An Identity-Based Security Mutual Authentication Method Combining the Advantages of Broadcasting
An identity and security technology, applied in the field of Internet security communication, can solve problems such as large transmission bandwidth and computing time overhead, complex certificate management, and inability to realize mutual authentication of Internet nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
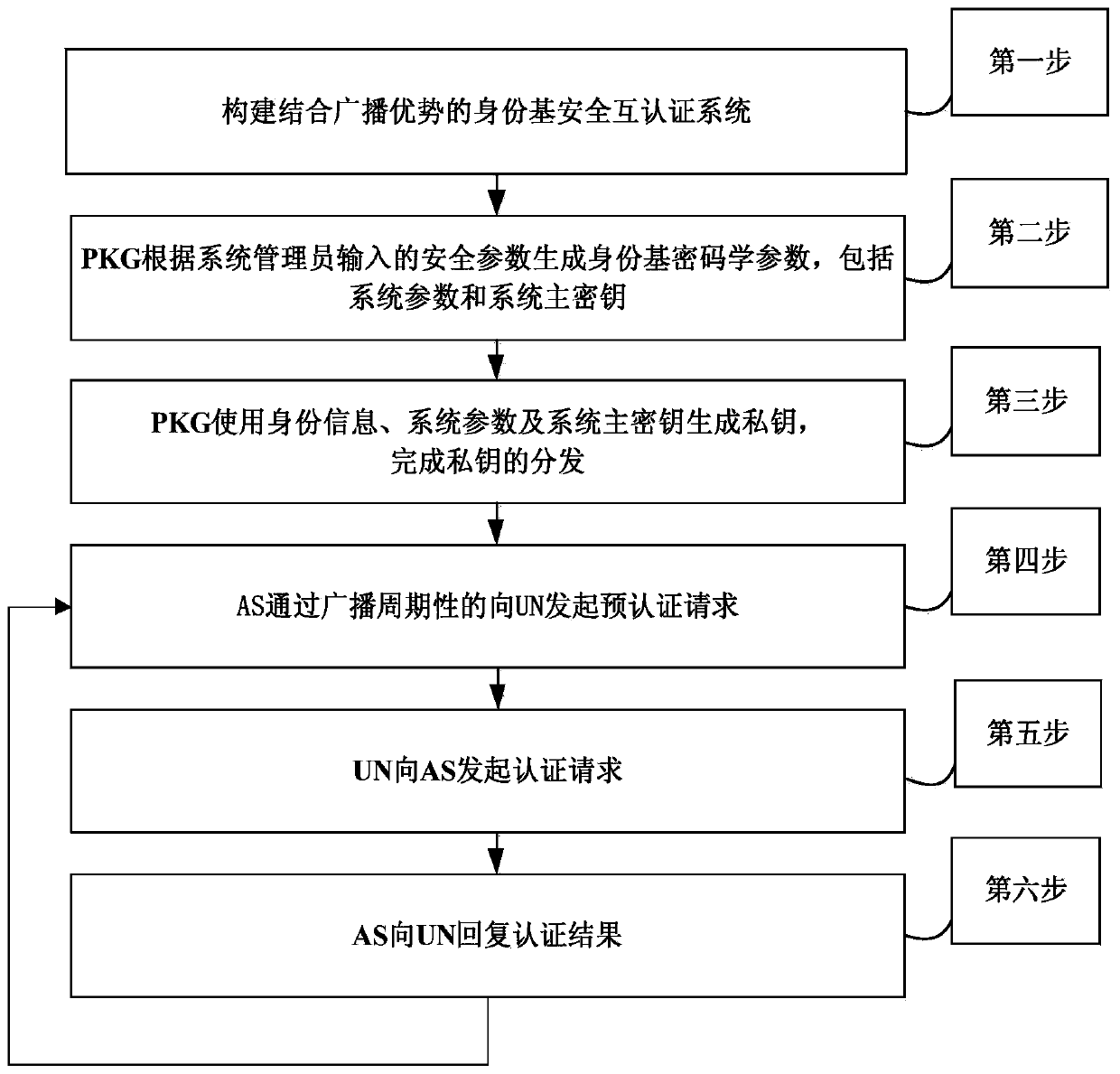
[0125] figure 1 It is an overall flowchart of the present invention, wherein the first step to the third step is to initialize the authentication system, and the fourth step to the sixth step is to perform user access security mutual authentication, and the specific steps are as follows:
