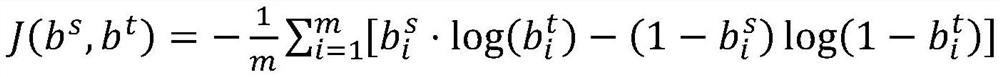Internet of things intrusion detection method based on combination of decision tree and self-similar model
An intrusion detection and decision tree technology, applied in the field of Internet of Things security, can solve the problems of failure to detect intrusion behavior, comparison, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
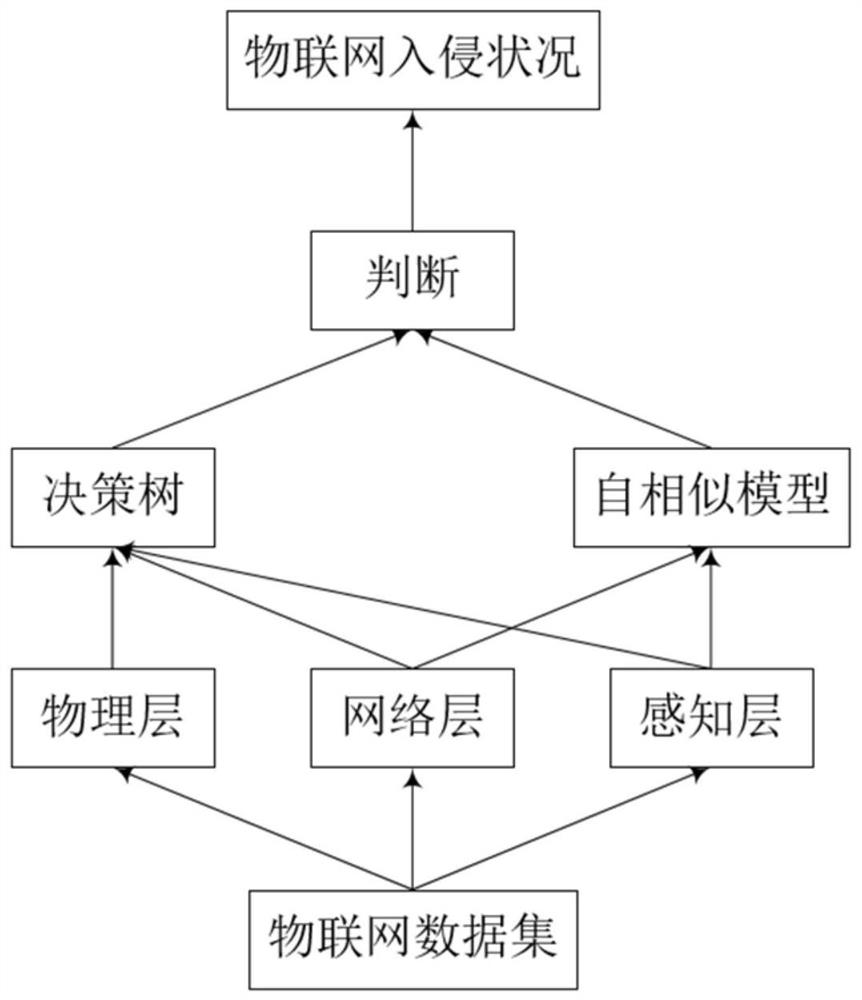
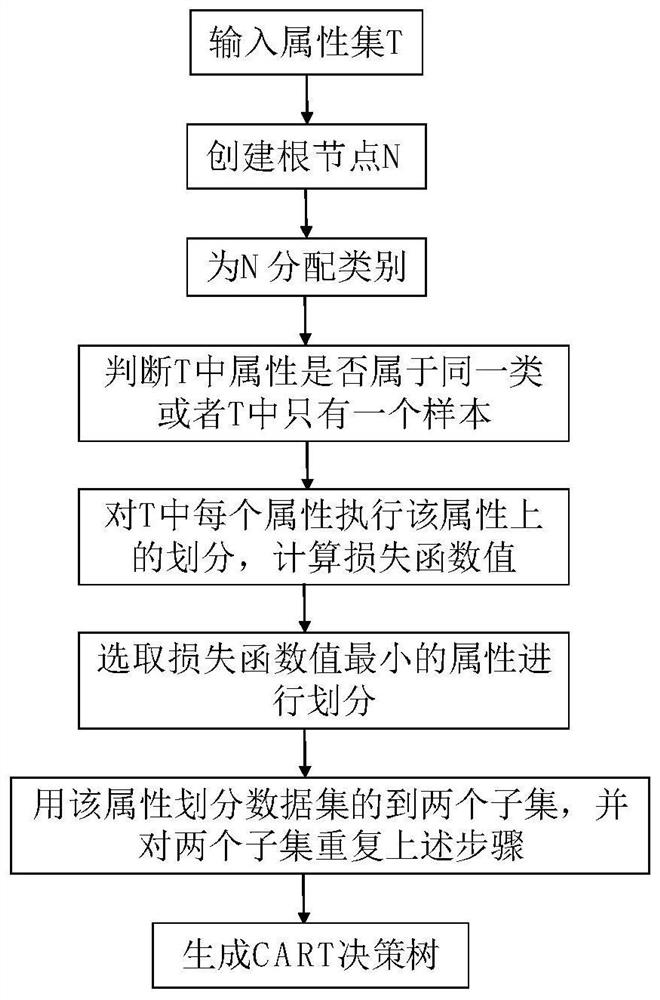
[0040] like figure 1 As shown, this embodiment designs an IoT intrusion detection method based on decision tree and self-similarity theory. According to the steps of this embodiment, a slight modification can also be used for intrusion detection in other network environments.
[0041] 1. Select a suitable dataset. Provides a data source for the decision tree algorithm to generate decision trees and self-similar models.
[0042] On the one hand, since the use of the decision tree algorithm to generate a decision tree is a process of machine learning, corresponding training sets and test sets need to be used. On the other hand, the self-similarity of self-similar theory means that the characteristics of a certain structure or process are similar from different spatial or temporal scales, or that the local properties or local structure of a system or structure are similar to the overall Similar. In addition, there is also self-similarity between the whole and the whole or betwe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com