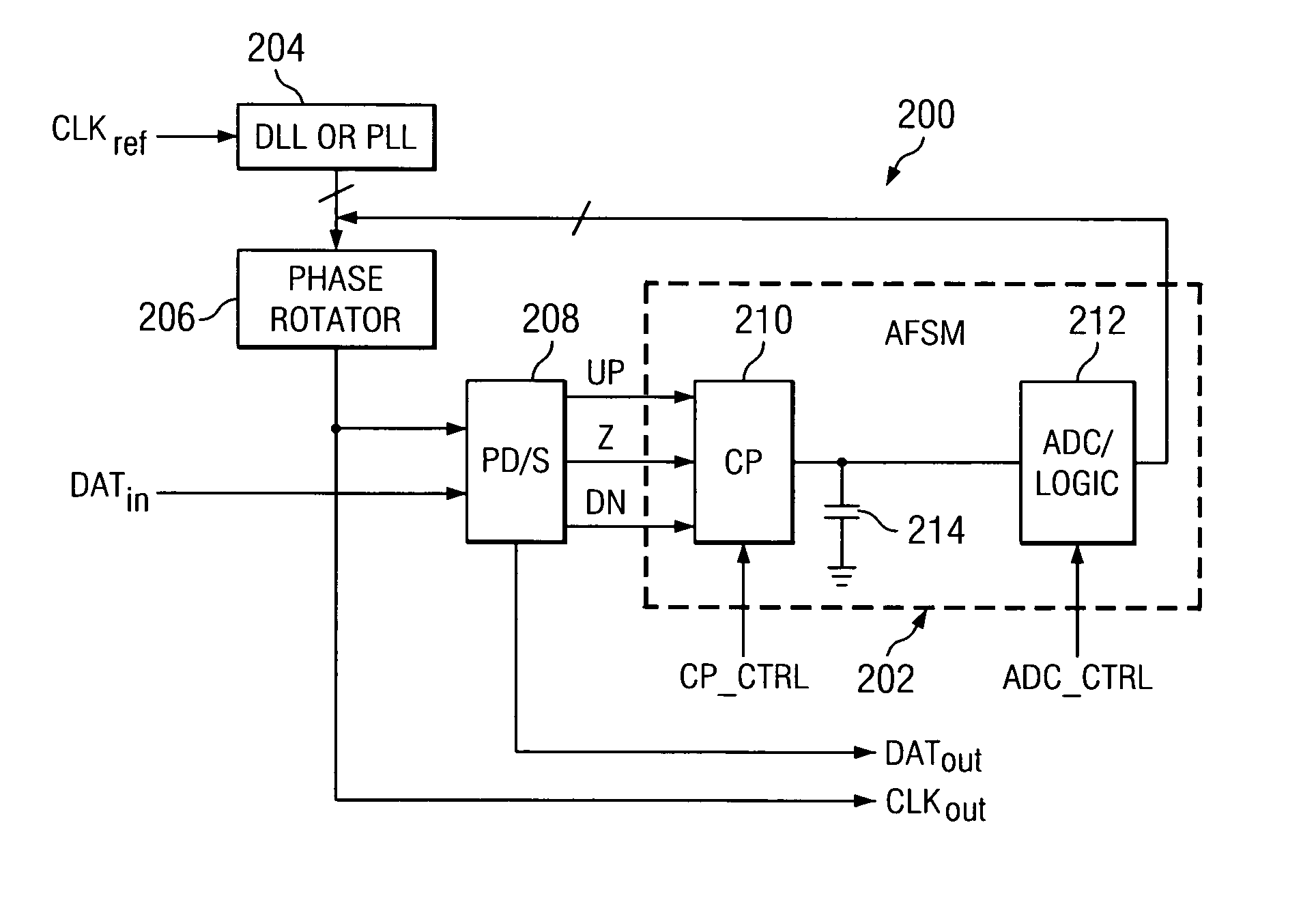
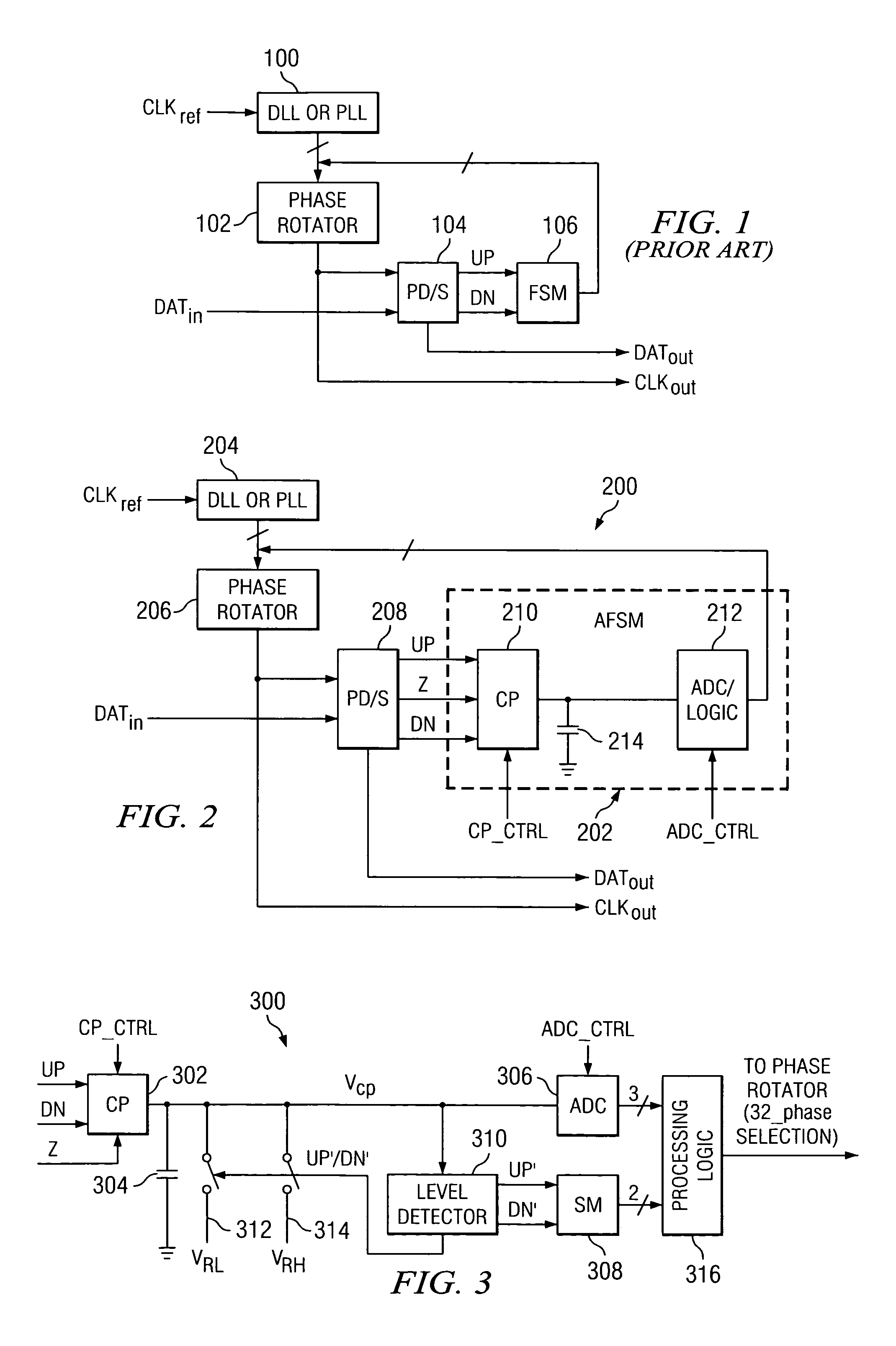
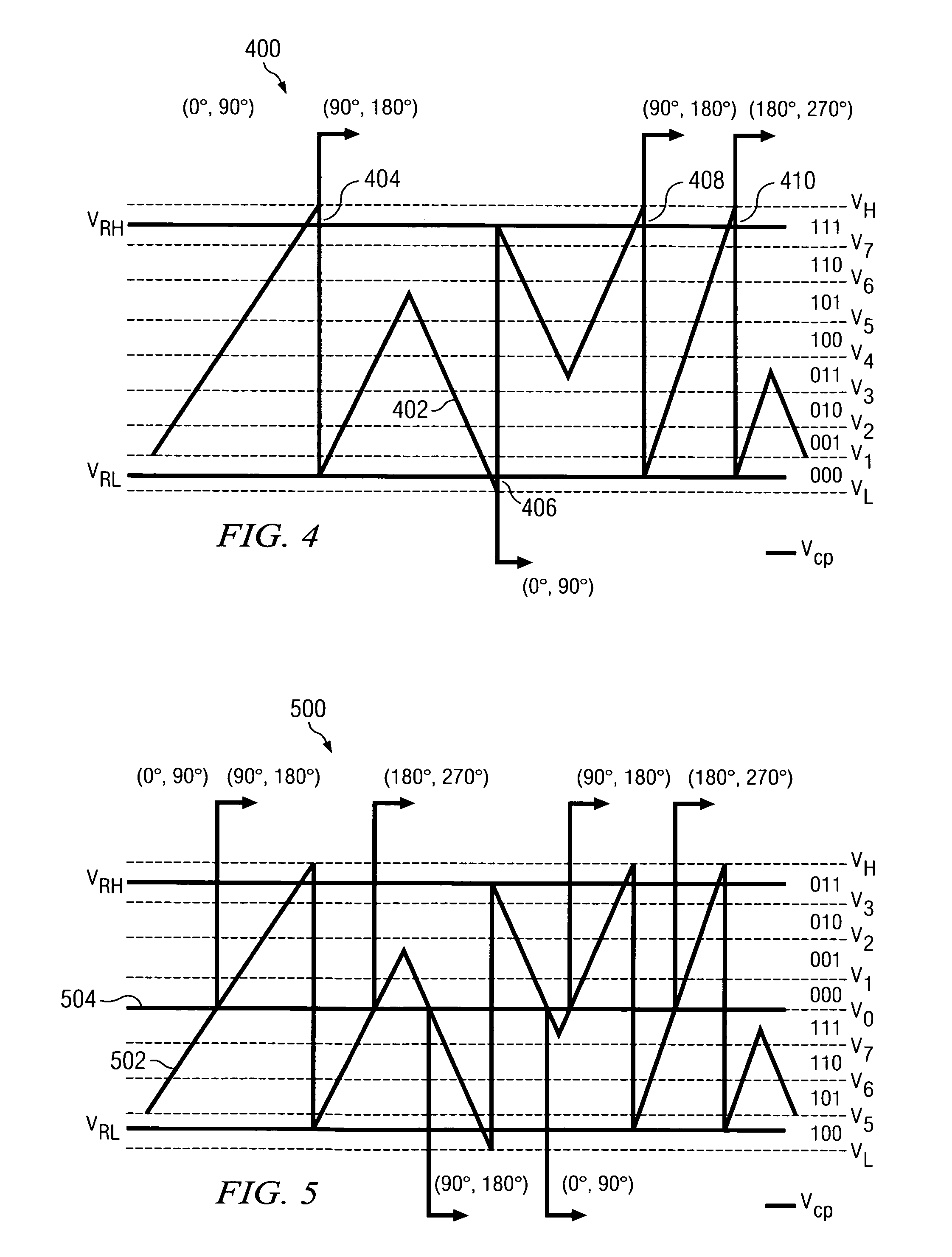
Semidigital delay-locked loop using an analog-based finite state machine
InactiveUS6927611B2Increase powerComplexity of hardwarePulse automatic controlSynchronising arrangementDigital signal processingEngineering
A low-power full-rate semidigital DLL architecture using an analog-based FSM (AFSM). The AFSM is a mixed-mode FSM in which analog integration is substituted for digital filtering, thus enabling a lower power implementation of the clock and data recovery function. An integrated voltage is converted to a digital code by an analog-to-digital converter (ADC), and the digital code is used either directly or after (low frequency) digital signal processing to control a controllable delay element, such as, a phase rotator, for data edge tracking.
Owner:GLOBALFOUNDRIES US INC
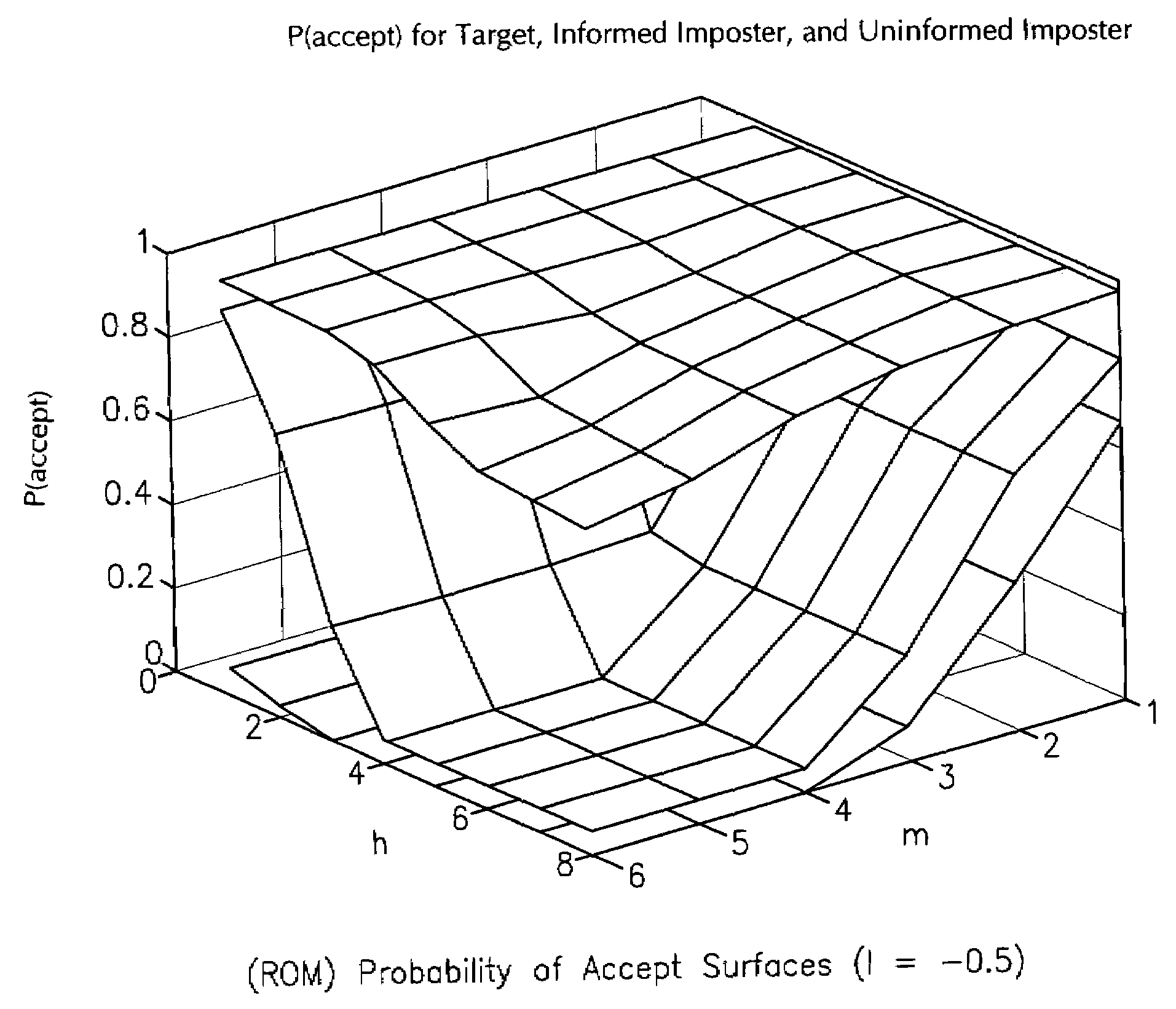
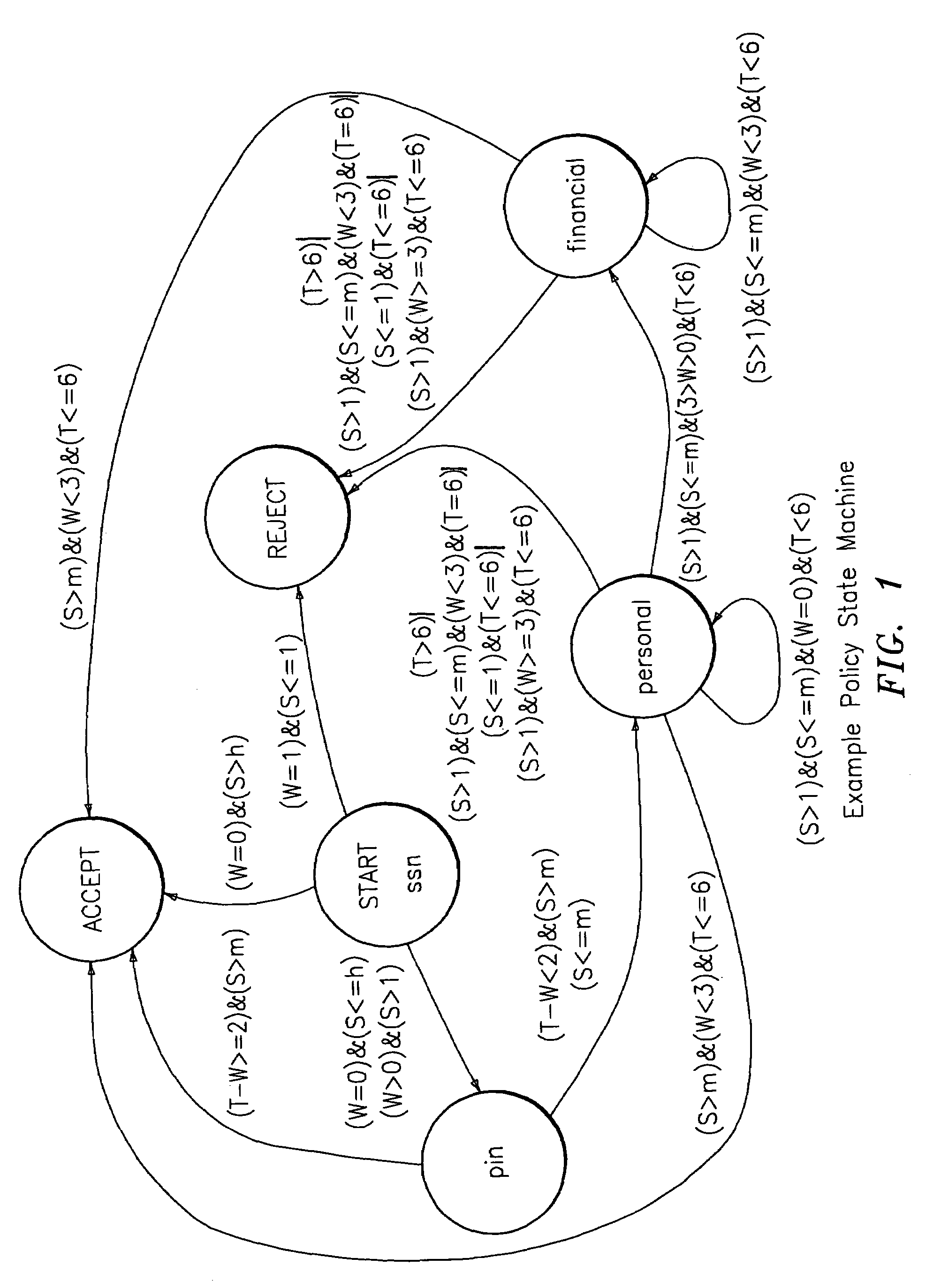
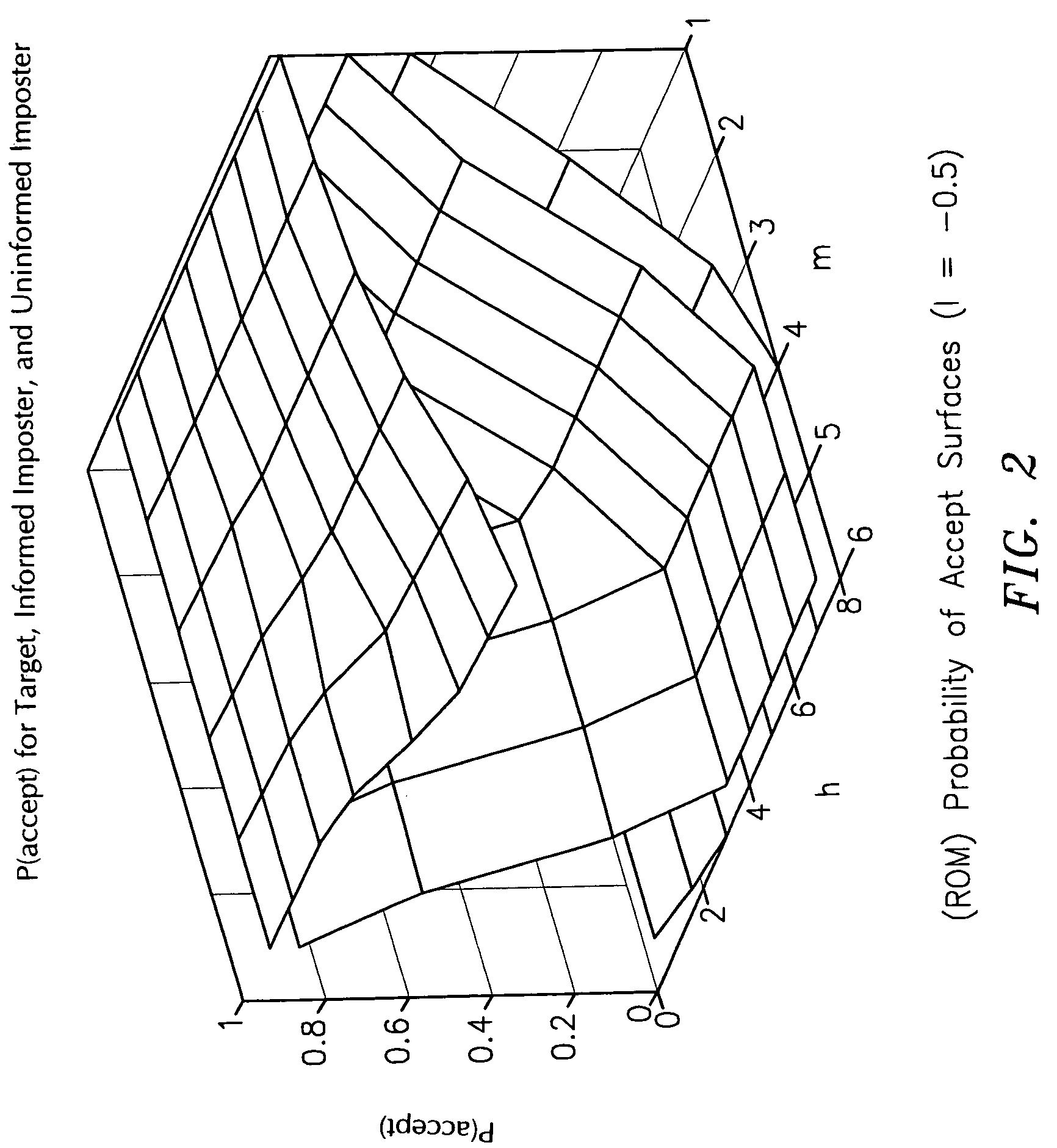
Policy analysis framework for conversational biometrics
InactiveUS7363223B2Digital data processing detailsMultiple digital computer combinationsSpeaker verificationFinite-state machine
The present invention describes a framework for the analytical and visual analysis and tuning of complex speaker verification systems guided by a policy finite state machine. The Receiver Operating Curve associated with the acoustic speaker recognition task is transformed into a multi-dimensional Receiver Operating Map (ROM), which results from a probabilistic analysis of the policy state machine. A Detection Cost Function (DCF) Map can be similarly generated. Results indicating that optimization over this surface (or the ROM) is an appropriate way to set thresholds are given.
