A monitoring method and system for protecting privacy
A privacy protection and monitoring system technology, applied in the field of computer vision, can solve problems such as user privacy leakage, cloud server data leakage, etc., and achieve the effects of strong scalability, small amount of feature data, and fast transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
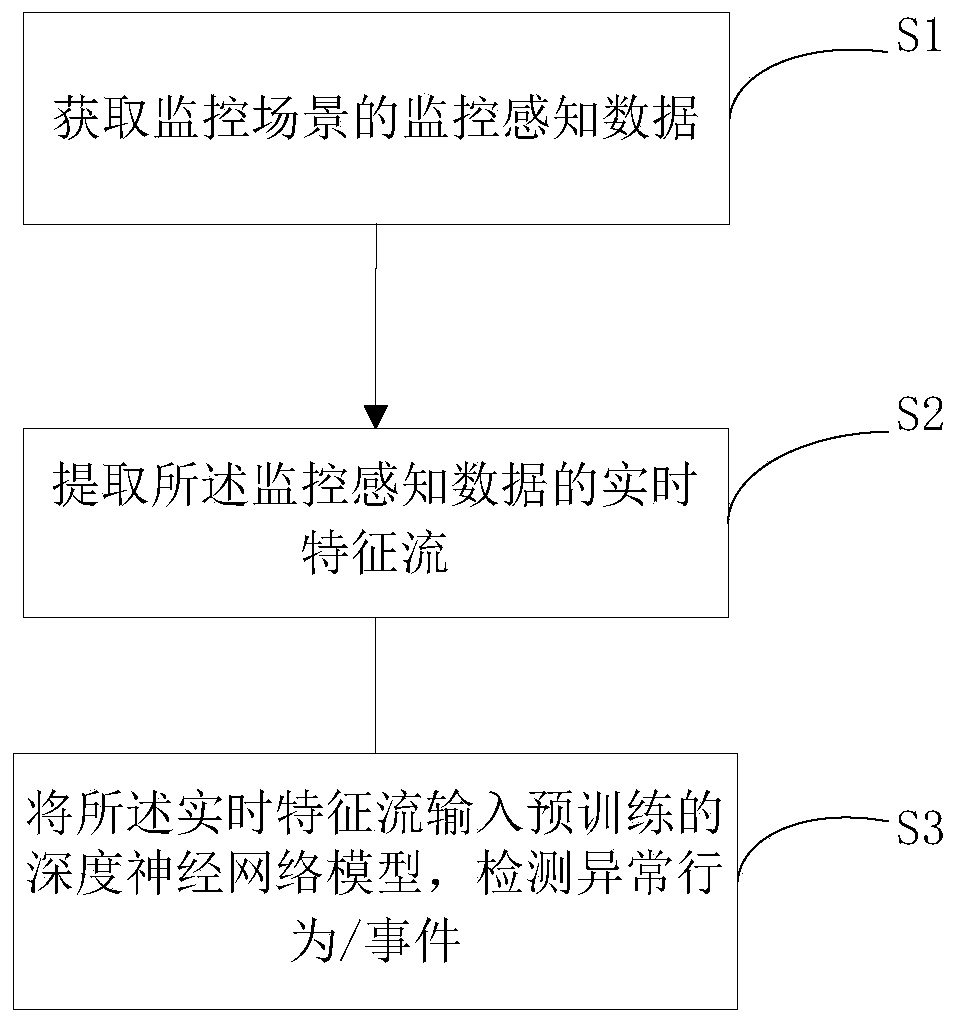
[0063] According to the embodiment of the present application, a monitoring method for protecting privacy is proposed, such as figure 1 shown, including:
[0064] S1. Obtain monitoring perception data of a monitoring scene; the monitoring perception data includes at least one of the following data: video data, audio data, smoke detection data, light detection data, and temperature data.
[0065] S2. Extracting the real-time feature stream of the monitoring perception data;
[0066] S3. Input the real-time feature stream into the pre-trained deep neural network model to detect abnormal behaviors / events.
