Virtual machine memory key generation device and method, encryption method and SoC system
A key generation device and key generation technology, applied in the field of virtualization, can solve problems such as ineffective security virtualization, and achieve the effects of ensuring data security, improving security, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033]Embodiments of the present invention will be described with reference to the drawings. The same components are given the same reference numerals. Exemplary embodiments of the present invention are first described. The exemplary embodiments are provided to illustrate aspects of the invention and should not be construed as limiting the scope of the invention. When exemplary embodiments are described with reference to block diagrams or flowcharts, each block may represent a method step or an apparatus element for performing a method step. Depending on the implementation, the corresponding device elements may be configured as hardware, software, firmware or a combination thereof.
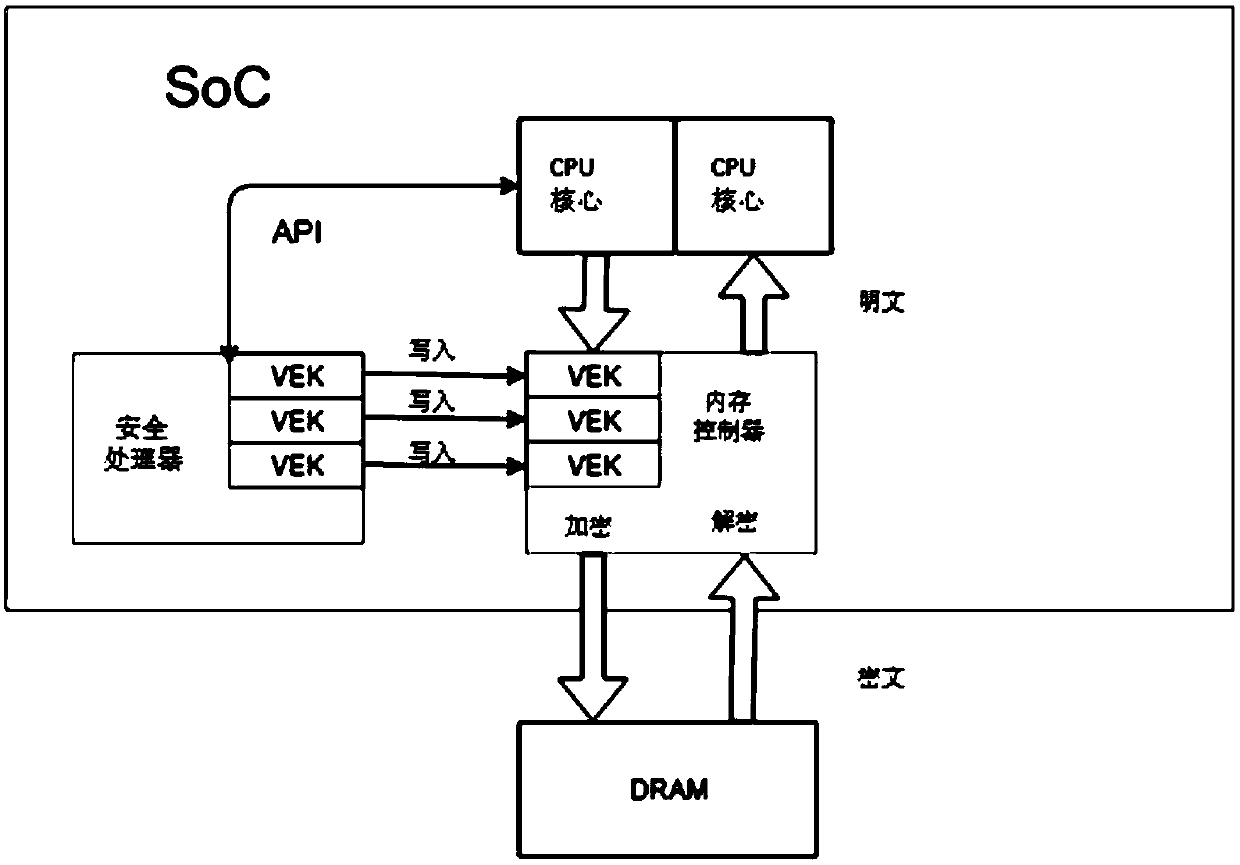
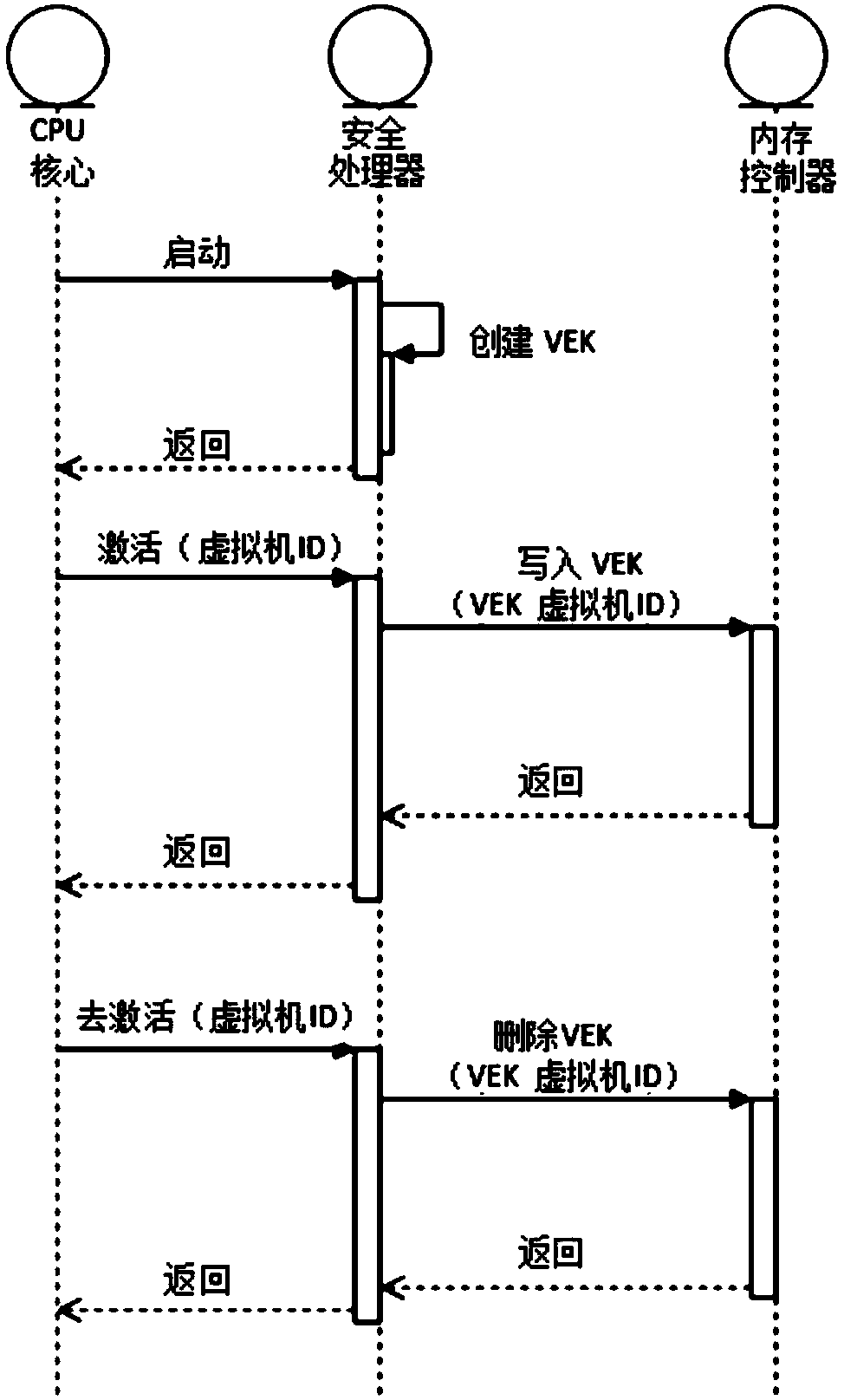
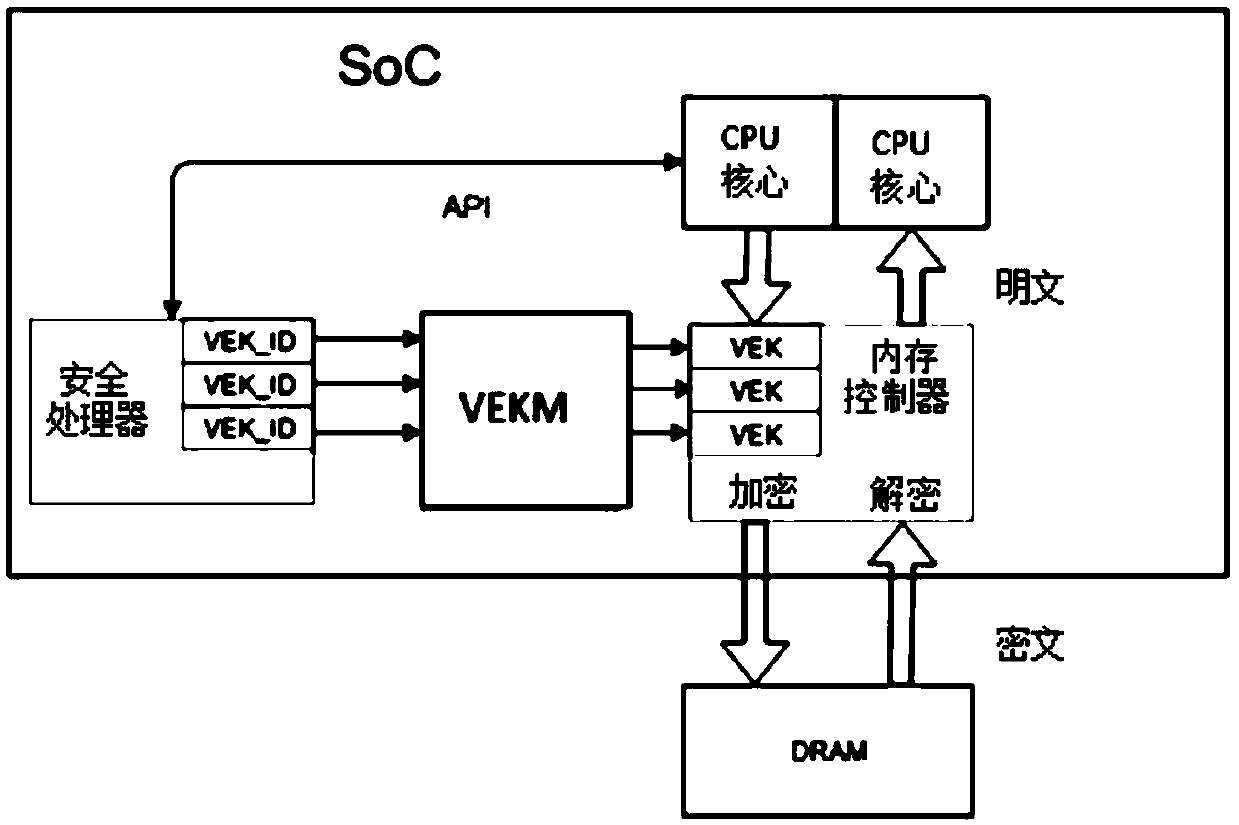
[0034] To ensure the security of VEK, the security virtualization technology uses a separate processor—the security processor to manage VEK. The processor in the security processor SoC (system on chip) handles memory encryption and decryption and starts virtual machines. The security processor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com