Owner:GOOGLE LLC
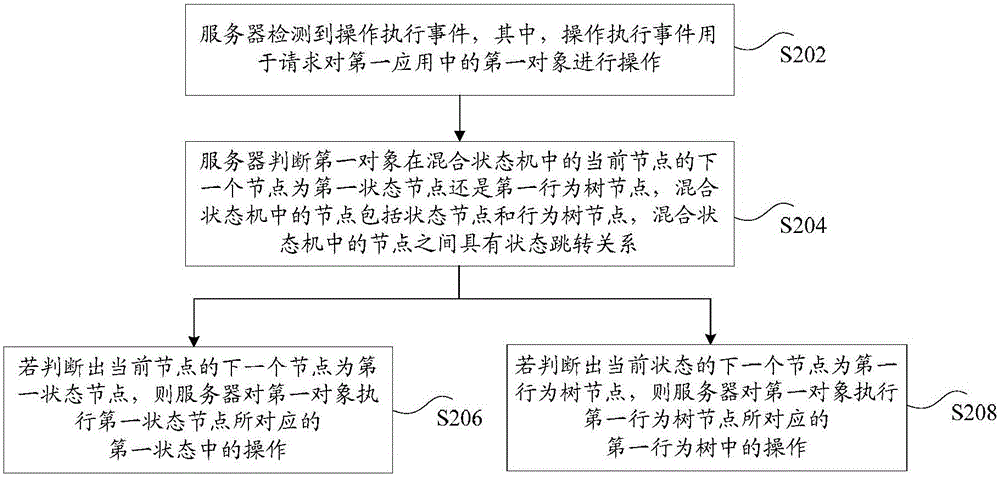
State control method and device
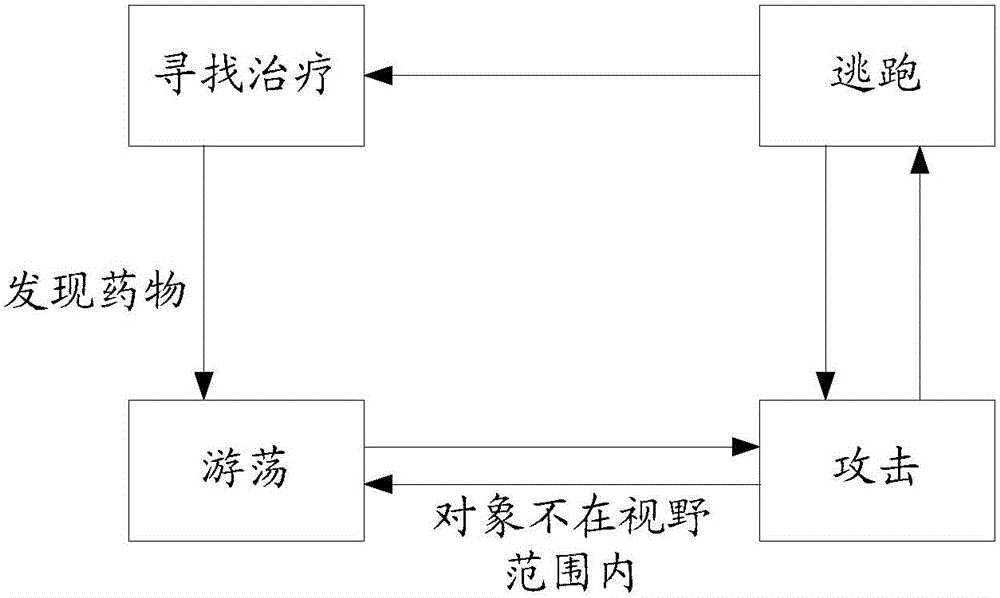
ActiveCN105656688AImprove operational efficiencySolve the technical problem of low efficiency of individual execution operationsProgram controlData switching networksVirtual finite-state machineBehavior Trees
The invention discloses a state control method and device. The method comprises the steps that a server detects an operation execution event, and the operation execution event is used for requesting for operating a first object in first application; the server judges whether the next node of a current node of the first object in a mixing state machine is a first state node or a first behavior tree node, nodes in the mixing state machine comprise state nodes and behavior tree nodes, and a state skip relationship exists between the nodes in the mixing state machine; if it is judged that the next node of the current node is the first state node, the server executes operation in a first state corresponding to the first state node on the first object; if it is judged that the next node of the current state is the first behavior tree node, the server executes operation in a first behavior tree corresponding to the first behavior tree node on the first object. The method solves the technical problem that when a finite state machine is used in the prior art for controlling, operation executing efficiency of individuals is low.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Finite state machine actuating device and method, and method for establishing and using finite state machine
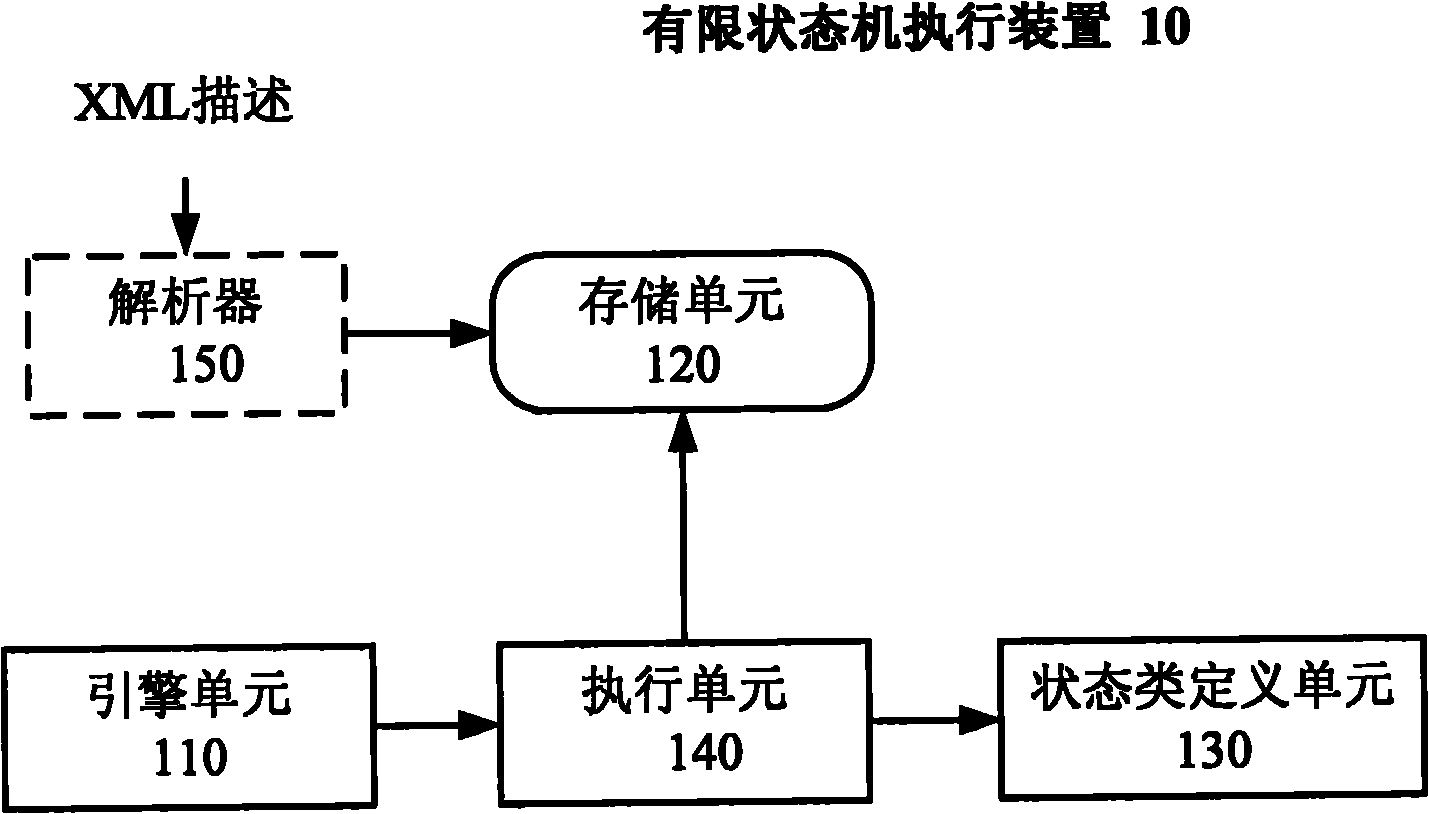
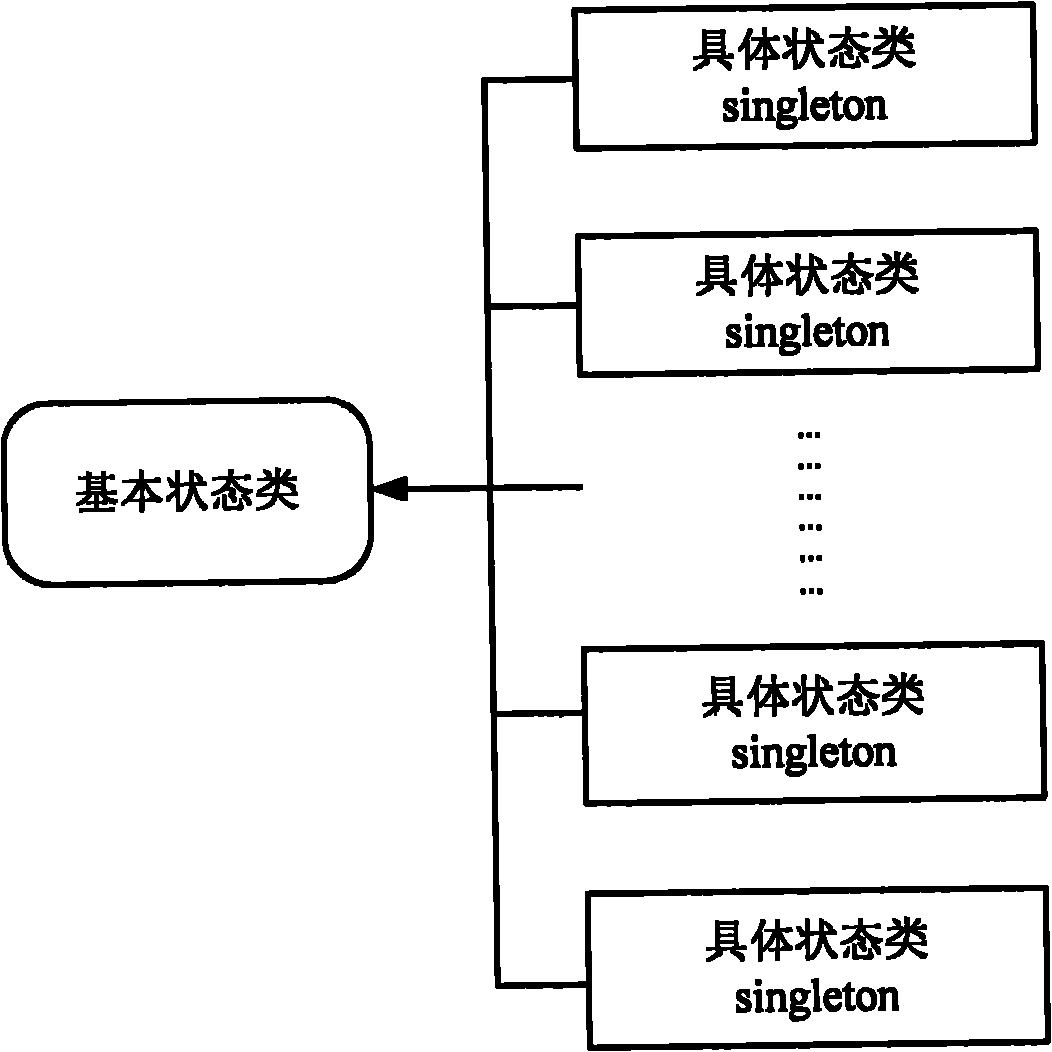
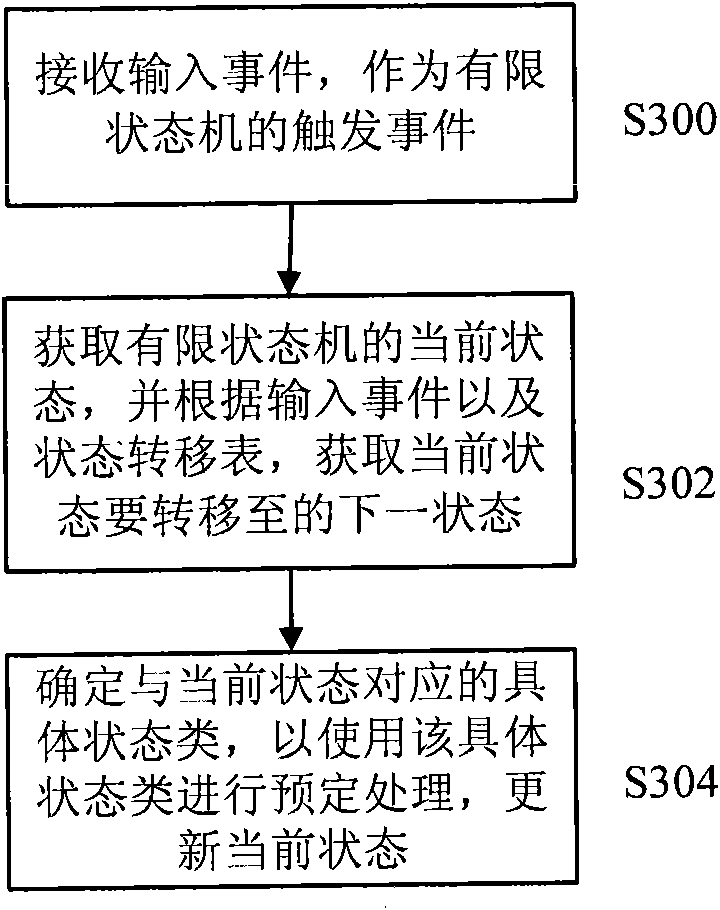
InactiveCN102103497AVersatilityLittle overheadSpecific program execution arrangementsMemory systemsResource consumptionTheoretical computer science
The invention discloses a finite state machine actuating device and method, and a method for establishing and using a finite state machine. The finite state machine actuating method comprises the following steps of: receiving a trigger event; acquiring the current state of the finite state machine and acquiring a next state to which a current state is to be shifted according to an input event and a state shifting table; and determining a specific state type which corresponds to the current state from one or more specific state types belonging to a basic state type according to the basic state type, performing predetermined processing by using the specific state type and updating the current state by using the acquired next state. By adopting the method, actuating logic of the finite state machine is improved in combination with the principle of an object-oriented state mode and a Flyweight mode, the specific state type of a single example mode is established, and repeated creation and deletion of an object are avoided, so that resource consumption of a system can be lowered on various application developing and modeling occasions and the like, and the actuating speed and efficiency of the application are improved.
Owner:ALCATEL LUCENT SAS
Using an embedded processor to implement a finite state machine
ActiveUS7131077B1CAD circuit designSoftware simulation/interpretation/emulationVirtual finite-state machineAssembly language
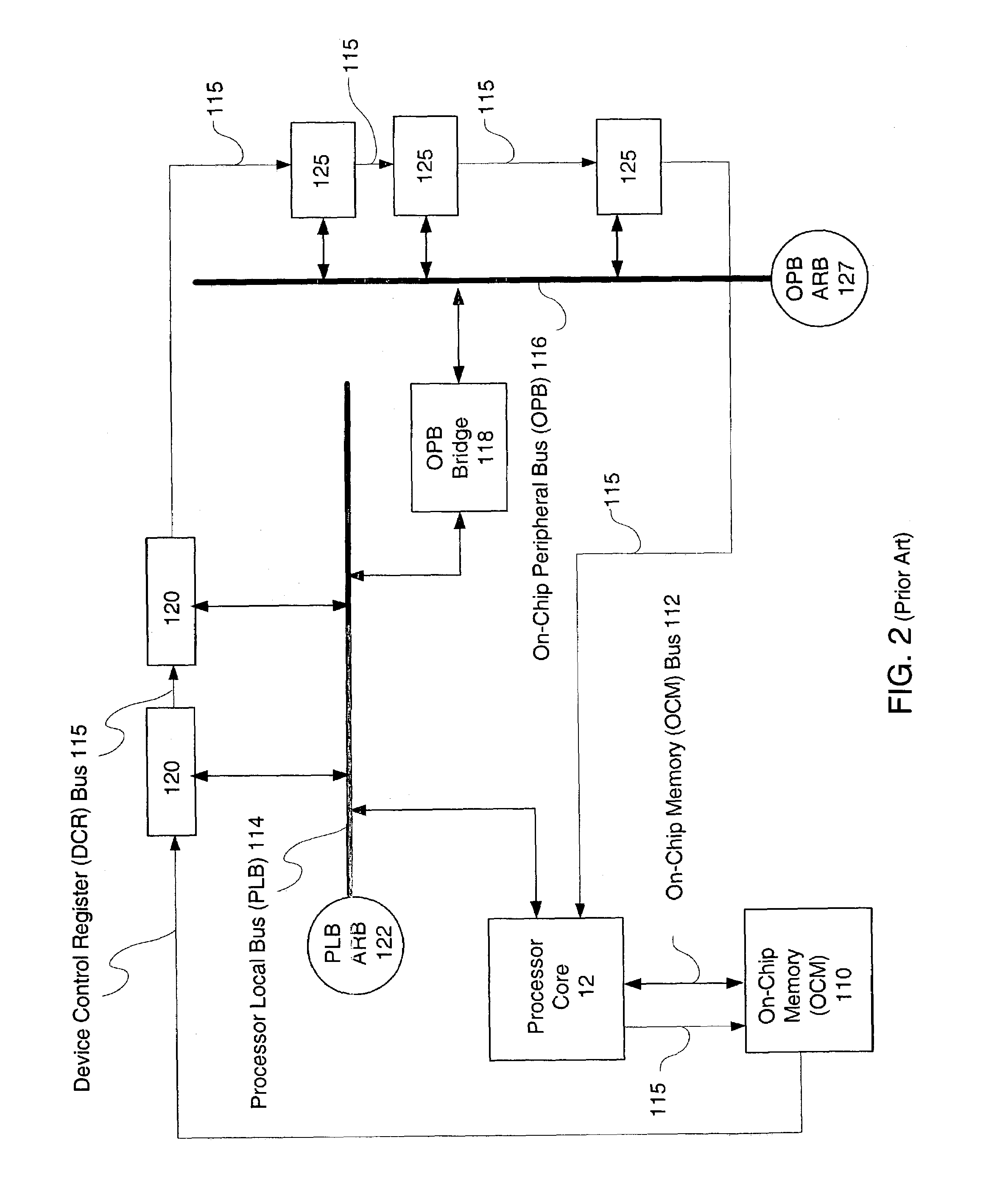
Method and System for implementing a Finite State Machine (FSM) using software executed on a processor and having accurate timing information is described, where the accurate timing information is determined without the need to execute the software. An exemplary embodiment includes an IC having an embedded processor and a programmable logic fabric, where part or all of an FSM is implemented using assembly language code stored in a memory, for example, a cache memory, of the embedded processor.
