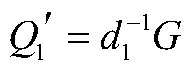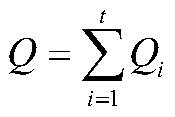Digital signature method for secret key distributed generation
A digital signature and distributed technology, applied in the direction of digital transmission system, homomorphic encryption communication, user identity/authority verification, etc., can solve the problem of low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
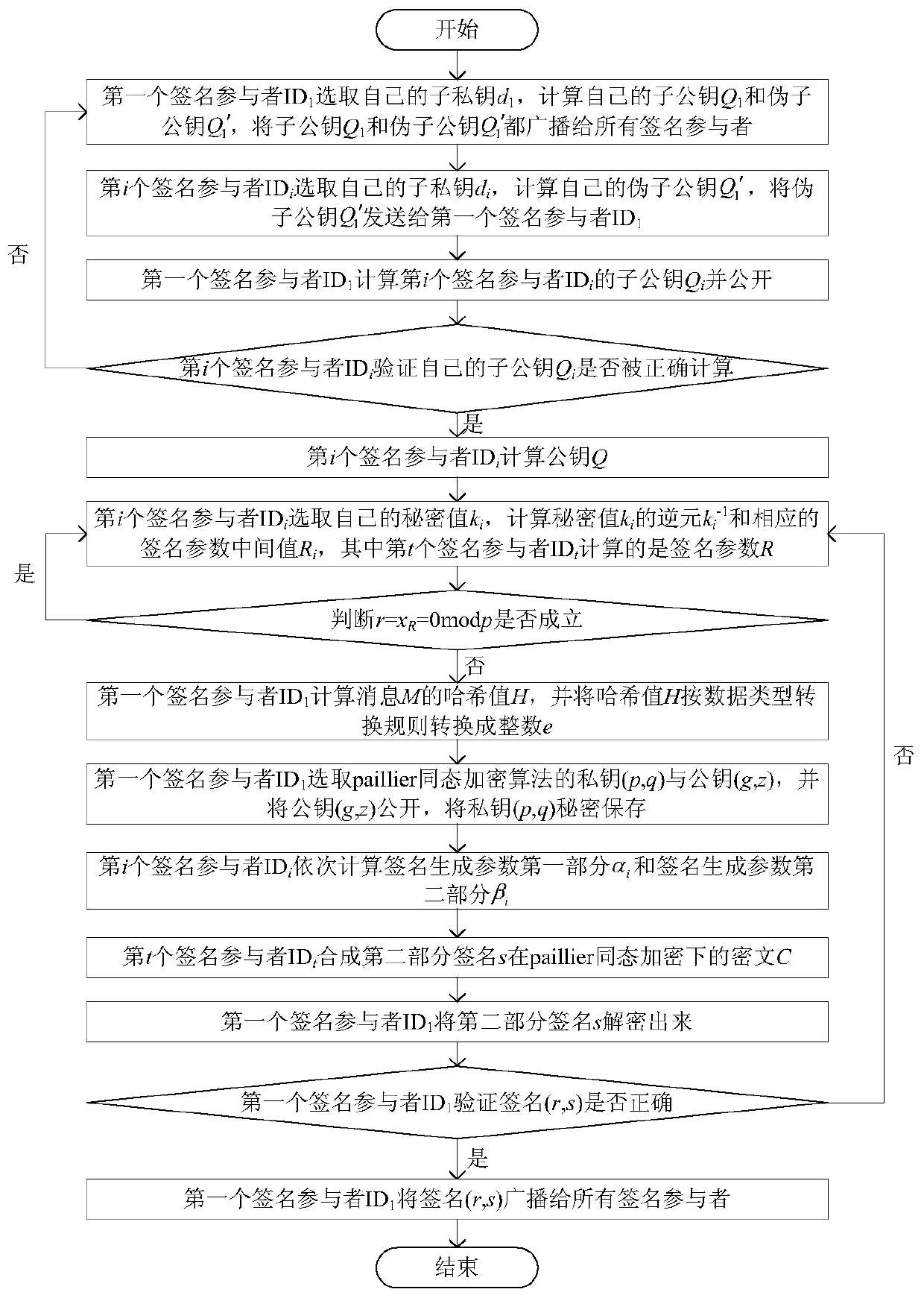
[0092] Glossary:
[0093] T: Parameters of the elliptic curve secp256k1;
[0094] p: generate finite field F p A large prime number whose value is FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEFFFFFC2F=2 256 -2 32 -2 9 -2 8 -2 7 -2 6 -2 4 -1;
[0095] a, b: parameters of the ellipse equation, a=0, b=7;
[0096] G: The base point of an order n on the elliptic curve, its value is 0479BE667EF9DCBBAC55A06295CE870B07029BFCDB2DCE28D959F2815B16F81798483ADA7726A3C4655DA4FBFC0E1108A8FD17B448A68554199C40D47D48FFB;
[0097] n: The order of the base point G of the elliptic curve, its value is FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141;
[0098] h: cofactor, control the density of selected points, its value is 01;
[0099] ID 1 : the first signing participant;
[0100] ID 2 : the second signature participant;
[0101] ID i : the i-th signature participant;
[0102] ID i+1 : the i+1th signature participant;
[0103] ID t : the tth signature p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com