Hybrid intrusion detection method based on Internet protocol version 6
An Internet protocol and intrusion detection technology, applied in the field of network security, to achieve the effect of improving overall security and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
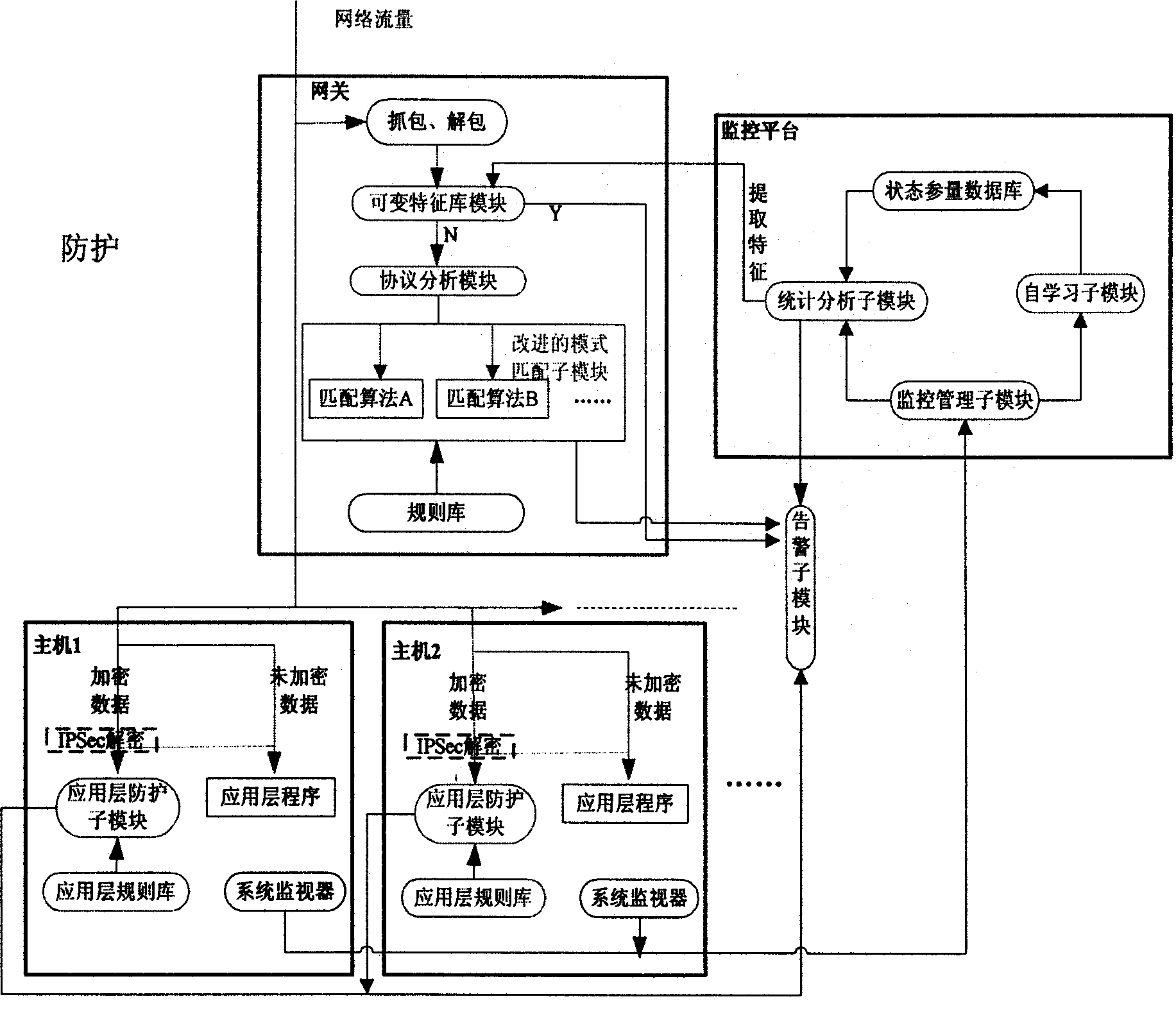
[0074] In order to meet the needs of the IPv6 environment, the IDS of this project adopts the overall architecture based on the combination of network and host, such as figure 1 shown.
[0075] 1. Protocol analysis sub-module
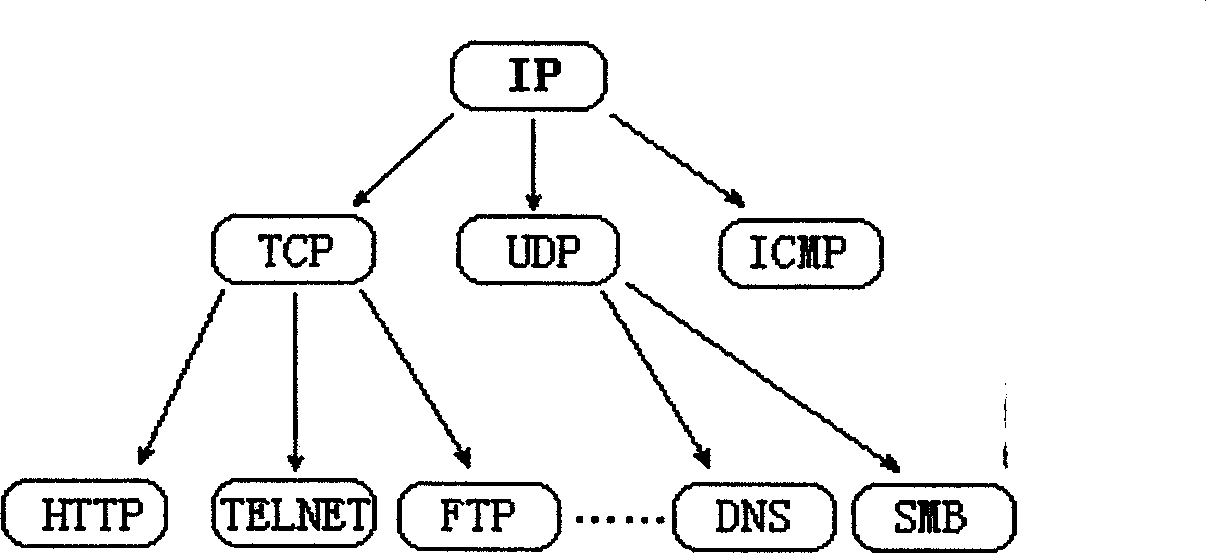
[0076] The protocol analysis sub-module is located on the variable feature library module, and performs protocol analysis on the received data packets, and divides the data packets into different detection method sets according to the analysis results. Matching algorithm A and matching algorithm B in the figure respectively represent optimization algorithms designed for specific protocols. In actual development, protocol analysis can be further refined, such as Figure 2 Show. This matching algorithm technology takes advantage of the highly ordered nature of network protocols, effectively reduces the matching range of targets, greatly reduces the amount of calculation, greatly improves the efficiency of intrusion analysis, and also makes the system m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com