A credibility measuring system and method
A technology of credibility and algorithms, applied in the field of information security, can solve the problems of lack of security design in Internet networks and computer security threats at all times, and achieve the effect of ensuring data integrity, highlighting substantive features, and ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
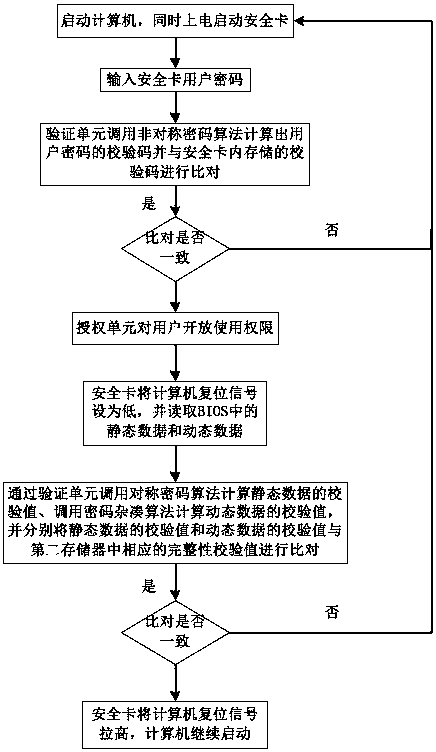
[0038] Specific embodiments of the present invention will be described below in conjunction with the accompanying drawings.
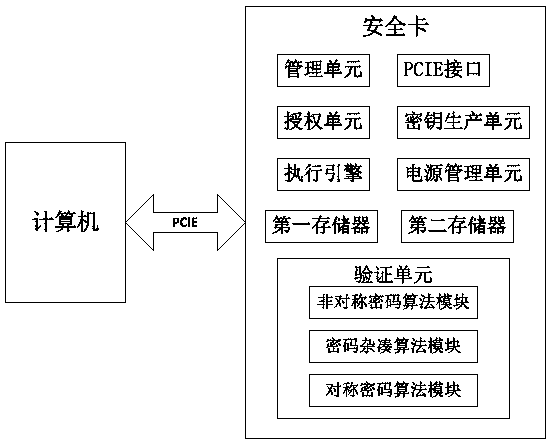
[0039] Such as figure 1 The shown trusted measurement system includes: a computer and a security chip, the security chip is installed on the motherboard of the computer through the PCIE interface, the security chip accesses the BIOS of the computer through the motherboard, and is used to protect the BIOS and the operating system from being modified.
[0040] The security chip includes:
[0041] The management unit is used to manage the internal resources of the security chip;
[0042] The PCIE interface is used for communication between the security chip and the outside world and between physical units inside the security chip. The PCIE interface includes: PCIE X1 signal interface, motherboard reset signal interface and SPI signal interface;
[0043] Verification unit for integrity check and identification;
[0044] The authorization unit is used to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com