Server credibility measuring method
A server and reliability technology, applied in the field of trusted computing, can solve problems such as high hardware cost, reduced motherboard compatibility, and equipment stability, and achieve the effect of reducing costs and facilitating promotion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
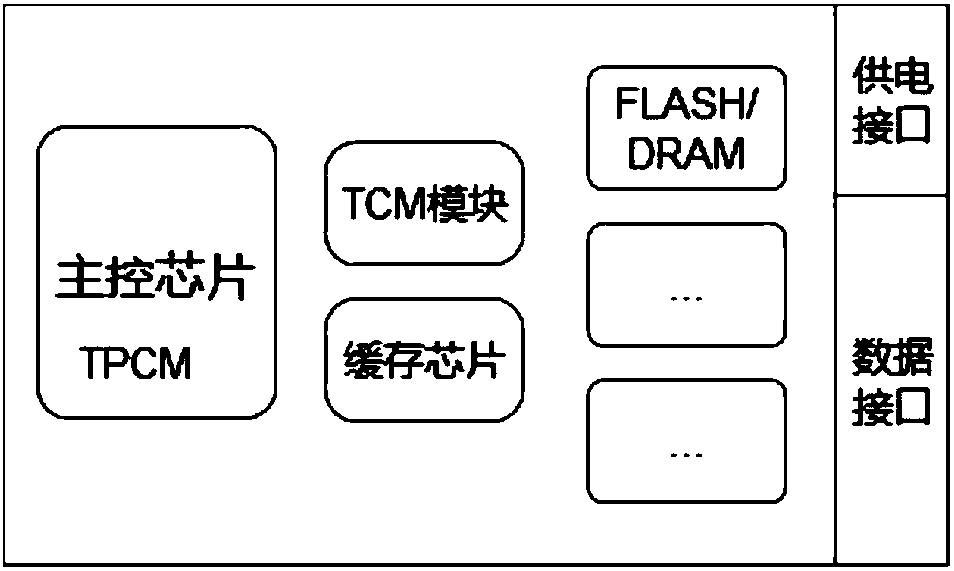
[0028] The device diagram of the TPCM storage system used to realize the trusted computing in the present invention is as follows figure 1 As shown, it mainly includes the following functional modules: main control chip, TPCM firmware is stored in the main control chip, which is used to complete the security measurement function; the trusted password module TCM is used to realize the trusted password verification function; The cache chip is used to cache data; the FLASH / DRAM module is used to store data; the power supply interface is used to directly supply power to the TPCM storage system through the motherboard battery after the device is turned on, so that the main control chip in the system Priority power-on; data interface, the data interface can support data communication protocols commonly used in the field such as SATA / SAS / PCIE.
[0029] Compared with the common storage system in the prior art, the above-mentioned TPCM storage system proposed by the present invention a...
Embodiment 2
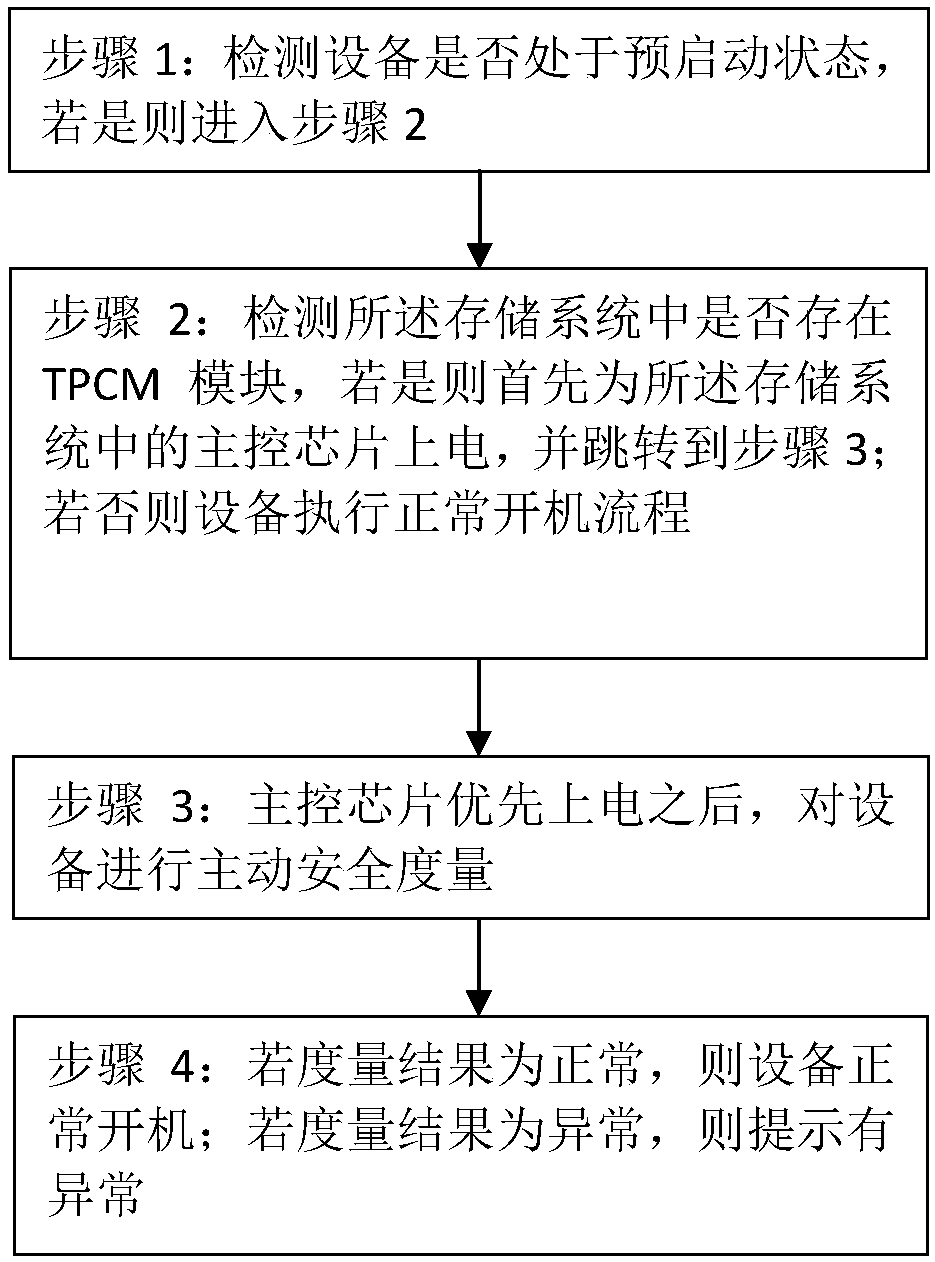
[0045] The device in this embodiment is a server, and the server also includes a baseboard management controller (BMC) for managing and controlling the server.
