A consortium chain node secret key distribution and backup system that improves the bip protocol
A node and key technology, applied in the blockchain field, can solve the problems of complex and inconvenient management of NVP node key distribution and backup, and achieve the effect of protecting privacy and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
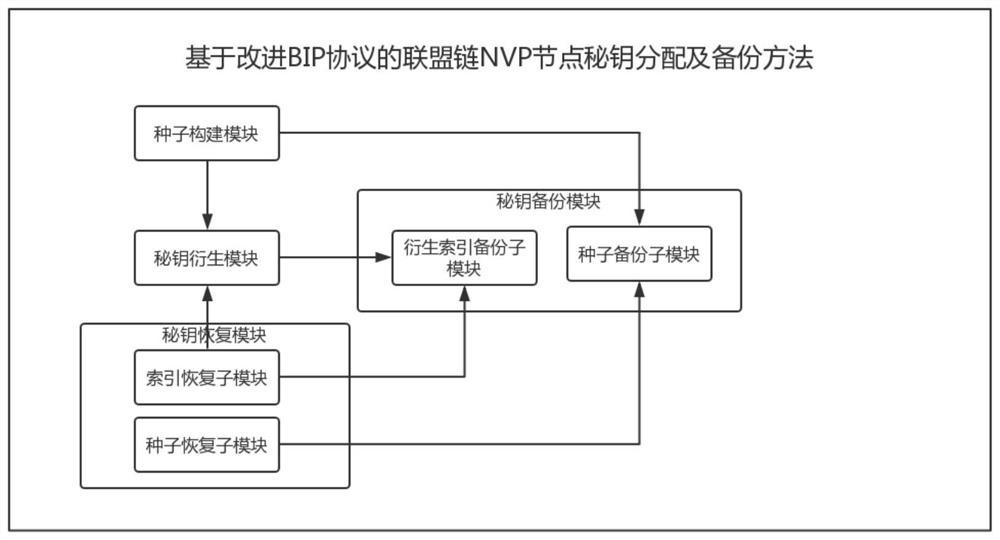
[0043] figure 1 It is a structural diagram of an improved BIP protocol alliance chain node key distribution and backup system of the present invention, as shown in figure 1 shown, including:
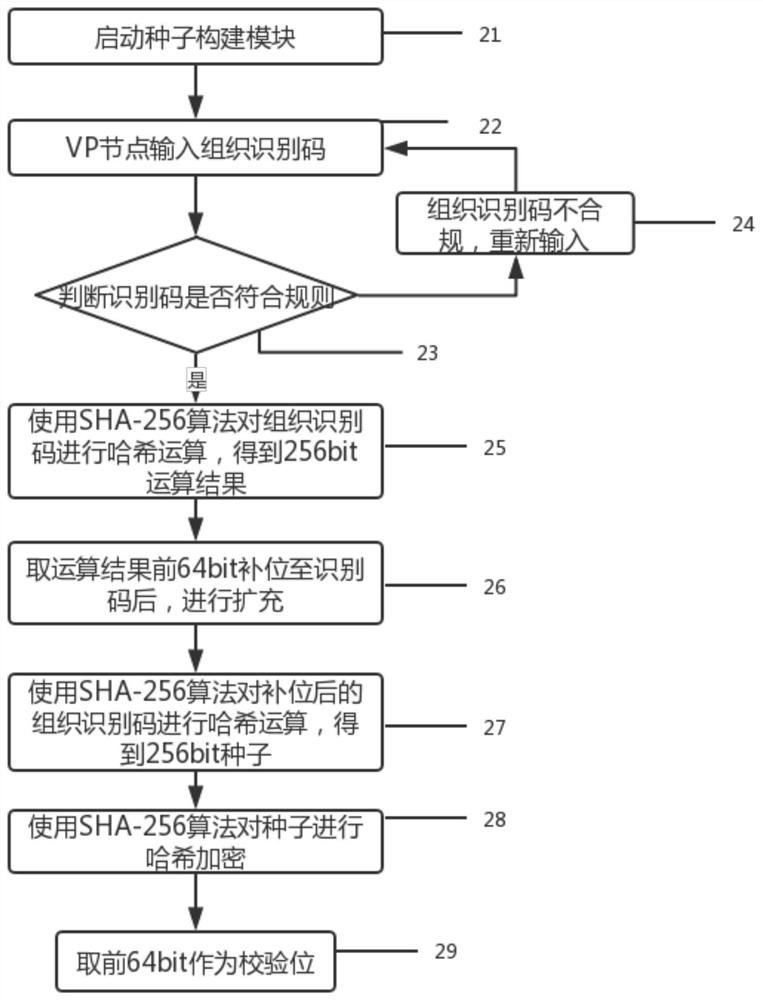
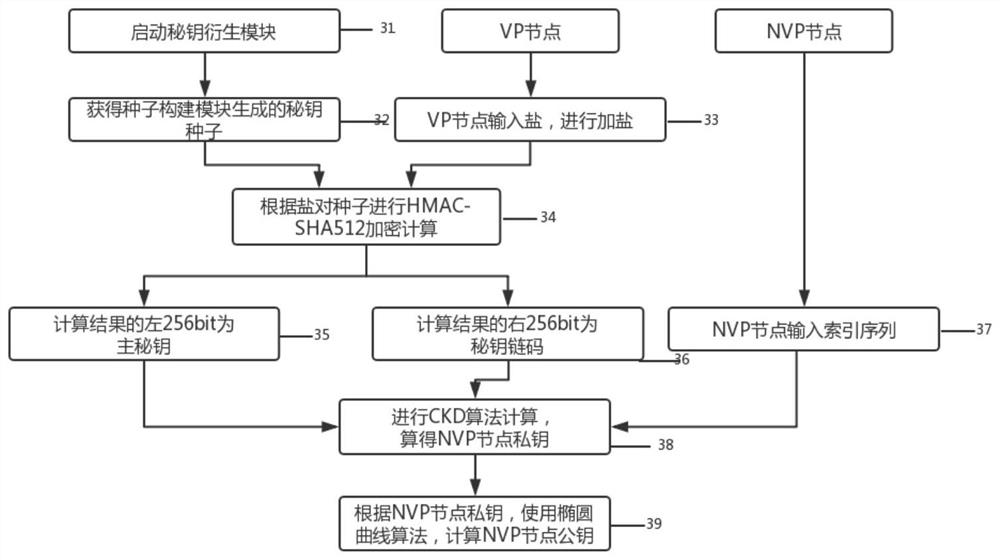
[0044]The seed construction module is connected with the seed backup sub-module in the secret key derivation and secret key backup module. Key seed is the core of key derivation and key recovery, and seed generation is also the initial step of this method. The current organization identification code is input through the VP node, and the seed is obtained through three hash operations in the seed building module. During the encryption process, the first 64 bits of the third hash result are extracted as the seed check bit, which is used to verify the correctness and integrity of the seed when the key is recovered. The double-hash hash operation e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com