An image encryption method and device
An encryption method and image technology, applied in the field of image processing, can solve the problems of obvious outline and concentrated encrypted information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
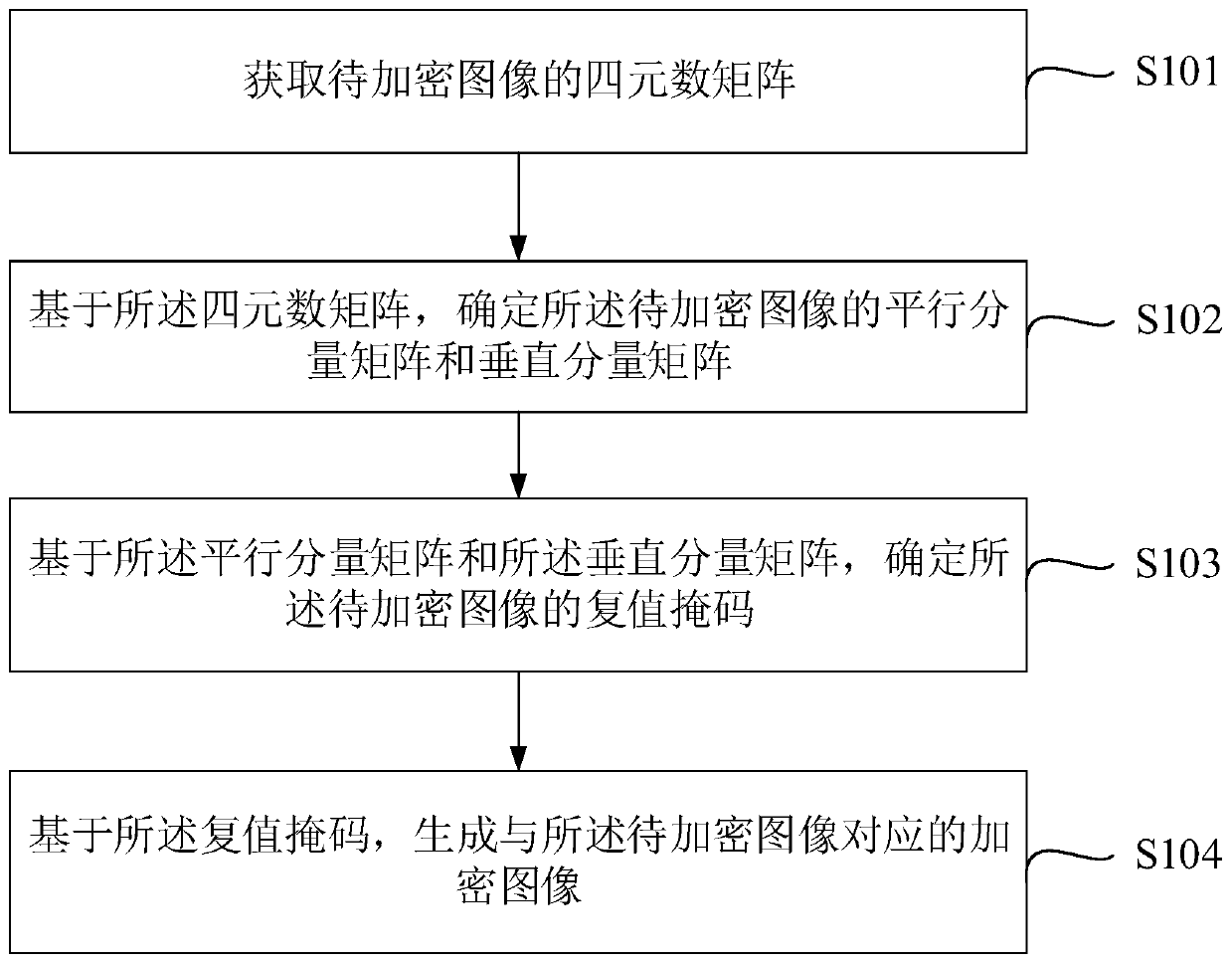
[0079] See figure 1 As shown, figure 1 This is a flowchart of an image encryption method provided in the first embodiment of this application, the method includes:
[0080] S101: Obtain a quaternion matrix of the image to be encrypted.
[0081] In a specific implementation, the image to be encrypted is first obtained, and the image to be encrypted is expressed as a first quaternion matrix, and further, the first quaternion matrix is Fourier transformed to obtain the second quaternion matrix.
[0082] Here, the formula for expressing the image to be encrypted as the first quaternion matrix can be f(x,y)=f 1 (x,y)+if 2 (x,y)+jf 3 (x,y)+kf 4 (x,y), where f(x,y) is the first quaternion matrix, f 1 (x,y), f 2 (x,y), f 3 (x,y), f 4 (x, y) is each single-channel image corresponding to the image to be encrypted, where the imaginary units i, j, and k satisfy ij=-ji=k, jk=-kj=i, ki=-ik=j, i 2 =j 2 =k 2 = -1.