Owner:XILINX INC
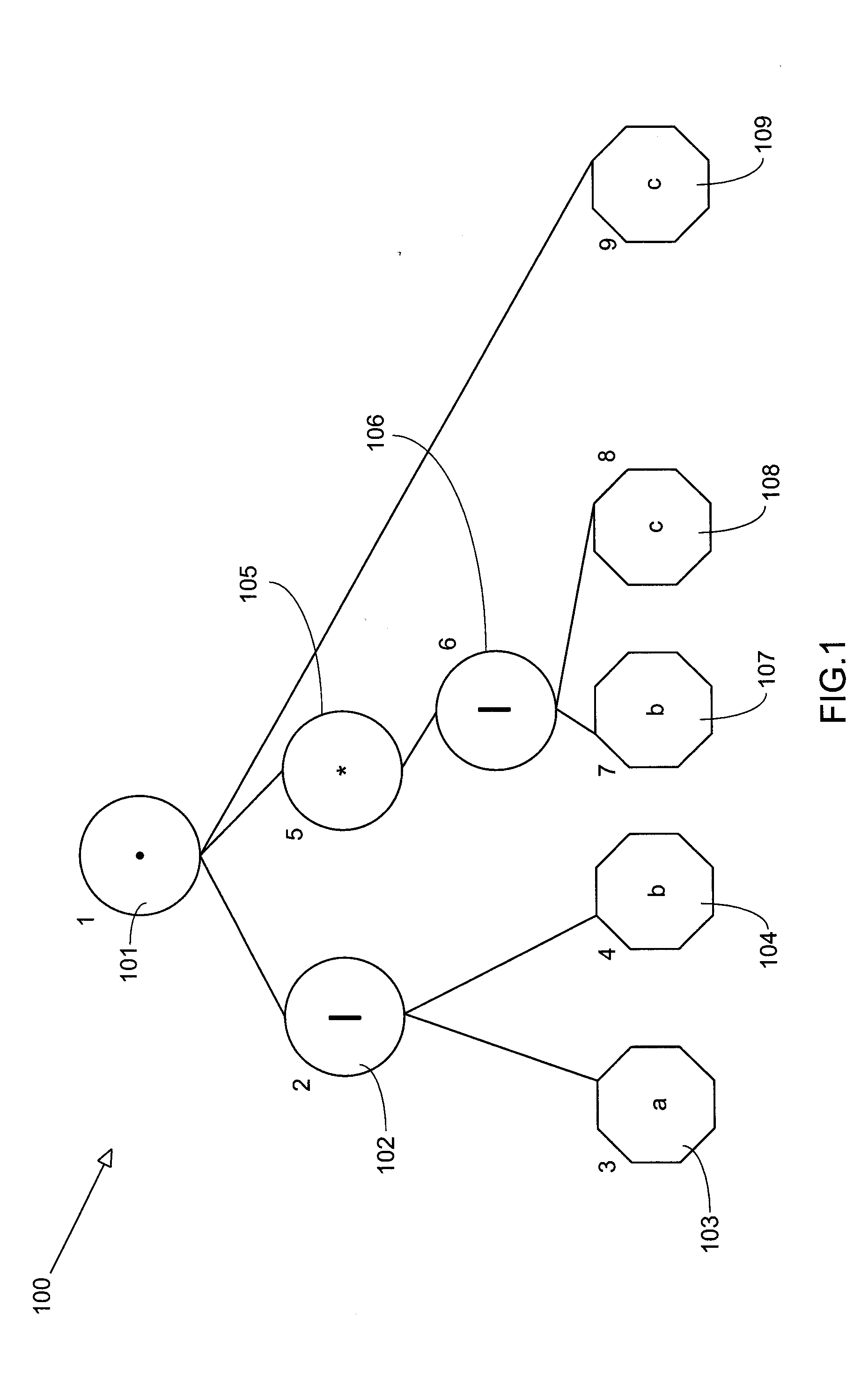
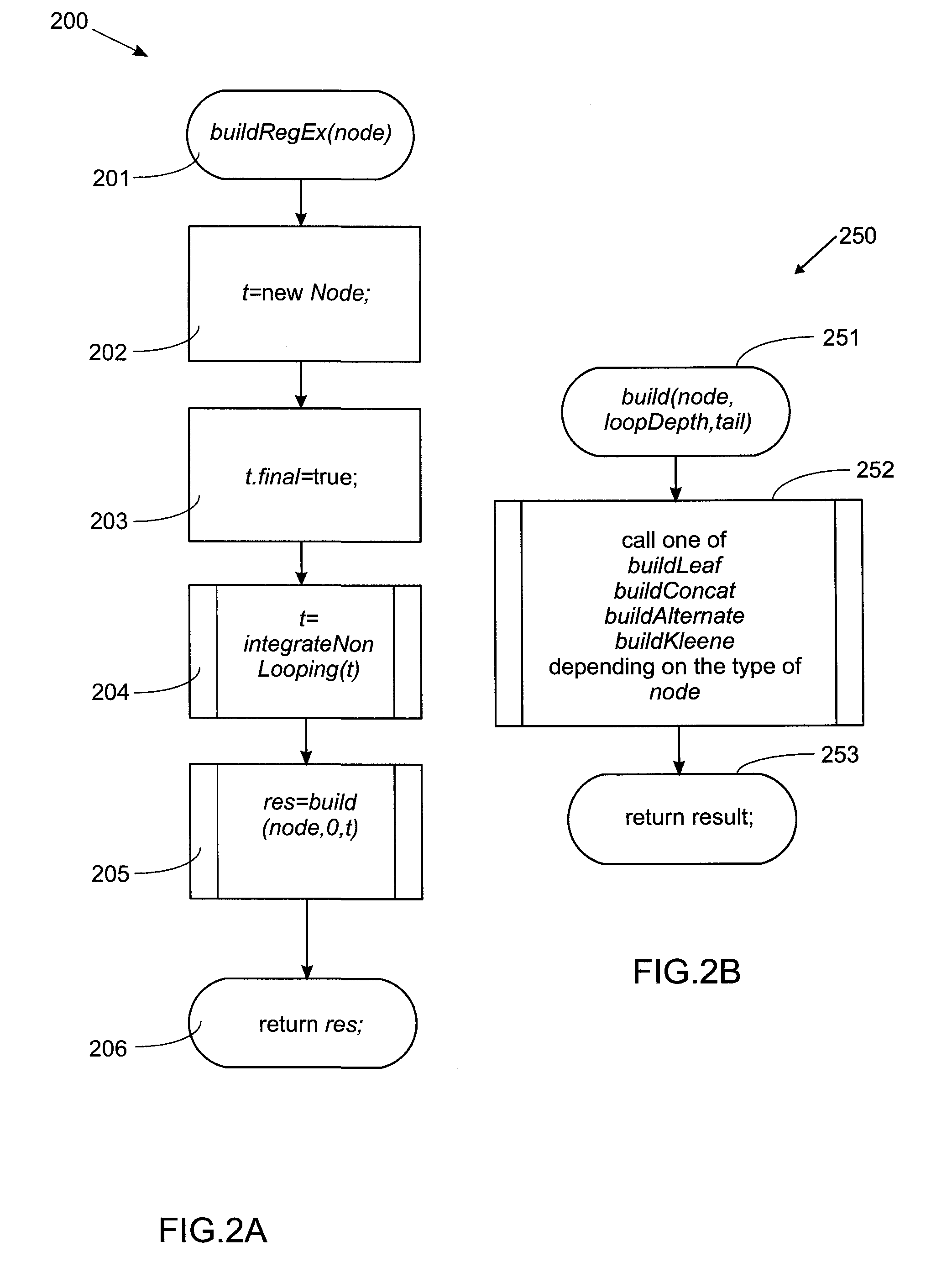
Direct construction of finite state machines
InactiveUS20100114811A1Reduce complexitySave a lot of spaceKnowledge representationSpecial data processing applicationsNODALConcatenation
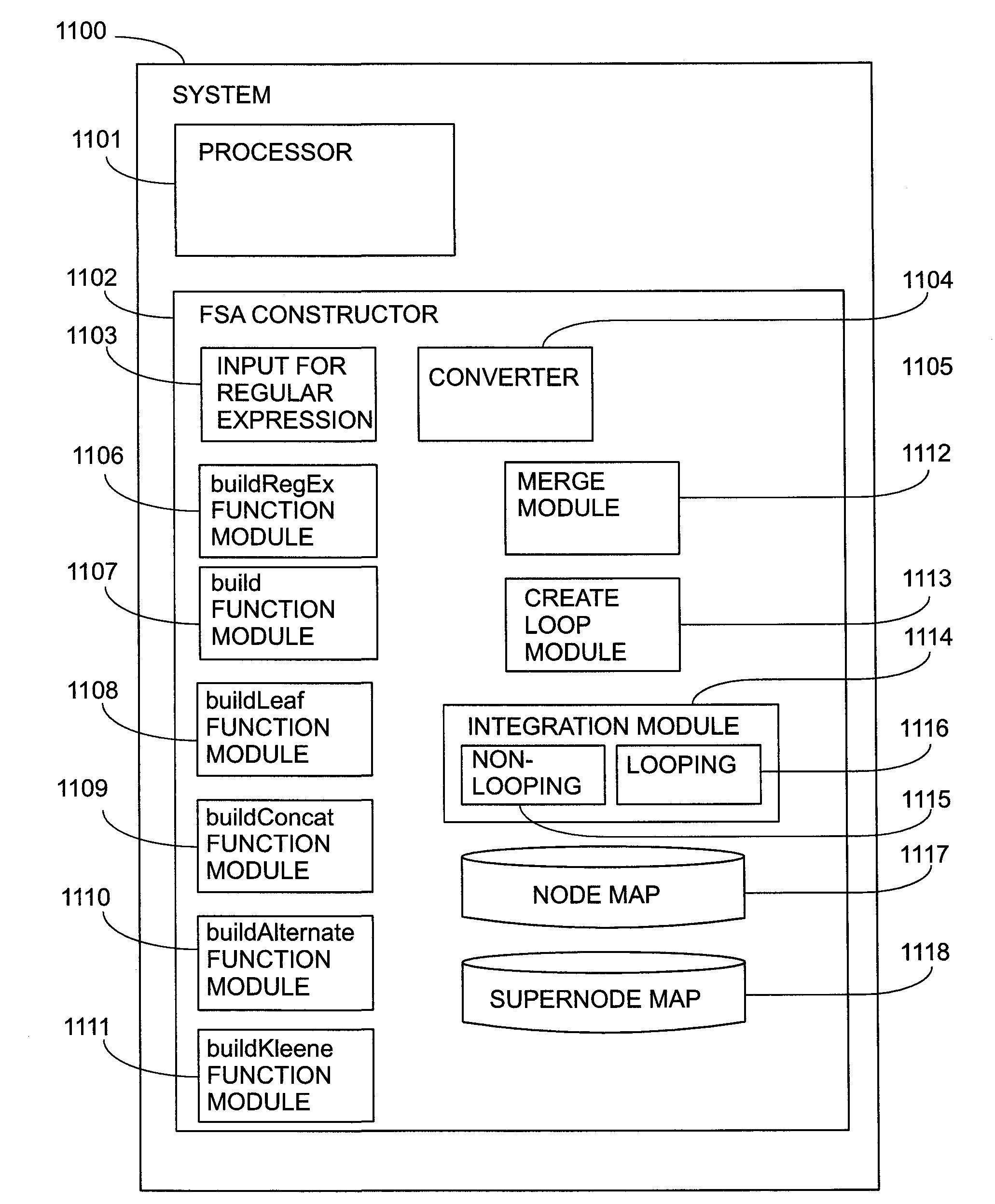
A method and system for direct construction of a minimal deterministic finite state machine corresponding to a regular expression are provided. The method includes providing a regular expression represented as a regular expression tree with nodes of operators and leaves of elementary character transitions and traversing the regular expression tree recursively to build minimal finite state automata (FSAs) corresponding to the branches of the tree, wherein the FSAs end in a specified tail automaton. The operators are concatenation, alternation, and Kleene closure. A concatenation operation is performed by recursive construction in reverse order wherein each automaton built becomes the tail for the preceding argument of the operation. An alternation operation is performed by recursively building automata corresponding to the arguments of the operation with the same tail and merging them. A Kleene closure operation is performed by: building an automaton terminating in a unique marker; merging the automaton with the tail automaton to form a combined automaton; and traversing the combined automaton to expand the marker into transitions and states to achieve the intended behaviour.
Owner:IBM CORP
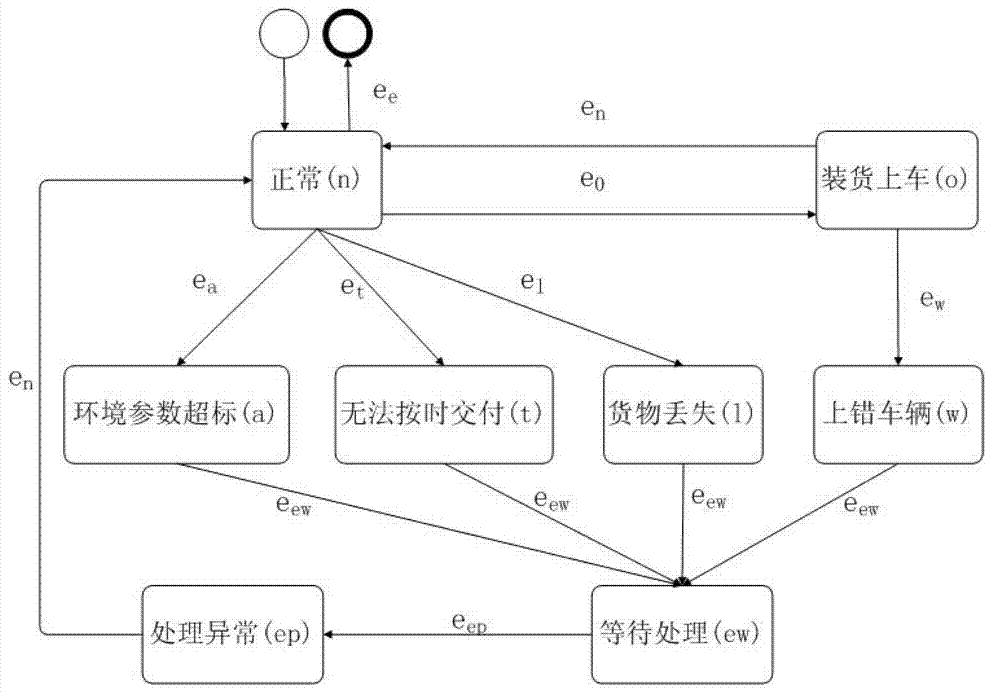
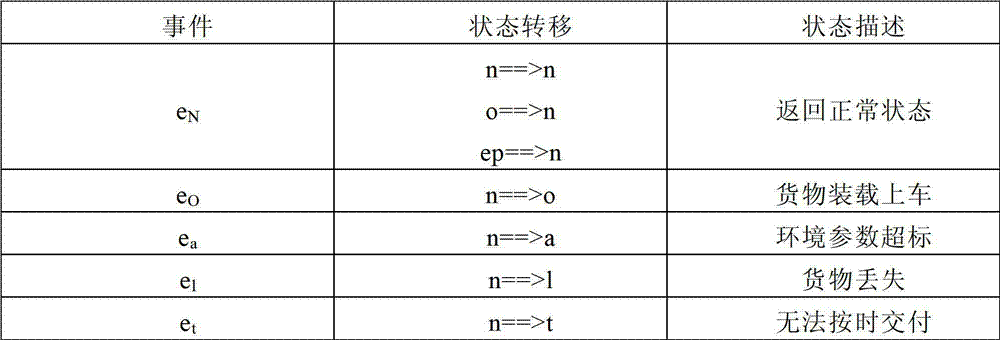
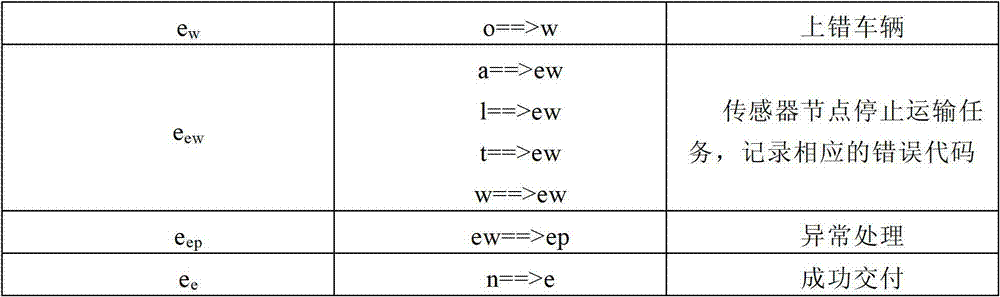
Finite state machine-based parcel transporting state monitoring method
InactiveCN103049838AAchieve autonomous controlReduce the burden onNetwork topologiesLogisticsLogistics managementVirtual finite-state machine
The invention provides a finite state machine-based parcel transporting state monitoring method, which is used for monitoring the transporting state of a parcel in a logistics transportation system. The aim of monitoring the transportation process of the parcel in real time is fulfilled by modeling aiming at the transporting state of the parcel during the overall transportation process, monitoring various events in the parcel through a wireless sensor node built in the parcel, skipping to different transporting states according to a finite state machine, and taking corresponding treatment measures for each state. According to the method, the monitoring of the parcel transporting state is realized by the wireless sensor node with sensing capacity and certain computing capacity; and analysis, treatment and decision making can be performed without transmitting the logistics state information to a background server, so that the decision making and the treatment of the parcel are performed more timely, the autonomous control of the parcel transporting state is realized, the burden of the background server is lightened, and the optimization of a logistics network is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