[0067] In the following preferred embodiments, the monitoring perception data is selected as video data and / or audio data to illustrate the inventive idea of the present invention.
[0068] In a preferred embodiment of the present application, the video stream data of the surveillance scene will be decomposed into image data according to the frame requirements according to...
Embodiment 2
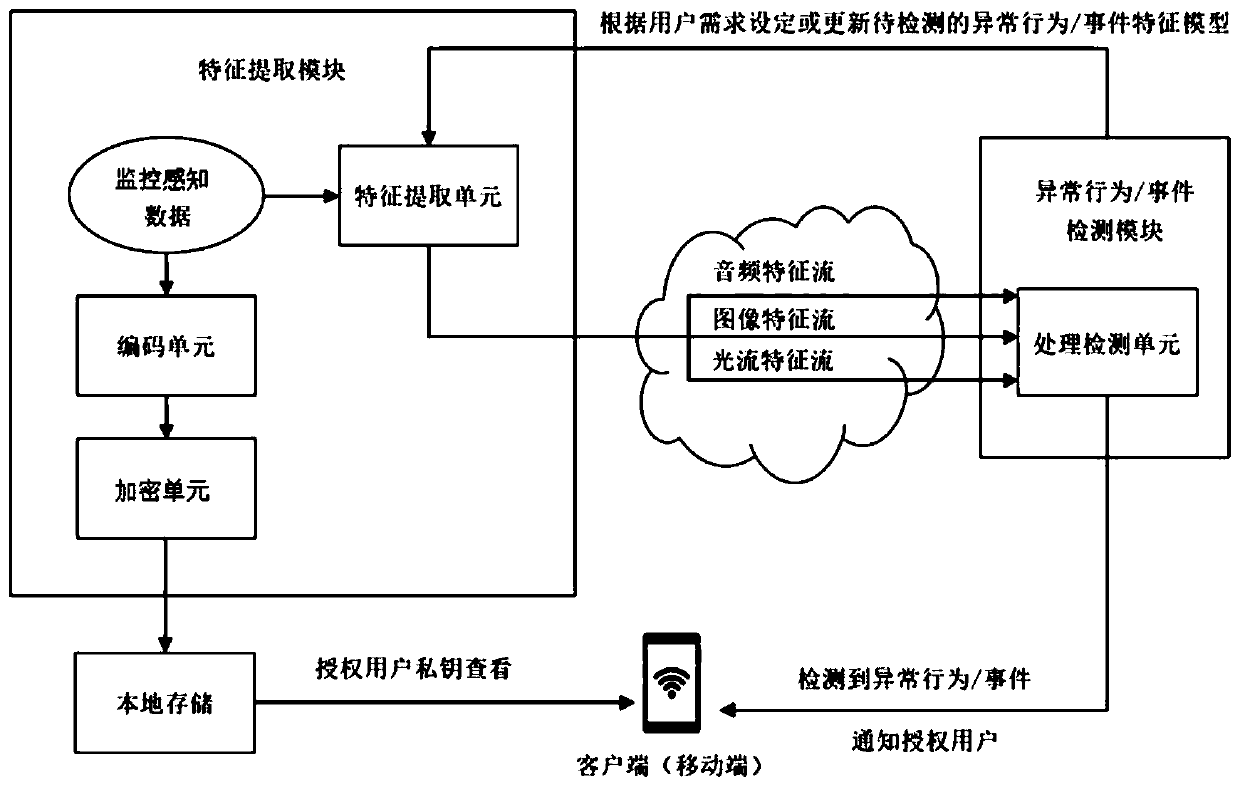
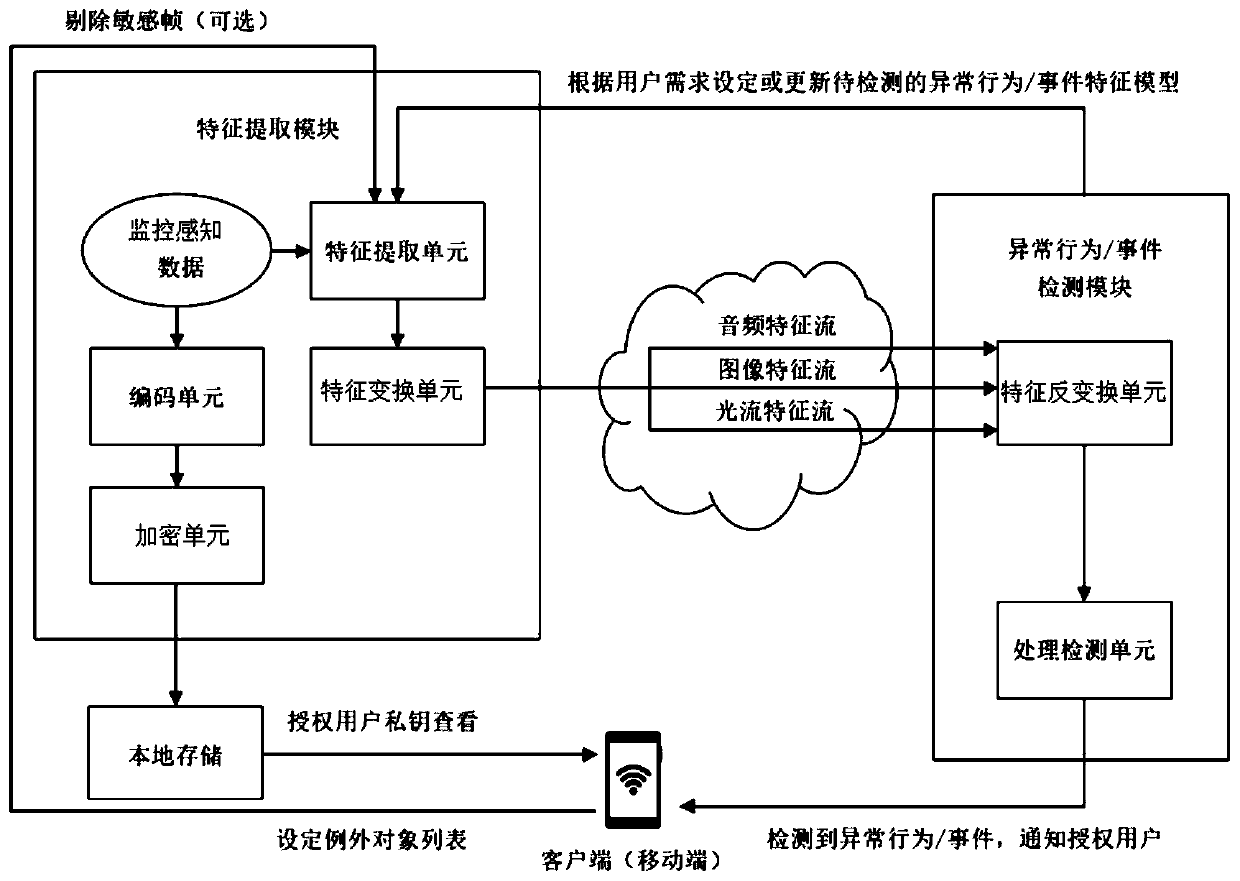
[0084] According to the implementation mode of the present application, a monitoring system for protecting privacy is also proposed, such as figure 2 As shown, it includes: a monitoring perception module, a feature extraction module and an abnormal behavior / event detection module; a monitoring perception module, which is used to obtain the monitoring perception data of the monitoring scene; a feature extraction module, which is used to extract the real-time feature flow of the monitoring perception data, and Send the real-time feature stream to the abnormal behavior / event detection module; the abnormal behavior / event detection module is used to input the real-time feature stream into the pre-trained deep neural network model to detect abnormal behavior / events. The monitoring perception data includes at least one of the following data: video data, audio data, smoke data, light data, and temperature data.
[0085] The dual-stream camera in the prior art is a camera capable of s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com