Data processing method, device and system, trusted computing device, appartus and medium
A technology of trusted computing and data processing, applied in the field of data processing, to achieve the effect of ensuring reliability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
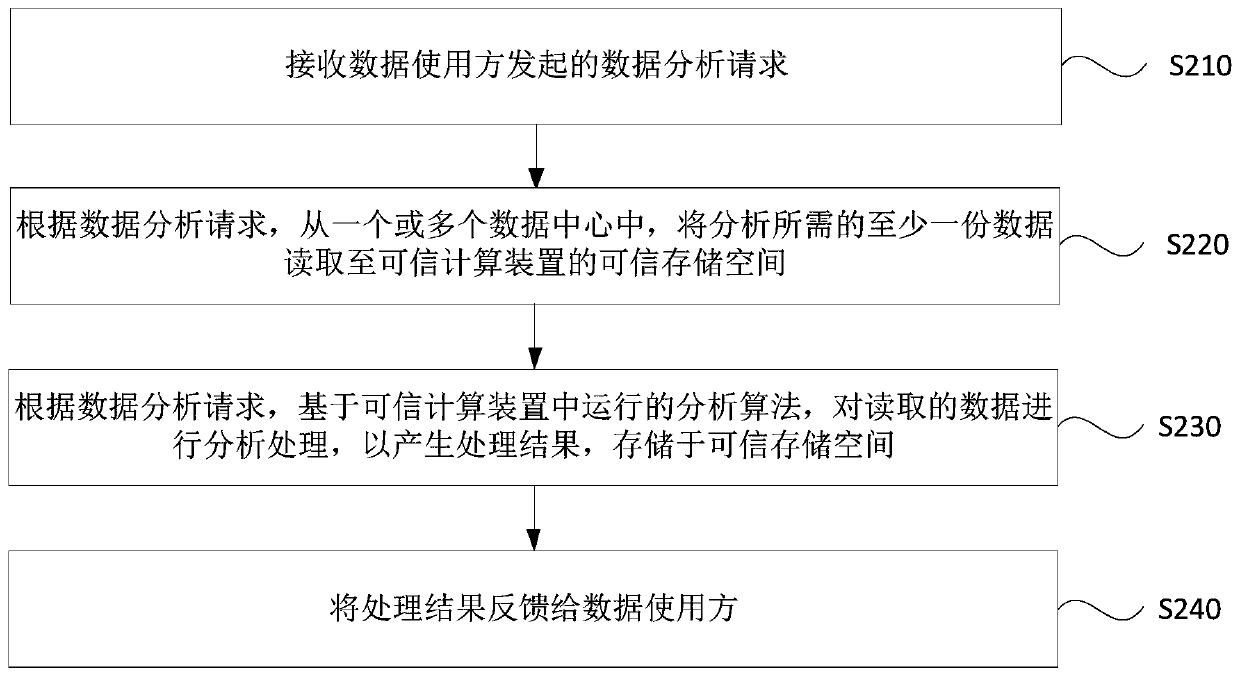
[0055] figure 2 It is a flow chart of a decentralized data processing method provided in Embodiment 1 of the present invention. This embodiment is applicable to data processing, especially applicable to one or more of the decentralized data system architectures. Scenarios in which multiple trusted computing devices, multiple data centers, and data users interact with each other to process data, so as to solve the existing contradictory data processing methods based on data centers. The technical solution of the embodiment of the present invention is executed by a trusted computing device, wherein the trusted computing device implements a trusted computing environment based on hardware. The method can be executed by a decentralized data processing device, which can be configured in a computing device of a trusted computing device, and implemented in the form of hardware and / or software. see figure 2 , the method specifically includes:
[0056] S210. Receive a data analysis...