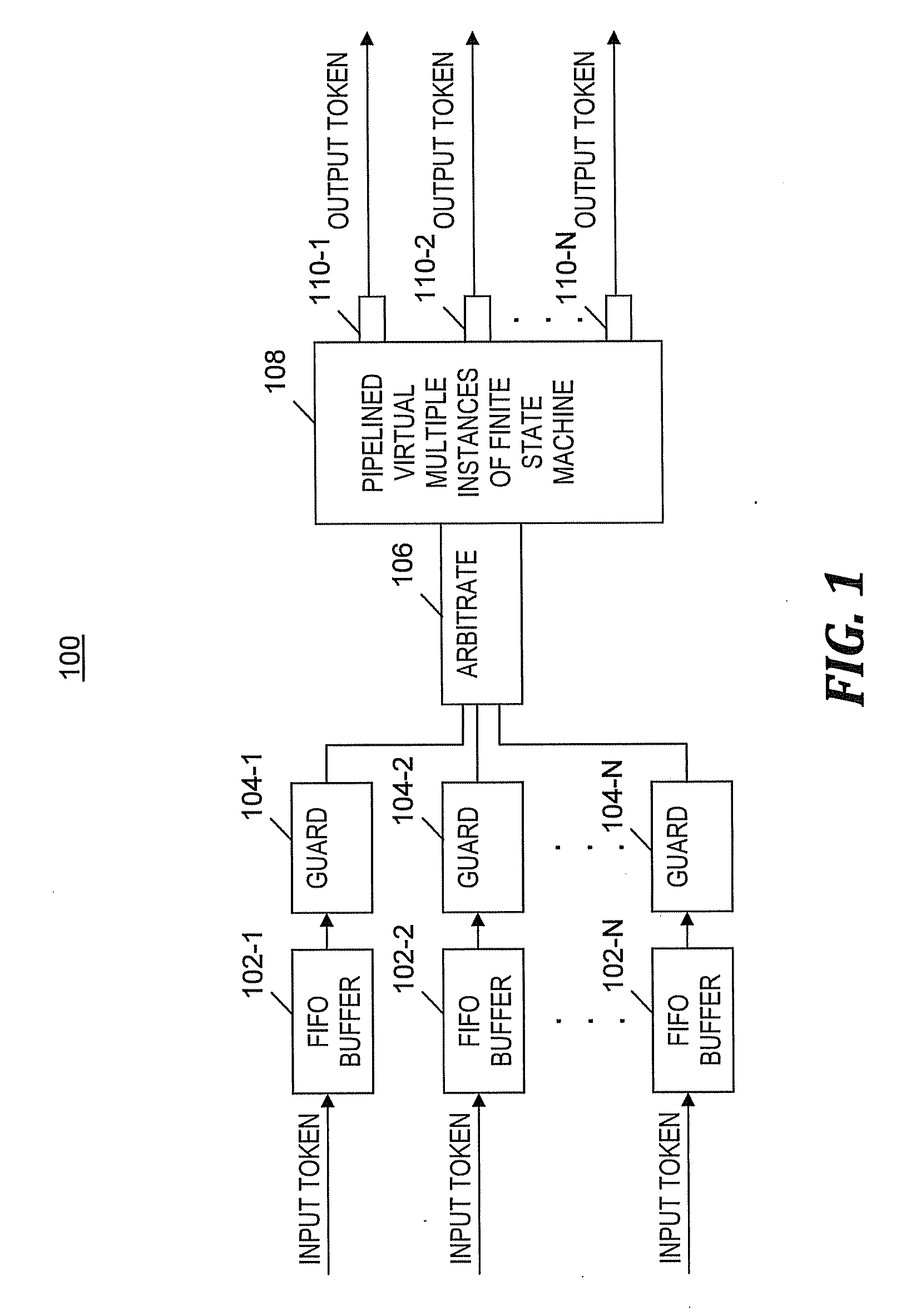
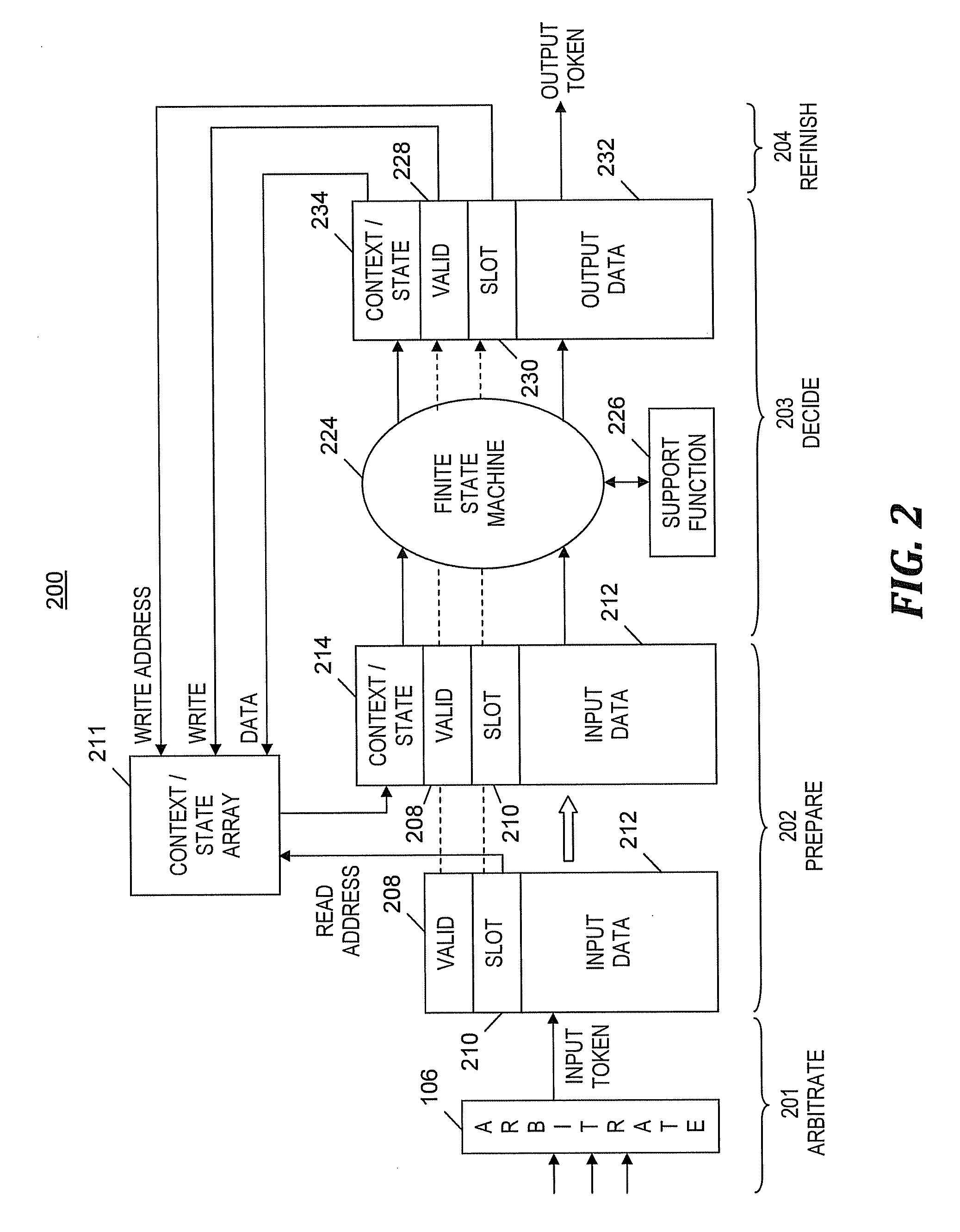
Efficiently implementing a plurality of finite state machines
InactiveUS20110055510A1Reduce complexityImprove portabilityDigital data processing detailsMemory adressing/allocation/relocationVirtual finite-state machineTheoretical computer science
A method and program product for processing data by a pipeline of a single hardware-implemented virtual multiple instance finite state machine (VMI FSM). An input token of multiple input tokens is selected to enter a pipeline of the VMI FSM. The input token includes a reference to an FSM instance. In one embodiment, the reference is an InfiniBand QP number. After being received at the pipeline, a current state and context of the FSM instance are fetched from an array based on the reference and inserted into a field of the input token. A new state of the FSM instance is determined and an output token is generated. The new state and the output token are based on the current state, context, a first input value, and an availability of a resource. The new state of the first FSM instance is written to the array.
Owner:IBM CORP
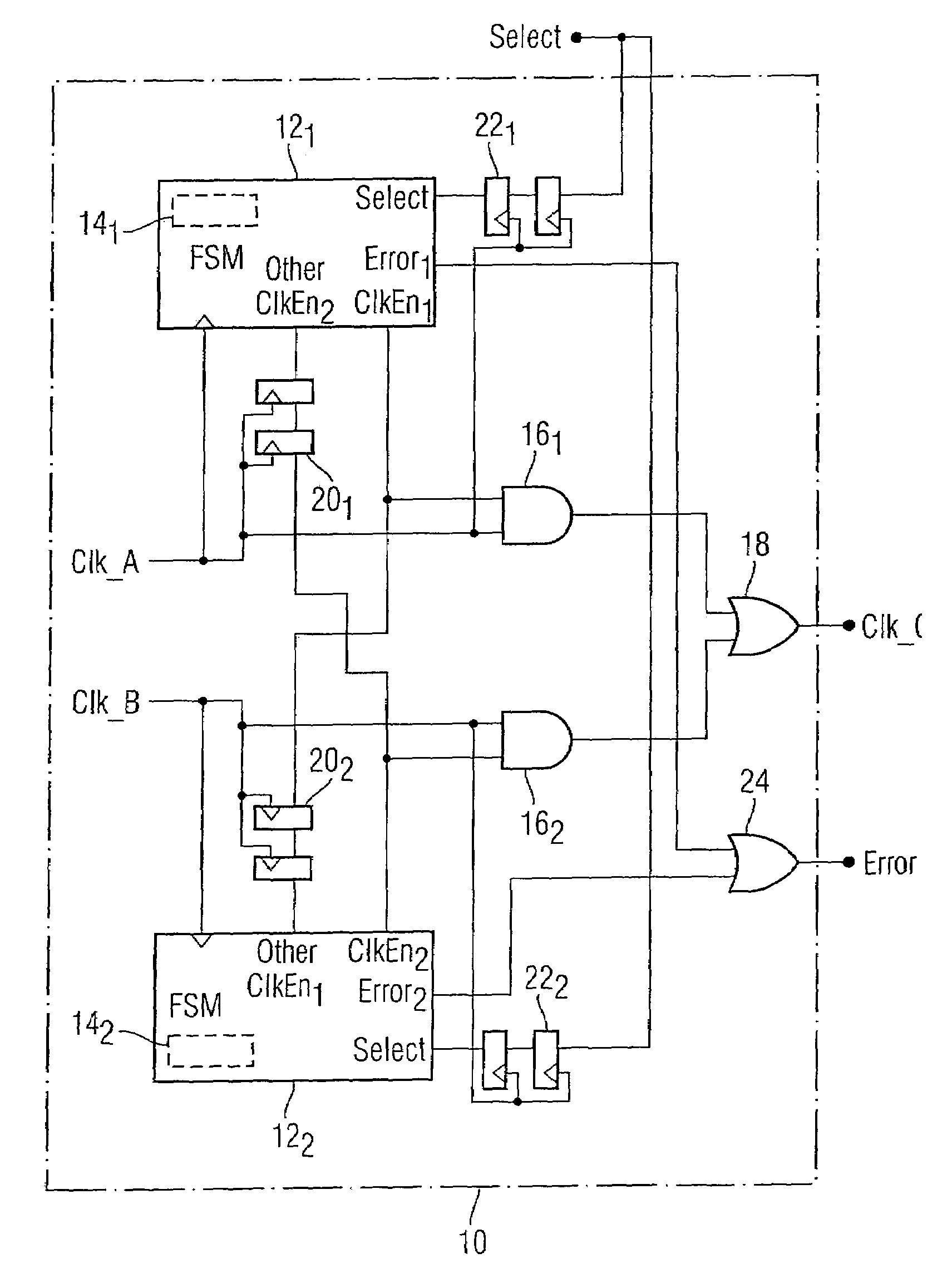
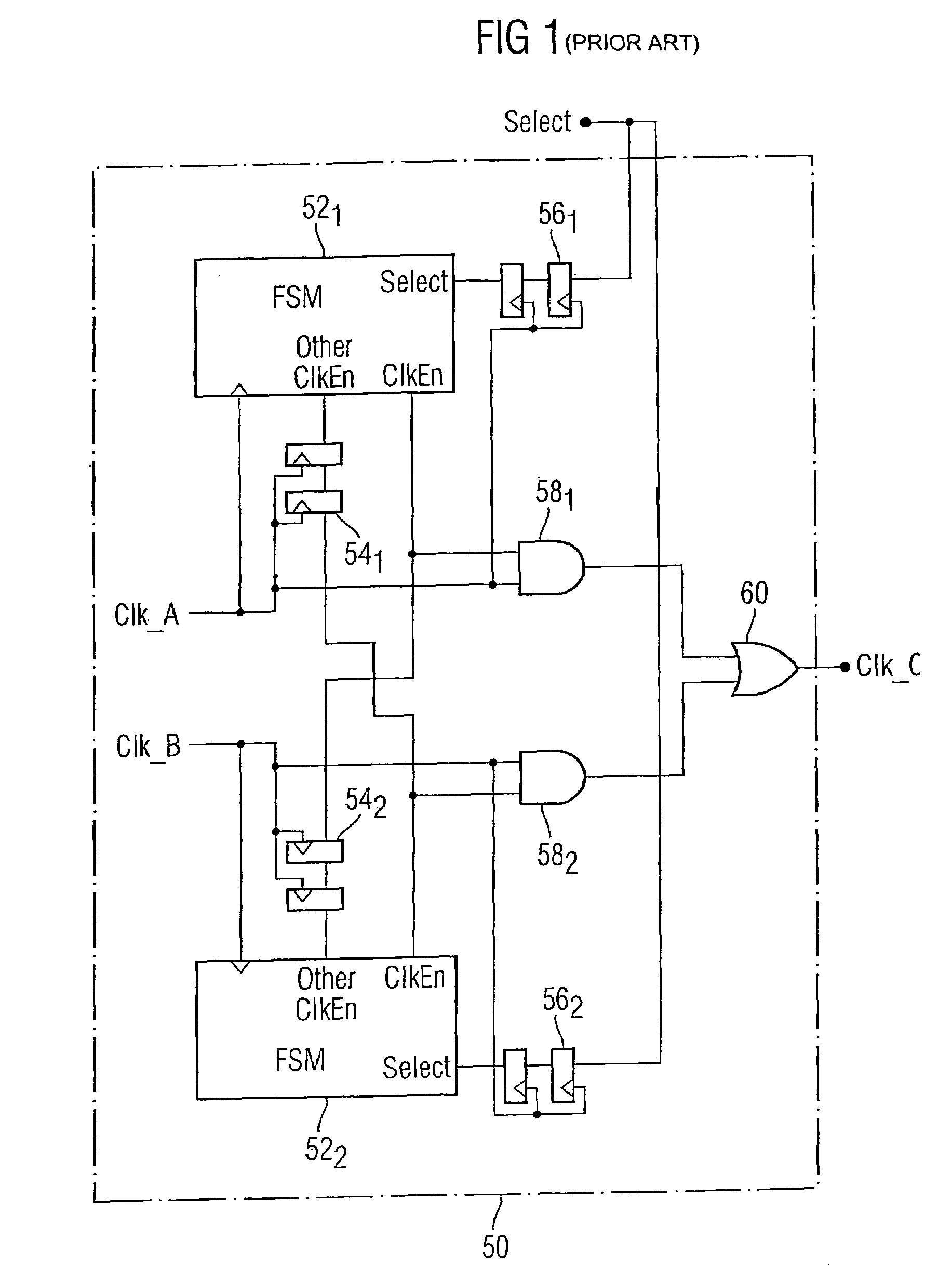
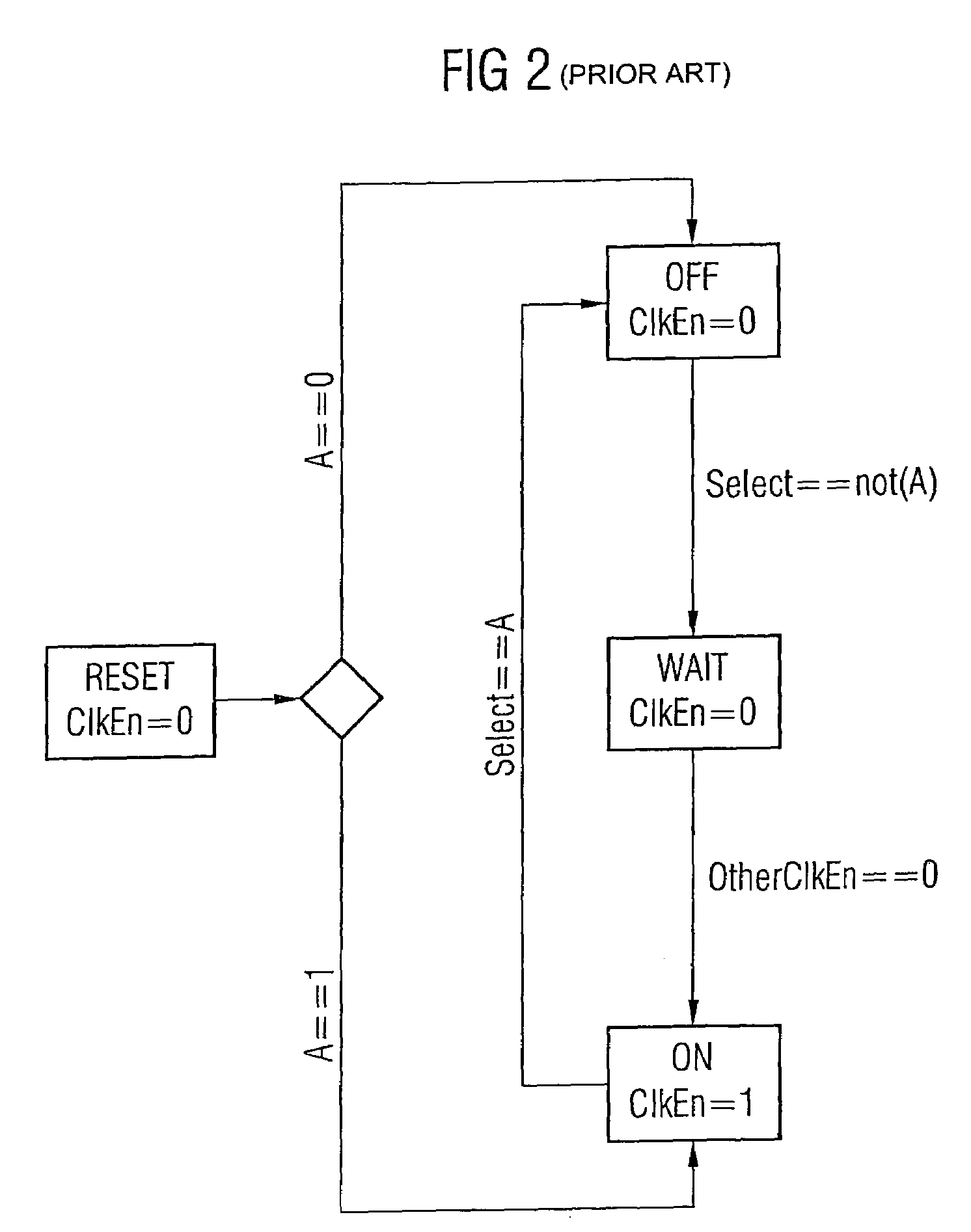
Digital clock switching means
A digital clock switching circuit and method is disclosed and is operable to deadlock-free switch a digital clock source for an integrated circuit. The circuit includes a first finite state machine associated with a first clock source and a second finite state machine associated with a second clock source. The finite state machines are connected to each other and monitor the current state of the other finite state machine. Each finite state machine receives an input select signal to control which clock source should be active and passed to a clock output. Each finite state machine includes a counter, wherein the counter associated with the active clock source is initialized to a first predetermined value when the input select signal indicates a switching off of the active clock source. The finite state machine associated with the active clock source enters a CHECK state and varies a count at each clock cycle. If the other finite state machine verifies a presence of its clock source before the counter reaches a second predetermined value the switch of the active clock source is effected.
