Public security police affair management method, device and equipment and storage medium
A management method and police technology, applied in the field of big data, can solve the problems of insufficient investigation methods, complex criminal methods, difficult data analysis and mining, etc., and achieve the effect of improving management and processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
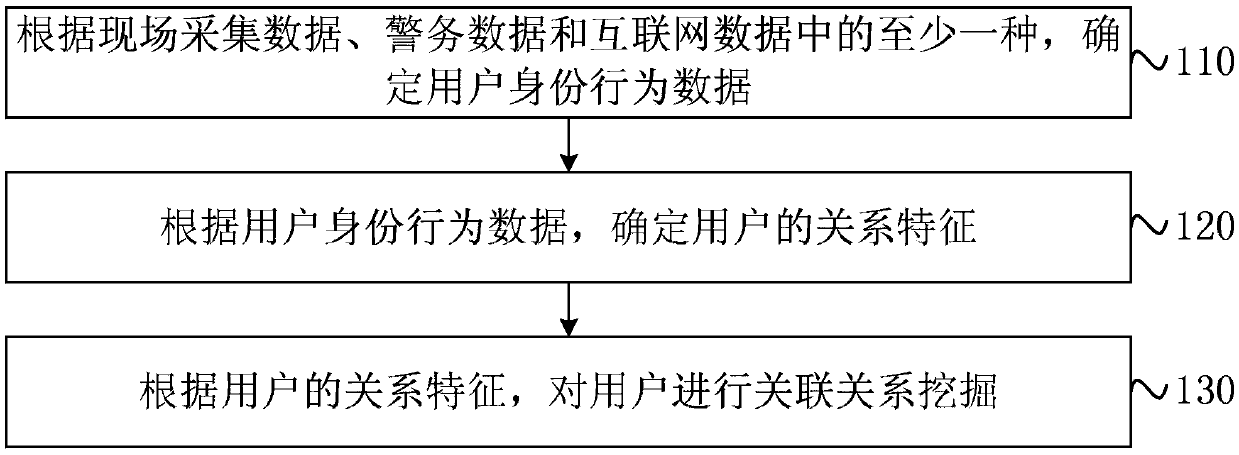
[0027] figure 1 It is a flow chart of a public security police management method provided by Embodiment 1 of the present invention. This embodiment is applicable to mining user association relationships based on big data, and the method can be executed by a public security police management device. The method specifically includes the following steps:
[0028] S110. Determine user identity behavior data according to at least one of on-site collection data, police data, and Internet data.
[0029] In a specific embodiment of the present invention, the core data assets used for public security and police management mainly include on-site collection data, police data and Internet data, and may include at least one of them, or may also include other than these three data sources Any data that can reflect sensitive events, sensitive people or sensitive areas. Among them, the on-site collected data may refer to third-party data collected outside the public security, and may includ...
Embodiment 2
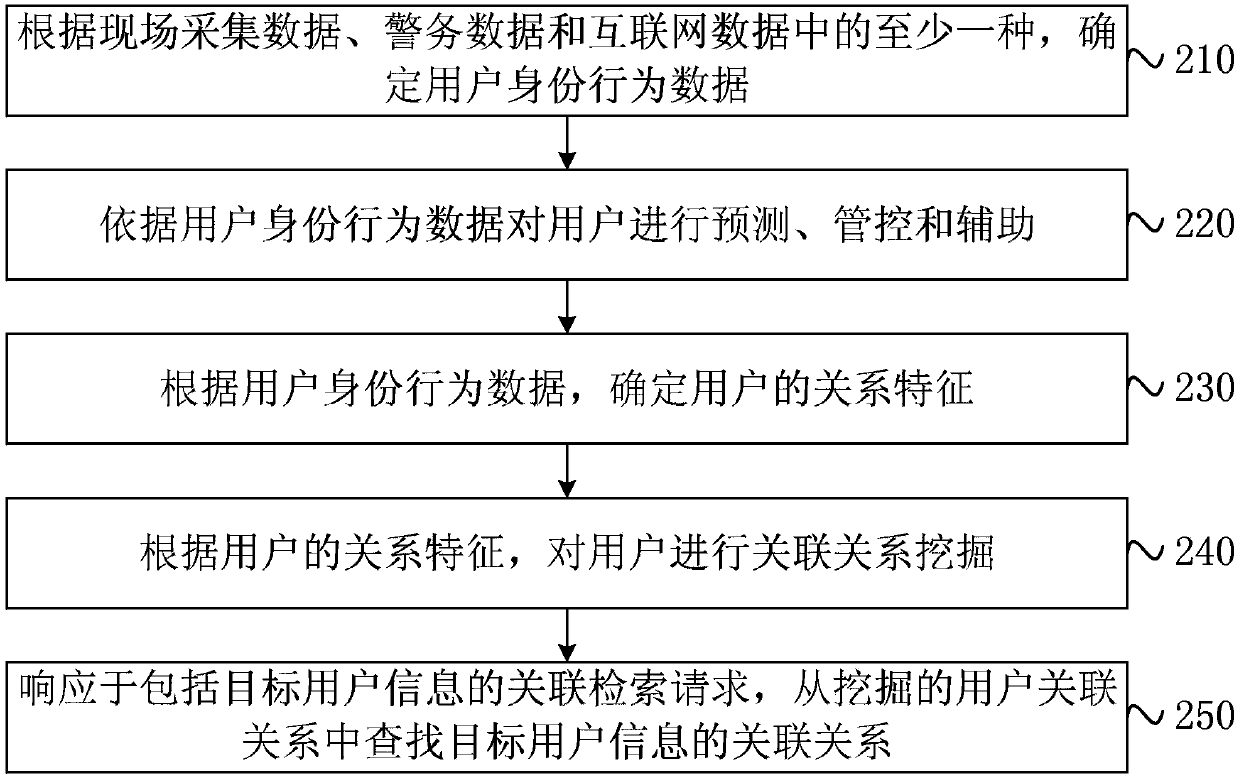
[0047] On the basis of the first embodiment above, this embodiment provides a preferred implementation of the public security police management method, which can perform functions such as sensitive user retrieval, sensitive behavior prediction, and investigation assistance based on big data analysis results. figure 2 A flow chart of a public security police management method provided by Embodiment 2 of the present invention, such as figure 2 As shown, the method includes the following specific steps:
[0048] S210. Determine user identity behavior data according to at least one of on-site collection data, police data, and Internet data.
[0049] In a specific embodiment of the present invention, the core data assets used for public security and police management mainly include on-site collection data, police data and Internet data, and may include at least one of them, or may also include other than these three data sources Any data that can reflect sensitive events, sensit...
Embodiment 3
[0079] Figure 4 A schematic diagram of the structure of a public security police management device provided by Embodiment 3 of the present invention. This embodiment is applicable to mining user associations based on big data. police management methods. Specifically, the device includes:
[0080] The user identity behavior data determination module 410 is used to determine the user identity behavior data according to at least one of on-site collection data, police data and Internet data;
[0081] A relationship feature determination module 420, configured to determine the user's relationship features according to the user identity behavior data;
[0082] The association relationship mining module 430 is configured to mine the association relationship of the users according to the relationship characteristics of the users.
[0083] Optionally, the association relationship mining module 430 is specifically used for:
[0084] According to the relationship characteristics of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com