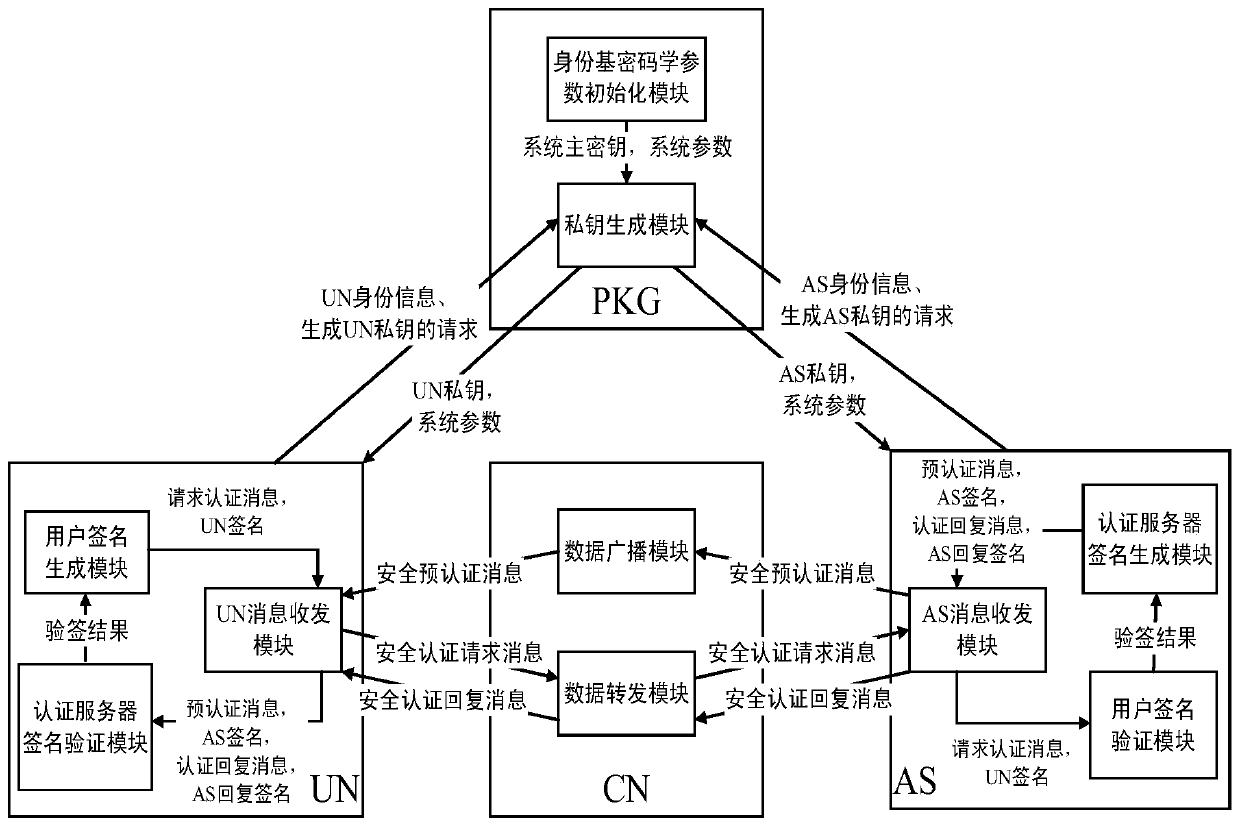
[0126] The first step is to build an identity-based security mutual authentication system that combines the advantages of broadcasting. like figure 2 As shown, the identity-based security mutual authentication system combined with broadcast advantages is composed of multiple user nodes UN to be authenticated, authentication server AS, security core node CN, and private key generation center PKG.
[0127] The PKG is installed with an identity-based cryptographic parameter initialization module and a private key generation module. The AS is installed with an authentication server signature generation module, a user signature verification module, and an AS message sending and receiving modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com