[0046] After judging that the flag bit in the storage system is 1, measure the integrity of the BIOS firmware and BMC firmware of the server at the same time. Do not turn on.
Embodiment 3
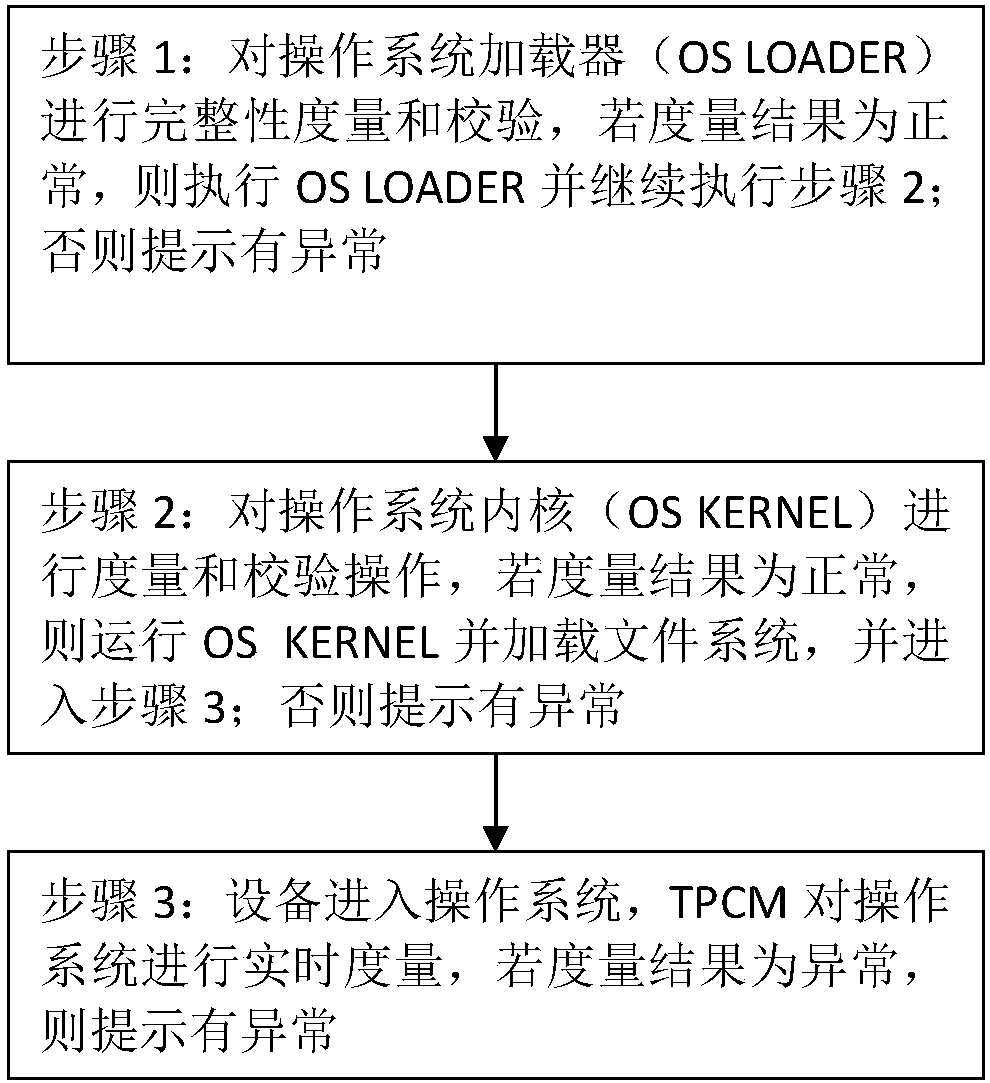
[0048] In this embodiment, UEFI is used to replace the traditional BIOS to boot the device, and the integrity of the BIOS firmware needs to be measured when measuring the integrity of the device.
[0049] Preferably, when the device is a server, it is also necessary to measure the integrity of the BIOS firmware of the server and the BMC at the same time, and only when the measurement results of the two are normal, the normal boot process of the server is continued, otherwise it will not start.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com