Method for training fraudulent transaction detection model, detection method and corresponding device
A detection model and transaction technology, applied in the computer field, can solve the problems of inaccurate results and incomplete detection methods, and achieve the effect of accurate detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
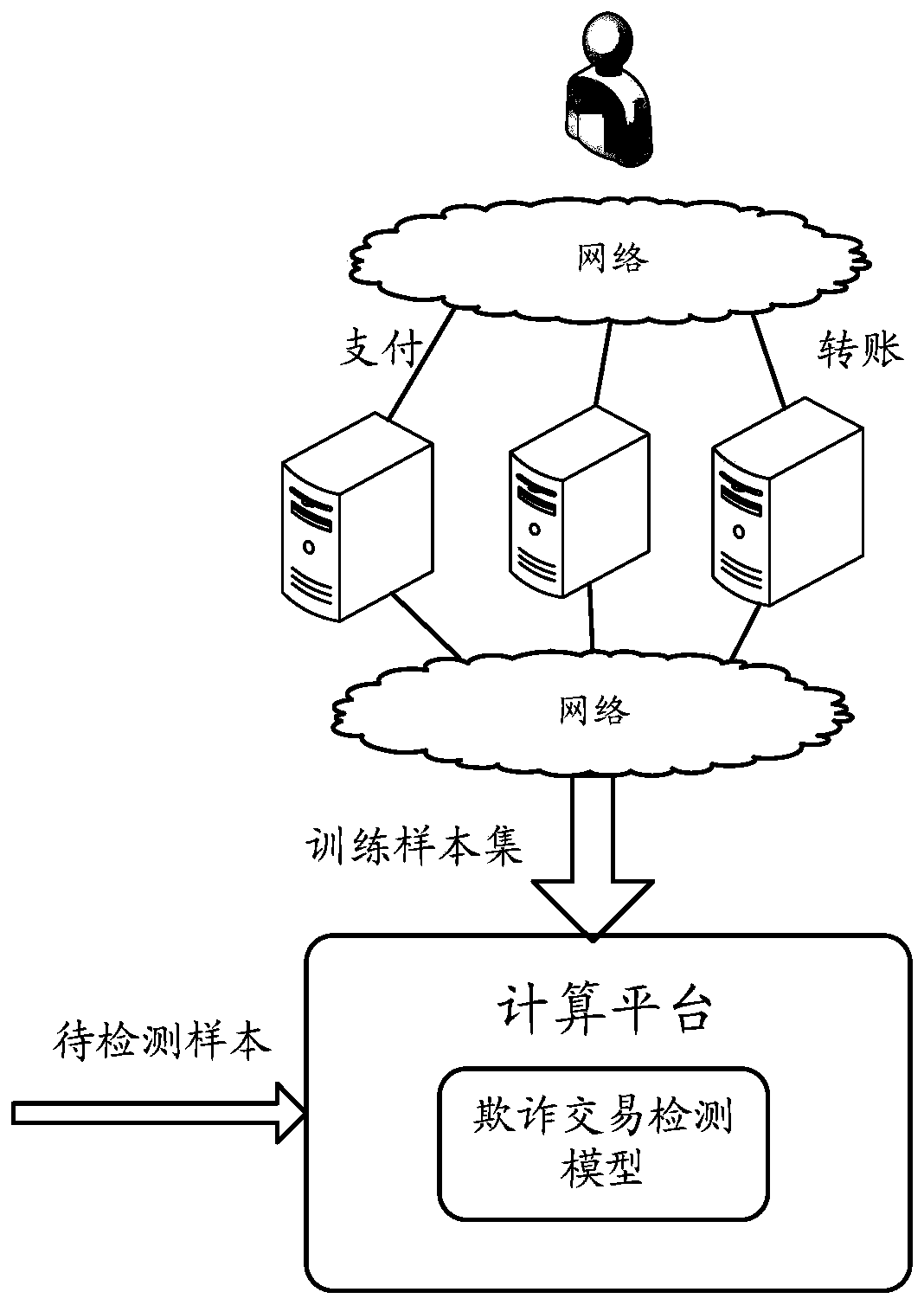
[0045] figure 1 It is a schematic diagram of an implementation scenario of an embodiment disclosed in this specification. Such as figure 1 As shown, users may perform various transaction operations through the network, such as payment, transfer, payment, etc. Correspondingly, the server corresponding to the transaction operation, such as the Alipay server, can record the user's operation history. It can be understood that the server that records the user's operation history may be a centralized server or a distributed server, which is not limited here.
