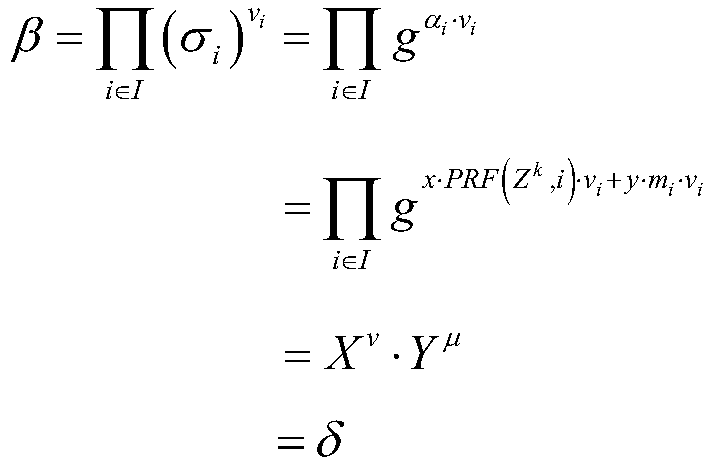Agent-based cloud storage data integrity detection method
A technology of data integrity and detection methods, applied in the field of cloud security, can solve problems such as low efficiency and unsuitability for lightweight mobile devices, and achieve high computing efficiency and improve computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
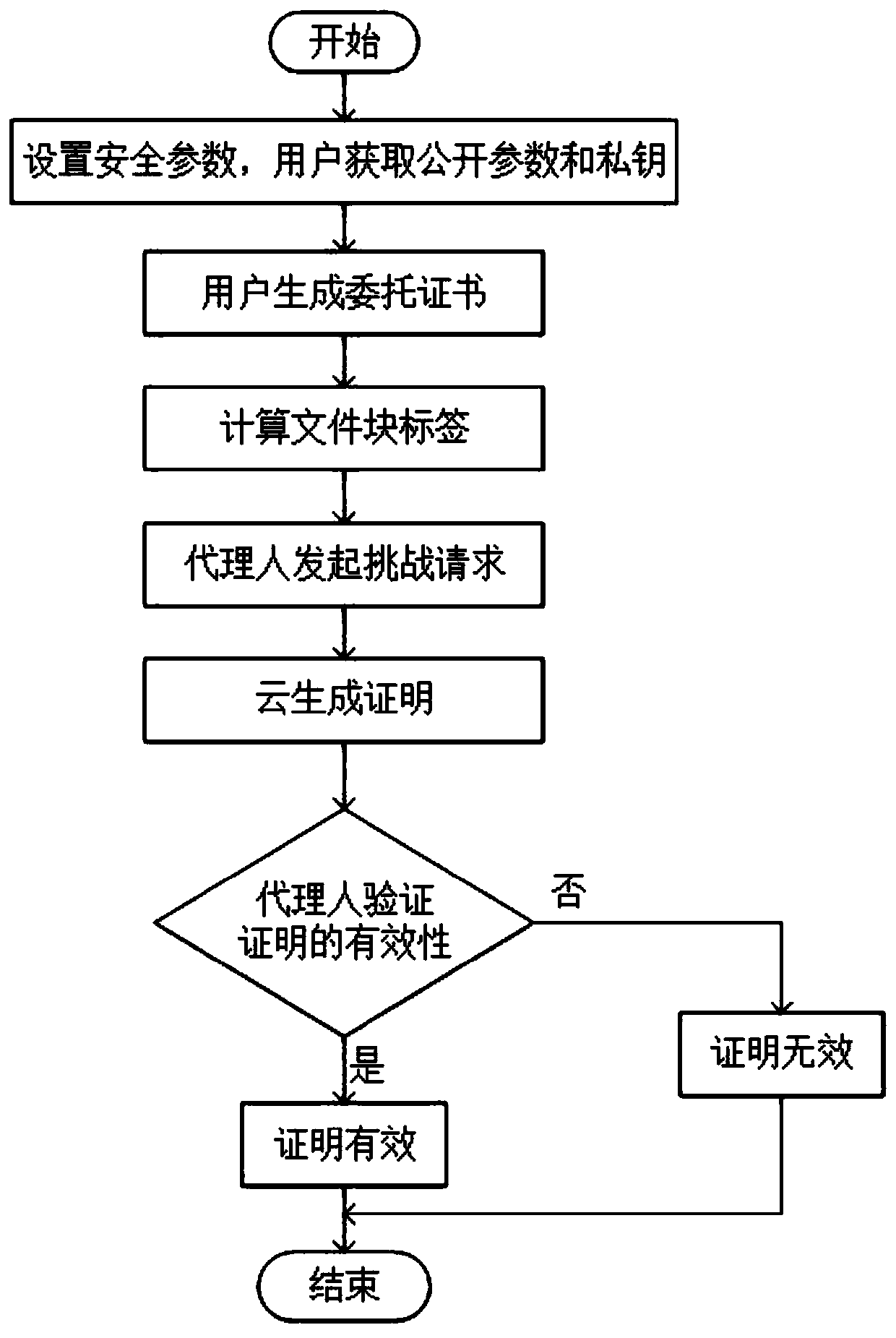
[0039] Such as figure 1 Shown, an agent-based cloud storage data integrity detection method, the method includes the following steps:
[0040] Step 1: System initialization;
[0041] Select the security parameter λ, the user selects a prime number p with λ bit length, and the finite field Z p Generator g, random signature public-private key pair (spk, ssk), signature scheme (Sig, Ver), the signature scheme can specifically use the DSA digital signature standard algorithm; pseudo-random function PRF, and random integers x, y∈Z p , calculate X=g x ,Y=g y ; cloud selection z ∈ Z p , calculate Z=g z , the system public parameters are PP=(p, g, spk, PRF, X, Y, Z).
[0042] Step 2: entrust an agent;
[0043] The user generates a power of attorney w, which includes the identity information of the principal and the agent and the validity period and other information, and the user selects k∈Z p , calculate K=g k , and then sign the proxy book and k with the private key ssk to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com