[0083] Here, the image to be encrypted can have two forms:
[0084] Form 1: The ima...
Embodiment 2
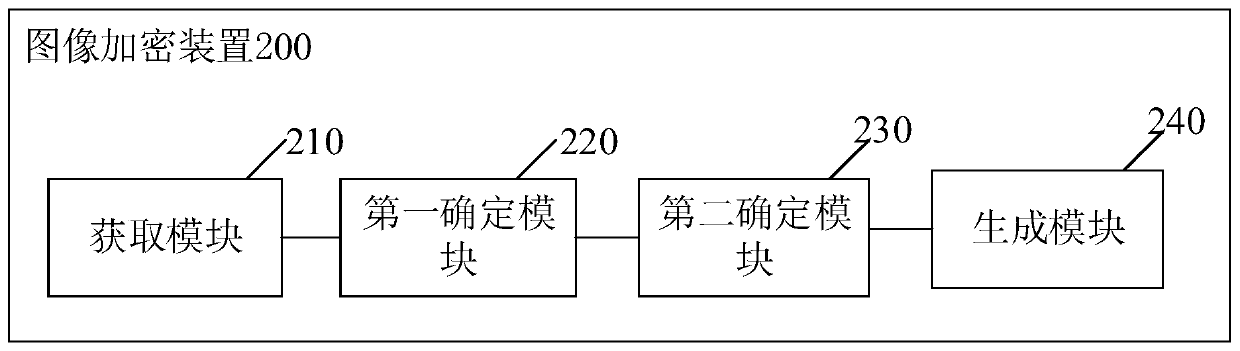
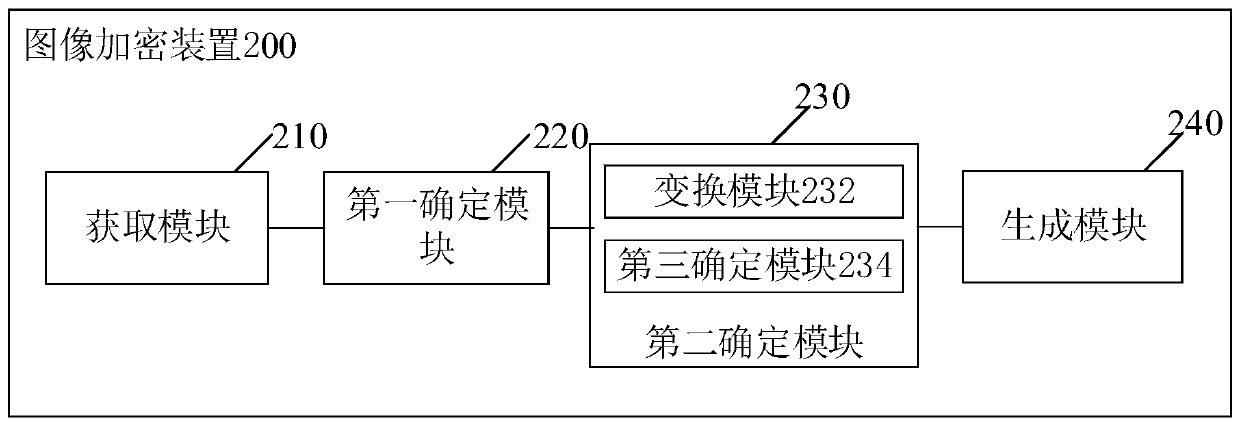
[0139] Based on the same application concept, the second embodiment of the application also provides an image encryption device corresponding to the image encryption method provided in the first embodiment. Since the principle of the device in the embodiment of the application to solve the problem is the same as that in the above-mentioned embodiment of the application The image encryption method is similar, so the implementation of the device can refer to the implementation of the method, and the repetition will not be repeated.
[0140] See figure 2 As shown, one of the functional module diagrams of an image encryption device 200 provided in the second embodiment of this application; see image 3 As shown, the second functional block diagram of an image encryption device 200 provided in the second embodiment of this application; wherein, the image encryption device 200 includes:
[0141] The obtaining module 210 is used to obtain the quaternion matrix of the image to be encrypted...
Embodiment 3
[0169] Based on the same application concept, see Figure 4 As shown, this is a schematic structural diagram of an electronic device 400 provided in the third embodiment of this application, including: a processor 410, a memory 420, and a bus 430. The memory 420 stores machine-readable instructions executable by the processor 410 When the electronic device 400 is running, the processor 410 and the memory 420 communicate through the bus 430, and the machine-readable instructions are executed when the processor 410 is running. figure 1 For the steps of the image encryption method in the first embodiment of the method shown, for specific implementation manners, please refer to the method embodiment, which will not be repeated here.
[0170] Specifically, when the machine-readable instruction is executed by the processor 410, the following steps are executed:
[0171] Obtain the quaternion matrix of the image to be encrypted;
[0172] Determine the parallel component matrix and the ver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com