Owner:INFINEON TECH AG
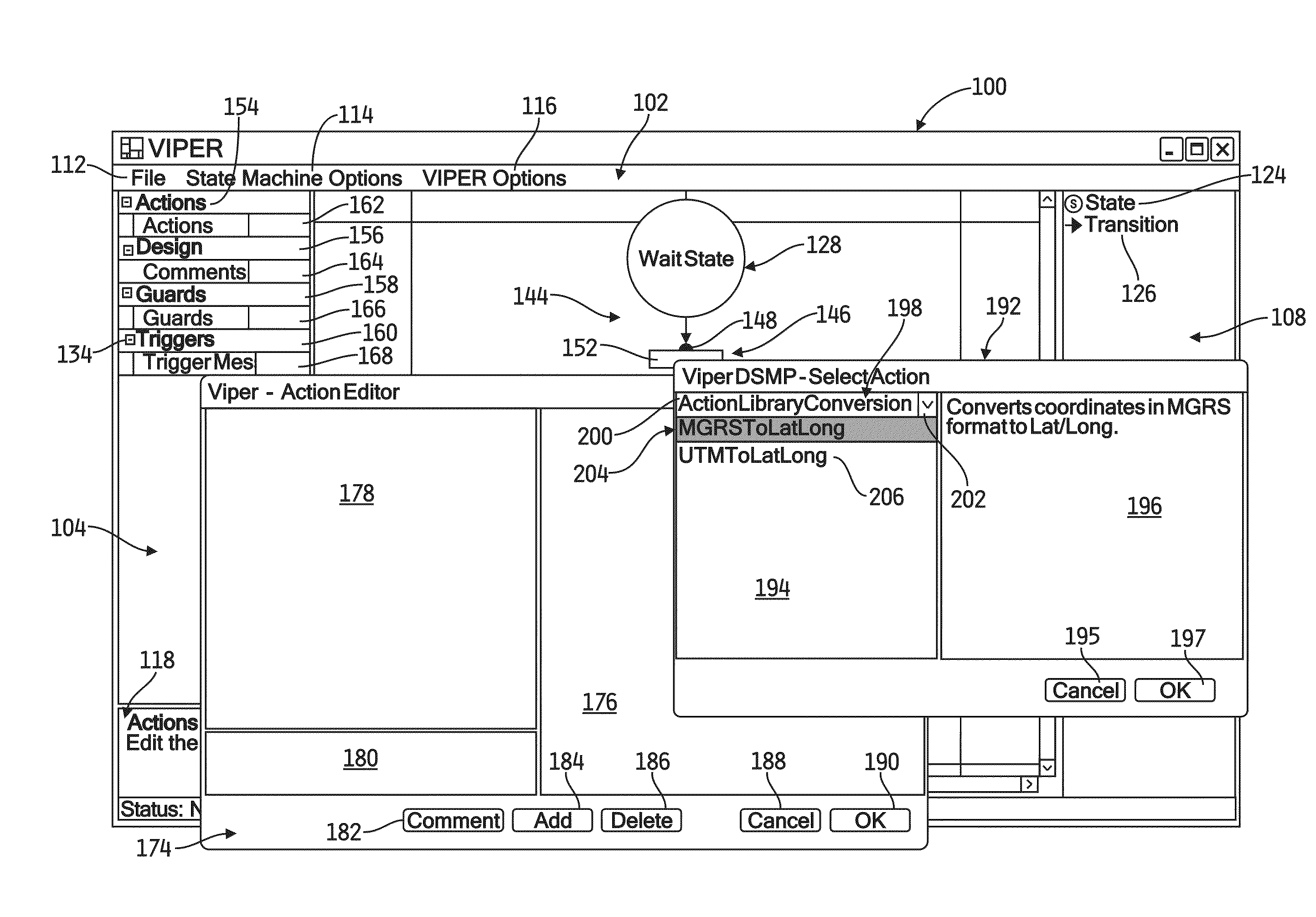
Finite state machine architecture for software development
ActiveUS20110161926A1Lower life cycle costsInefficiency associated with gapModel driven codeSpecific program execution arrangementsSoftware development processDisplay device
A system for developing an application program having functionality that corresponds to a finite state machine (FSM) model includes a visual interface that generates a graphical environment on a display for displaying an FSM model representing functionality of the program, a dynamic state machine processor that uses XML descriptions associated with the FSM model to generate the program executed at run-time, and an extensible graphic user interface that provides the end-user interface features to the end-user as generated during run-time by the processor based on the FSM model.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
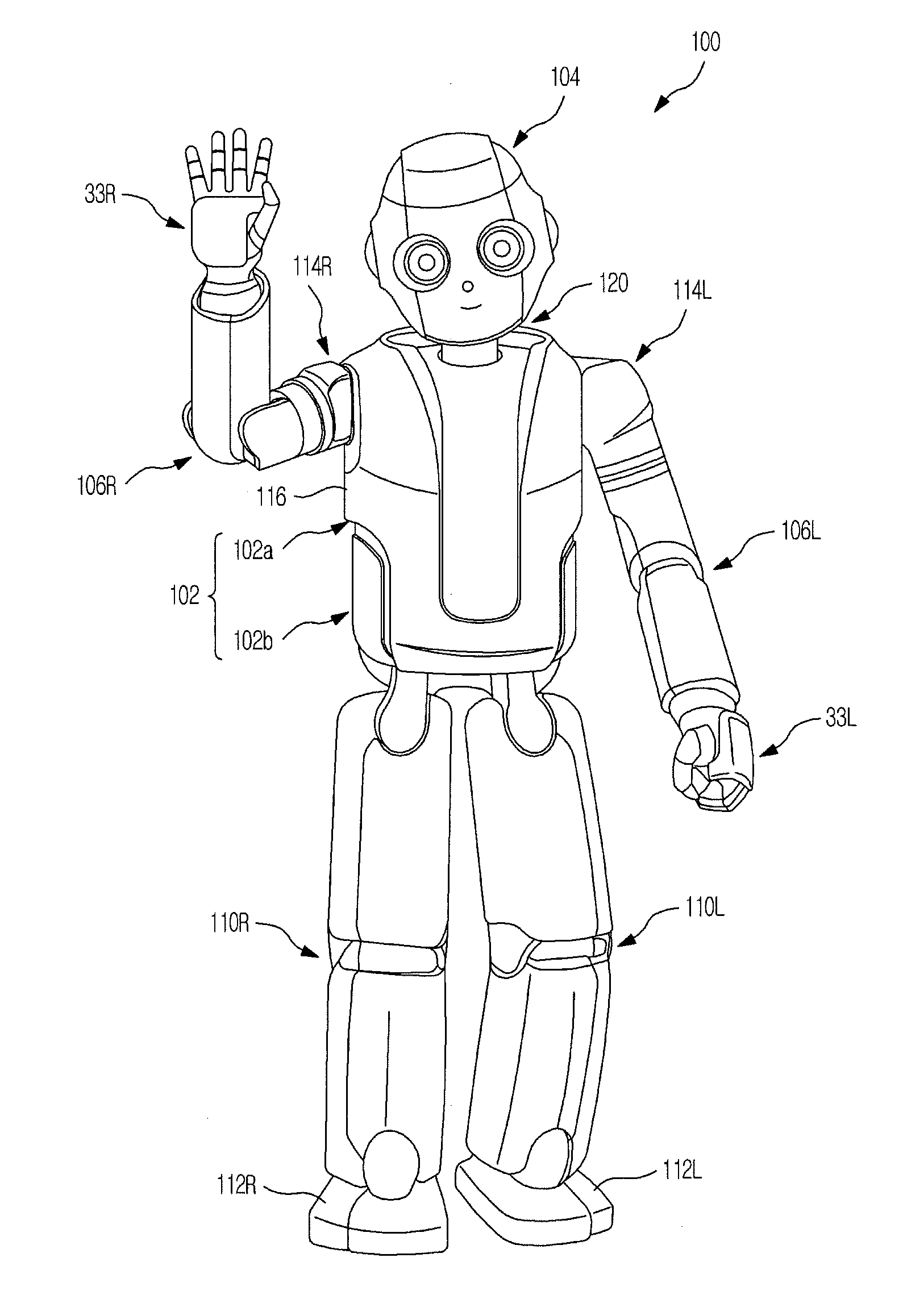
Humanoid robot and walking control method thereof
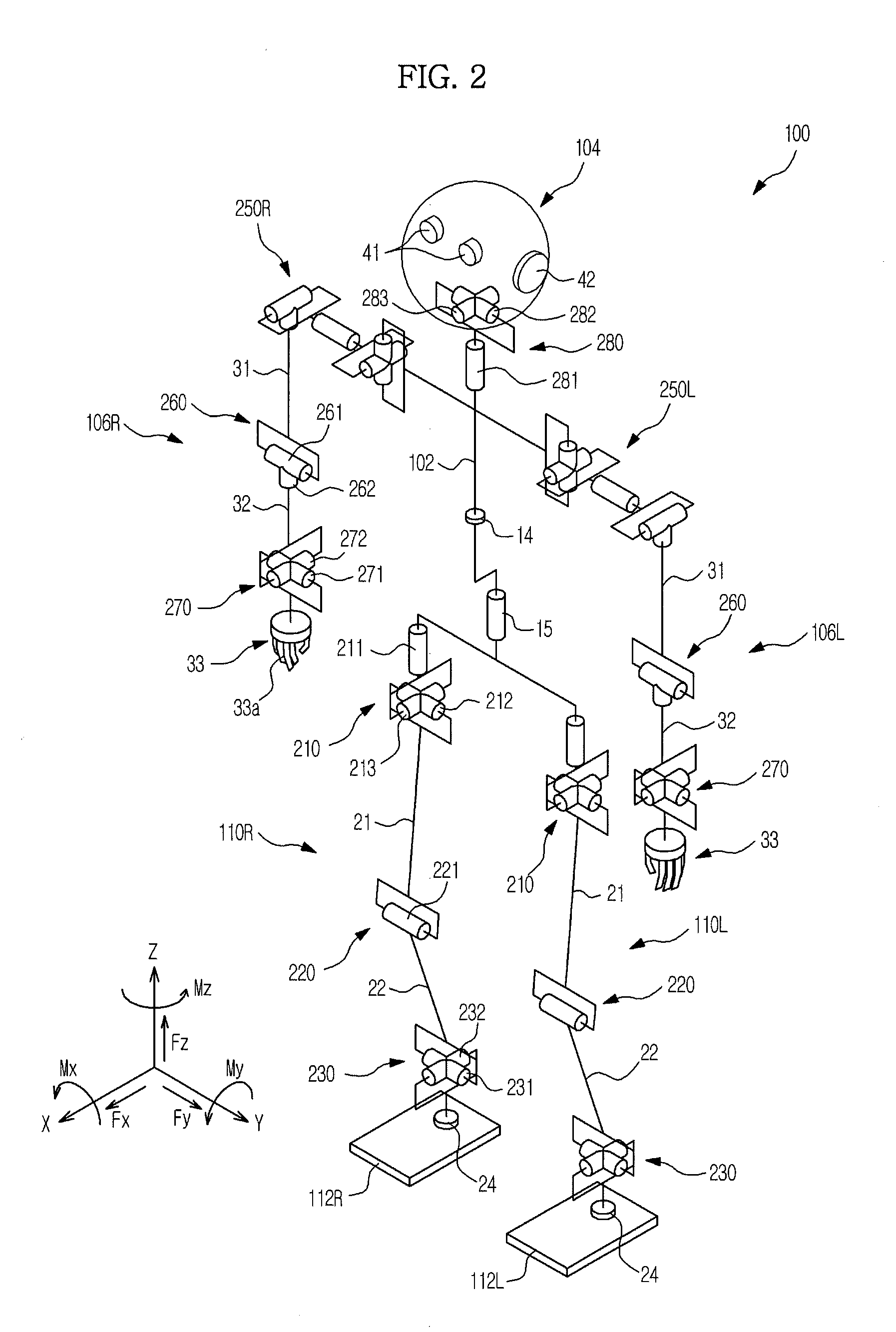
ActiveUS20110178636A1Pointing errorDistrict heating systemLighting and heating apparatusHumanoid robot naoVirtual finite-state machine
Disclosed herein are a humanoid robot that compensates for a zero moment point (ZMP) error during finite state machine (FSM)-based walking to achieve stable walking and a walking control method thereof. The humanoid robot compensates for a joint position trajectory command or a joint torque command using compensation values calculated based on situations divided according to the position of a calculated ZMP and the position of a measured ZMP in a stable region of the robot.
Owner:SAMSUNG ELECTRONICS CO LTD
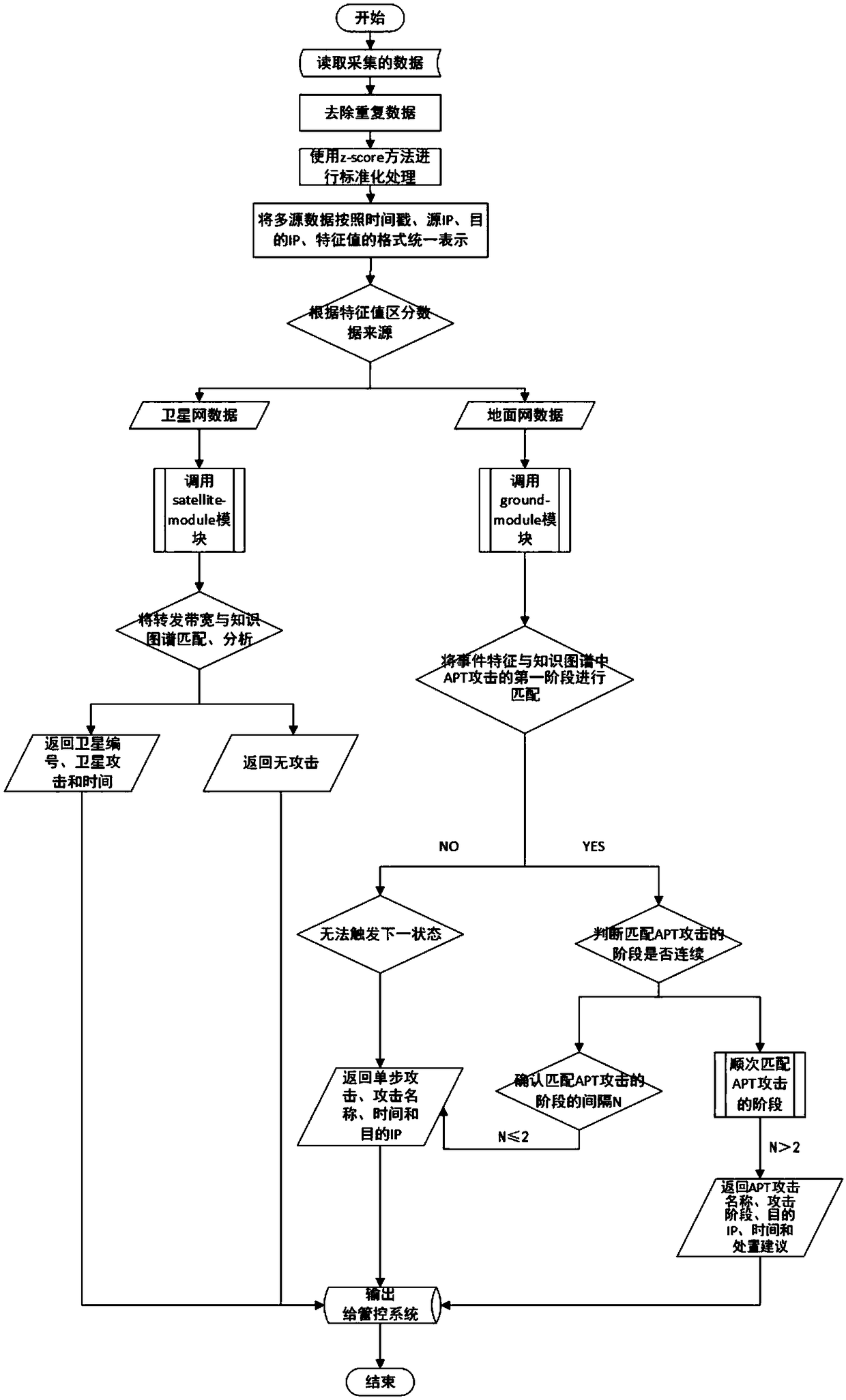
Space-ground integrated network security state analysis method based on finite state machine
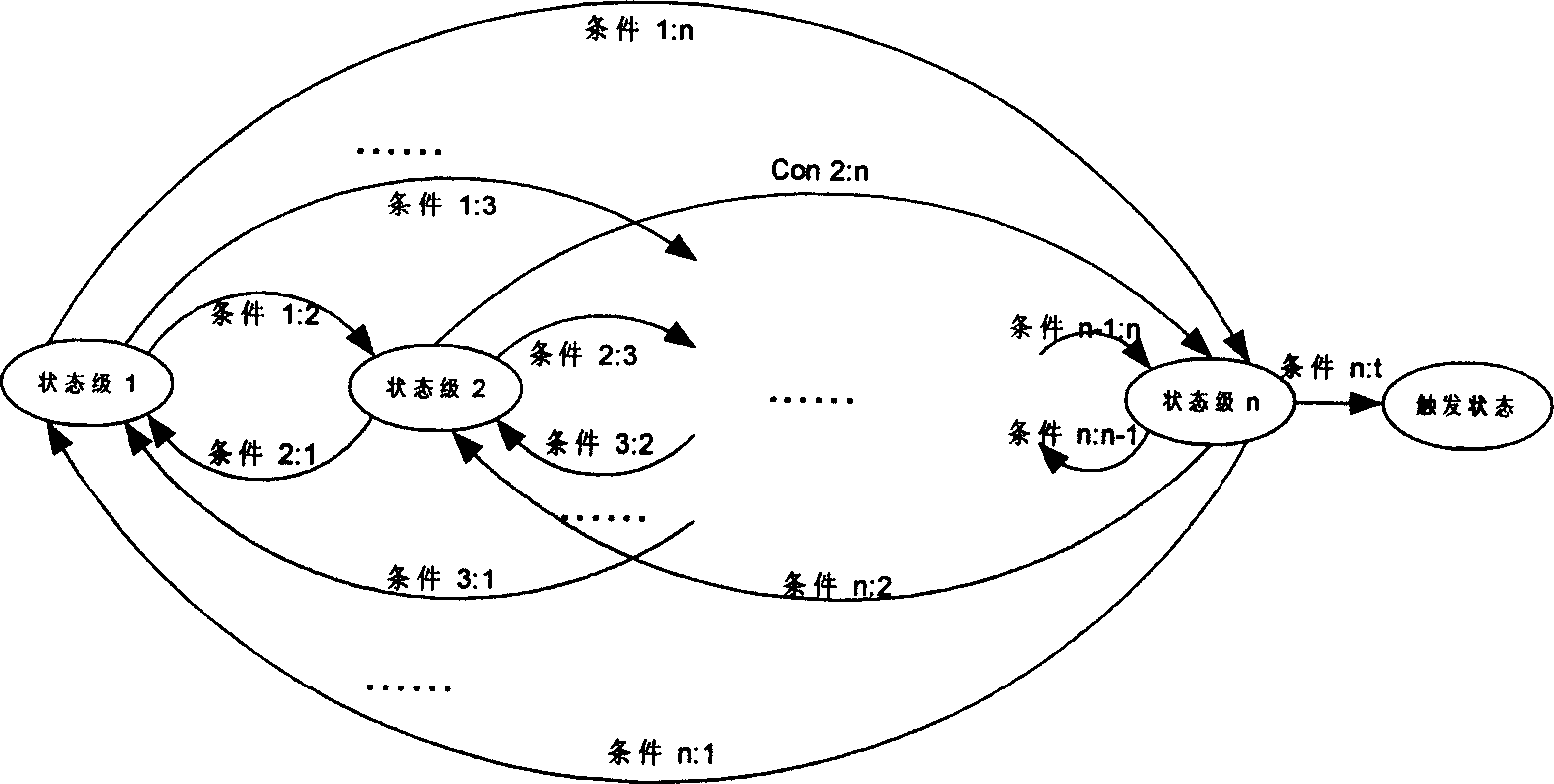
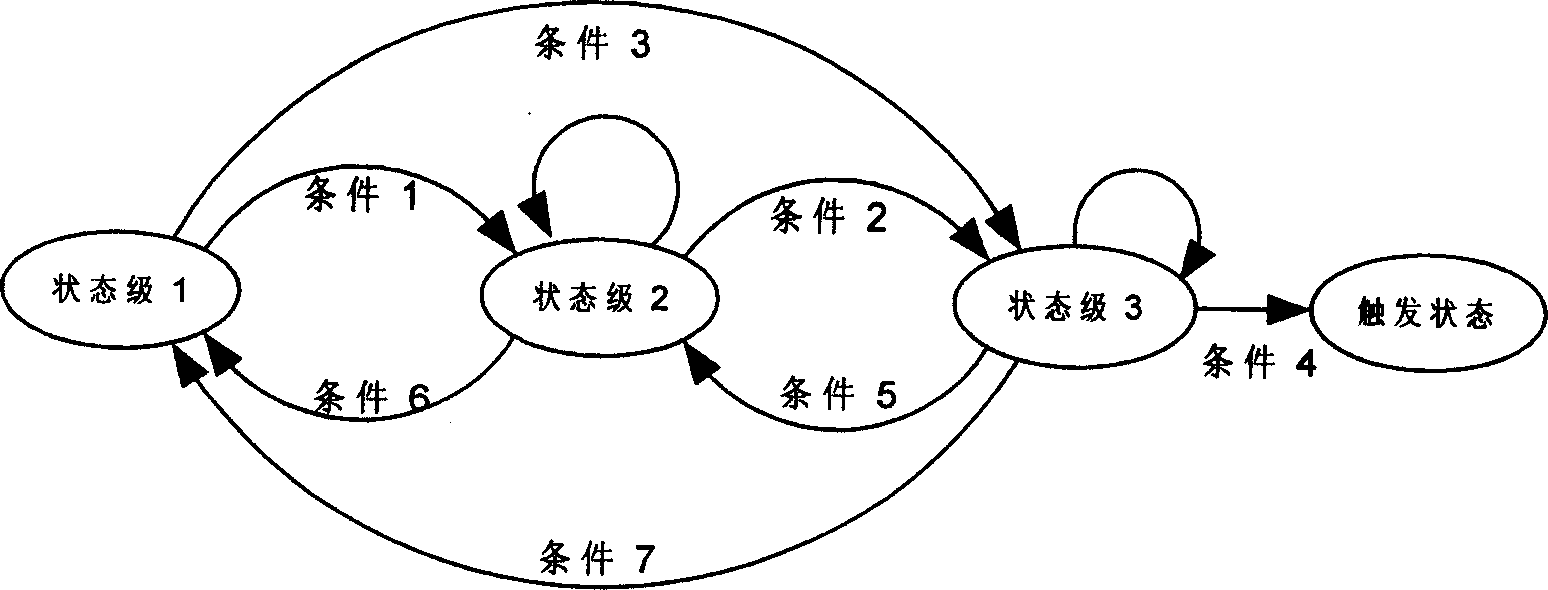
The invention aims to provide a space-ground integrated network security state analysis method based on a finite state machine. Based on the uniqueness of the space-ground integrated network, the actual deployment situation of a security processing module of the space-ground integrated network, and the actual demand design of a control system, the method effectively analyzes the current attack status corresponding to the data by the collected data and provides disposal suggestions to reduce misinformation and misstatements. The method comprises the following steps: collecting data of the space-ground integrated network; reading and processing the collected data; distinguishing the data sources according to characteristic values of the data, dividing the data into terrestrial network data and satellite network data, calling different finite state machine modules according to the data sources to process the data, matching the data characteristics with the knowledge in a knowledge map inorder, storing the results returned after the matching in the state machine, obtaining a final analysis result by setting a trigger condition, and outputting the status of the current attack and related knowledge corresponding to the analysis result to the control system.
