Invasion detection method of radio self-organization network
A technology of network intrusion detection and wireless self-organization, which is applied in the field of network security, can solve problems such as undetermined detection and achieve the effect of reducing consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
[0026] This embodiment includes the following steps:
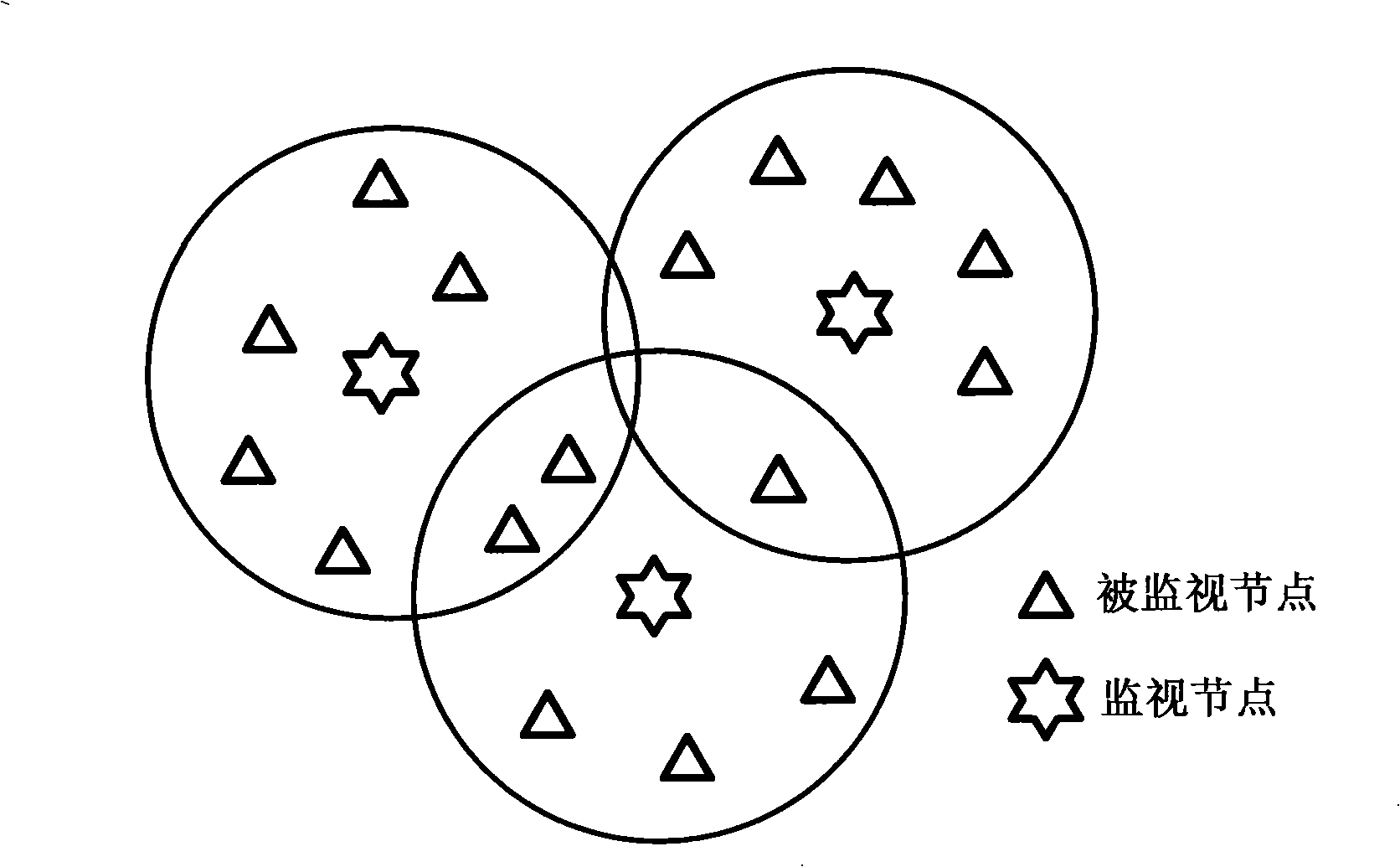
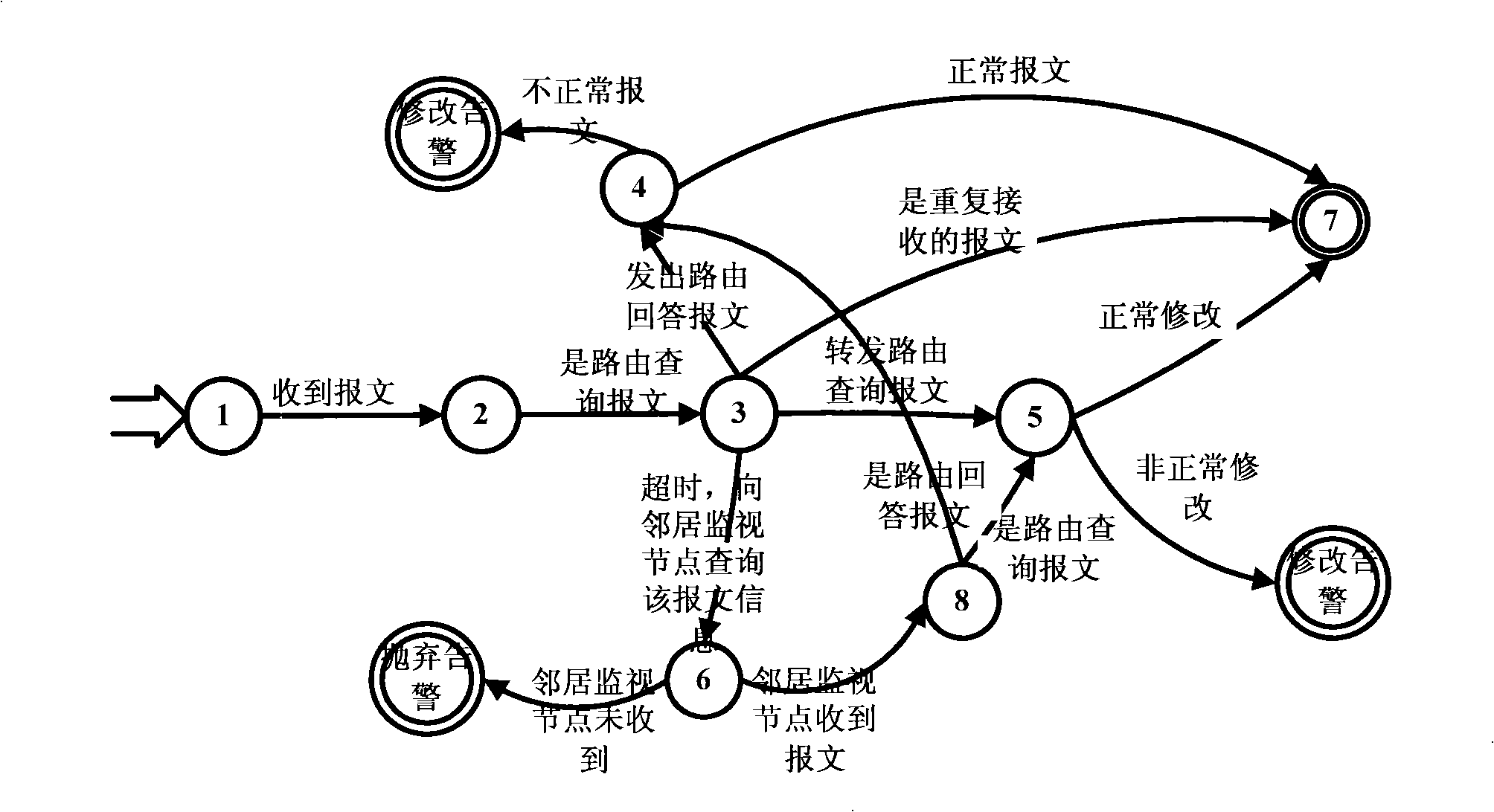
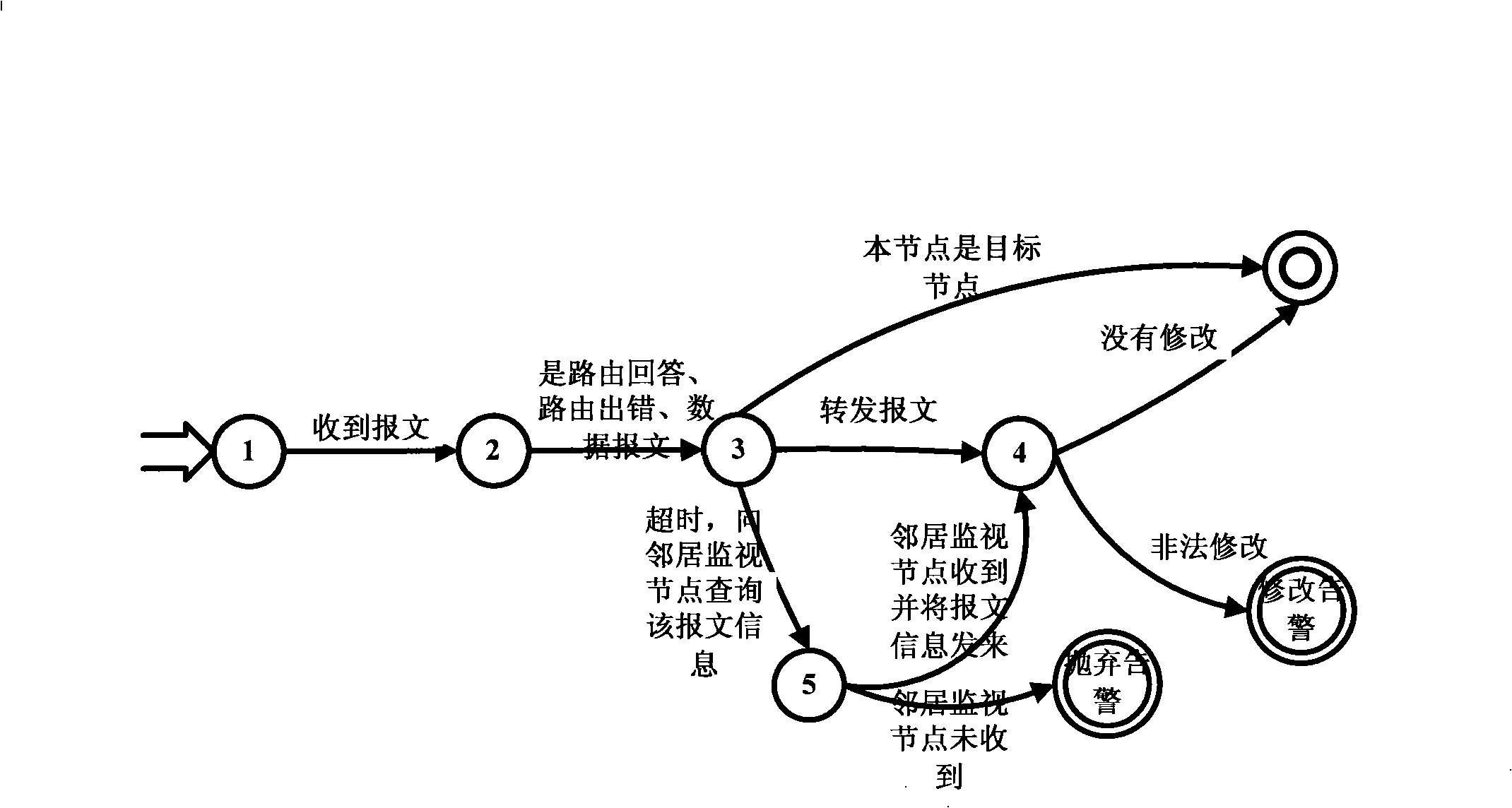
[0027] Step 1. Intrusion detection based on distributed cooperation of cluster heads: In wireless ad hoc networks, the resources of nodes are very limited, so the entire ad hoc network is divided into several areas, and each area is selected by a free competitive election method. A cluster head is set up as a monitoring node to be responsible for intrusion detection in the entire area. The cluster head collects the behavior information of the nodes in the entire area, and analyzes it according to the finite state ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com