Method and system for verifying user data
A technology of user data and verification method, applied in the field of data verification, can solve problems such as information verification loopholes, malicious server attacks, and user economic losses, so as to improve safety and reliability, avoid unnecessary losses, and ensure user data security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
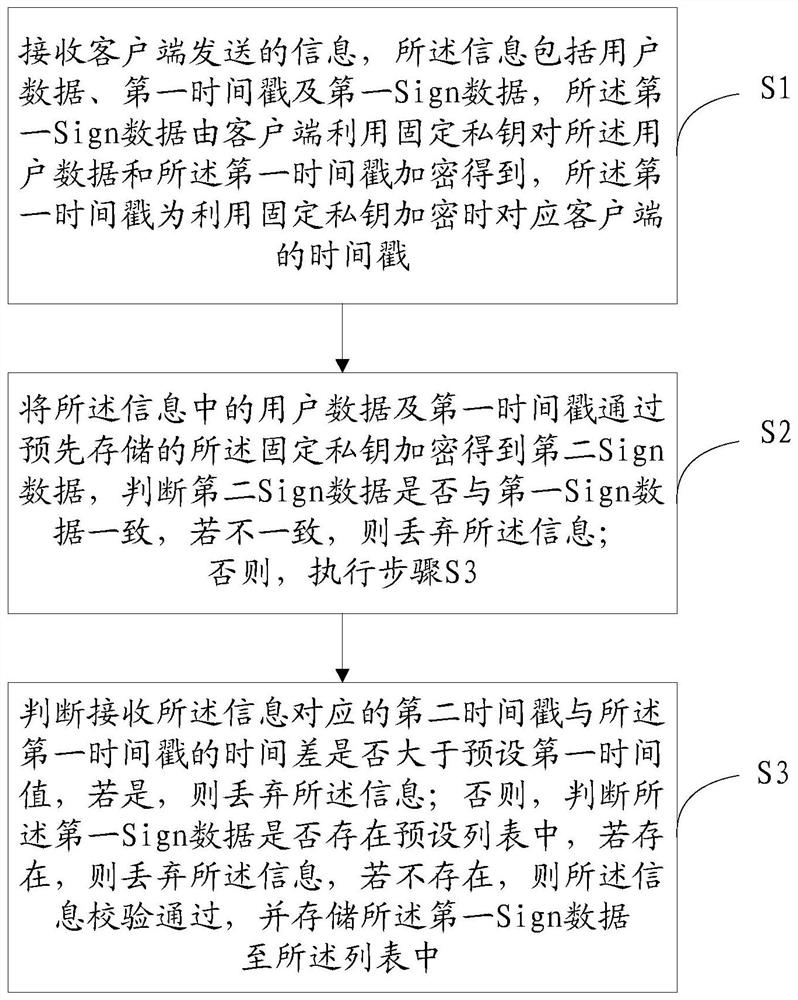
[0069] Please refer to figure 1 , Embodiment 1 of the present invention is:
[0070] A method for verifying user data provided by the present invention includes the following steps:
[0071] S1: Receive the information sent by the client, the information includes user data, first time stamp and first Sign data, and the first Sign data is paired by the client using a fixed private key to the user data and the first time The stamp is obtained by MD5 encryption, and the first timestamp is the timestamp corresponding to the client when encrypted with a fixed private key;
[0072] S2: Encrypt the user data and the first timestamp in the information with the pre-stored fixed private key through MD5 to obtain the second Sign data, determine whether the second Sign data is consistent with the first Sign data, if not, then Discard the information; otherwise, execute step S3;
[0073] "Judge whether the second Sign data is consistent with the first Sign data" is specifical...
Embodiment 2
[0084] A method for verifying user data provided by the present invention includes the following steps:
[0085] Encrypt the user data and the current first timestamp with a fixed key to obtain the first Sign data;
[0086] According to the user data, the first timestamp and the first Sign data, the information in JSON format is obtained;
[0087] And send the information to the server through the HTTP protocol, so that the server encrypts the user data and the first timestamp in the information with the fixed private key stored in advance by the server to obtain the second Sign data, and judges the second Whether the Sign data is consistent with the first Sign data, if not, then discard the information; otherwise: determine whether the time difference between the second timestamp of the server corresponding to receiving the information and the first timestamp is greater than the preset first time value , if so, then discard the information; otherwise, judge whether t...
Embodiment 3
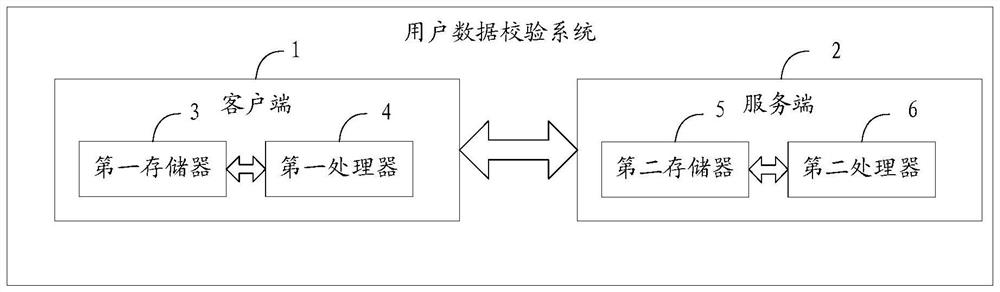
[0089] The present invention also provides a user data signature verification system, including a client and a server. The client includes a first memory, a first processor, and a system stored in the first memory and capable of running on the first processor. A first computer program, the server includes a second memory, a second processor, and a second computer program stored on the second memory and operable on the second processor, and the first processor executes the The first computer program implements the following steps:
[0090] Encrypt the user data and the current first timestamp with a fixed key to obtain the first Sign data;
[0091] According to the user data, the first timestamp and the first Sign data, the information in JSON format is obtained;
[0092] And send the information to the server through the HTTP protocol, so that the server encrypts the user data and the first timestamp in the information with the fixed private key stored in advance by th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com