Owner:NAT UNIV OF DEFENSE TECH
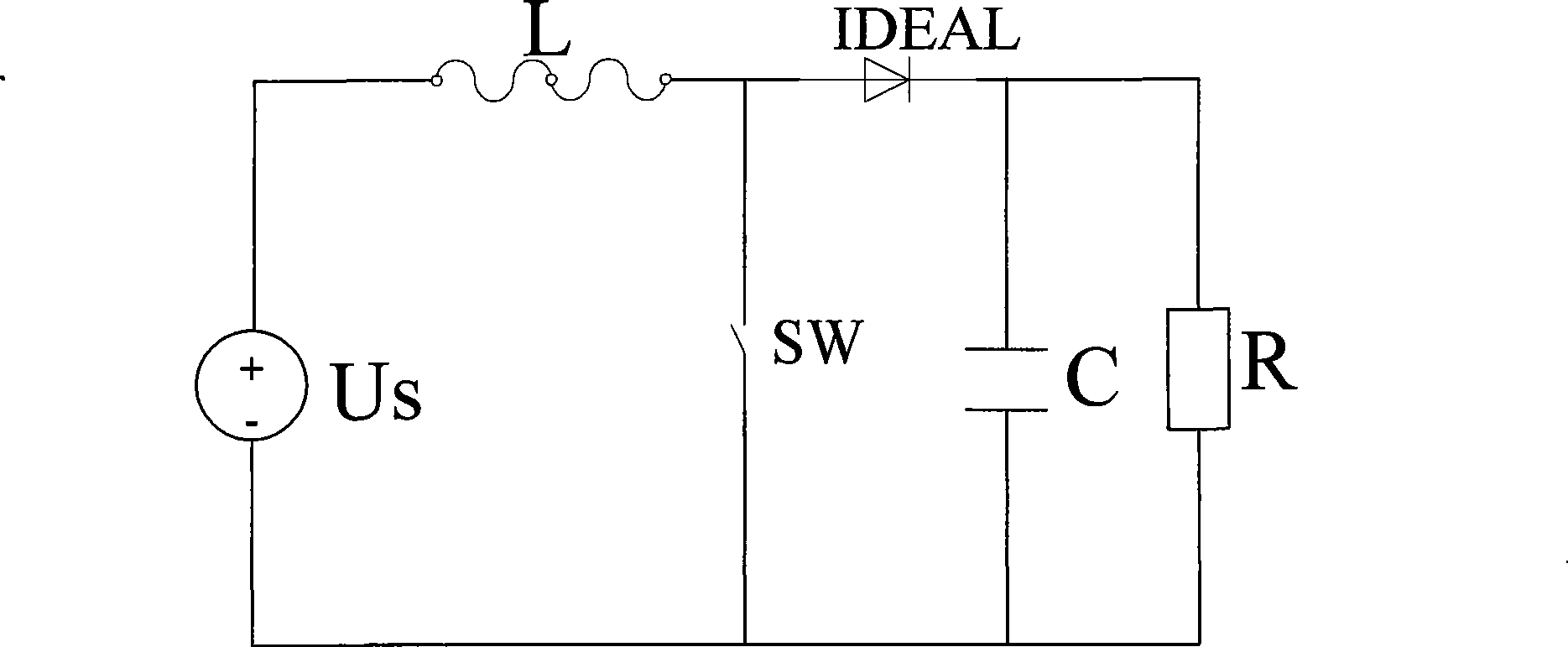
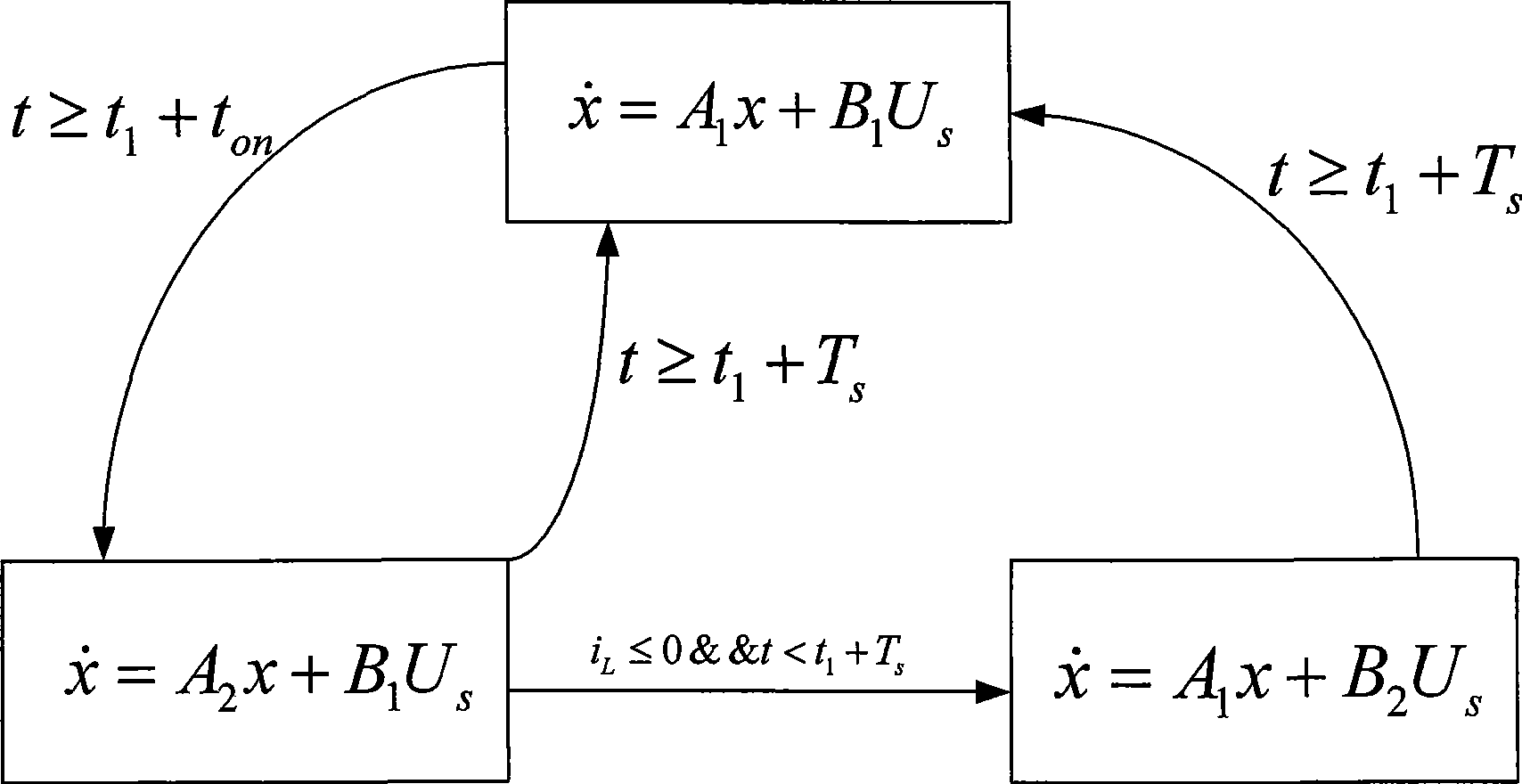
Boost circuit modeling approach and use thereof based on finite state machine
InactiveCN101393578AEffective modelingReduce volumeSpecial data processing applicationsCircuit modelingVirtual finite-state machine
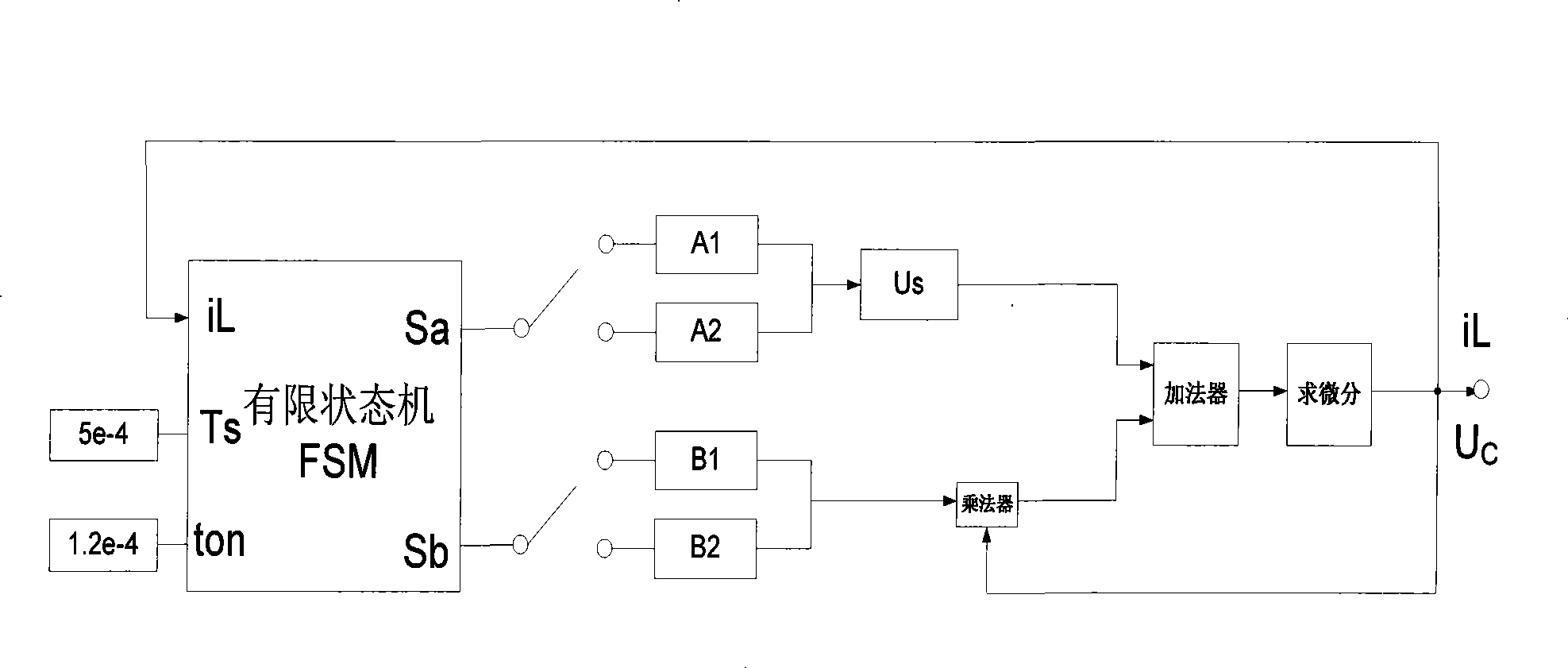
The invention provides a finite state machine-based Boost circuit modeling method and application thereof. The modeling method is characterized by comprising the following steps: (1) determining the number of operational states; (2) determining conversion conditions among the operational states; (3) establishing a mathematical equation; (4) determining a matrix according to parameters; and (5) building a model. The modeling method has the advantages that the Boost circuit model built by using the finite state machine is very precise and is easy to analyze the control characteristics of a system, especially a plurality of complicated characteristics caused by the switching of a switch in a converter system. The Boost circuit has the advantages of small volume, simple structure, high conversion efficiency and so on.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Invasion detection method of radio self-organization network
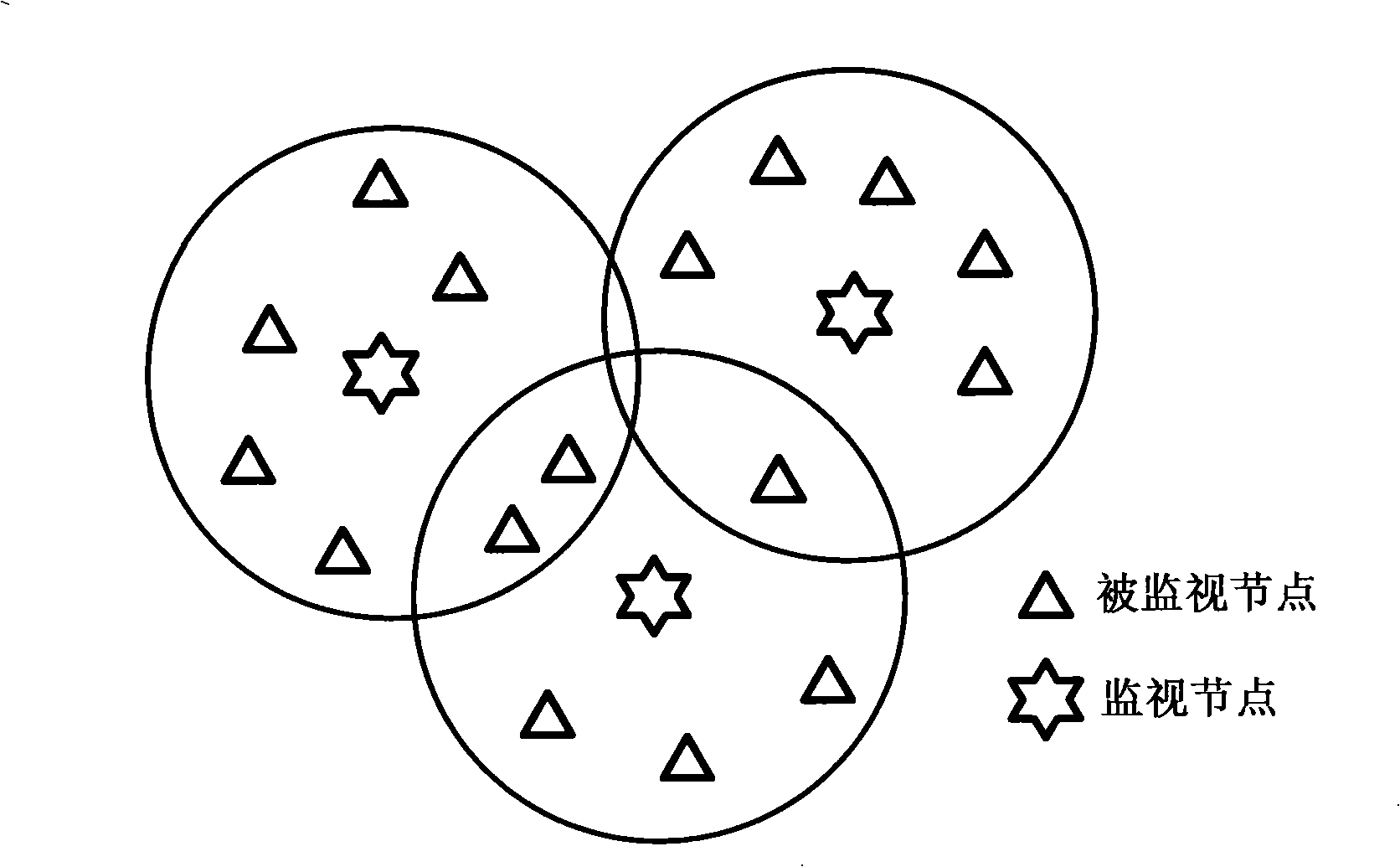
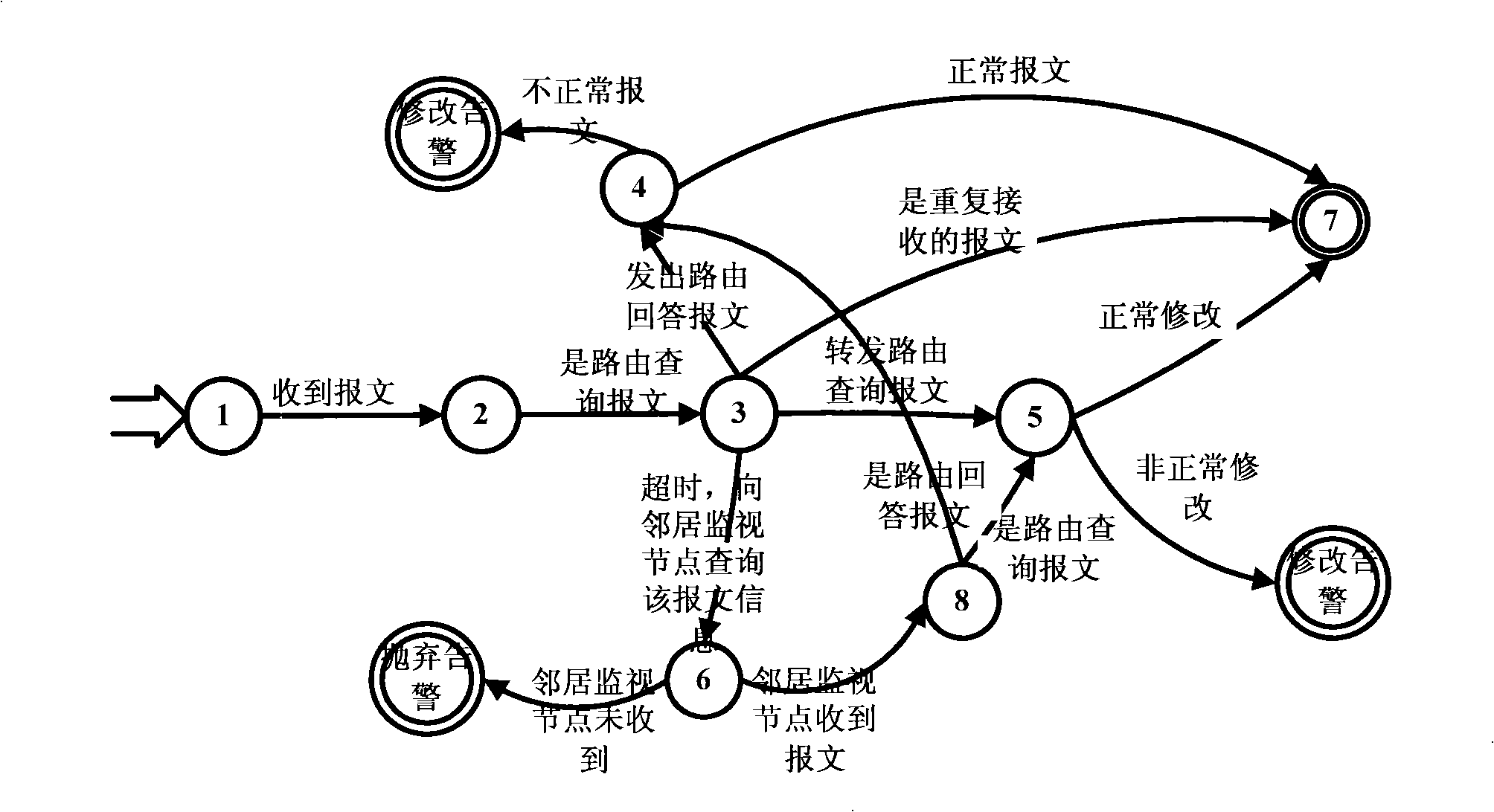
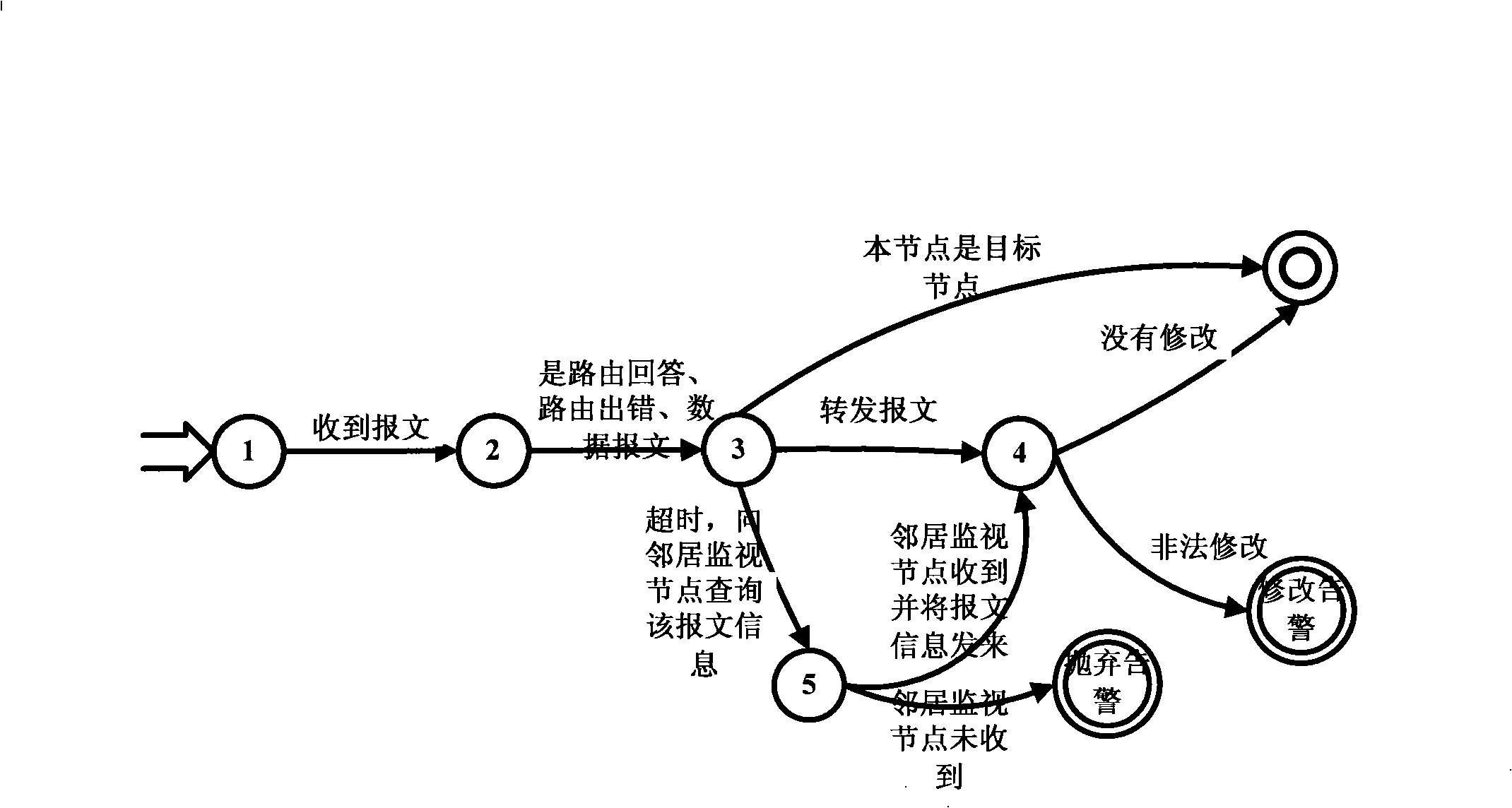
InactiveCN101340292AReduce consumptionReal-time detection of intrusion behaviorData switching by path configurationSecuring communicationVirtual finite-state machineNetwork security policy
A wireless self-organized network intrusion detection method belongs to the technical field of network security, which comprises the following steps: step one, in a wireless self-organized network, the whole self-organized network is divided into a plurality of areas, and a cluster head is chosen in each area as a monitoring node in charge of the intrusion detection of the whole area, and the cluster head is used for collecting the behavior information of the nodes in the whole area; step two, the routing protocols of the wireless self-organized network are formed into a finite state machine which is then used for judging the behavior of each node in the wireless self-organized network collected by the cluster head in step one, and if the behavior of the node is not complied with the behavior of the finite state machine, the behavior of the node is regarded as an aggressive behavior, otherwise, the finite state machine enters the final state. The method of the invention is distributed cooperation intrusion detection, which requires no data training in advance and can detect intrusion behavior in real time.
