An efficient privacy protection perception big data collection method based on fog computing
A technology of privacy protection and fog computing, which is applied in security devices, network traffic/resource management, electrical components, etc., and can solve problems such as ignoring the privacy protection of sensitive data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described in detail below through the specific examples, the following examples are only descriptive, not restrictive, and cannot limit the protection scope of the present invention with this.
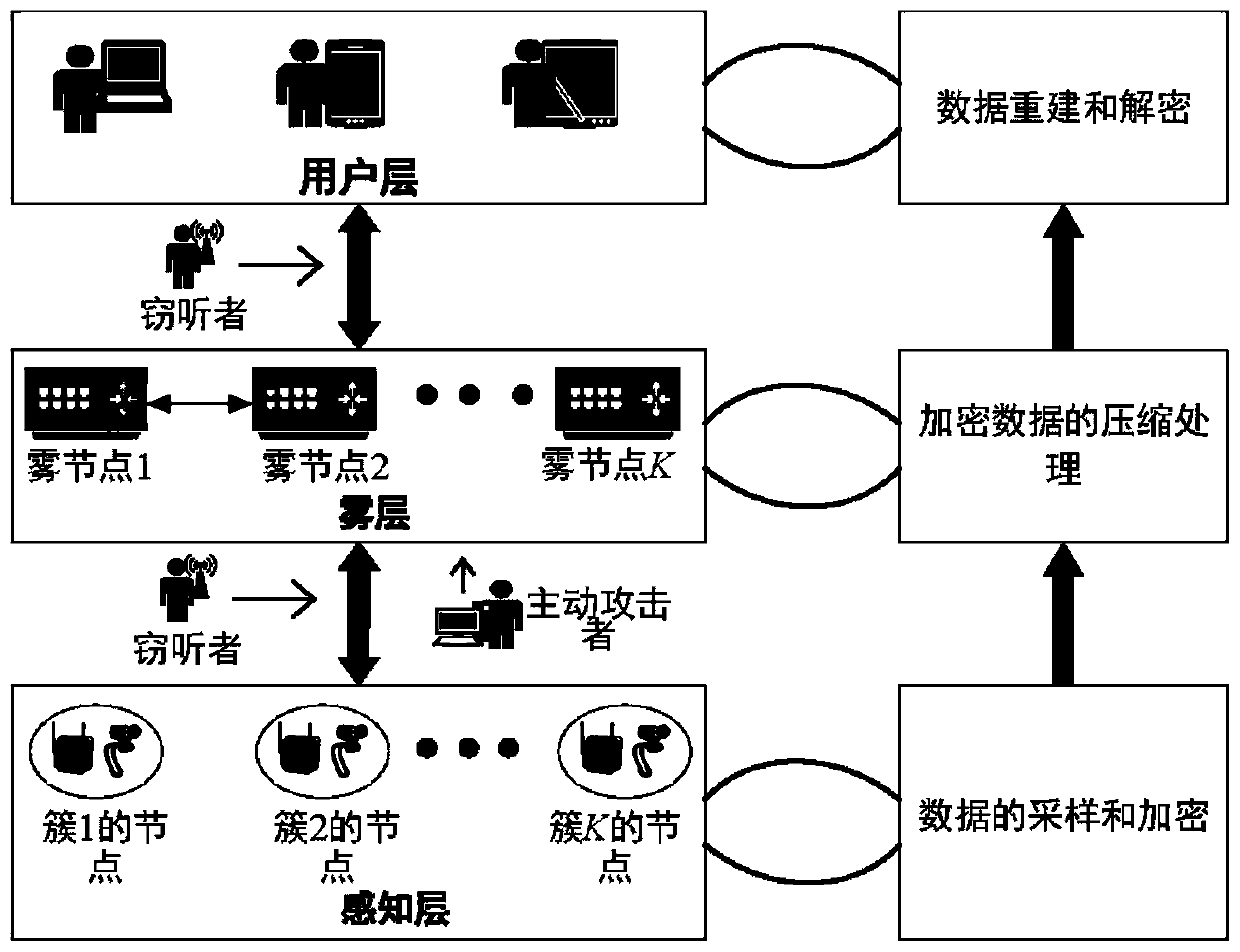
[0052] Such as figure 1 As shown, an efficient privacy protection-aware big data collection method based on fog computing includes the following steps:
[0053] (1) Design a layered perception fog computing architecture. The perception fog computing architecture is divided into interconnected perception layer, fog layer and user layer from bottom to top.