Embodiment 2
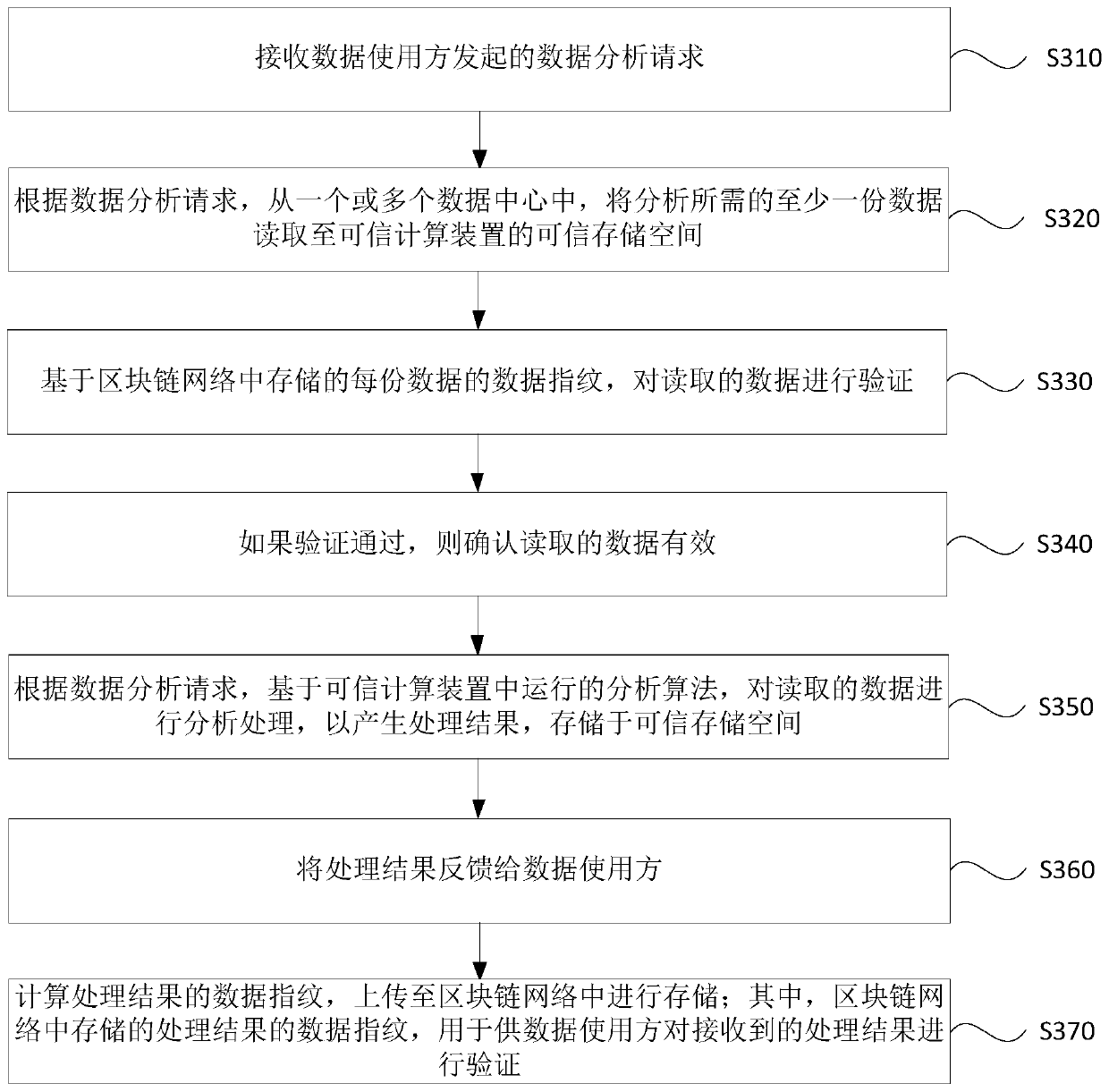
[0077] image 3 It is a flow chart of a decentralized data processing method provided in Embodiment 2 of the present invention. This embodiment is based on the above embodiments, and in the case where the decentralized data processing system architecture includes a blockchain network , for further optimization. see image 3 , the method specifically includes:
[0078] S310. Receive a data analysis request initiated by a data user.
[0079] S320. According to the data analysis request, read at least one piece of data required for analysis from one or more data centers to the trusted storage space of the trusted computing device.
[0080] S330, verifying the read data based on the data fingerprint of each piece of data stored in the blockchain network.
[0081] In this embodiment, the data fingerprint is an anti-counterfeiting signature method, which has a unique effect; for each piece of data, it can be divided into different unit data granularities according to actual need...
Embodiment 3
[0096] Figure 4 It is a flow chart of a decentralized data processing method provided in Embodiment 3 of the present invention. This embodiment is further optimized on the basis of the foregoing embodiments. see Figure 4 , the method specifically includes:
[0097] S410. Receive a data analysis request initiated by a data user.
[0098] S420. According to the data analysis request, query whether the data required for analysis exists in the trusted storage space.
[0099] In this embodiment, for the data read into the trusted storage space, the trusted storage space needs to be cleared due to the limitation of the trusted storage space usage policy. For example, when the trusted storage space is full, clear the data to release the trusted storage space Therefore, when the trusted computing device needs the read data again, it needs to read the data from the data center again; if there is data that needs to be used in the trusted computing device, it can be used directly wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com