Vulnerability scanning and maintenance method for computing device system
A vulnerability scanning and computing equipment technology, applied in the field of electronic communication, can solve problems such as complex organizational structure, multiple distribution points, complex network structure, etc., and achieve the effect of reducing waiting time and saving management and communication expenses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention is described in further detail below in conjunction with accompanying drawing:
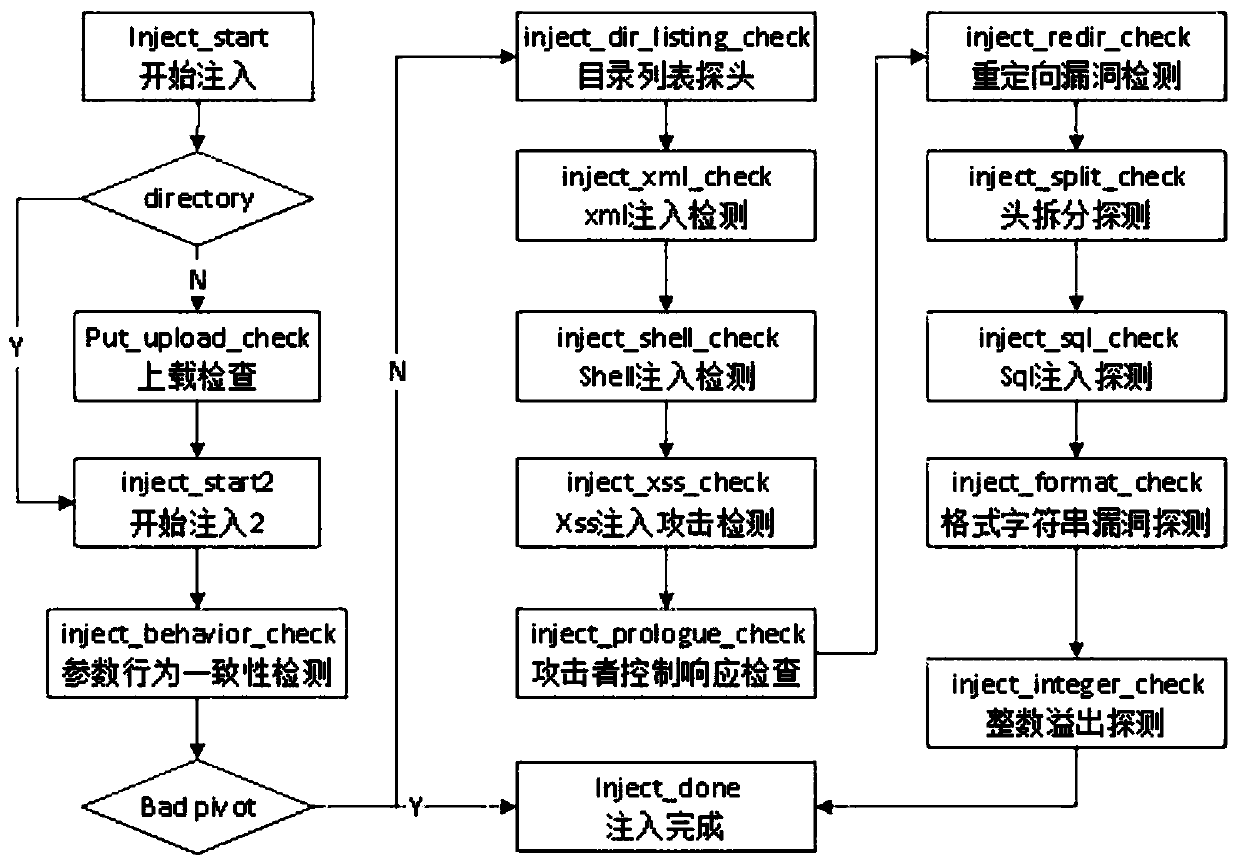
[0059] see figure 1 , the vulnerability scanning and maintenance method of the present invention needs to capture and record a lot of new urls, requests and links, how to organize and apply these structures will have an impact on the performance of the program, and the preservation and management in the vulnerability scanning and maintenance method will be introduced below Data structures for urls, requests and links.
[0060] In this vulnerability scanning and maintenance method, url information will be stored in a pivot tree structure and stored in a tree structure. The pivot node is mainly composed of pointers to parent nodes and child nodes, pointers to the url request packet and response packet, and some detection status indication parameters of the node in the crawler module.
[0061] The process of building a pivot tree has three steps:
[0062] req->pivot->c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com