Owner:SHANGHAI JIAO TONG UNIV
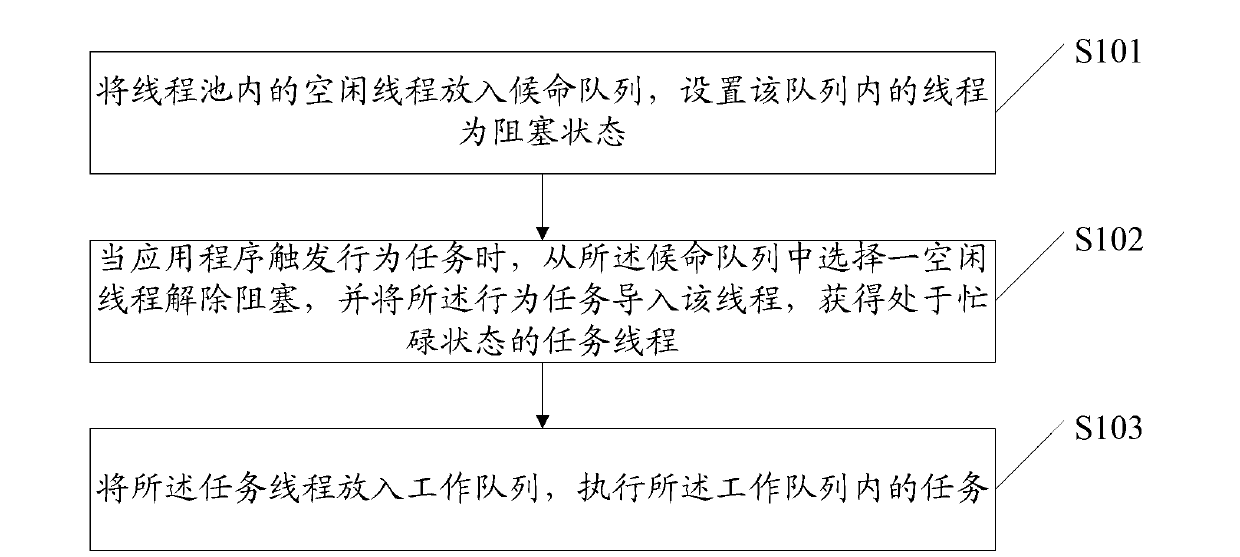
Multi-thread finite state machine switching method and multi-thread finite state machine switching device based on thread pool
InactiveCN103218264ARich role objectsIncrease profitResource allocationVirtual finite-state machineDistributed computing
The invention discloses a multi-thread finite state machine switching method based on a thread pool. The method comprises the following steps of putting idle threads in the thread pool in a candidate queue and setting the threads in the queue in a blocked state; when an action task is triggered by an application program, selecting one idle thread from the candidate queue to relieve blocking, and leading the action task to the idle thread so as to obtain a task thread in a busy state; and putting the task thread in a work queue and executing a task in the work queue. With the method, the utilization rate of a CPU (Central Processing Unit) can be better increased through the optimal management of the thread pool, so that a system can run more smoothly.
Owner:GUANGDONG VTRON TECH CO LTD
Intelligent cellphone application interaction interface program usability testing method
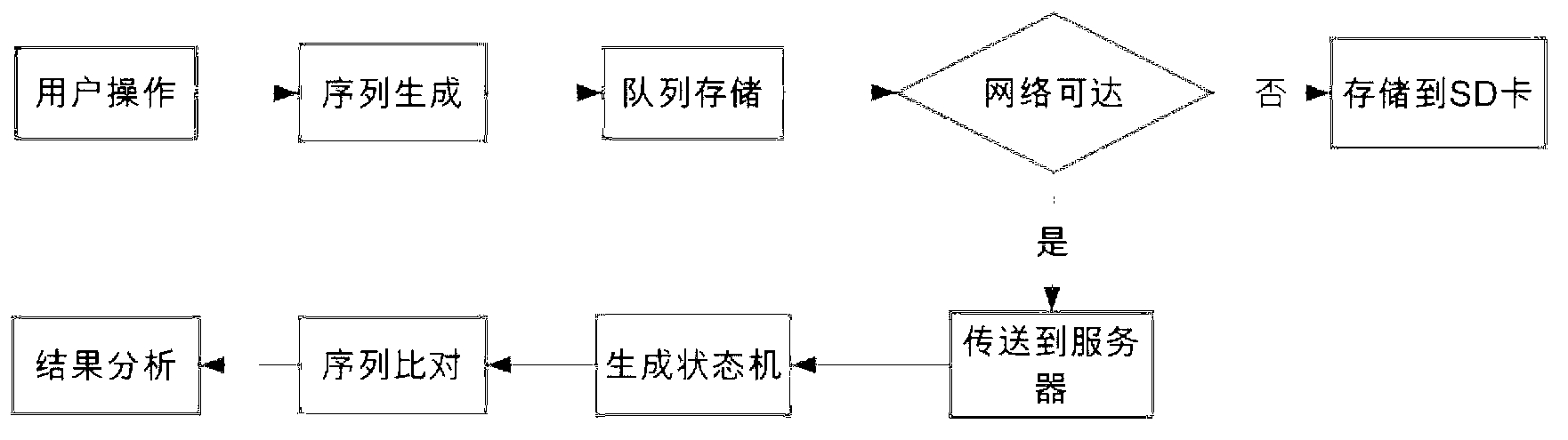
ActiveCN103312851AOperation diversificationRealize automatic information collection functionSoftware testing/debuggingSubstation equipmentInteraction interfaceVirtual finite-state machine
The invention provides an intelligent cellphone application interaction interface program usability testing method, which does not need to manually record the process that a user operates a cellphone program, and comprises the steps of embedding a small number of codes into an application program; uploading a user operation event to a server in the process that the user operates a cellphone; and analyzing by testing personnel through a finite state machine according to collected data. According to the method, only little modification is carried out on the original program during intelligent cellphone application interaction interface program usability testing, automatic usability testing can be realized under the condition of not influencing the performance of the original program, more finer user operation data can be collected, and more bugs can be found.
Owner:NANJING UNIV
Gather using index array and finite state machine
ActiveUS8972697B2Single instruction multiple data multiprocessorsInstruction analysisMicro-operationArray data structure
Methods and apparatus are disclosed for using an index array and finite state machine for scatter / gather operations. Embodiment of apparatus may comprise: decode logic to decode a scatter / gather instruction and generate a set of micro-operations, and an index array to hold a set of indices and a corresponding set of mask elements. A finite state machine facilitates the gather operation. Address generation logic generates an address from an index of the set of indices for at least each of the corresponding mask elements having a first value. An address is accessed to load a corresponding data element if the mask element had the first value. The data element is written at an in-register position in a destination vector register according to a respective in-register position the index. Values of corresponding mask elements are changed from the first value to a second value responsive to completion of their respective loads.
Owner:INTEL CORP
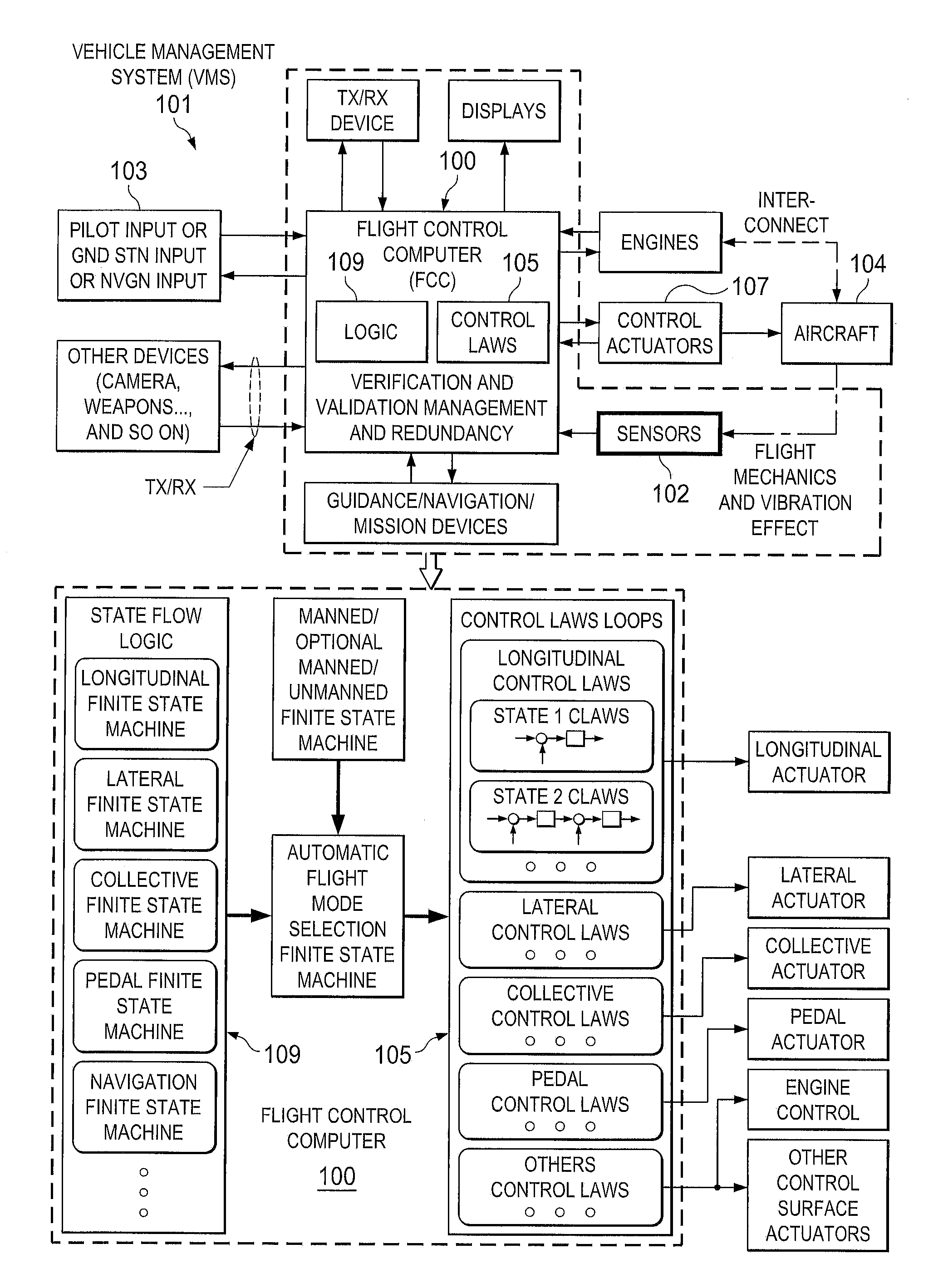
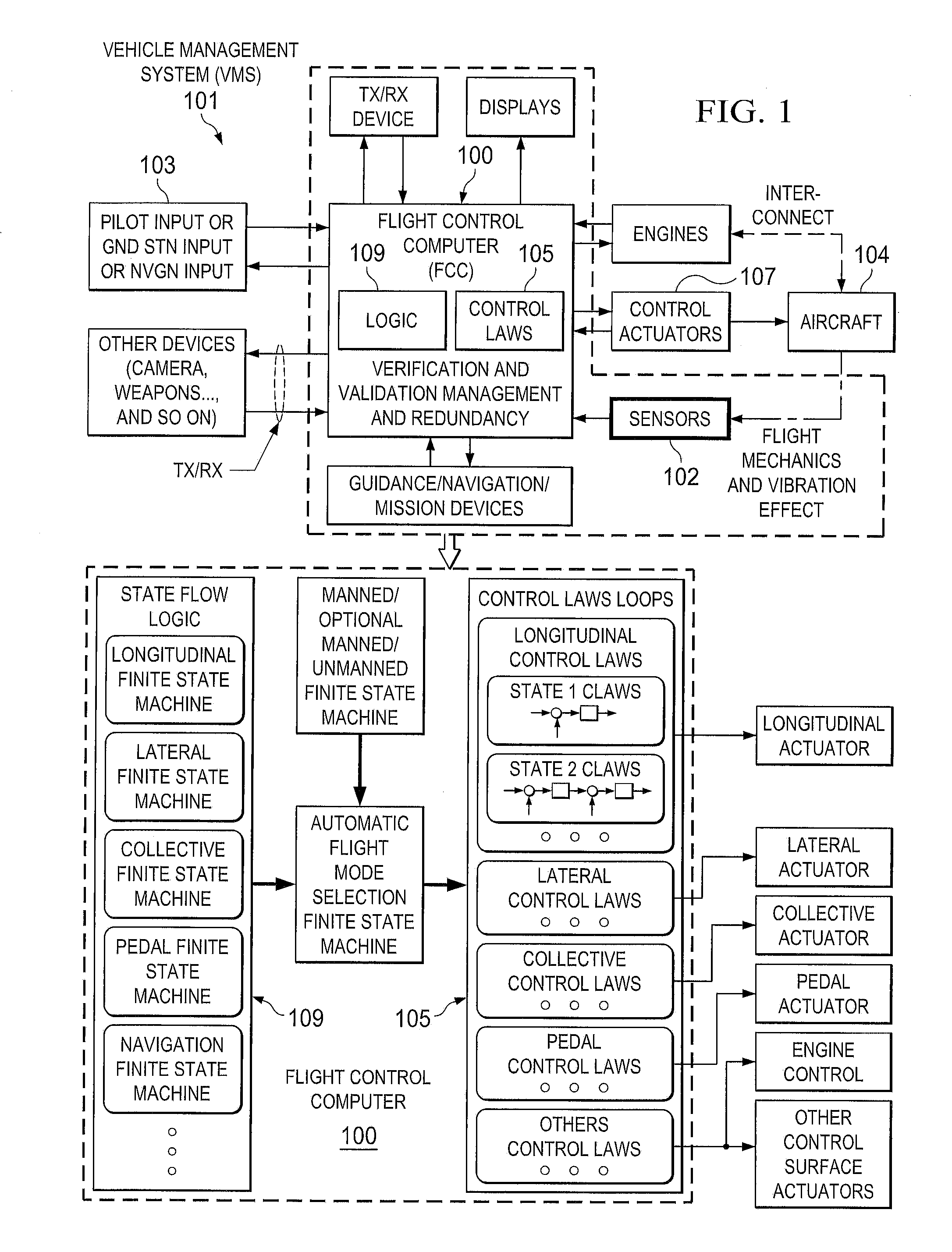
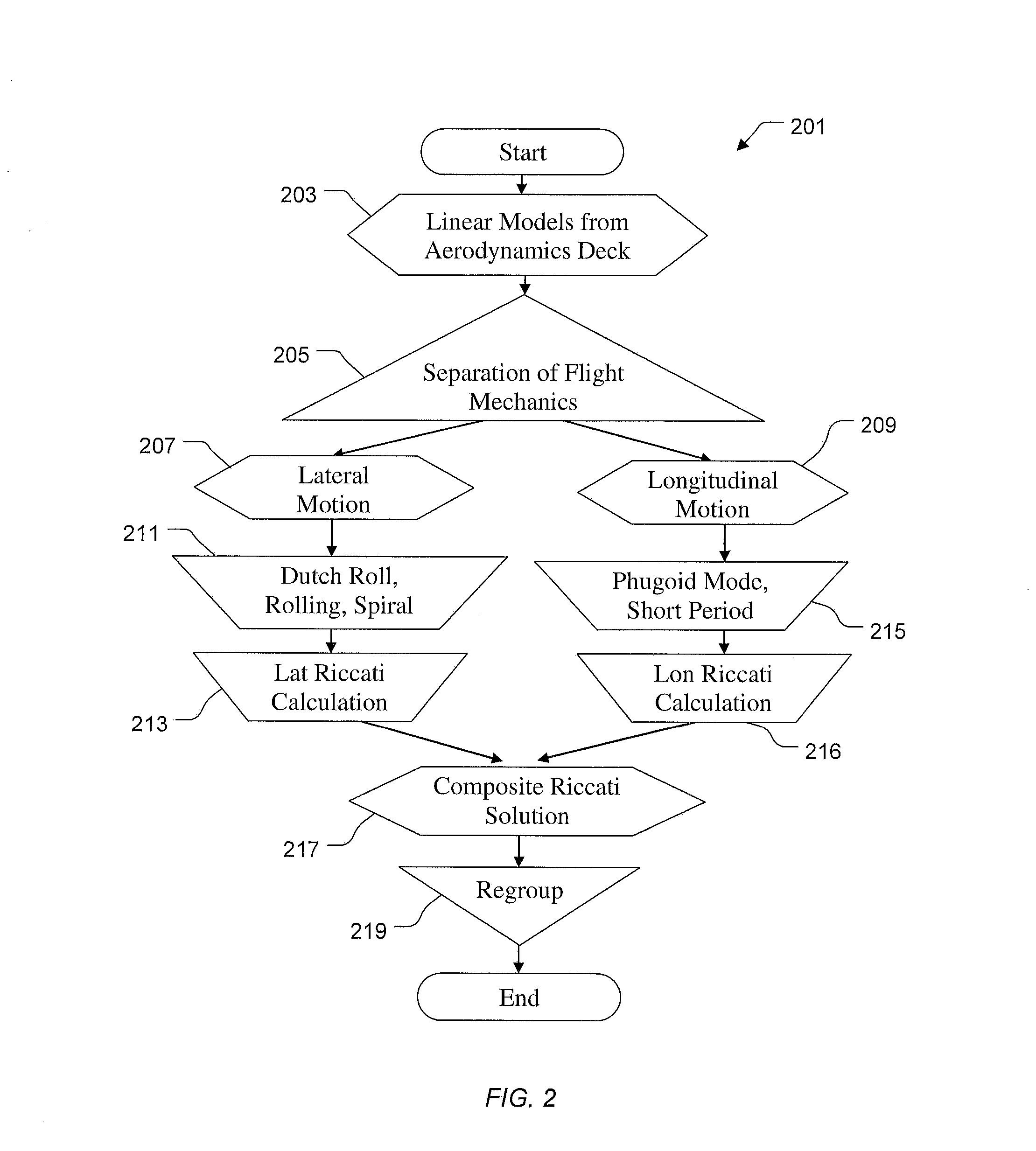
Vehicle management system using finite state machines
A system includes a plurality of actuators and a management system operably associated with the plurality electronic and mechanical devices. The management architecture includes interfaces configured to the entire electronics and mechanics to provide a parameter to a computer. The computer includes a control and management architecture using modular finite state flow designs configured to analyze the parameter. The computer with a plurality of finite state machines can conduct a plurality of control laws operably associated with one or more actuators for finite functions of mobility. The method includes matching the parameter with the finite state machine and controlling the actuator via control law operably associated with finite state machine. The method can therefore be achieved either manually, semi-autonomously and autonomously with seamless and switchless control using a central control computer with integration of electronic and mechanic sensors and devices.