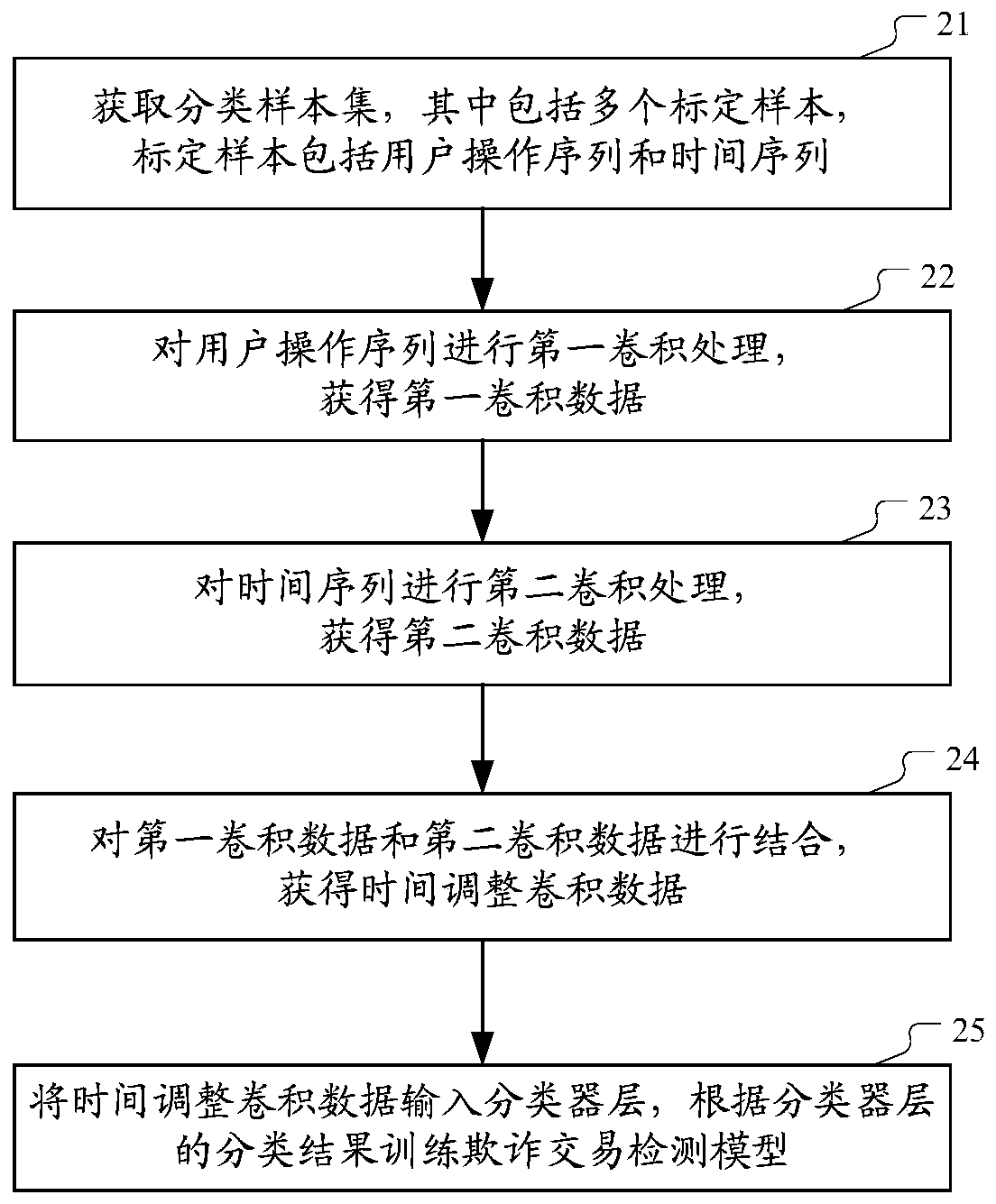
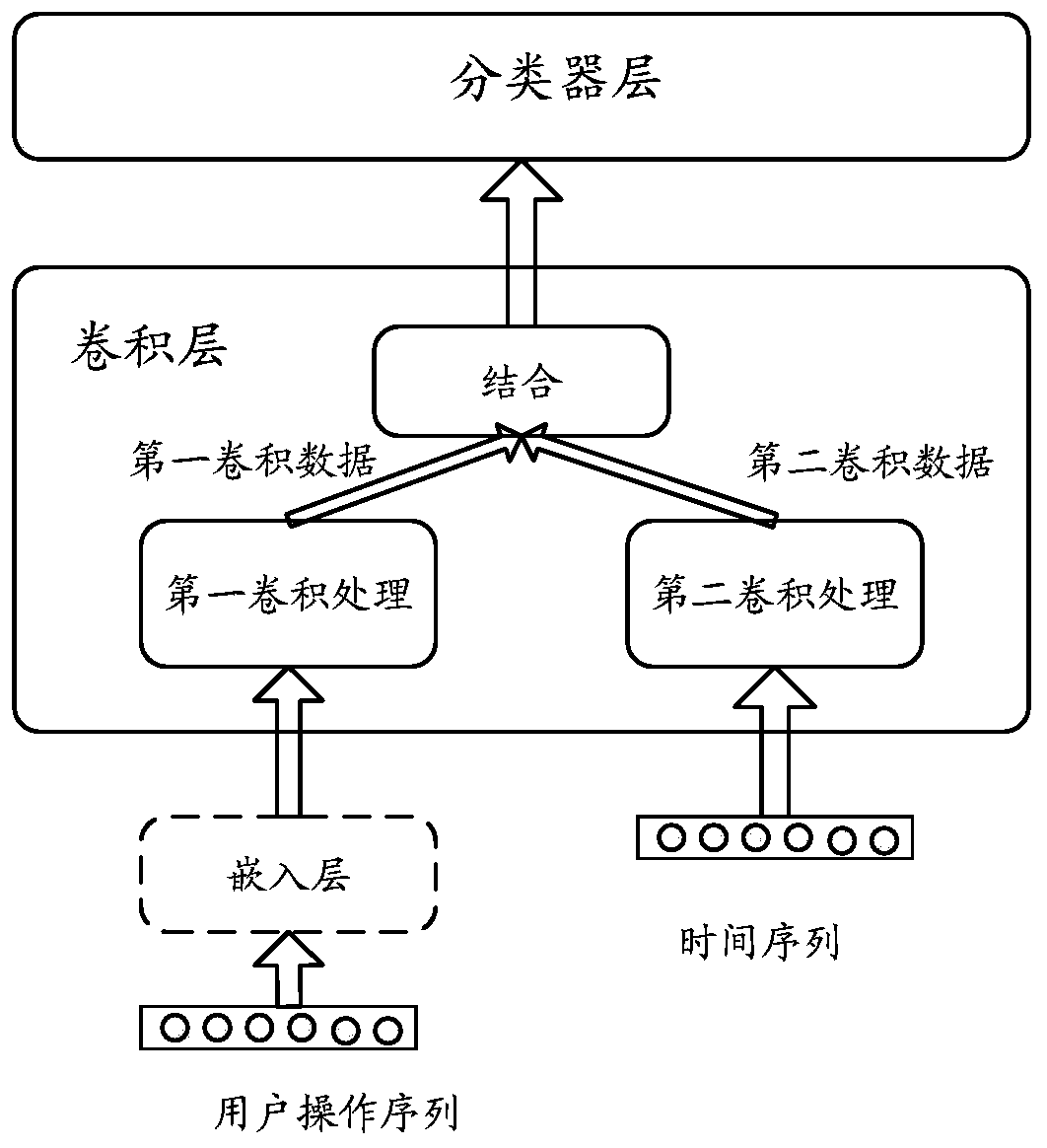
[0046] In order to train the fraudulent transaction detection model, a training sample set can be obtained from user operation records recorded in the server. Specifically, some fraudulent transaction operations and normal operations can be pre-determined by manual calibration or other methods. Then...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com