Network security domain knowledge graph construction method and device for dynamic threat analysis
A technology of network security and domain knowledge, applied in the field of network security and network security of dynamic threat analysis, can solve the problems of quantitative deviation of threat transfer probability, difficulty in applying threat risk analysis, affecting threat path and accuracy of probability measurement, etc., to achieve The effect of strong practicality and operability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
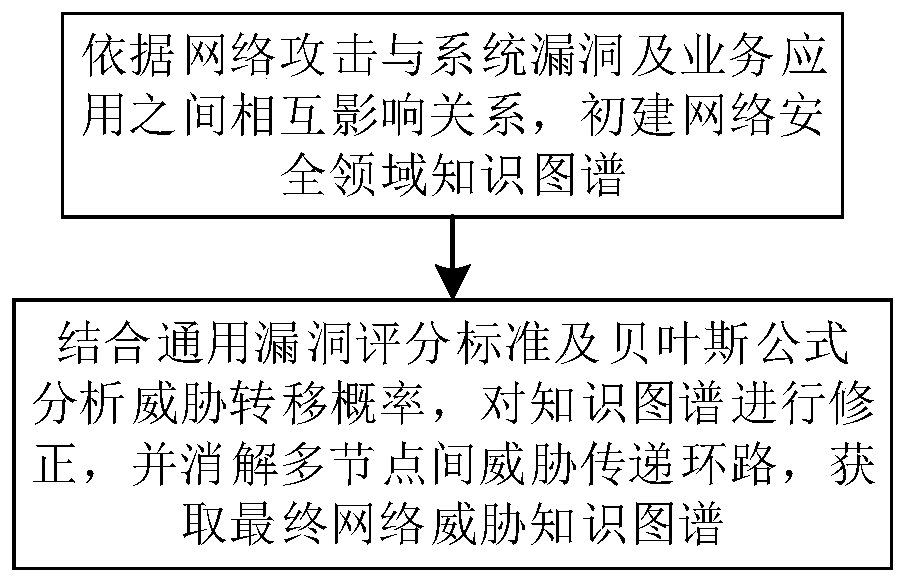
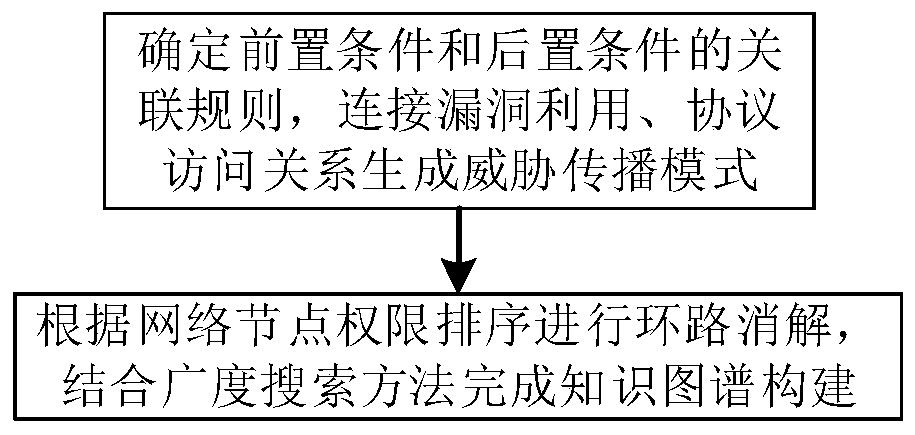
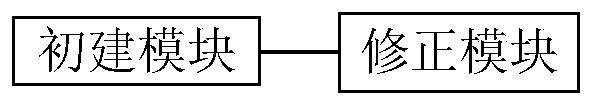
[0032] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions. The technical term involved in the embodiment is as follows:
[0033] Knowledge graph, also known as scientific knowledge graph, is called knowledge domain visualization or knowledge domain mapping map in the library and information industry. Resources and their carriers, mining, analyzing, constructing, mapping and displaying knowledge and their interconnections. By combining the theories and methods of applied mathematics, graphics, information visualization technology, information science and other disciplines with metrology citation analysis, co-occurrence analysis and other methods, and using visual maps to vividly display the core structure, development history, and frontiers of disciplines The modern theory that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com