Method, system, device and storage medium for brute force attack detection
An attack detection and brute force technology, applied in the field of network security, can solve the problem of not considering the network status, unable to detect whether the brute force attack is successful, etc., to achieve the effect of solving the judgment problem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
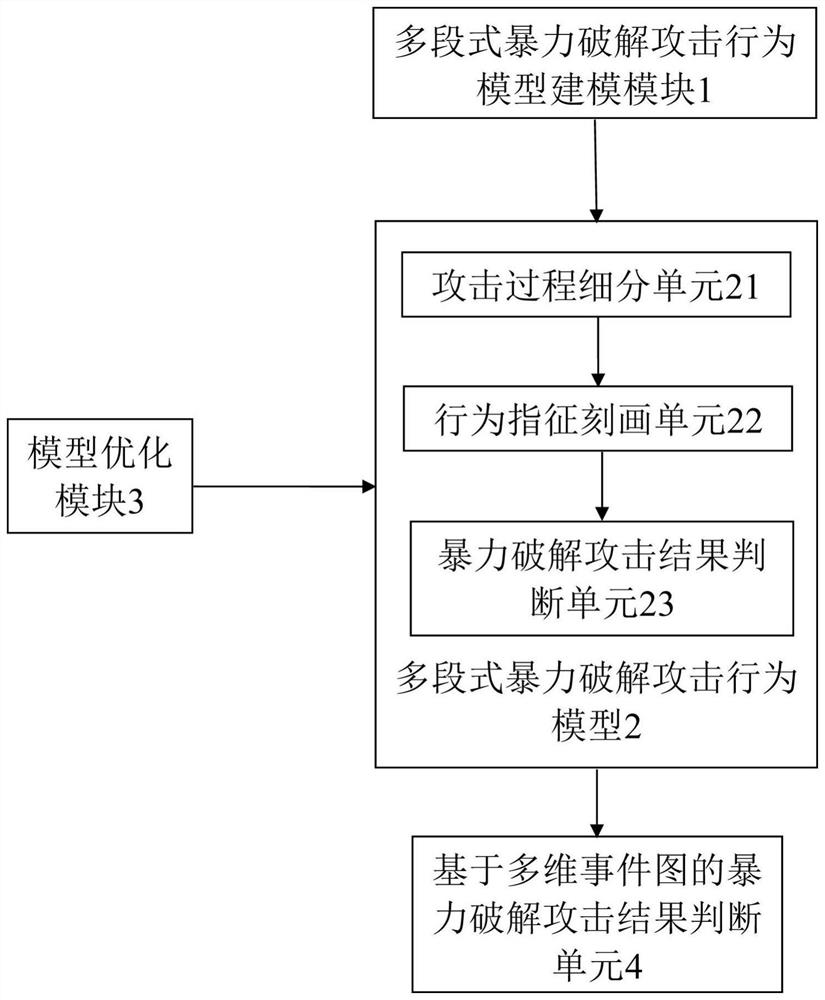
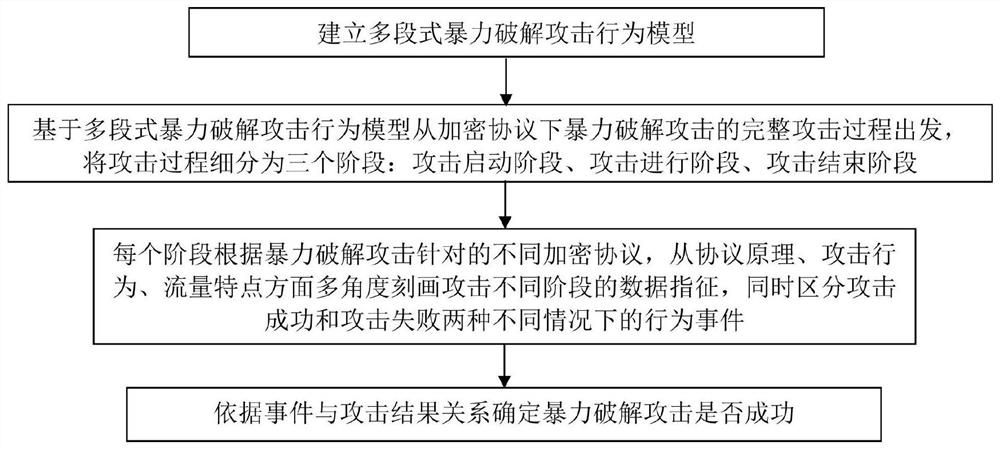
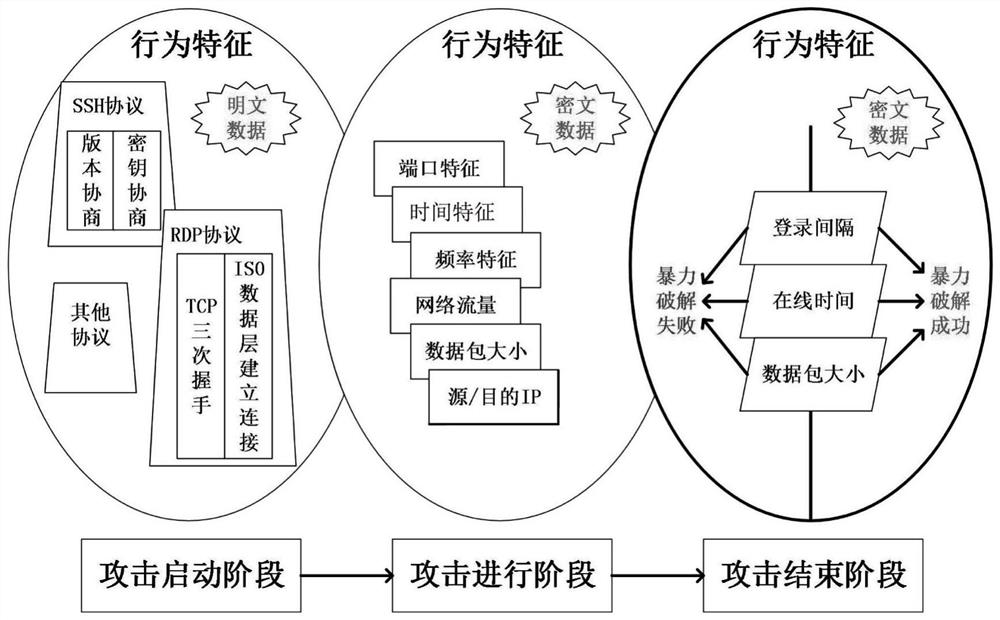
[0031] Brute force cracking attack means that the attacker enumerates all possible username / password combinations by guessing or dictionary, sends them as login credentials to the server login verification system, and tries to guess one by one to find usable username / password pairs.
[0032]According to the differences in the transmission modes supported by different connection protocols, user login can be roughly divided into plaintext login and ciphertext login. It is relatively easy to detect and judge the success of a brute-force cracking attack under the condition of plaintext login. The success of the attack can be confirmed by checking the key fields of the server response packet. The ciphertext login system uses an encryption protocol to ensure the privacy of transmitted data, which increases security for users and increases difficulty for detection. Since the client and the server use the negotiated public / private key pair to encrypt the communication data between the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com