Method for constructing dynamic heterogeneous redundant architecture
A dynamic heterogeneous and heterogeneous technology, applied to electrical components, transmission systems, etc., can solve problems such as difficult escapes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
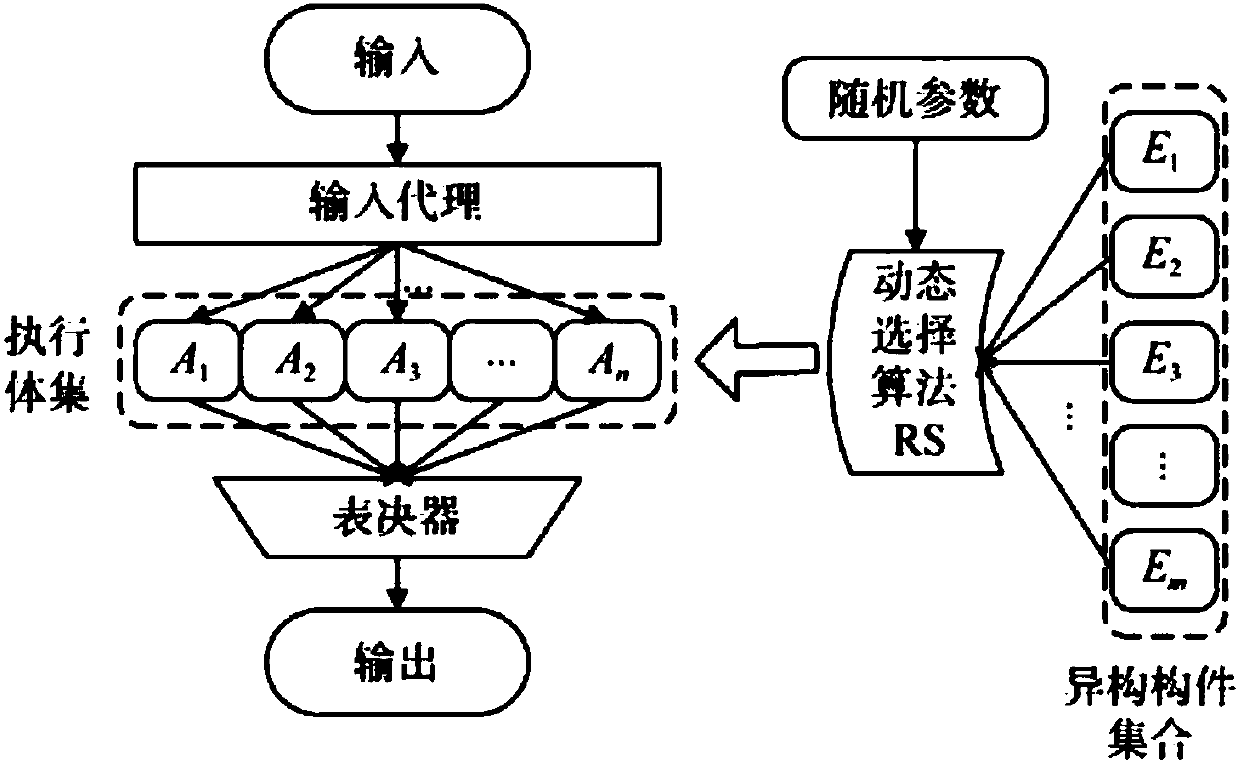
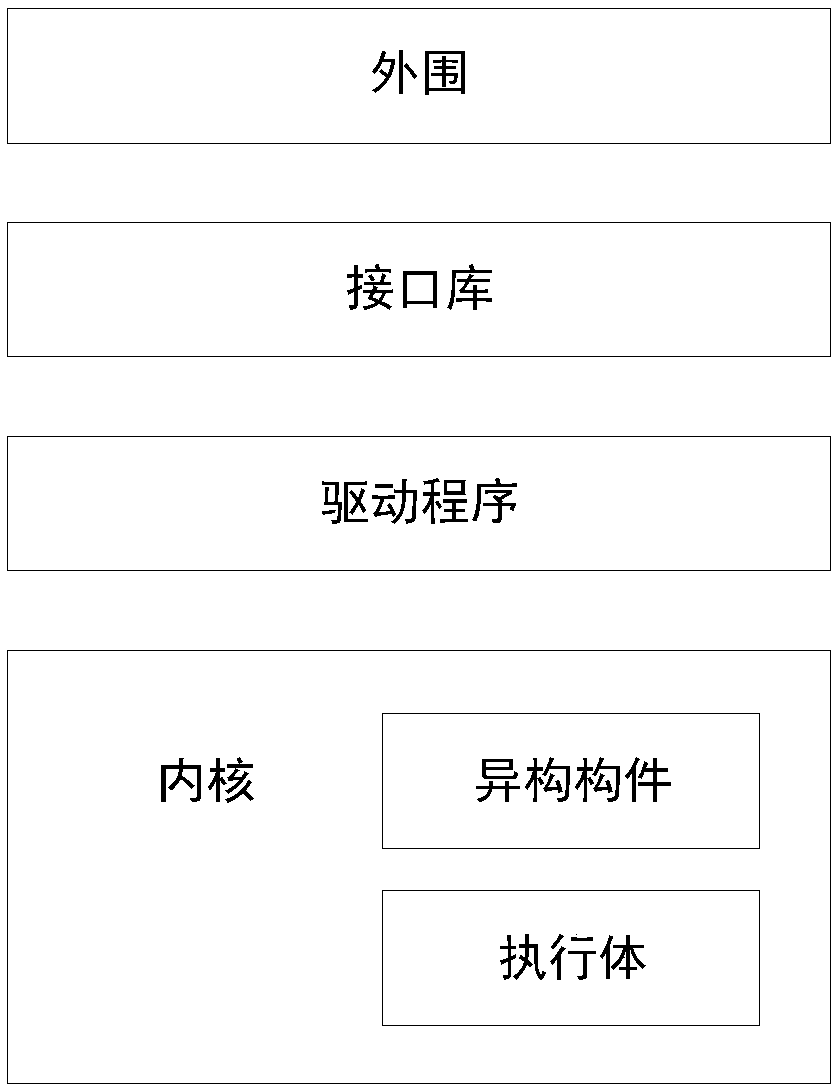
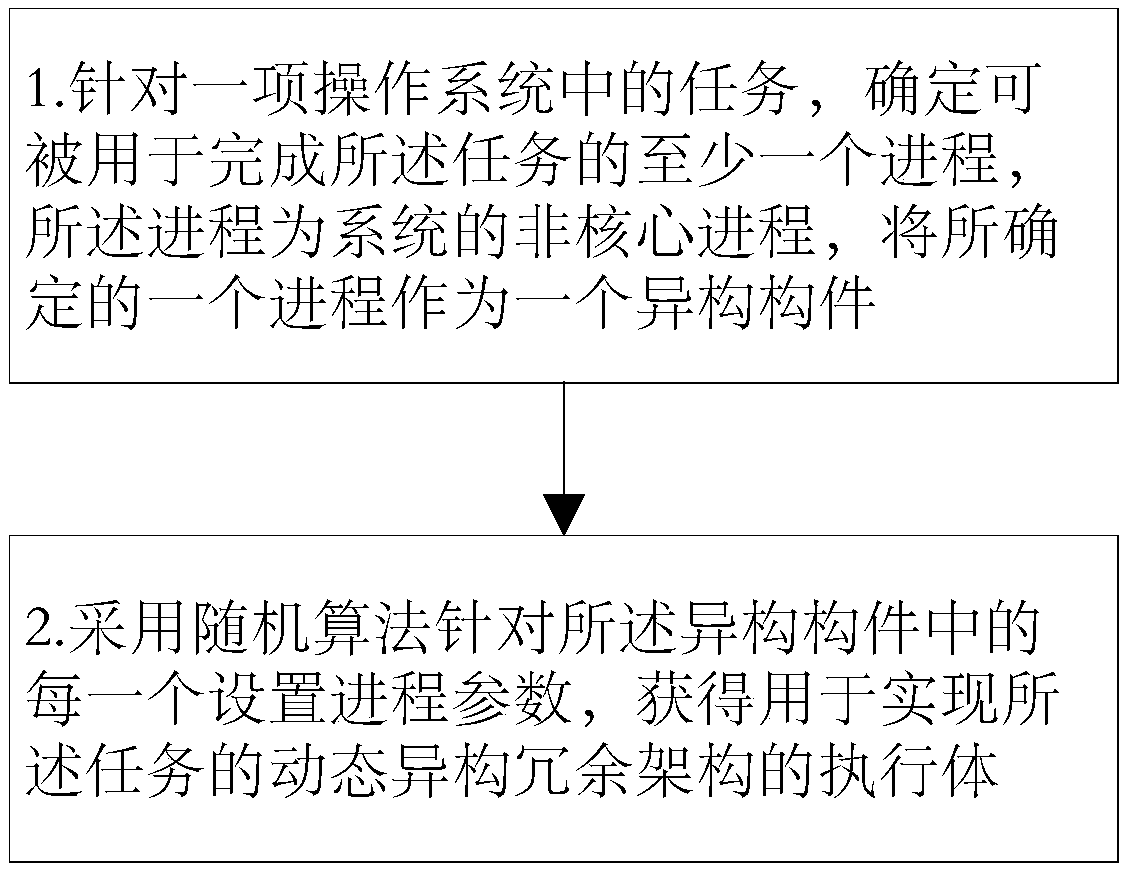
[0043] As introduced in the background technology, the DHR architecture dynamically and randomly configures the parameters of heterogeneous elements to obtain functionally equivalent heterogeneous executives. However, this method is not operable in all fields.
[0044] figure 1A schematic structural diagram of an existing DHR architecture is shown. refer to figure 1 , the system includes an input agent, a collection of heterogeneous components, a dynamic selection algorithm using random parameters, an executive body set, and a voter. The input agent and the voter constitute a "mimic bracket", and the protection scope limited by the mimic bracket is A "poisonous" heterogeneous execution environment with unknown vulnerabilities, backdoors, software and hardware codes such as viruses and Trojan horses. When in use, m functionally equivalent h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com