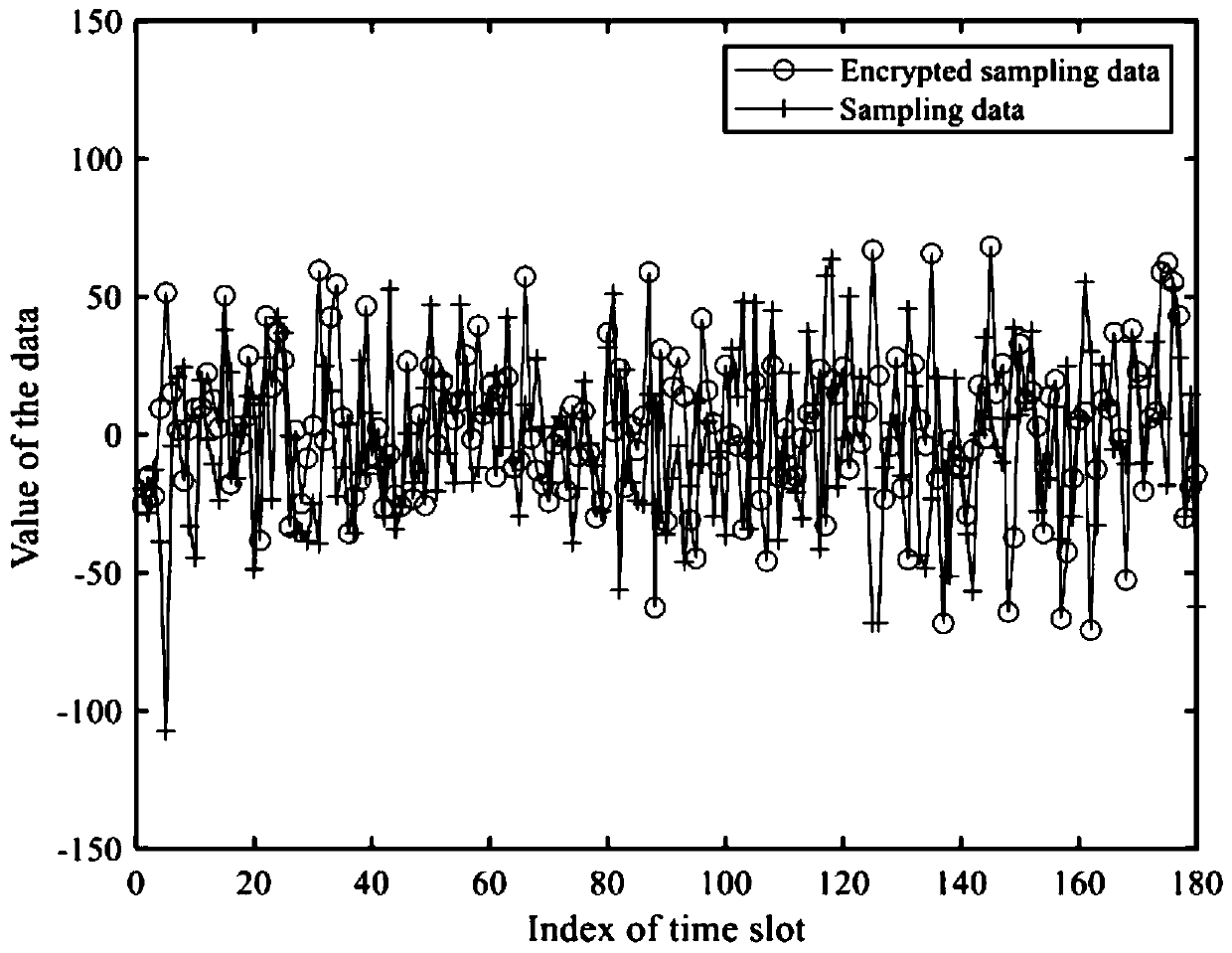
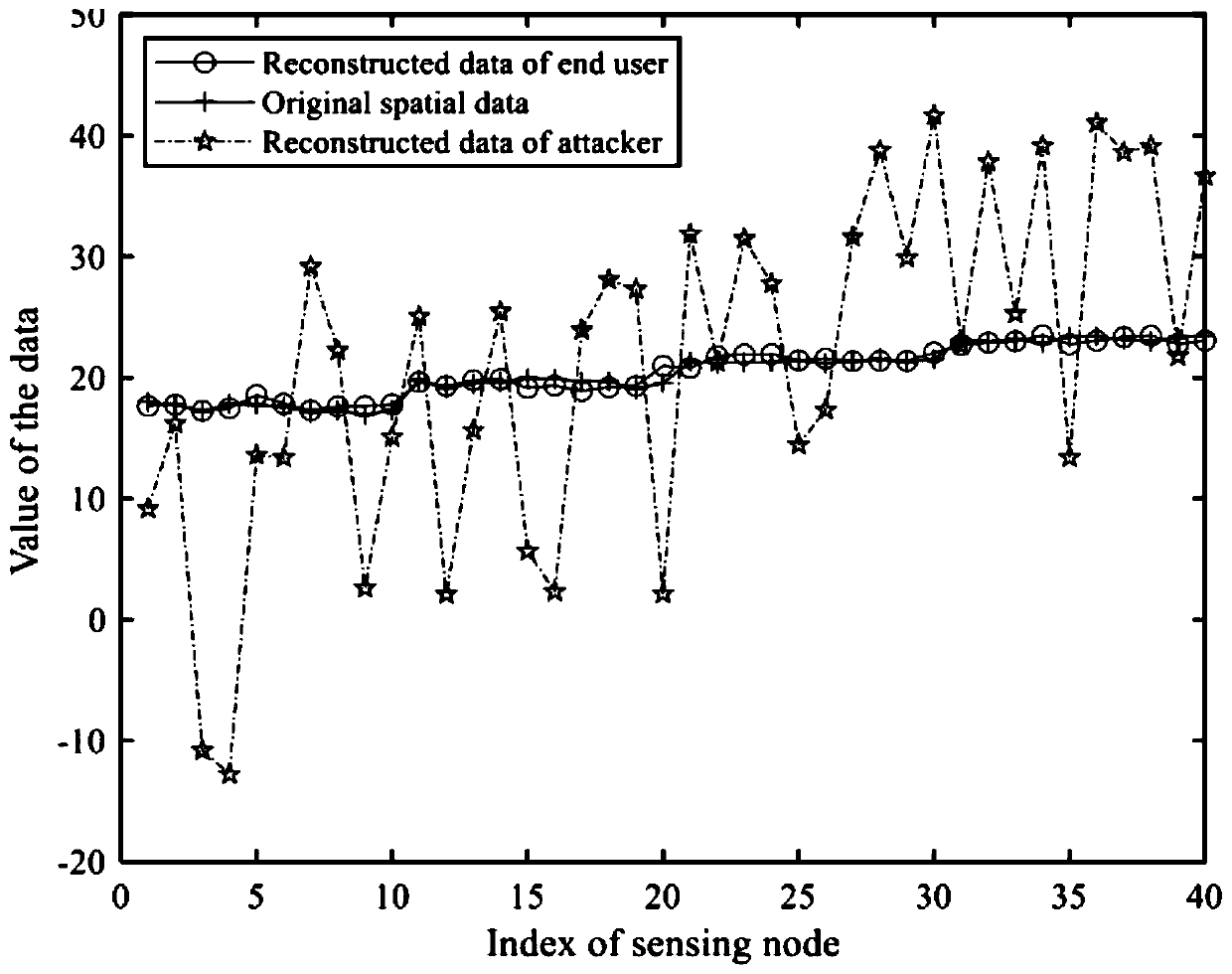
[0054] The sensing layer consists of various sensing devices for monitoring designated areas. According to the location information of sensing devices, it is divided into multiple clusters. That is, the perception layer consists of K clusters, each cluster contains L perception nodes, and the sampling period of the perception nodes is N. The perception device performs disturbance and en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com