Owner:TEXTRON INNOVATIONS
Reconfigurable test access port with finite state machine control
ActiveUS20170269157A1Memory architecture accessing/allocationDigital circuit testingComputer hardwareFinite-state machine
A processor includes logic to implement a reconfigurable test access port with finite state machine control. A plurality of test access ports may each include a finite state machine for enabling implementation of different test interfaces to the processor, including JTAG IEEE 1149.1, JTAG IEEE 1149.7, and serial wire debug.
Owner:INTEL CORP
Wireless radio resource management system using a finite state machine
InactiveUS7058398B2Radio/inductive link selection arrangementsWireless commuication servicesQuality of serviceNon real time
Radio resource management (RRM) components and methods for a wireless telecommunications system utilize Finite State Machines (FSMs), preferably dividing RMM functions on the basis of Real Time (RT) and Non Real Time (NRT) communications and also UpLink (UL) and DownLink (DL) functions. The use of FSMs for RRM functions promotes Quality of Service (QoS), maximum system capacity and stability and coordination among different RRM algorithms
Owner:INTERDIGITAL TECH CORP
Oscilloscope condition triggering method based on finit state machine
InactiveCN1710429AImprove general performanceStrong characteristicDigital variable/waveform displayFinite-state machineVirtual finite-state machine
A condition triggering method of oscilloscope based on finite state computer includes making state computer series be n which is integer being greater than or equal to one ; providing four selectable conditions by system to client as automatic condition referring that sub-condition is always being set up , edge condition referring that condition is being set up when specific edge polarity of specific electric level is satisfied , overtime condition referring that condition is being set up after specific delay time is satisfied and forbidden condition referring that this condition is never being set up.
Owner:SOUTHEAST UNIV
Biomimetic controller for increased dexterity prosthesis
ActiveUS20140128992A1Programme-controlled manipulatorArtificial handsVirtual finite-state machineProsthesis
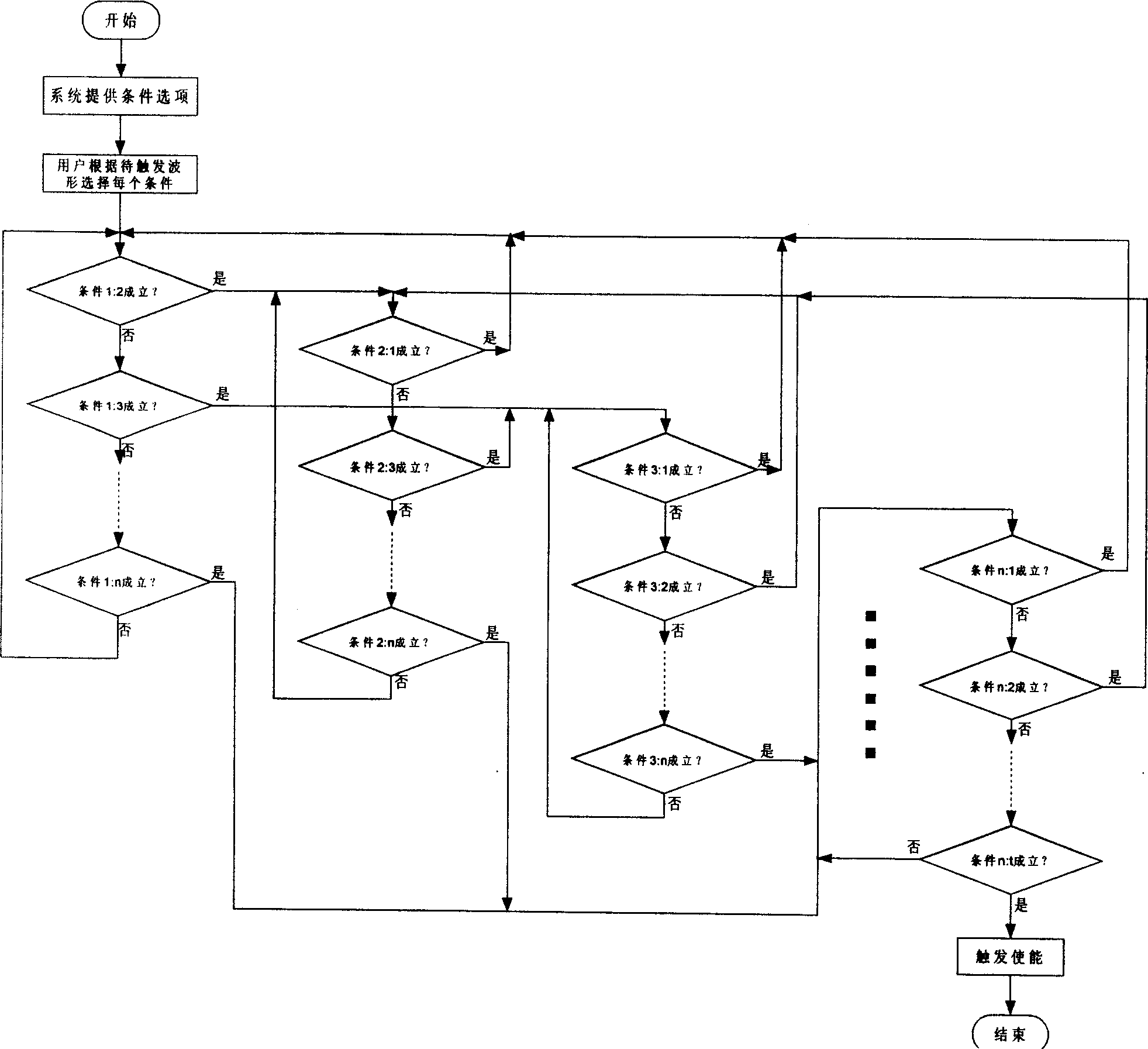
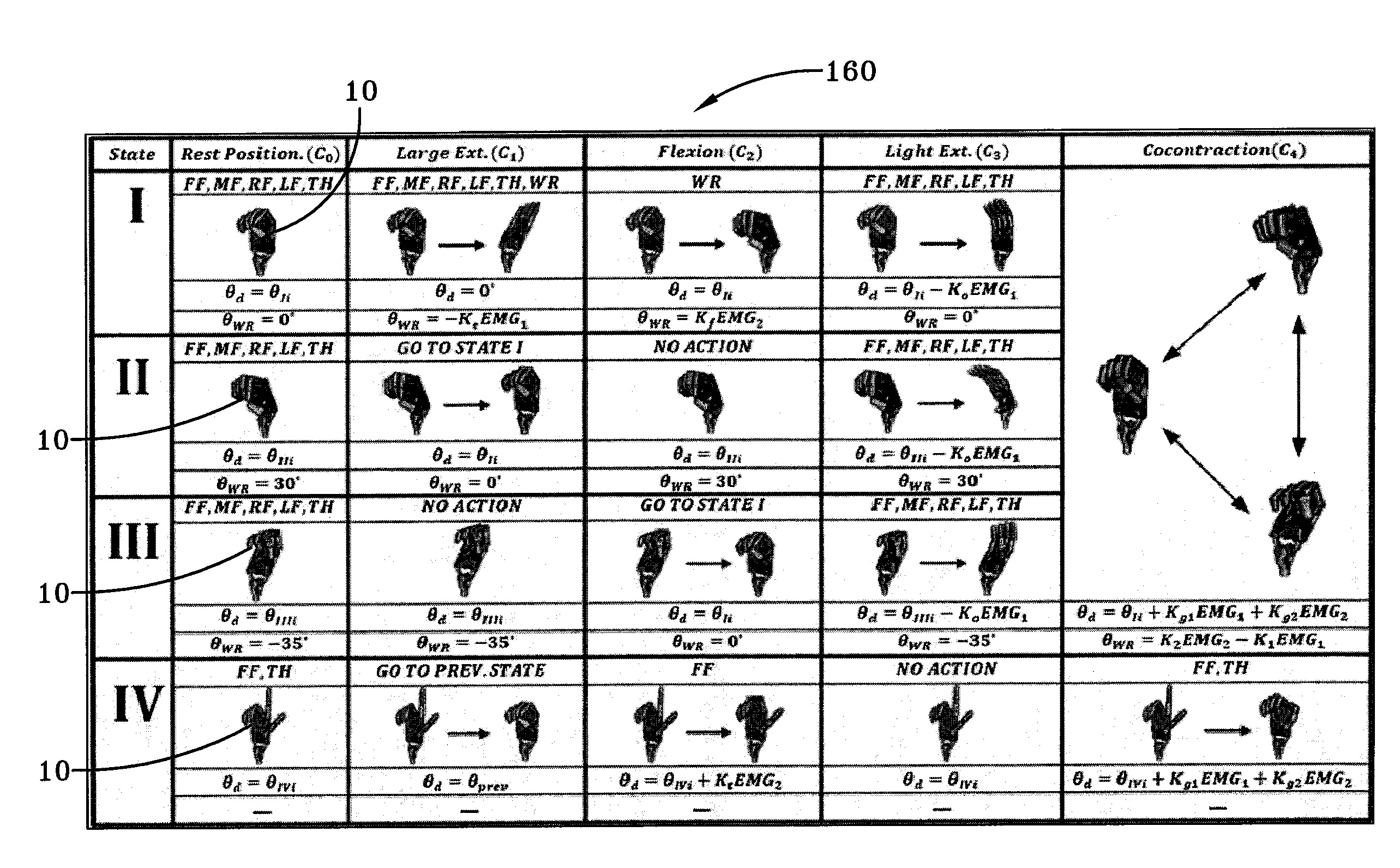
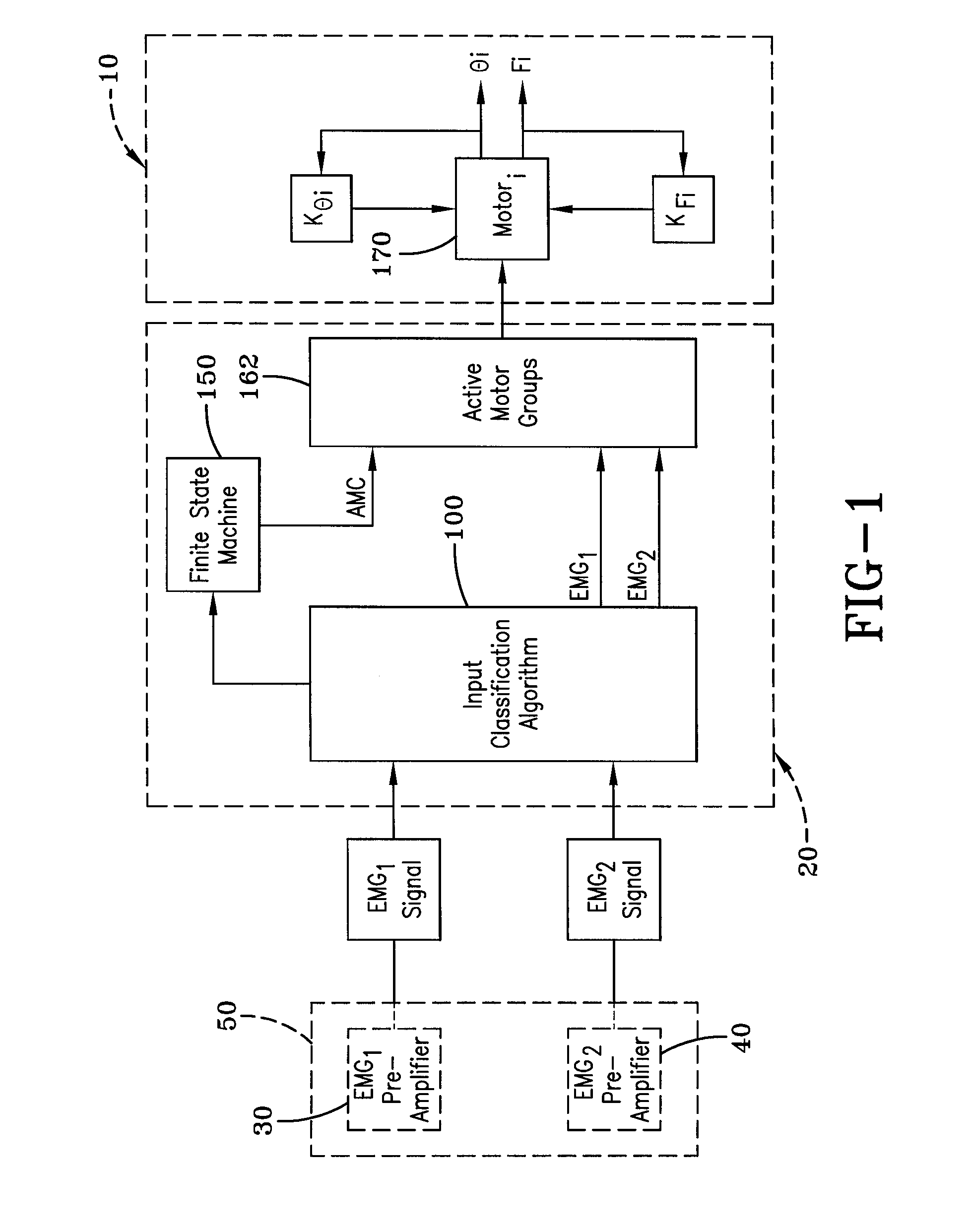
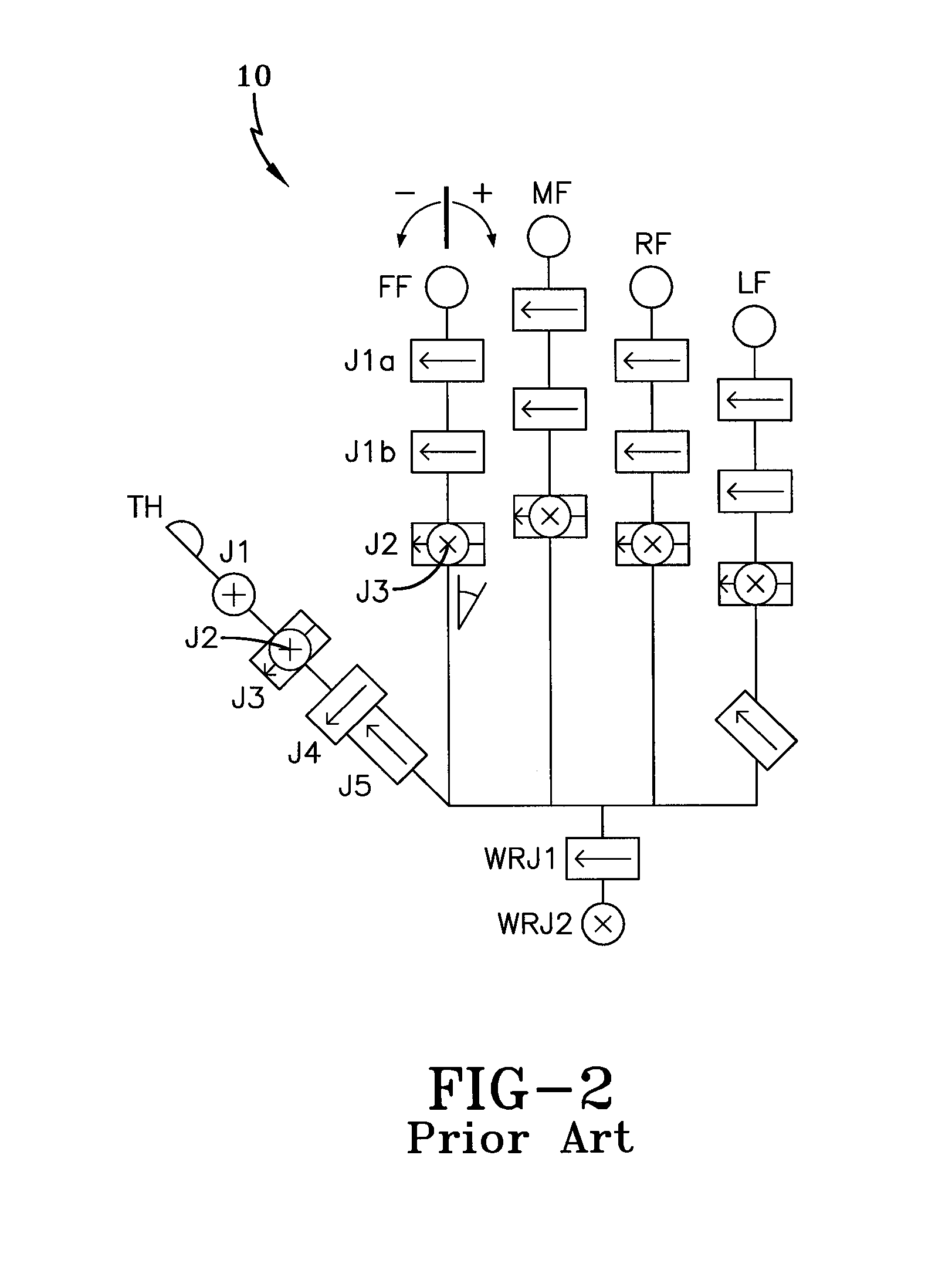
A sliding mode biomimetic (BSM) controller for a prosthetic device, such as a prosthetic hand, includes an input classification component that receives electromyogram (EGM) signals from two or more electromyogram (EGM) sensors that are positioned on an amputee's body. The input classification component compares the EGM input signals based on predetermined activation threshold values and identifies an input class to determine the amputee's intended movement of the prosthetic device. A finite state machine utilizes the current position of the prosthetic hand and the identified input class to identify the coordinates of a lookup table to determine the next state or position of the prosthetic device. As a result, the biomimetic controller is able to simultaneously control two or more degrees of freedom (DOFs) or functions of the prosthetic hand using only two EGM input signals.
Owner:THE UNIVERSITY OF AKRON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com